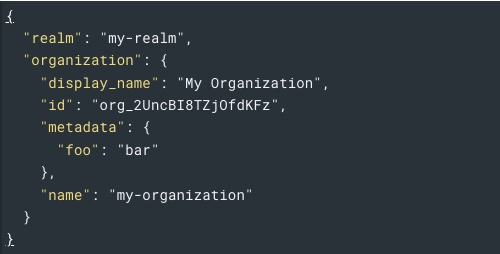
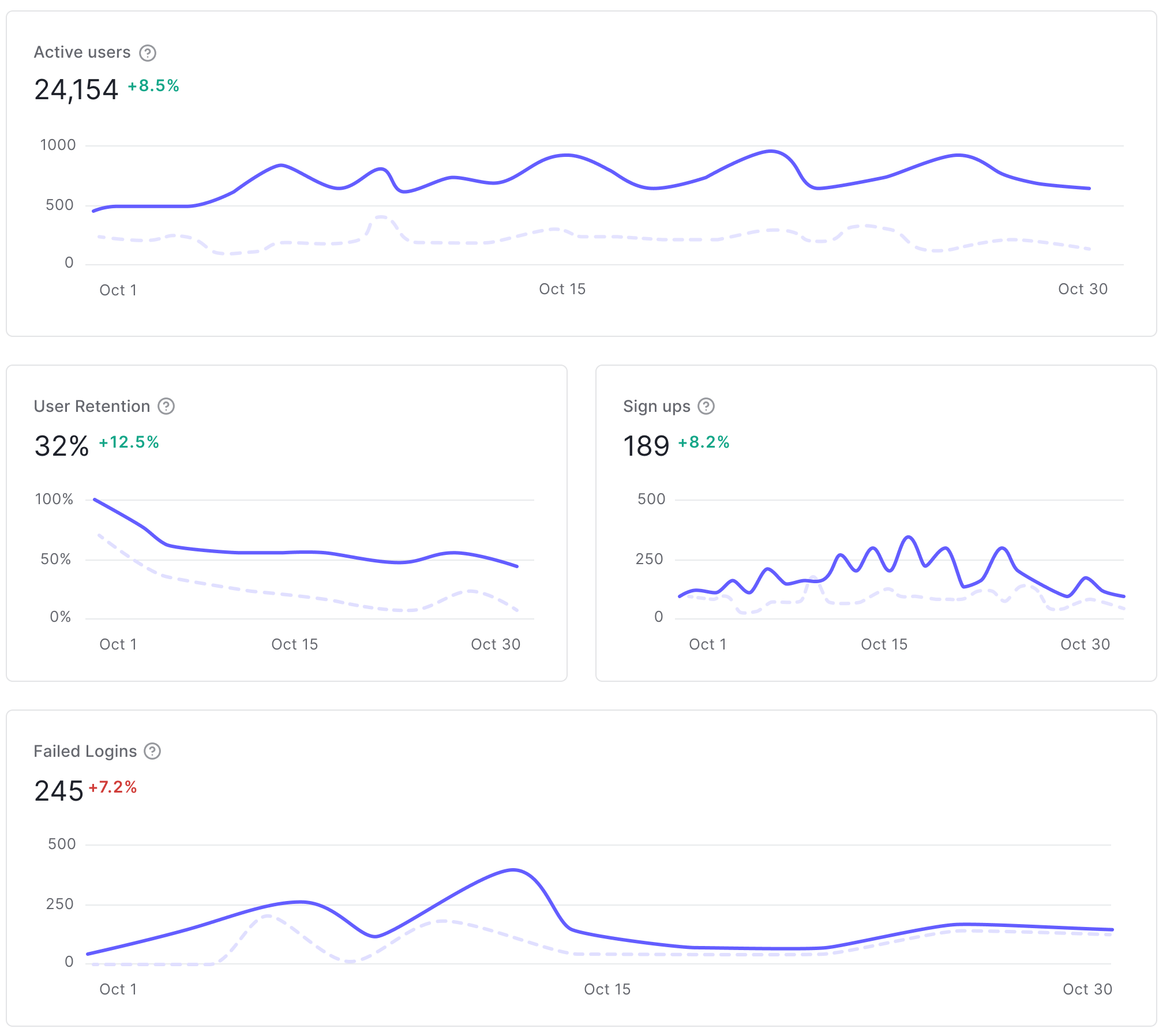
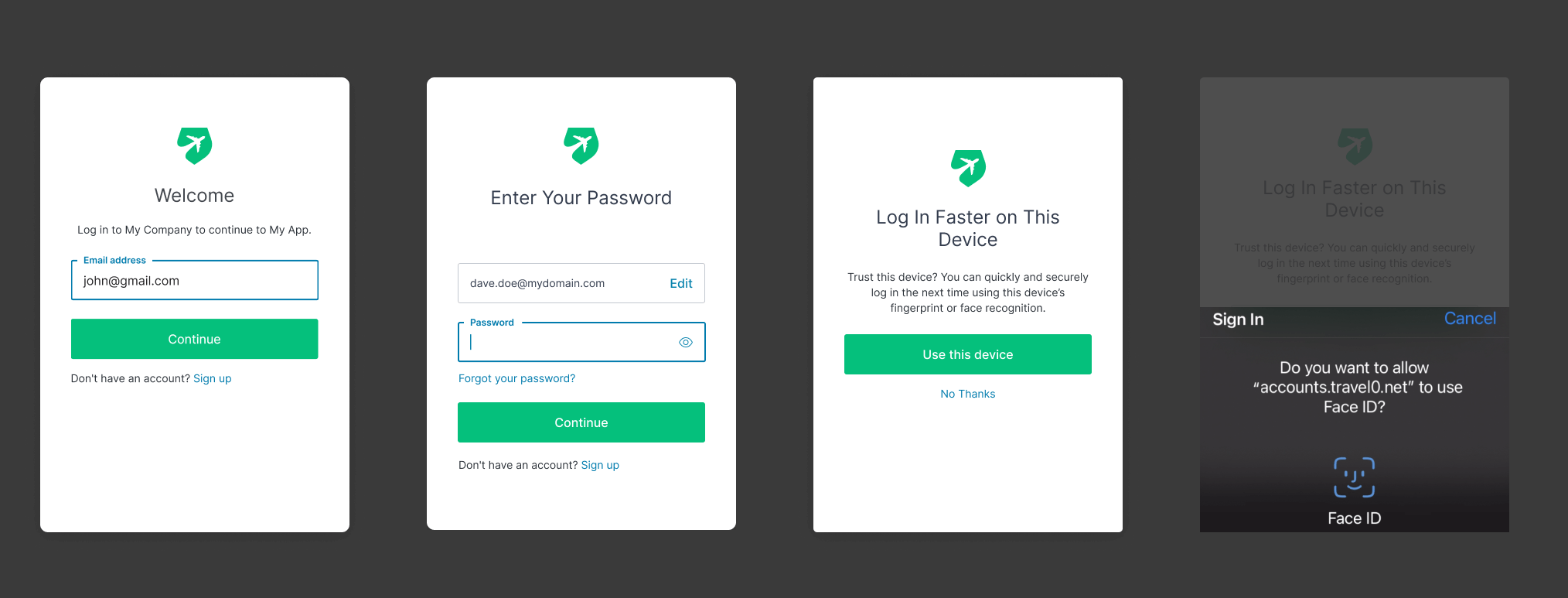
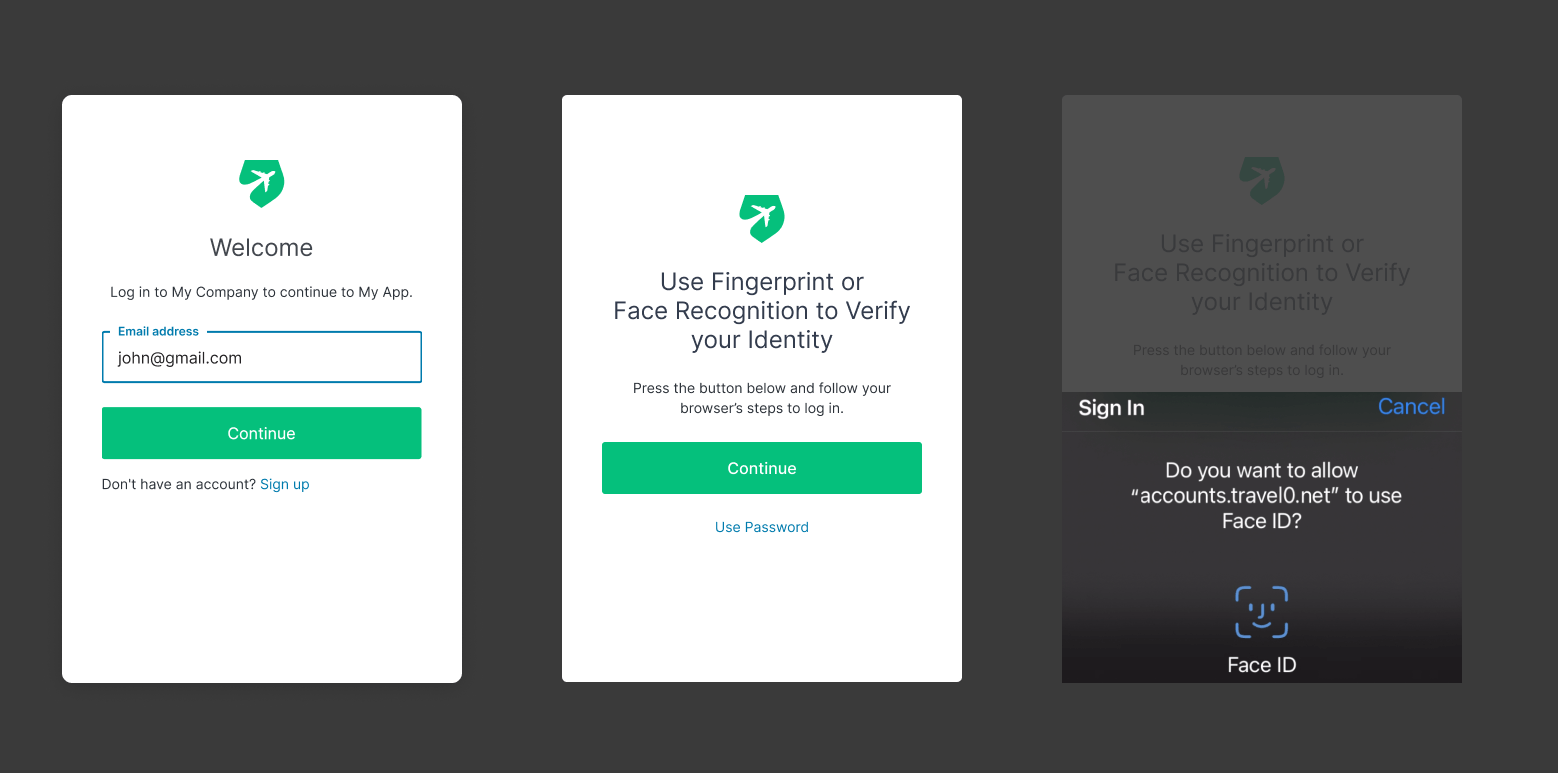
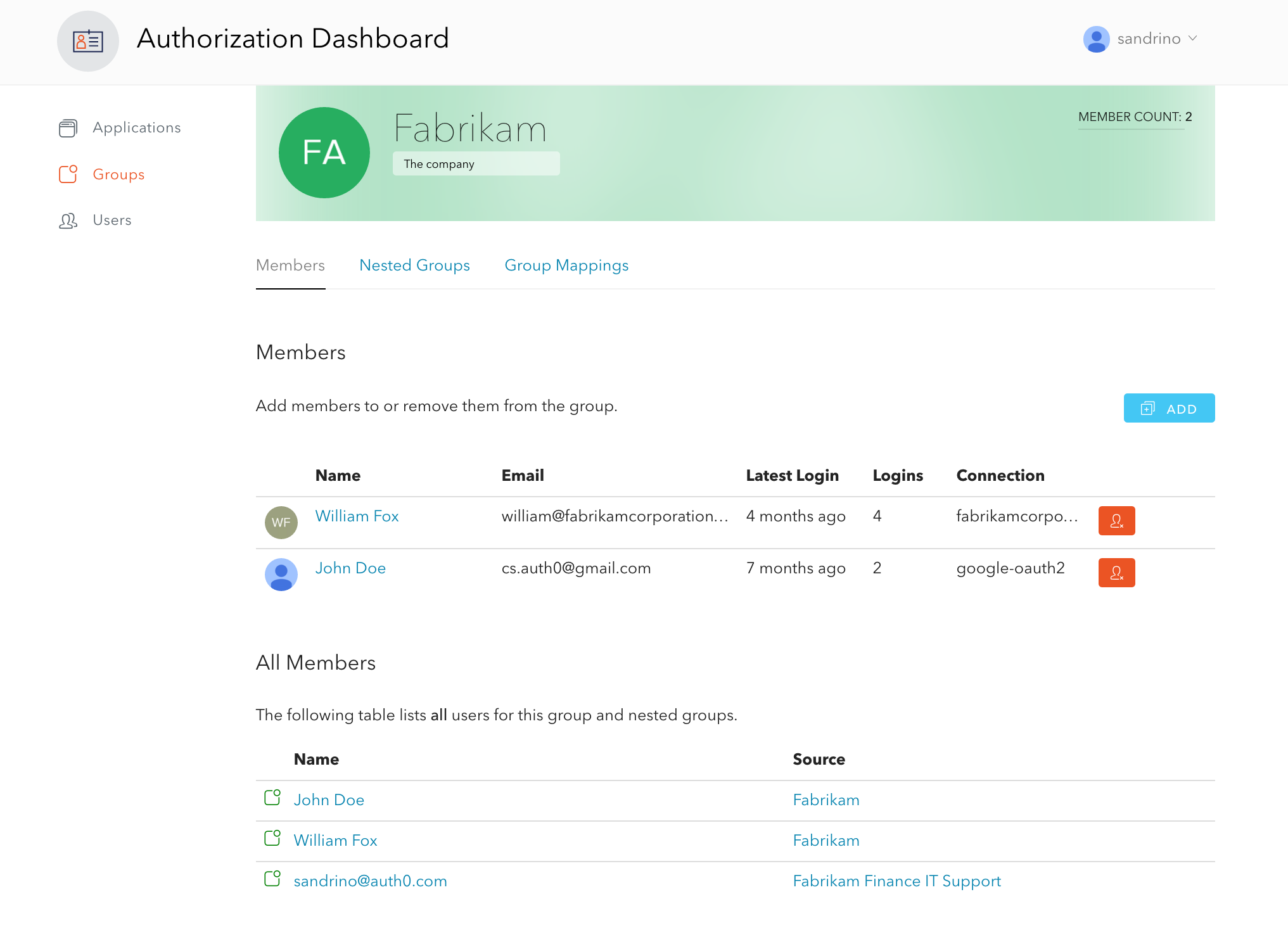
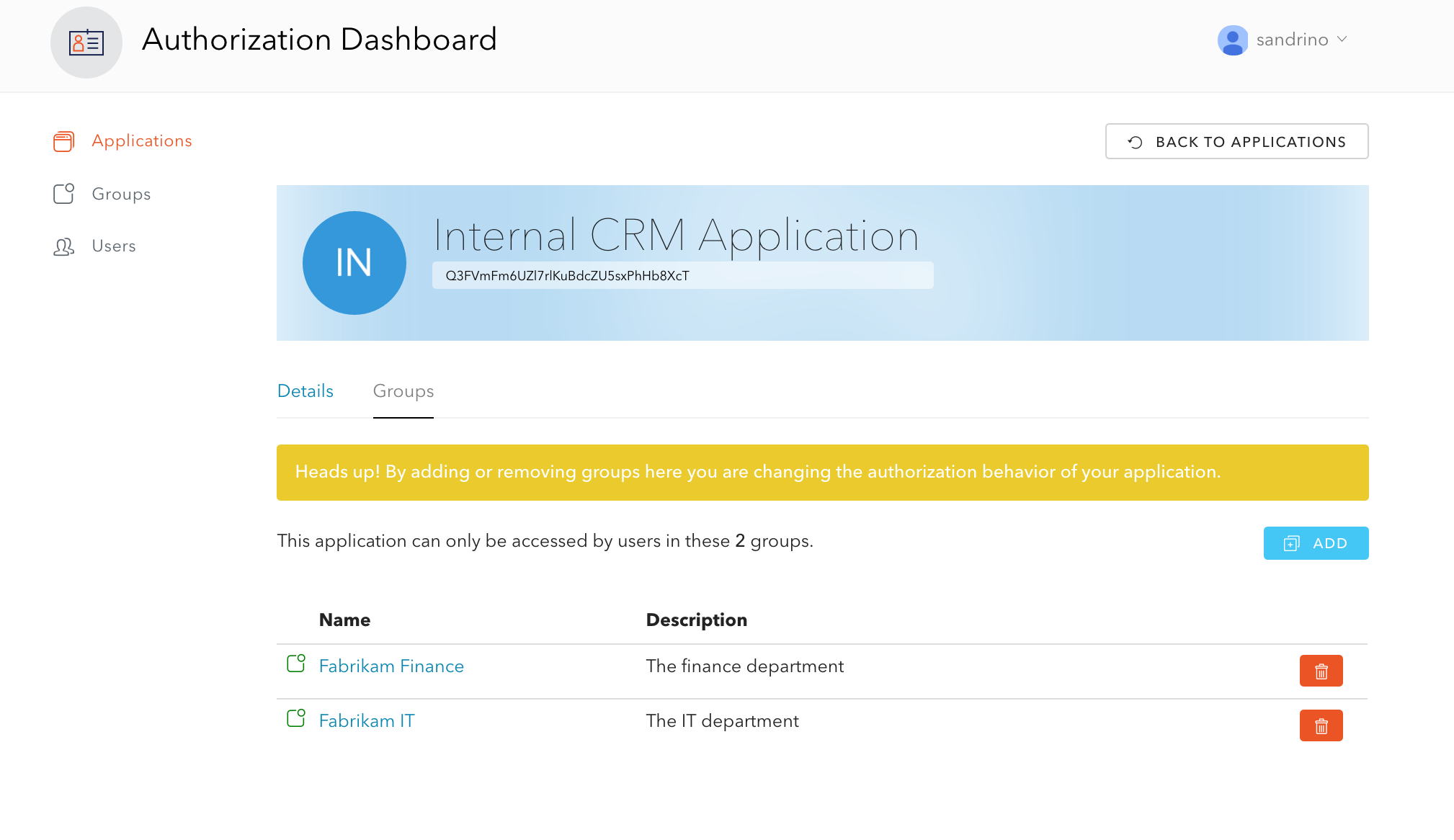
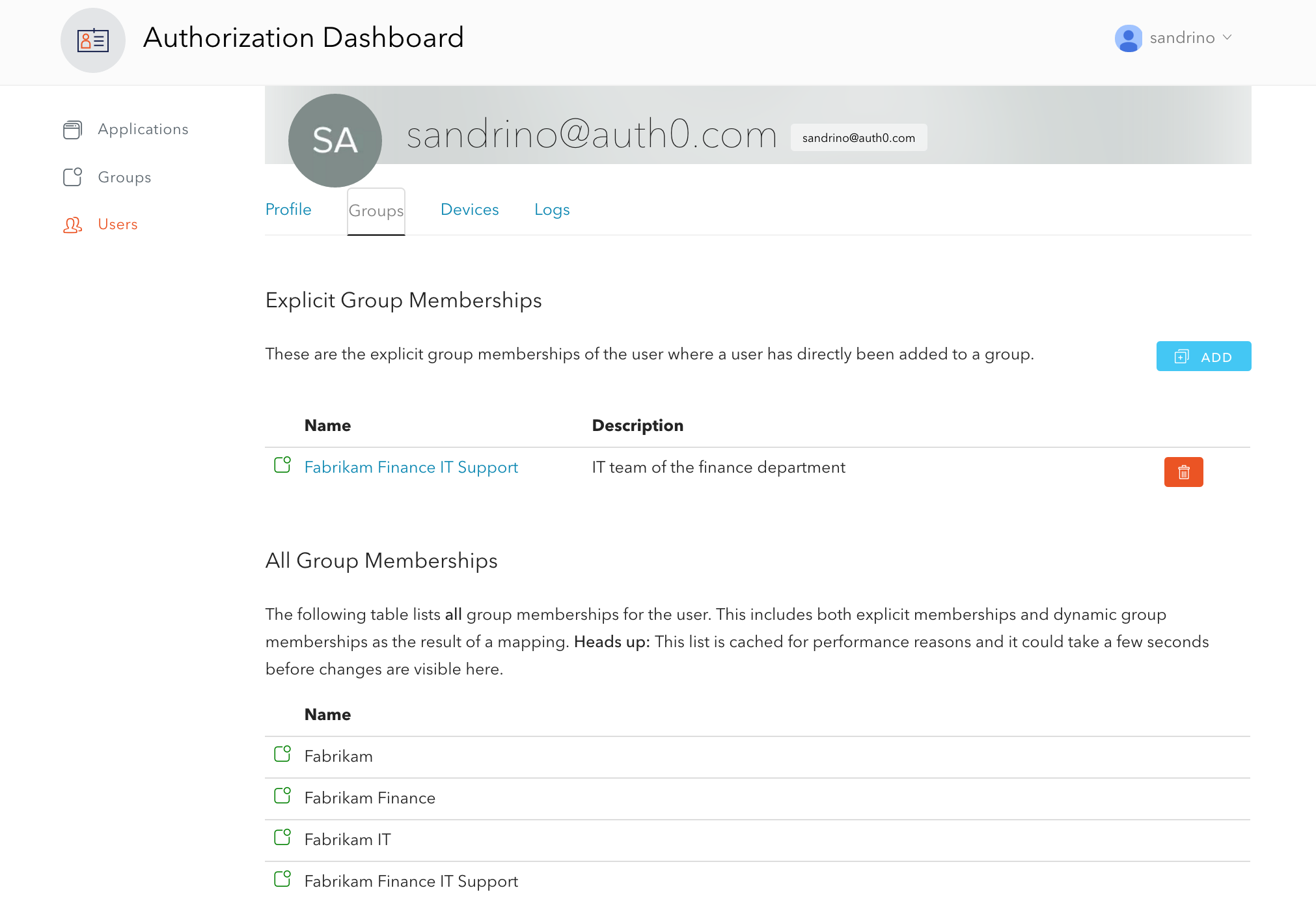
added
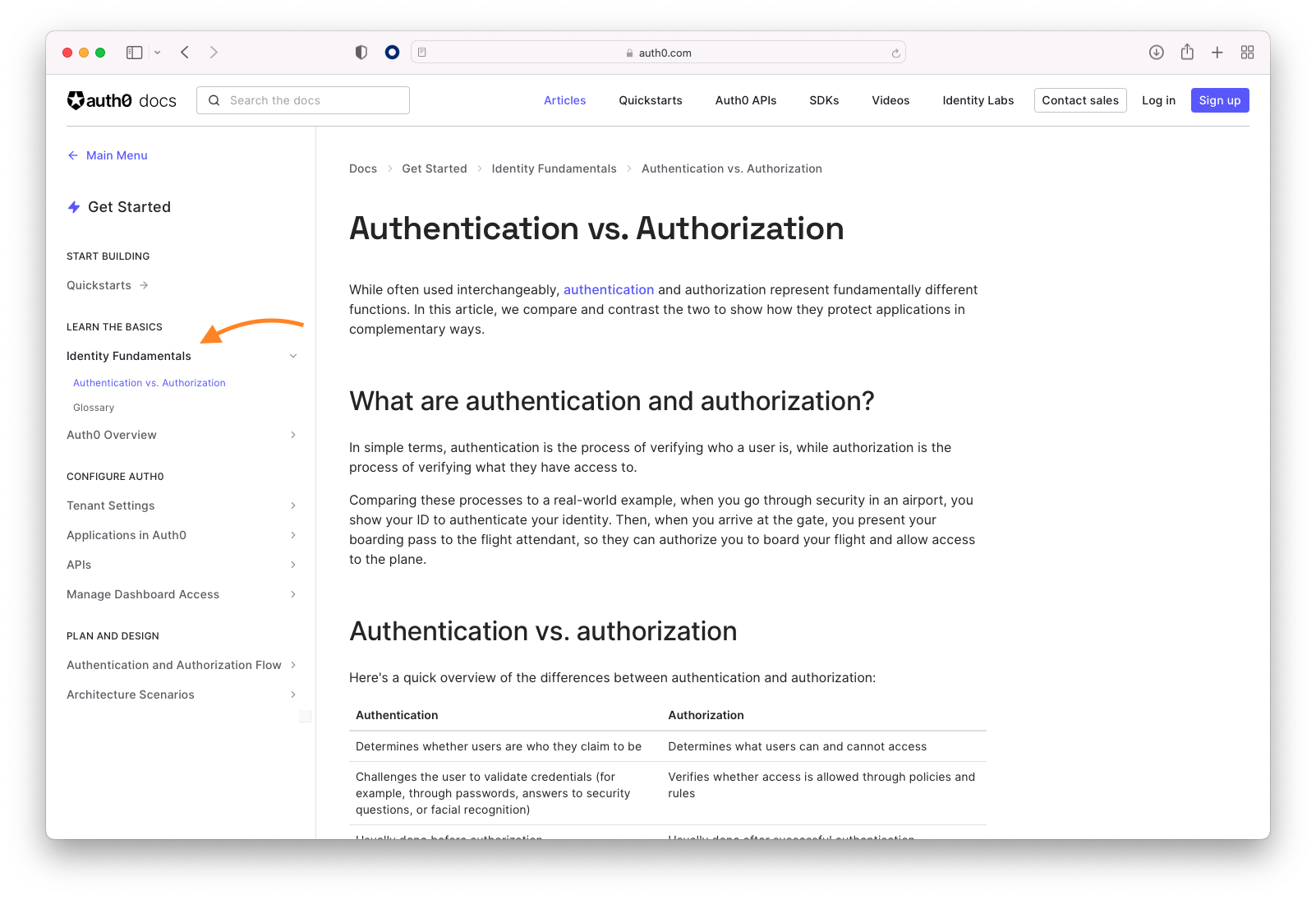
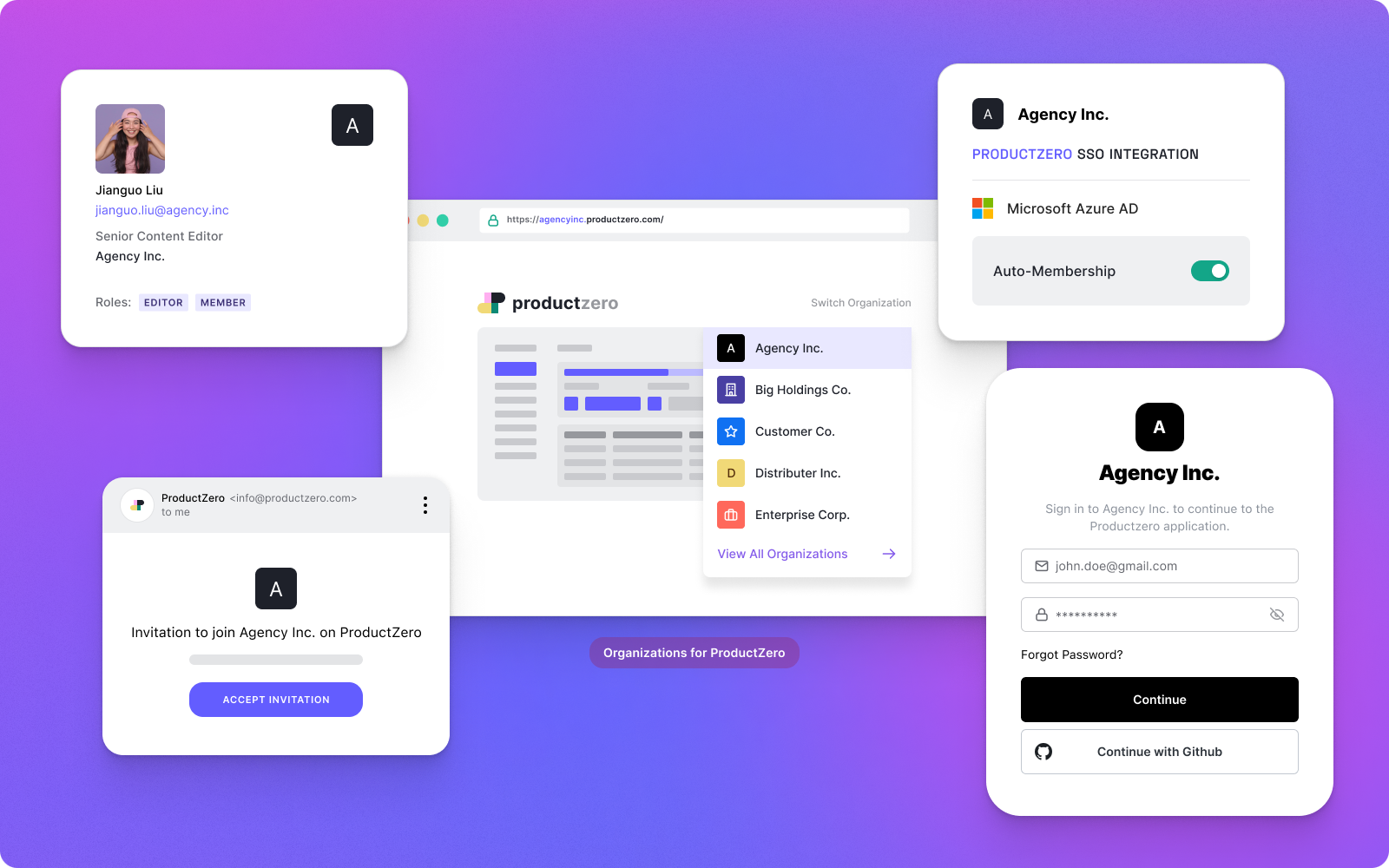
Auth0 Agent Skills (Beta)
We're introducing Auth0 Agent Skills Beta- structured guidance that teaches AI coding assistants how to implement Auth0 authentication correctly across any framework.
Agent Skills are AI-native instructions that work with popular coding assistants like Claude Code, Codex, Gemini CLI, etc... They provide production-ready code patterns, security best practices, and step-by-step implementation flows directly within your development workflow.
Key Features
- Framework Coverage: Support for React, Next.js, Vue, Angular, Express, Nuxt, React Native, and more
- Security First: Built-in best practices for MFA, protected routes, and secure token handling
- Migration Support: Guided migration from Firebase Auth, AWS Cognito, Supabase, and other providers
- Easy Installation: Install via CLI (npx skills add auth0/agent-skills) or directly in Claude Code plugins
- Production Ready: Generate complete authentication implementations in minutes
Getting Started
- Install Auth0 Agent Skills:
npx skills add auth0/agent-skills - Then ask your AI assistant: "Add auth0 to my app" and you're ready to go.
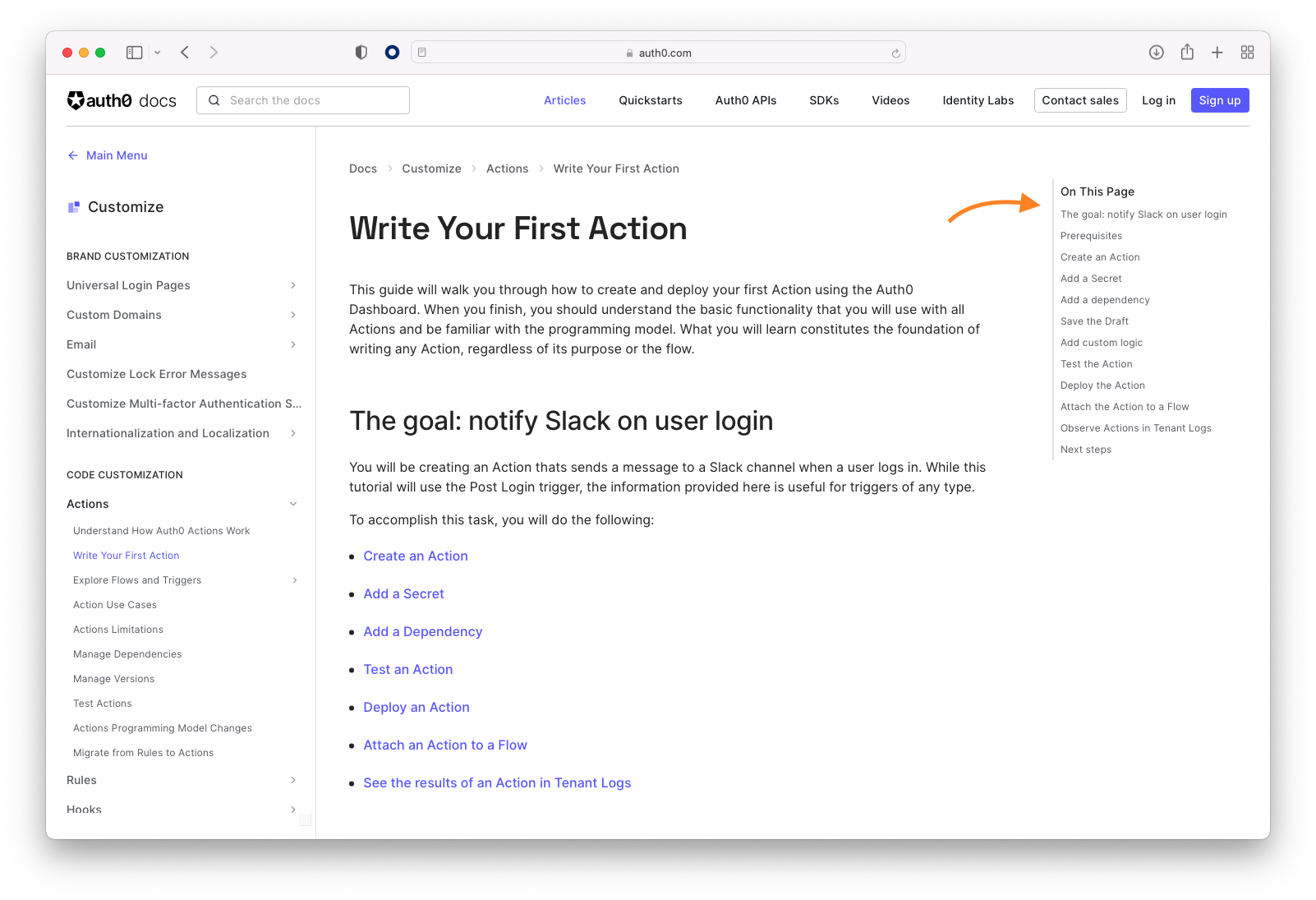
Learn More

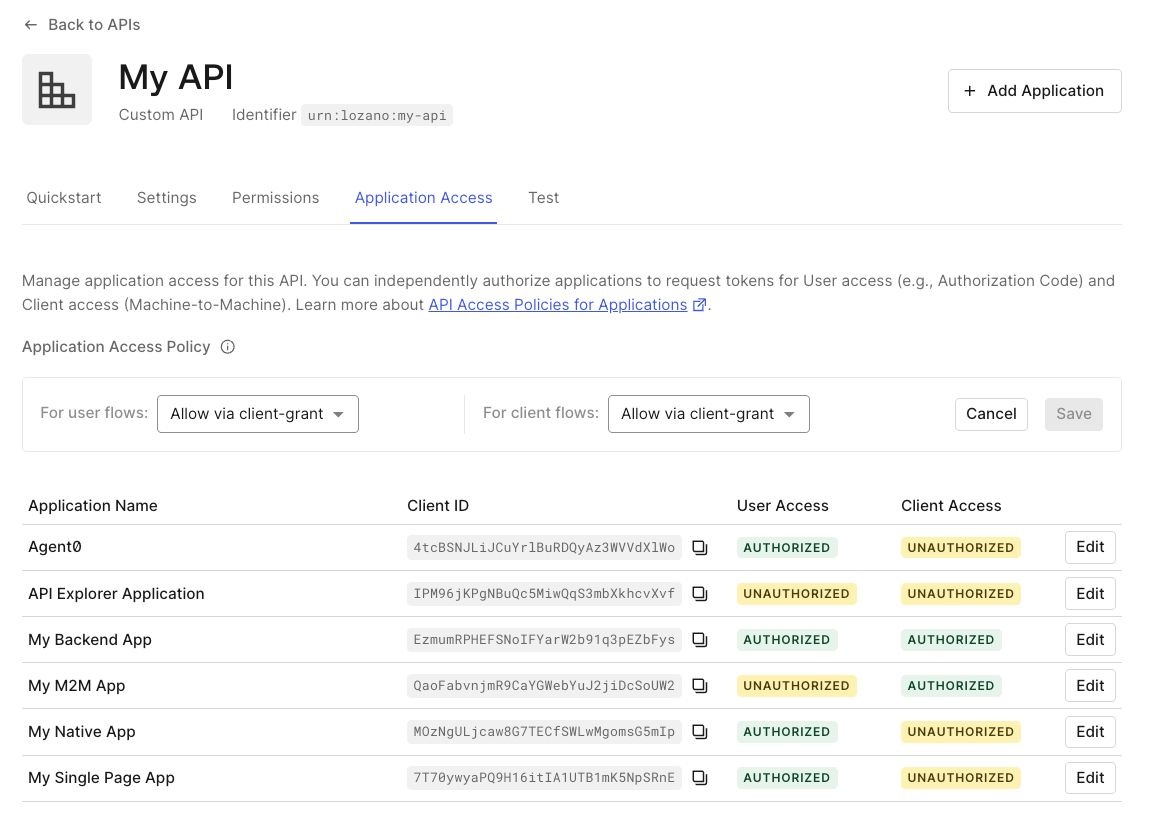

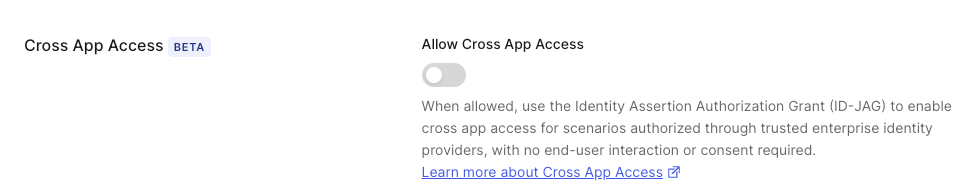
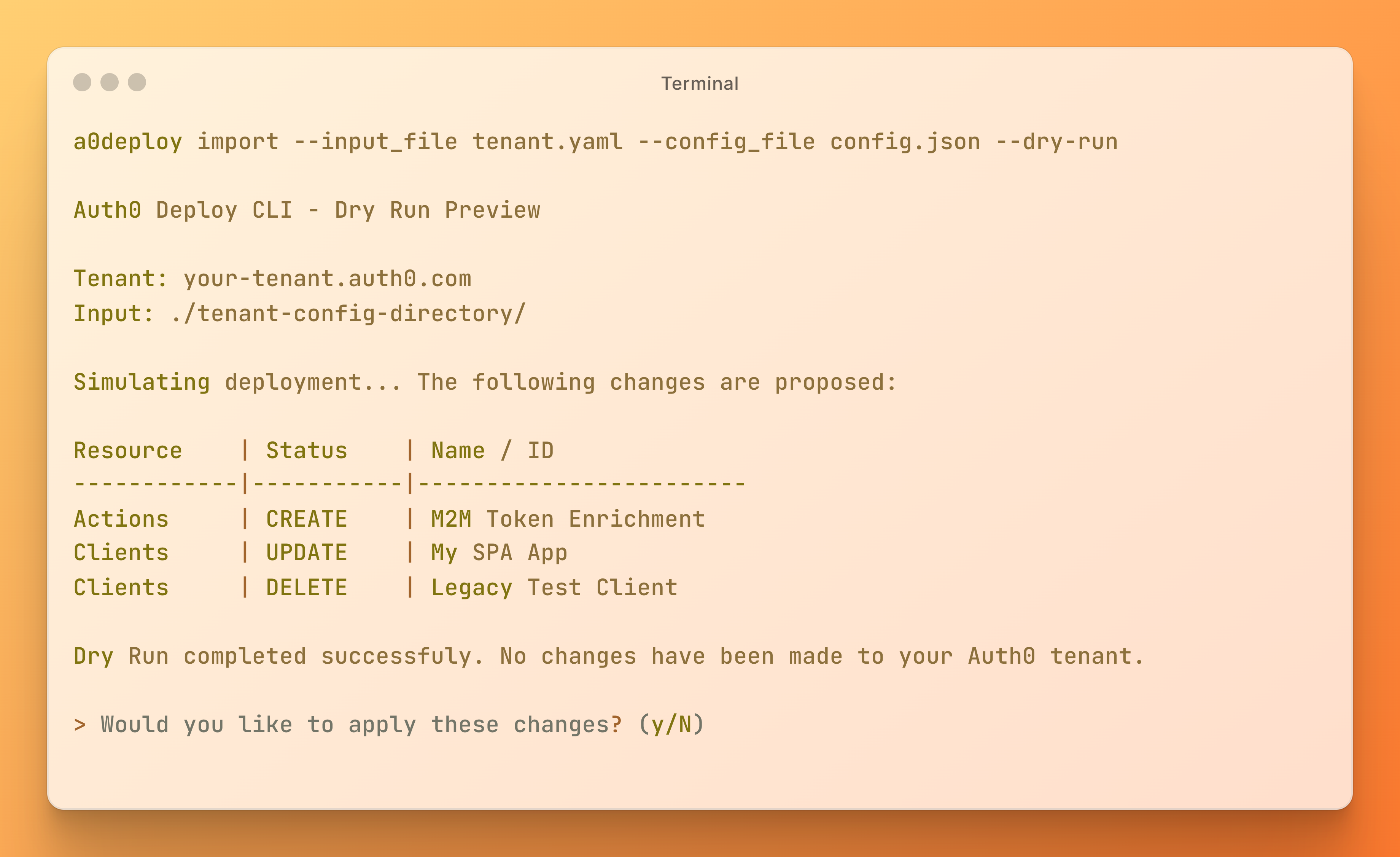




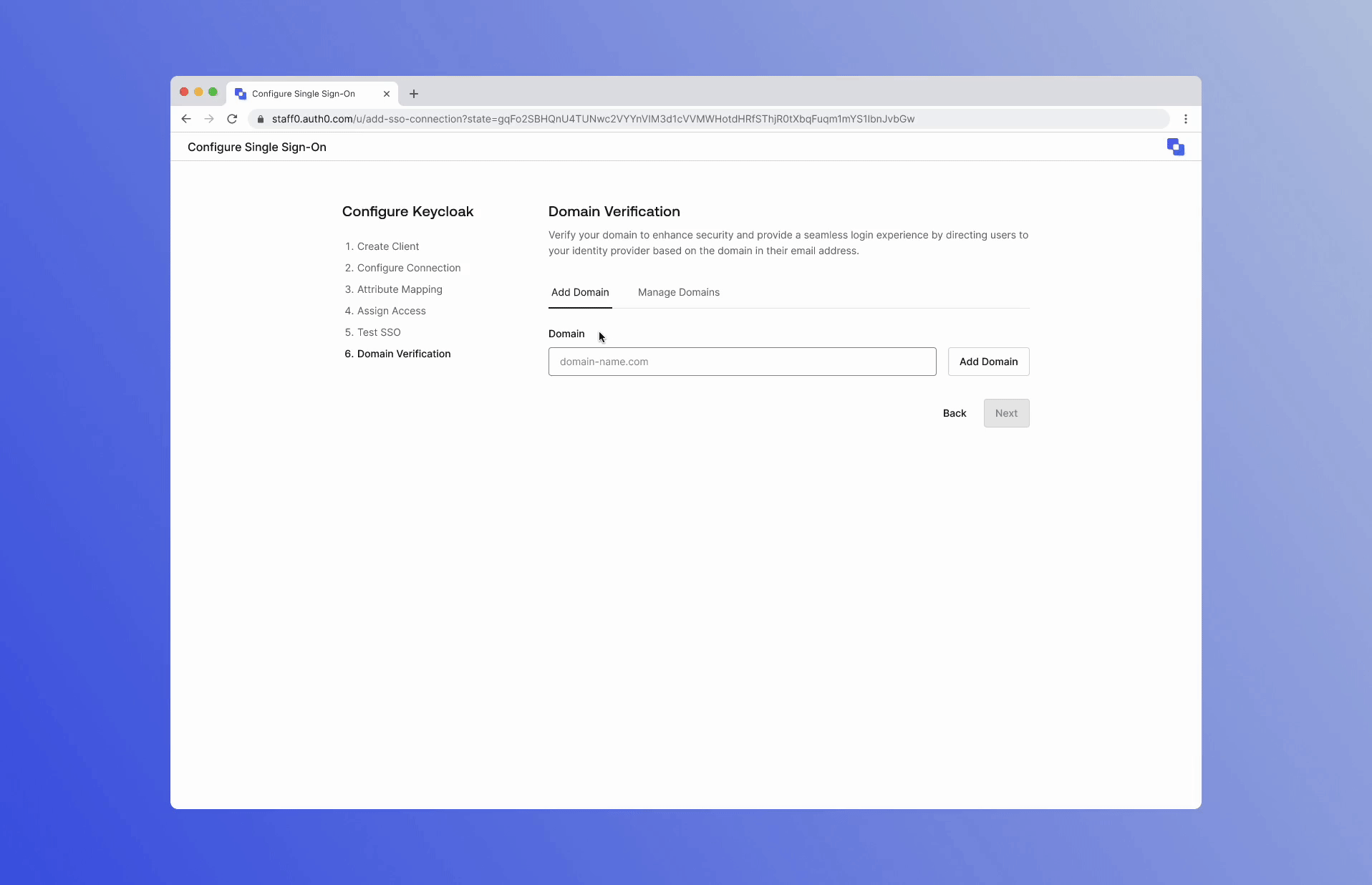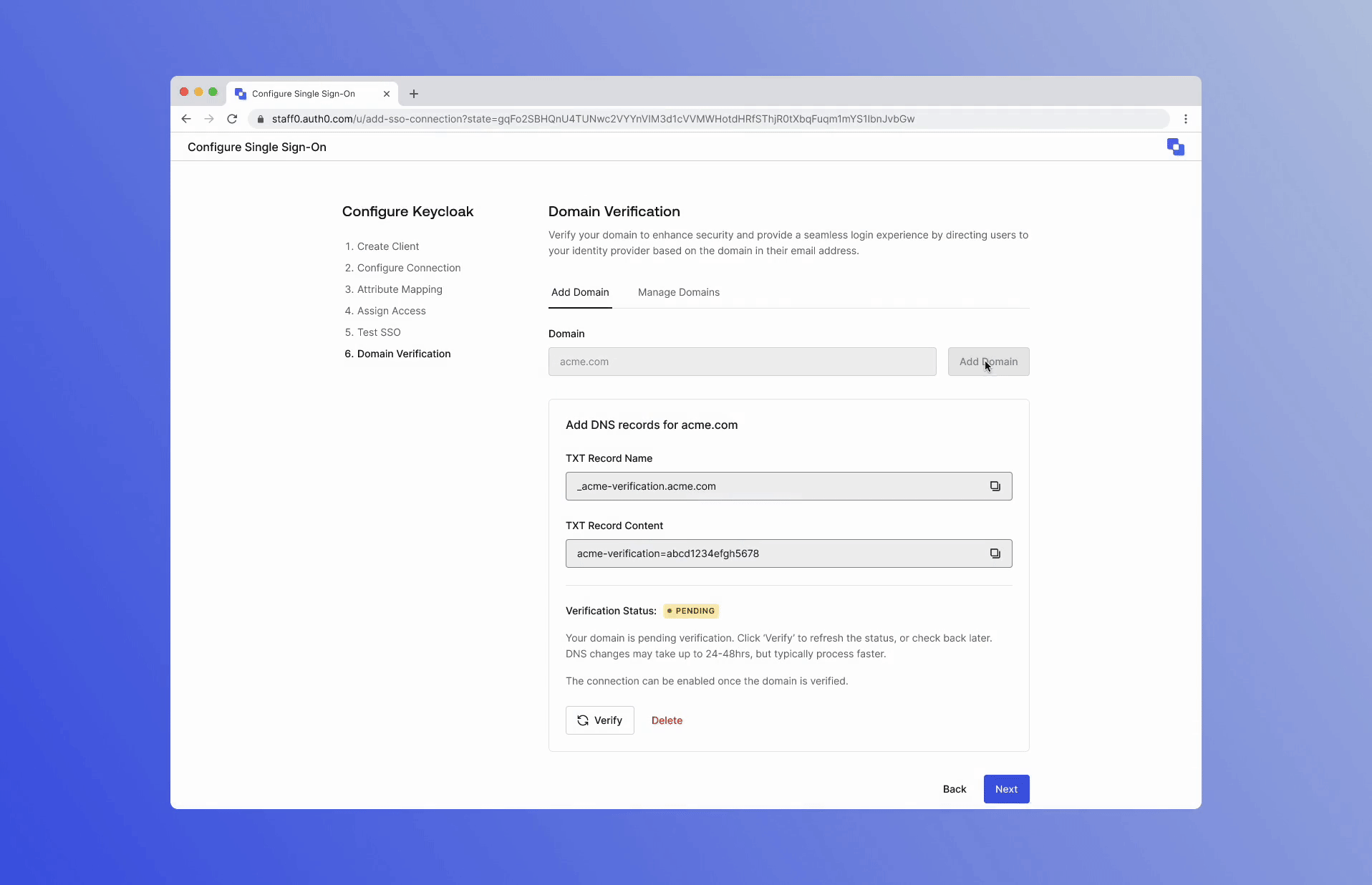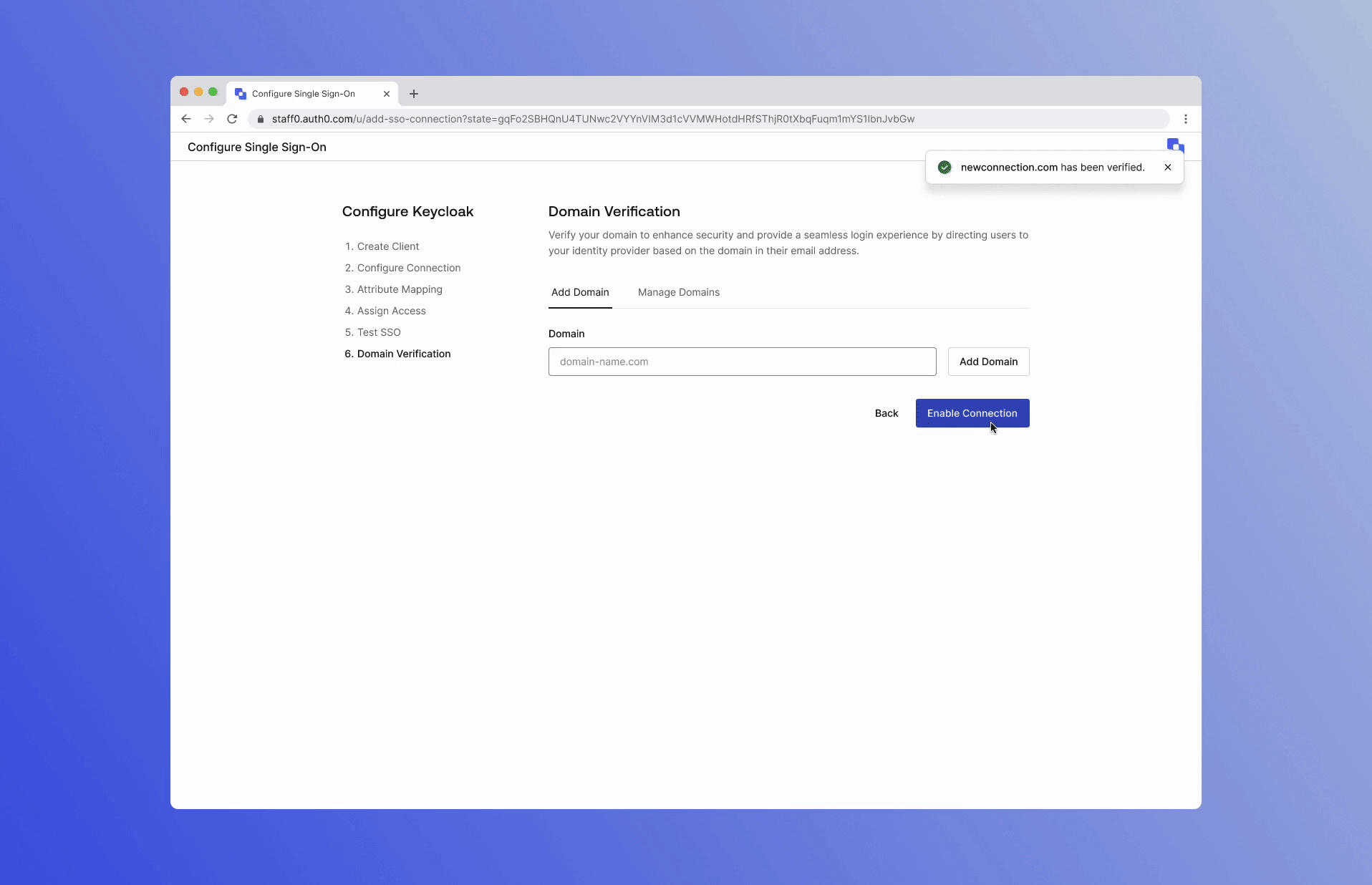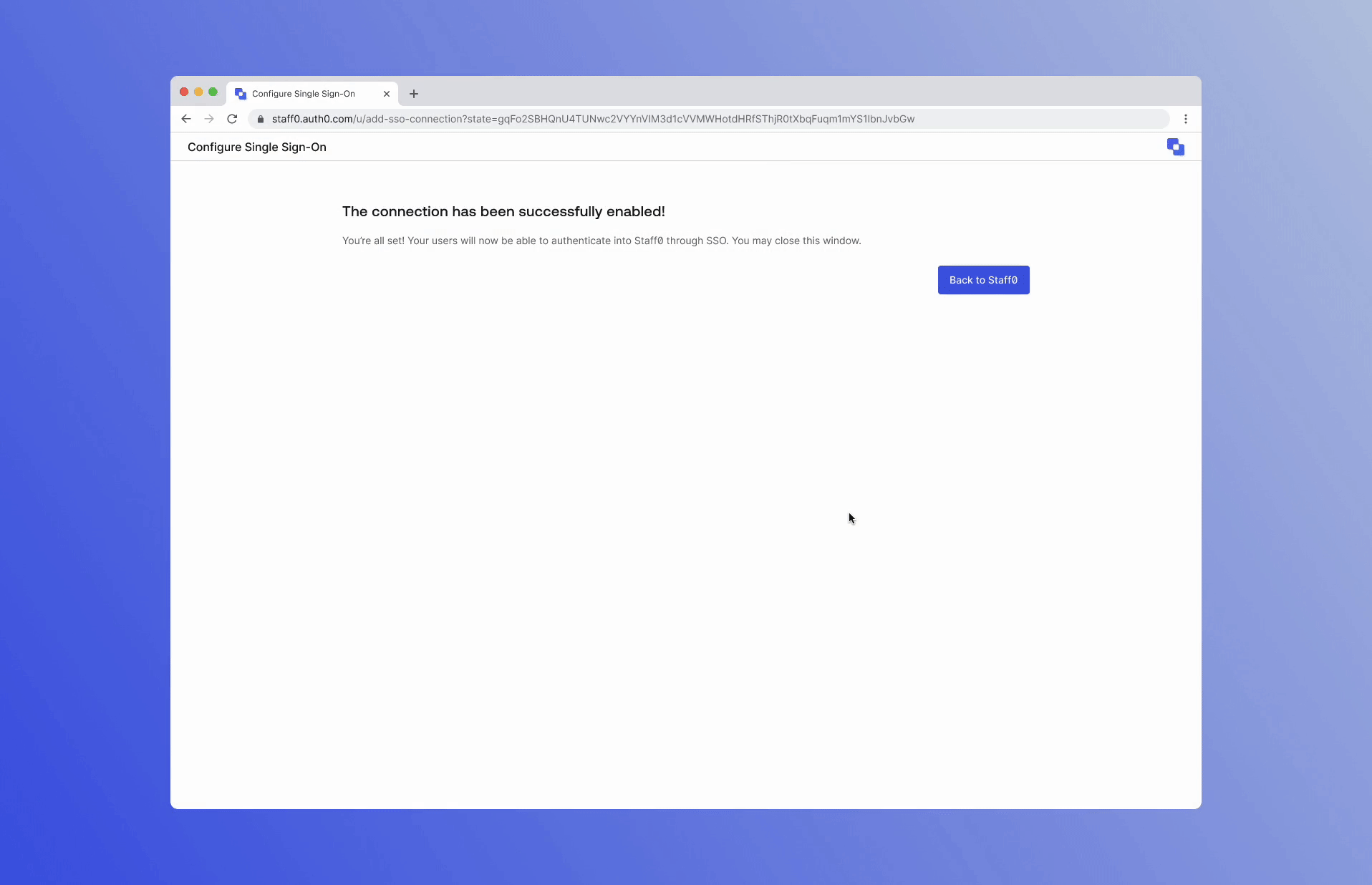
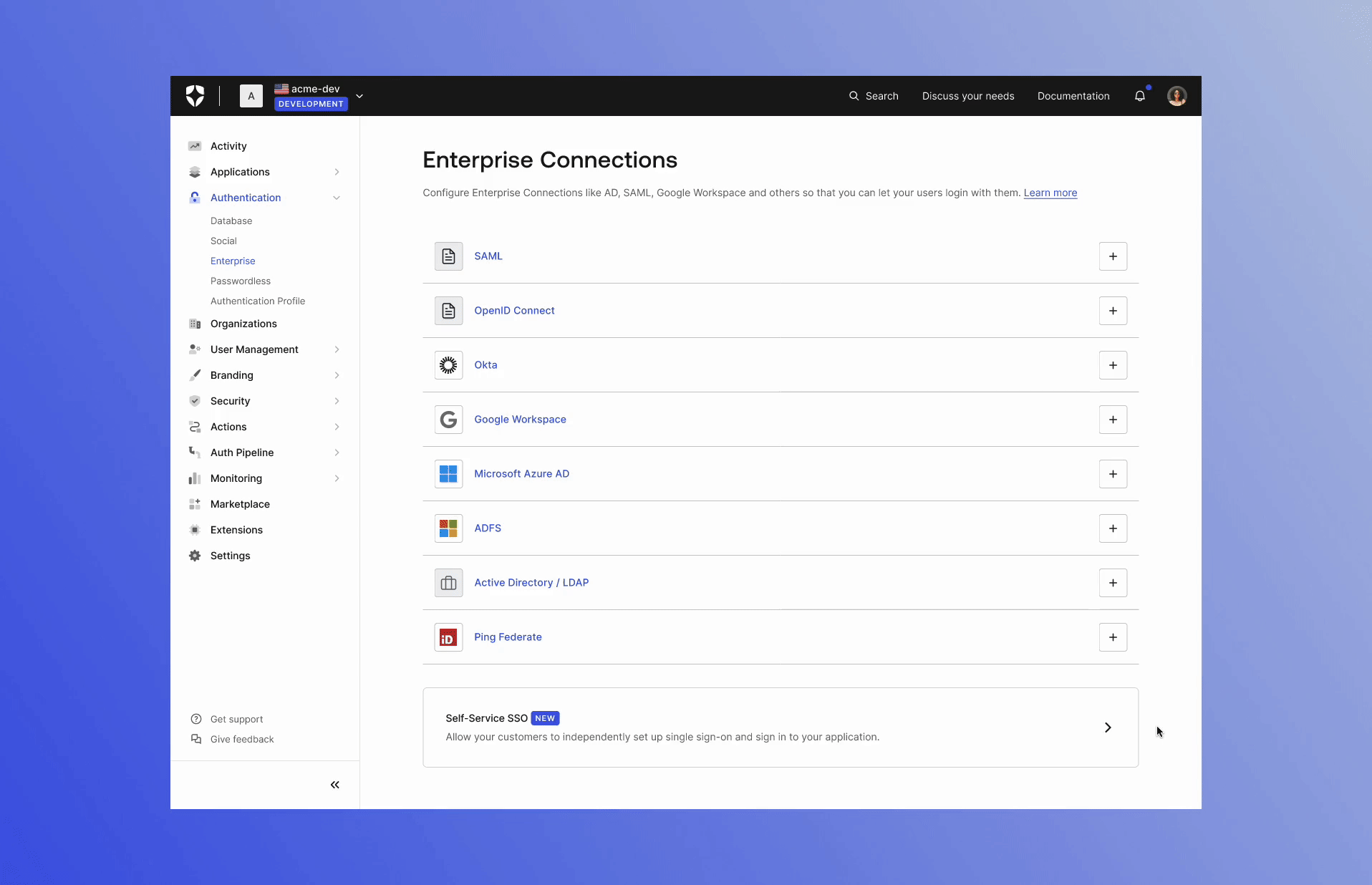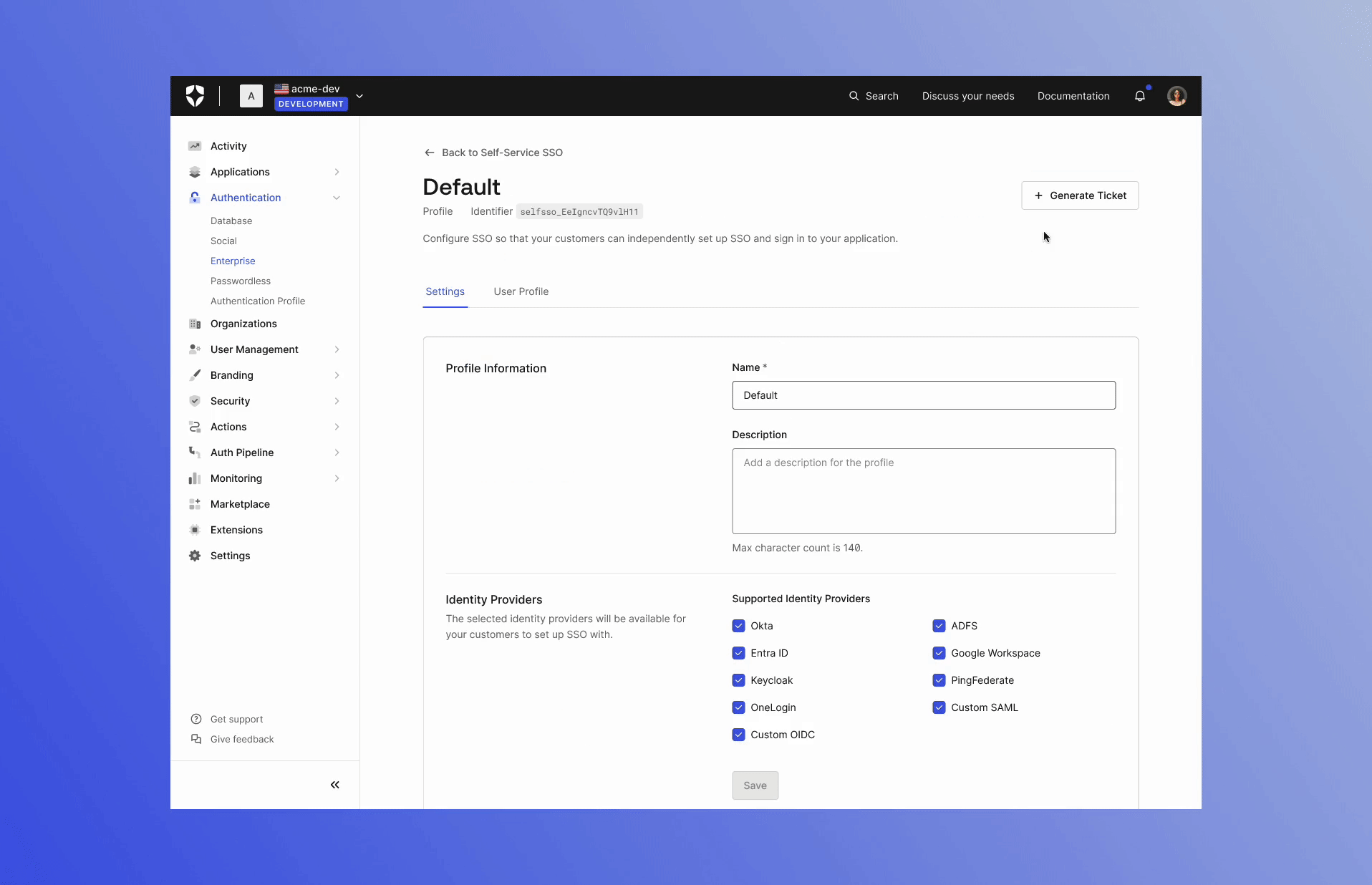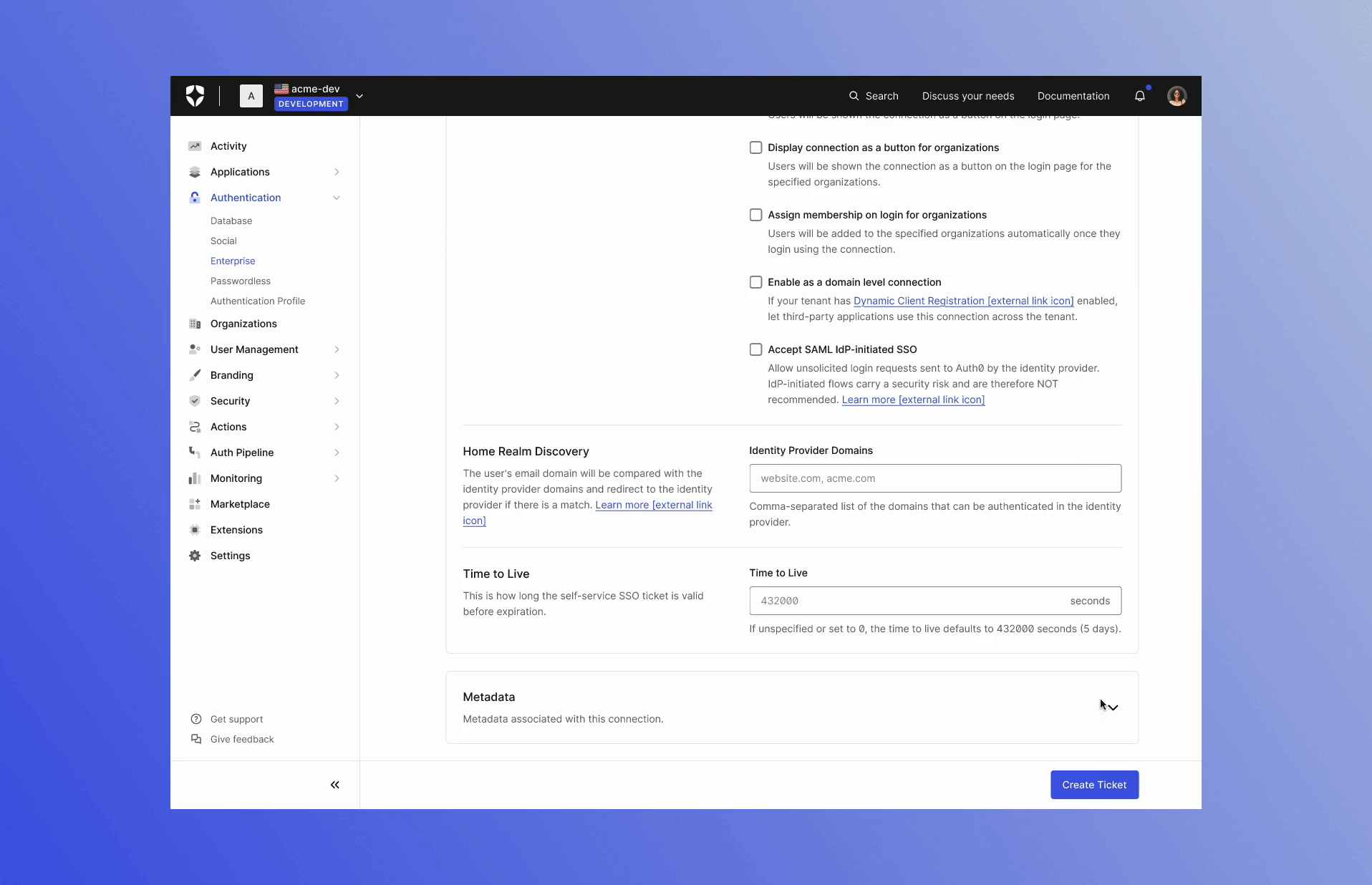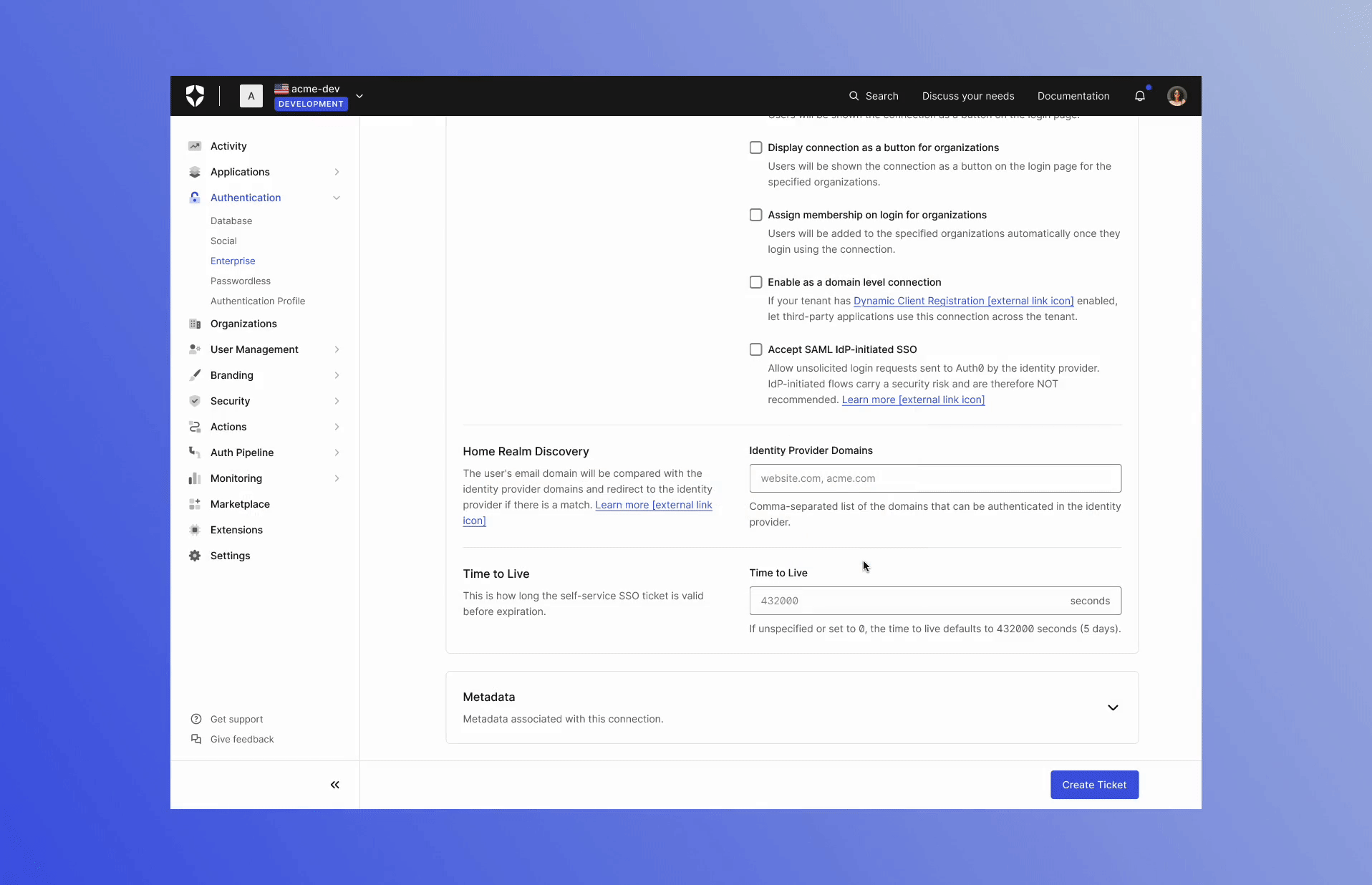
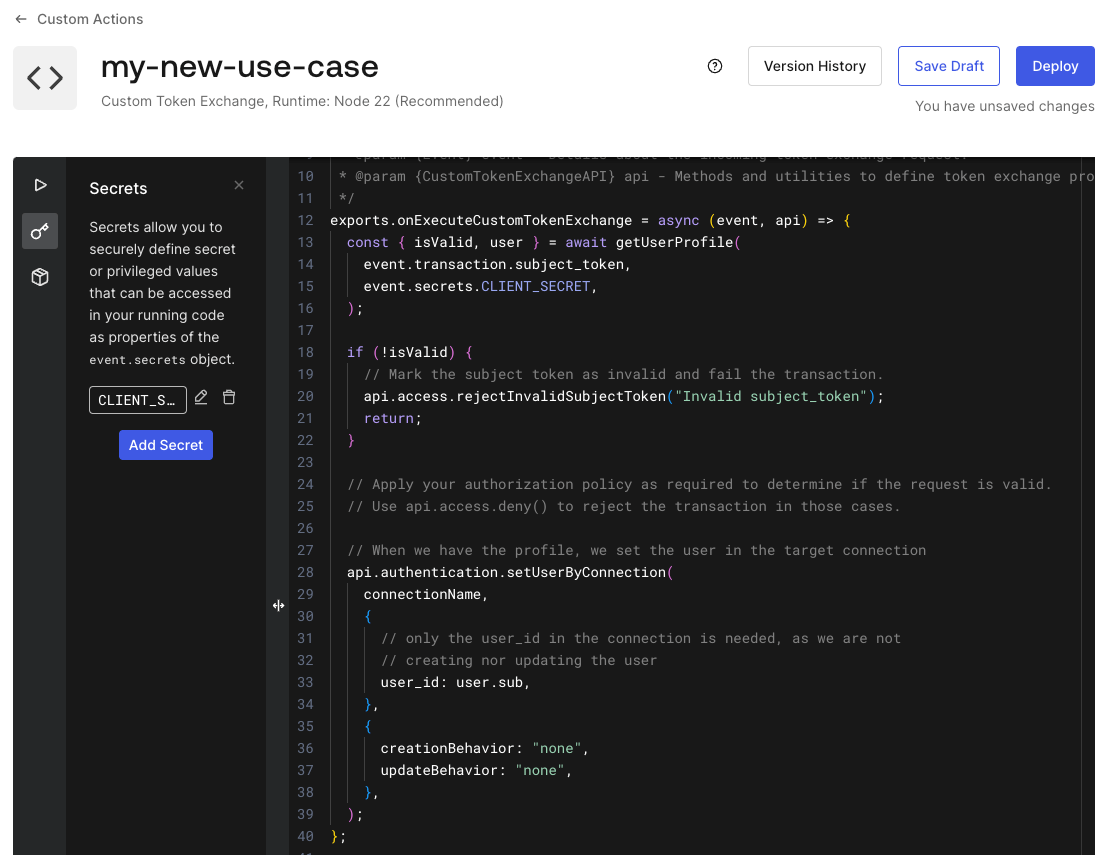







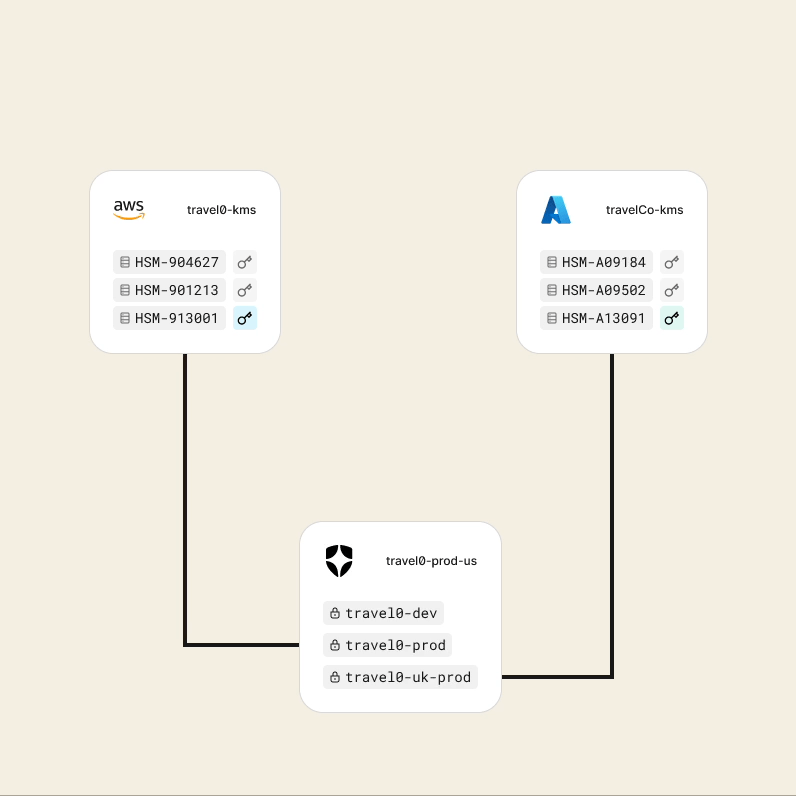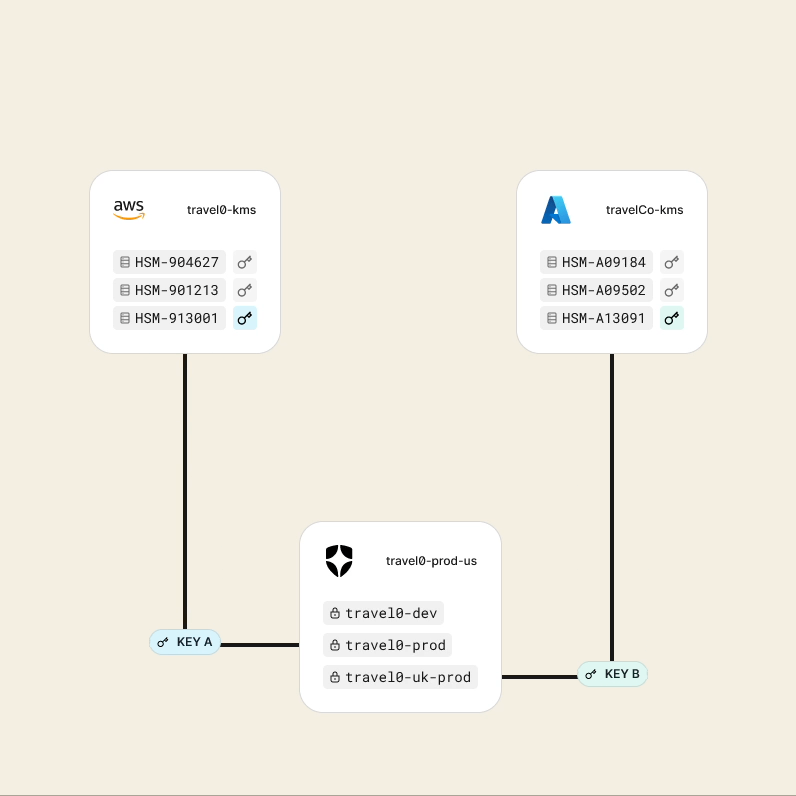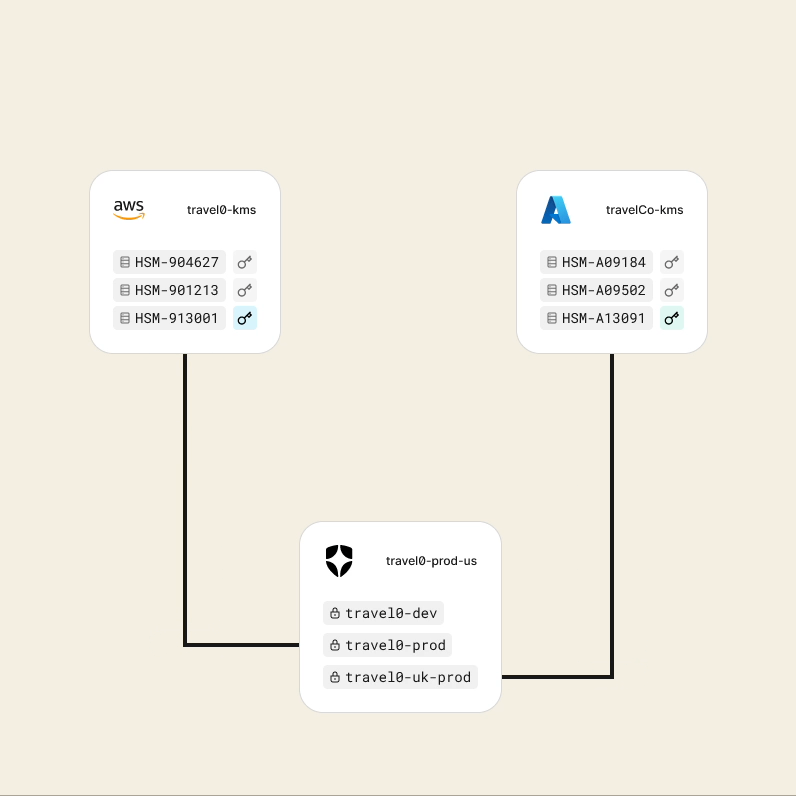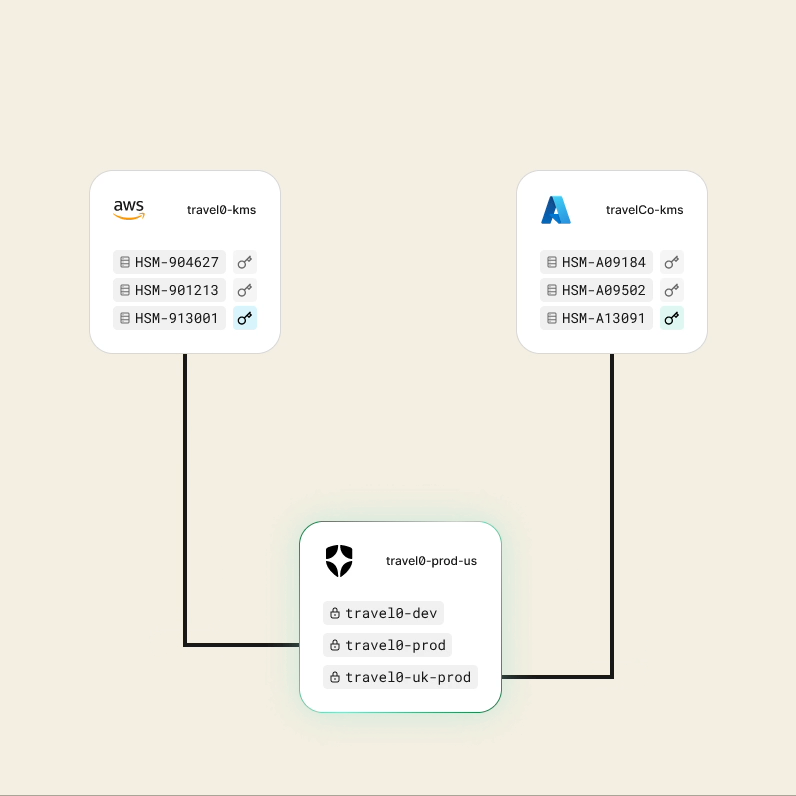

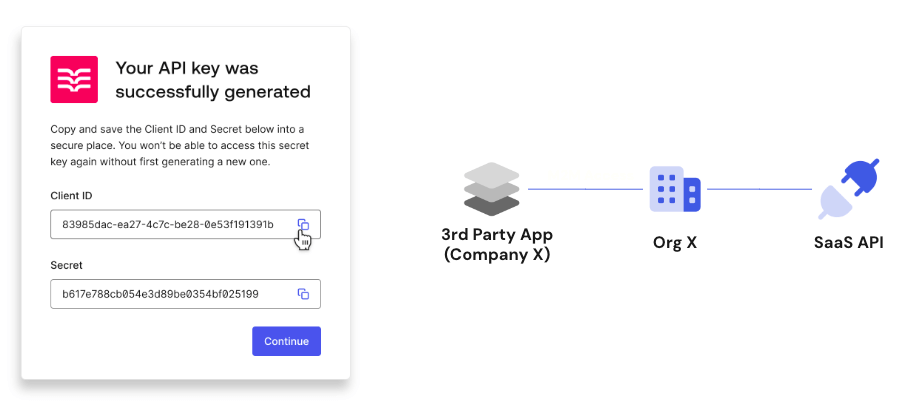
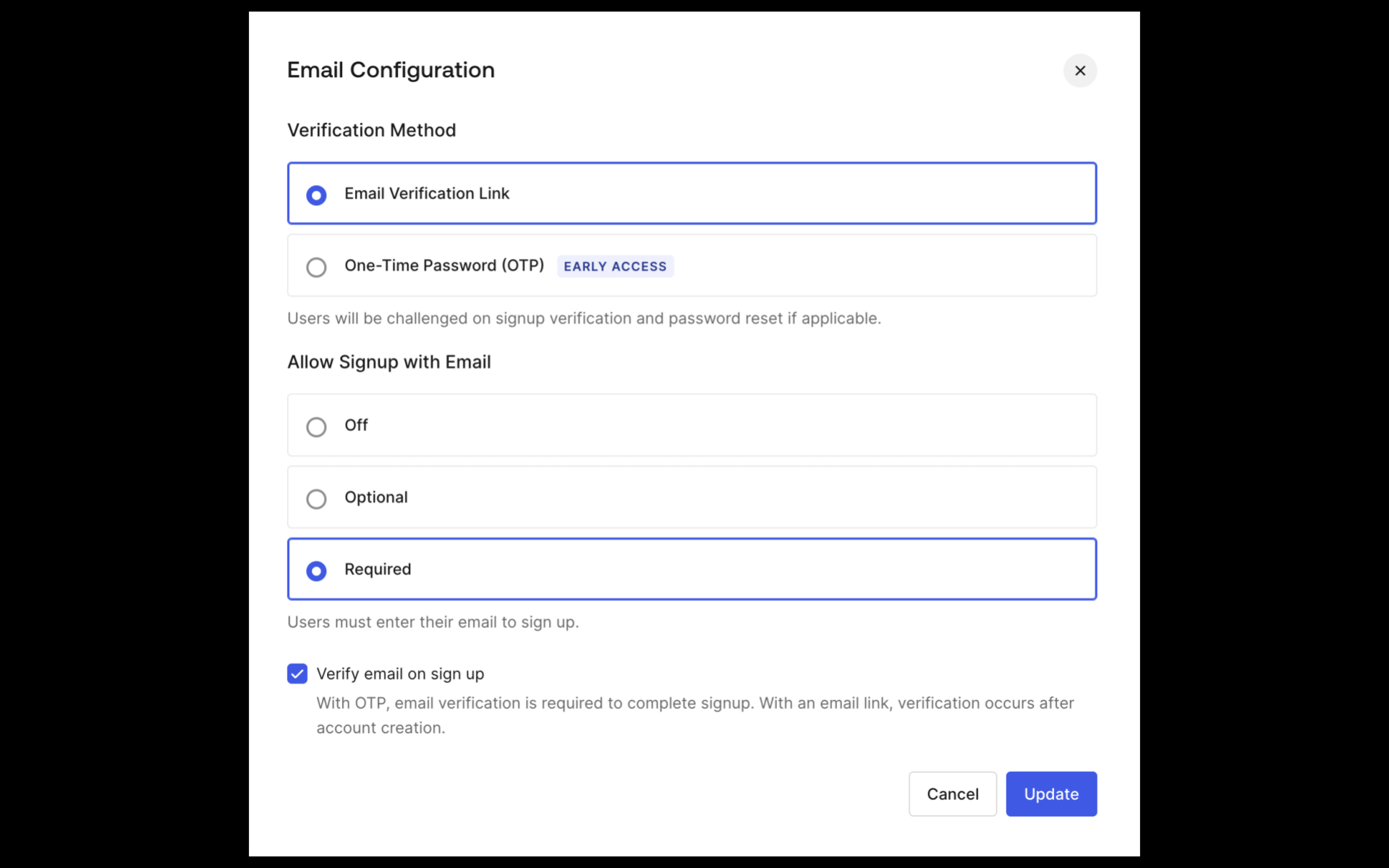

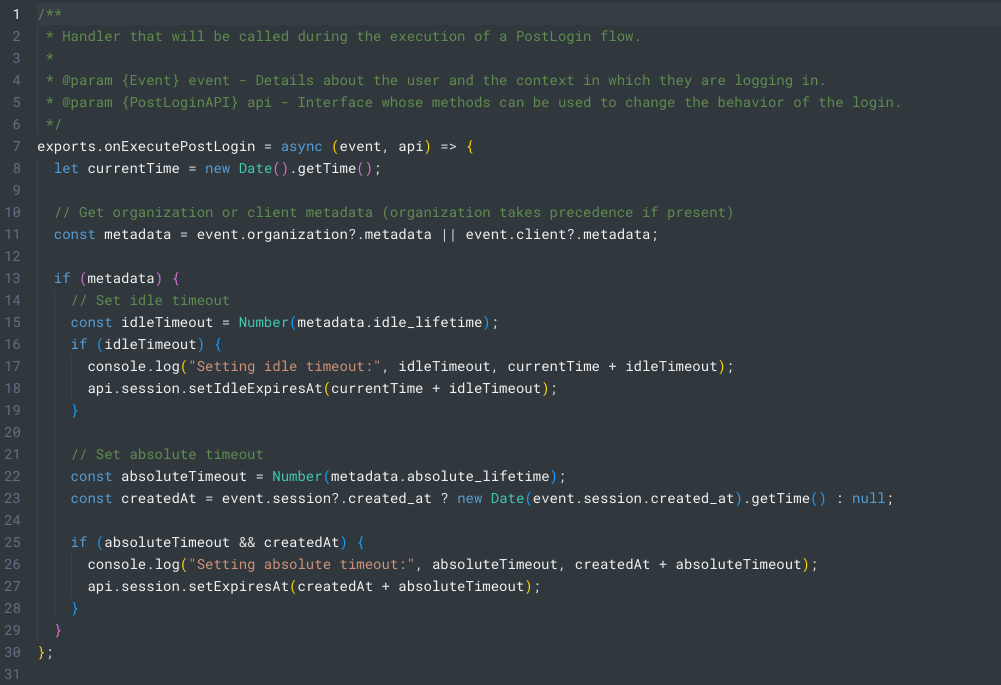




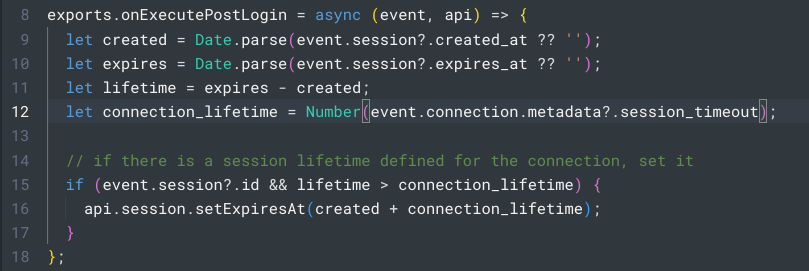


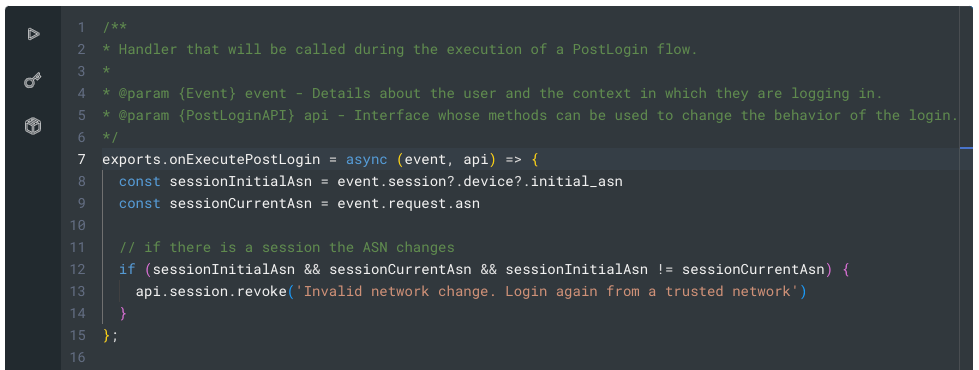
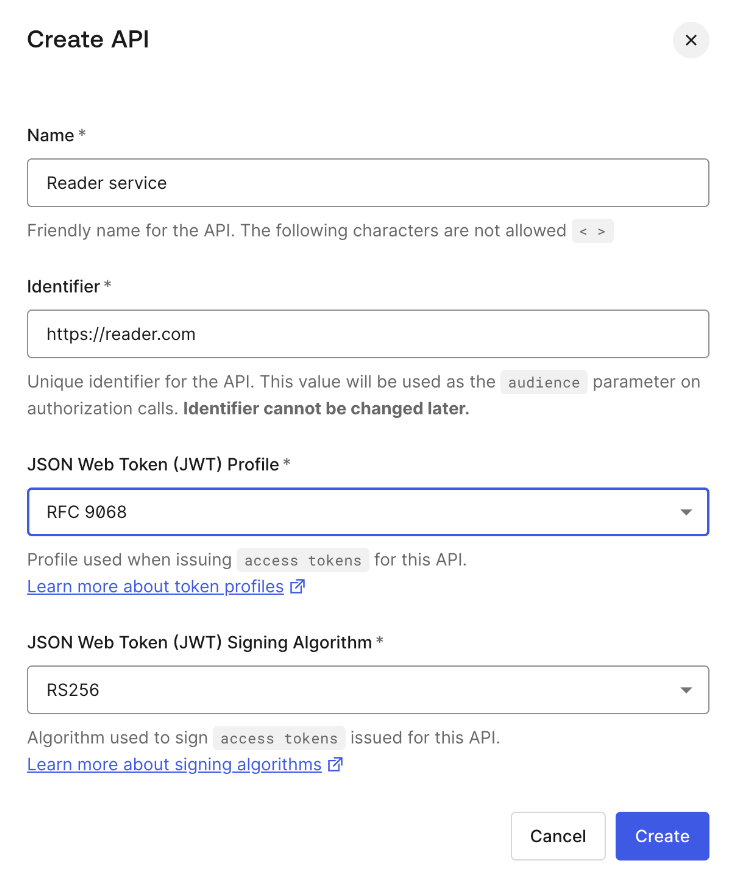


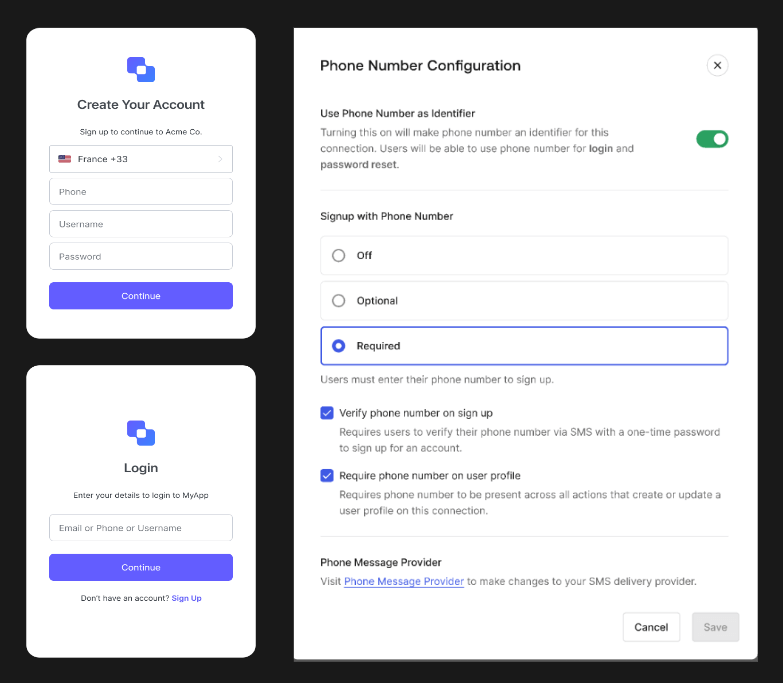
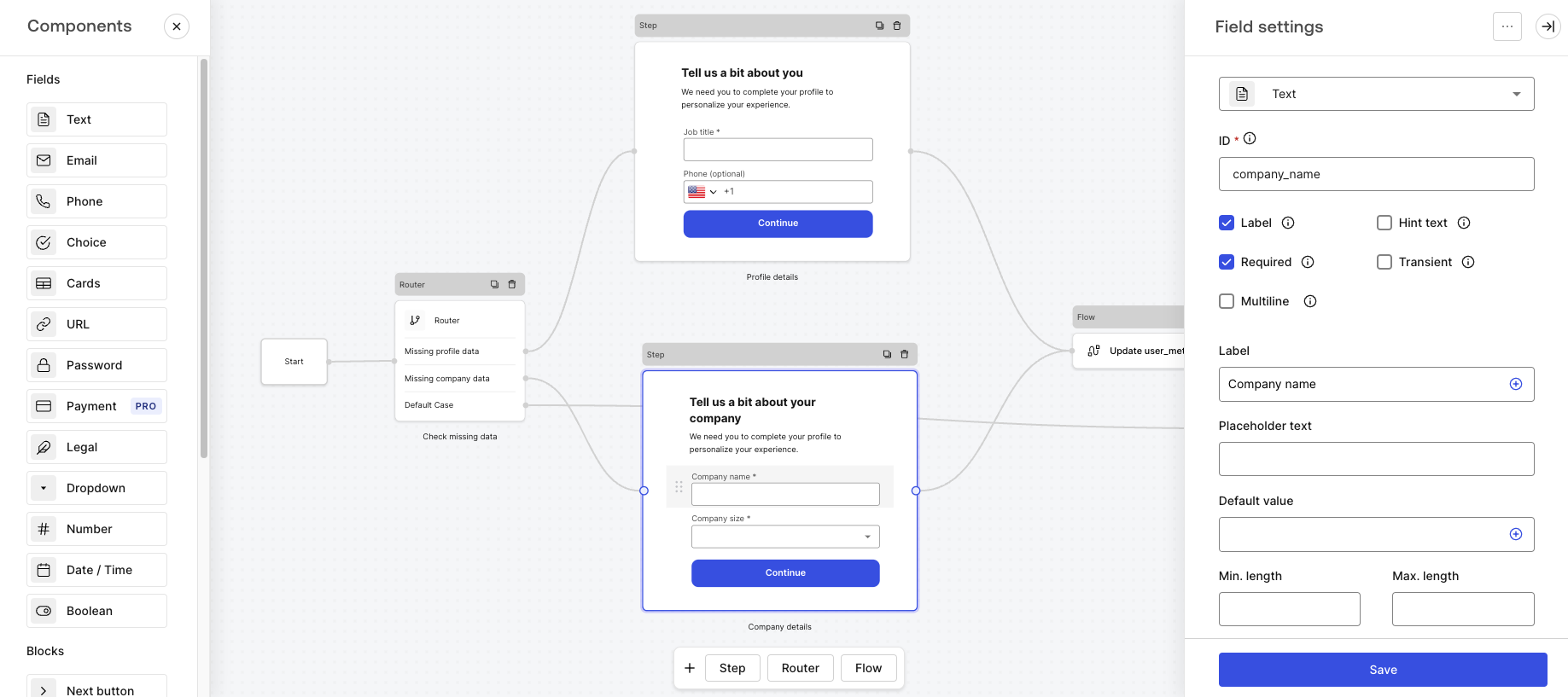


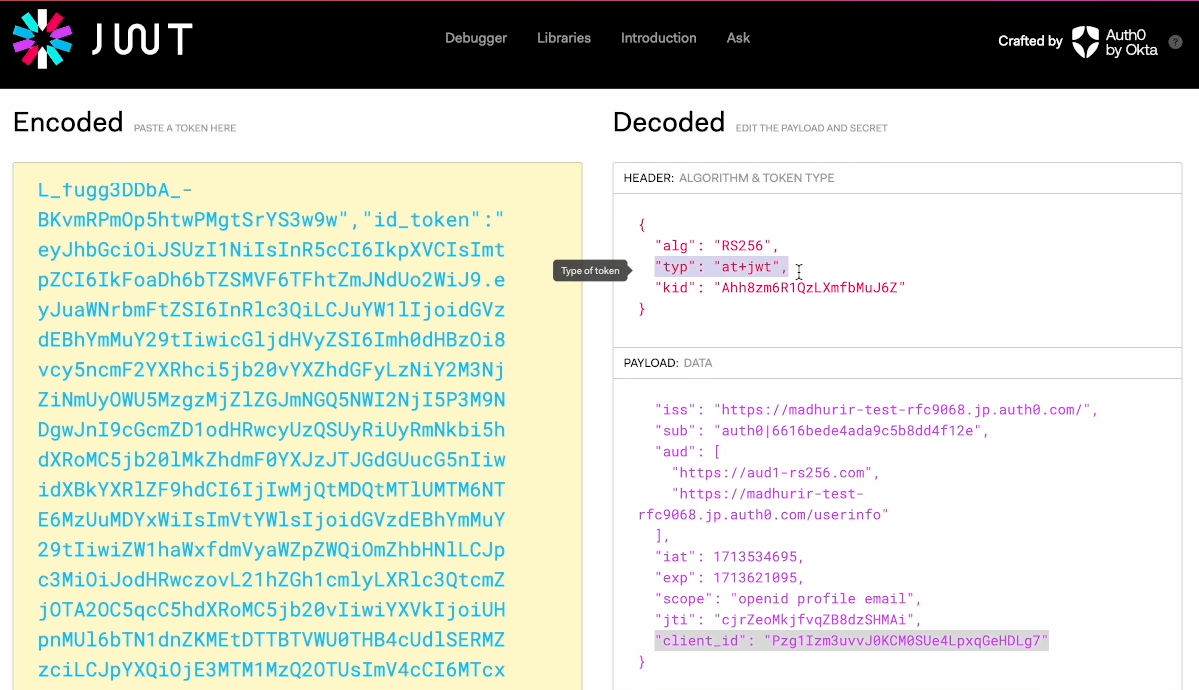
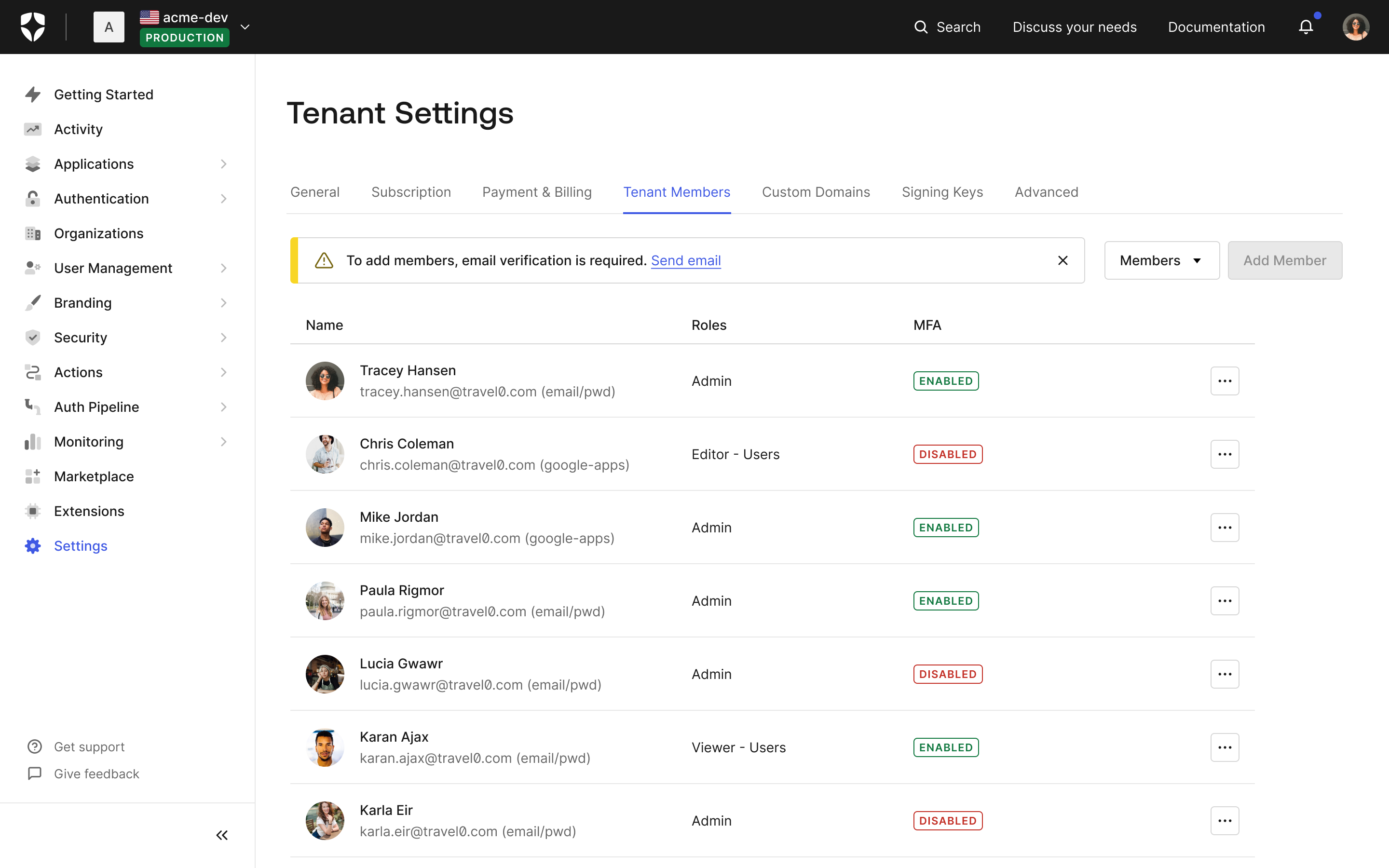
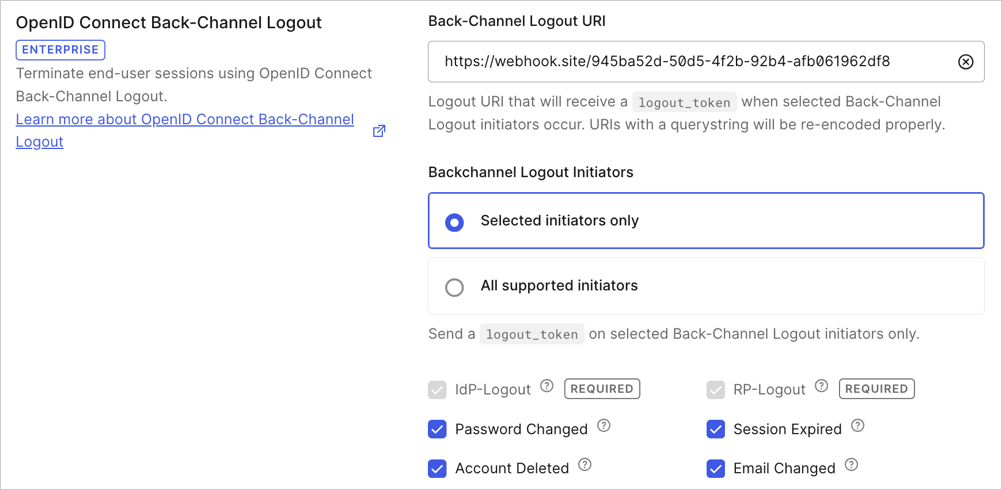
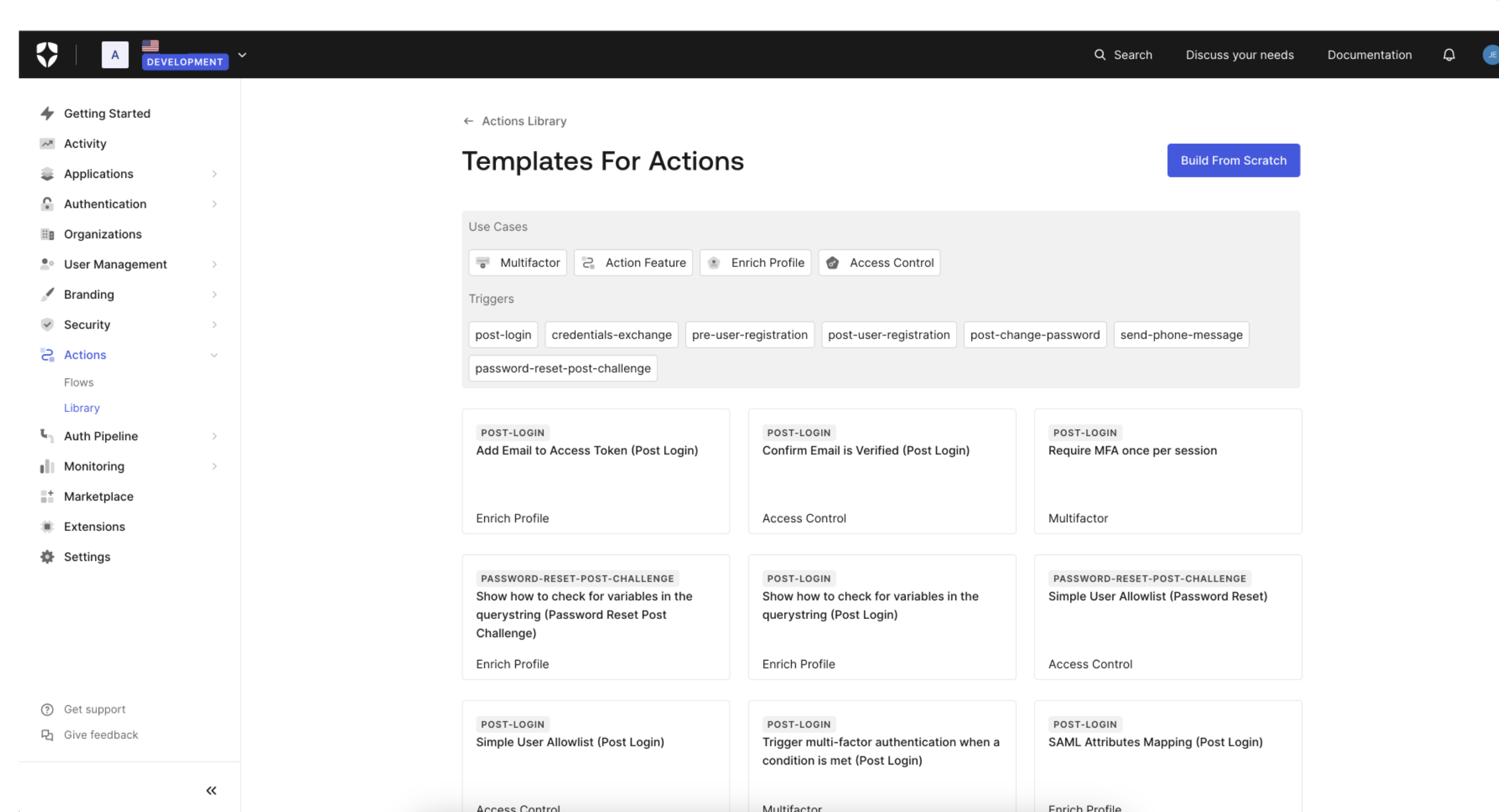 You can learn more about Templates for Actions from our
You can learn more about Templates for Actions from our 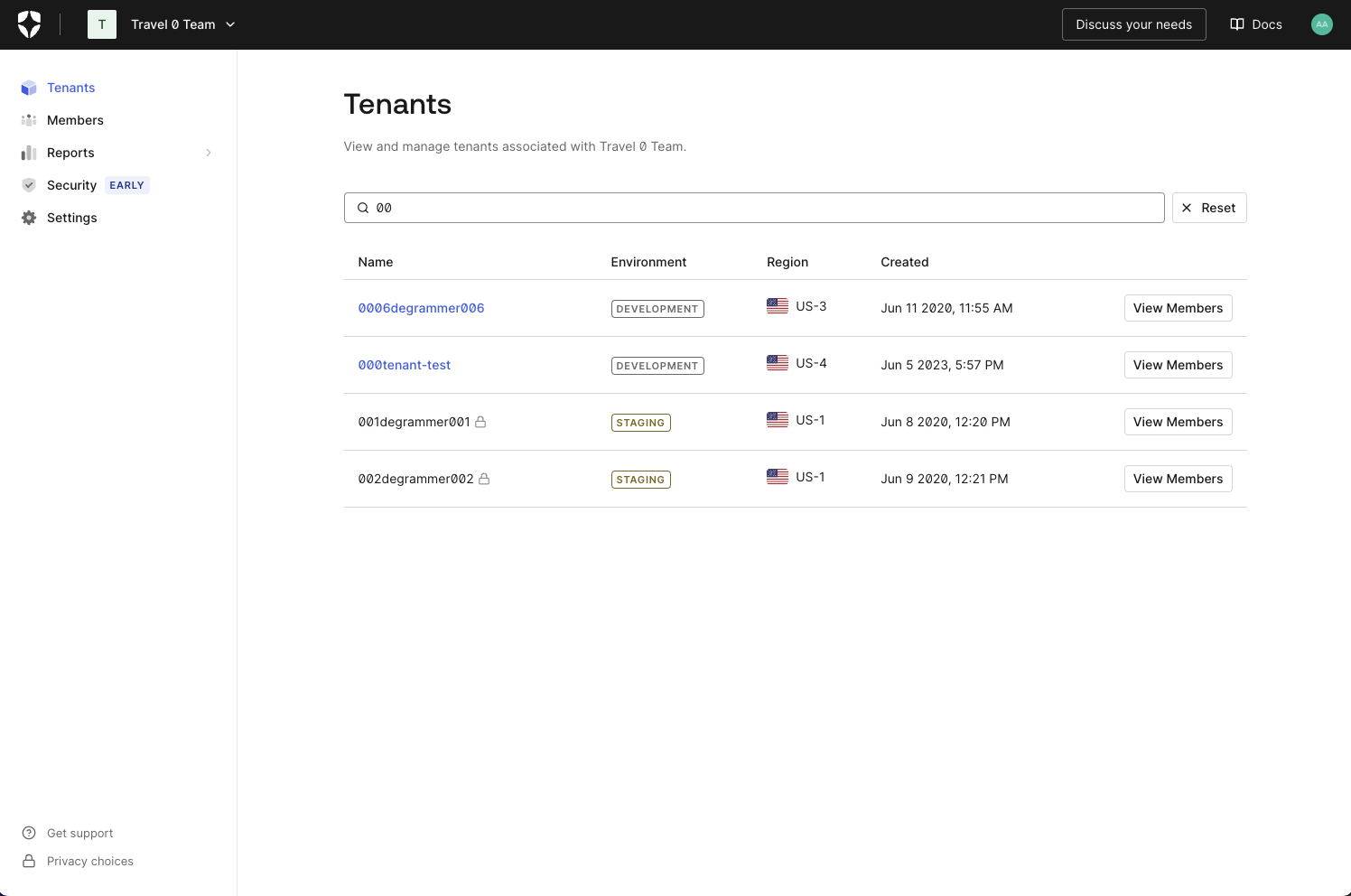
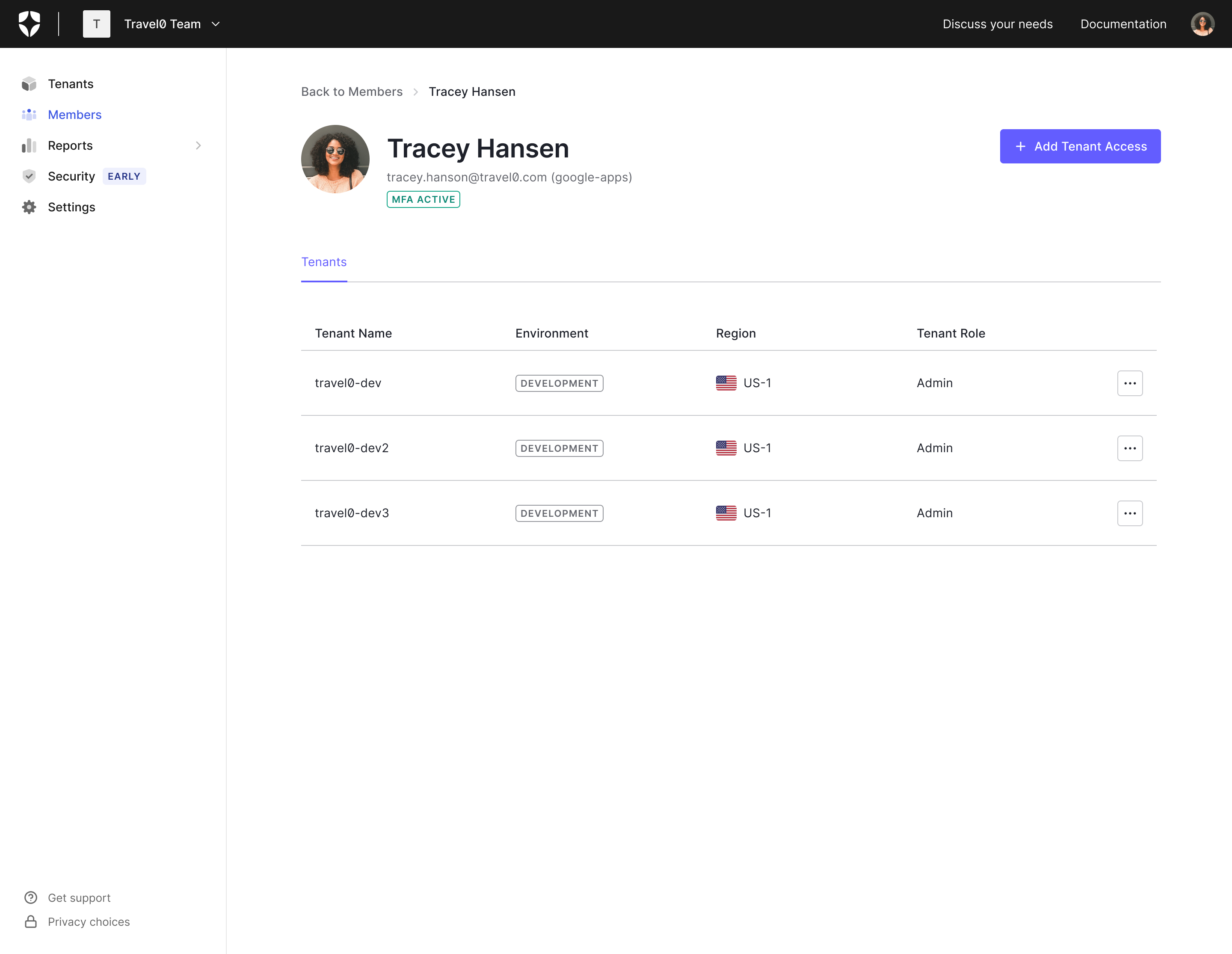
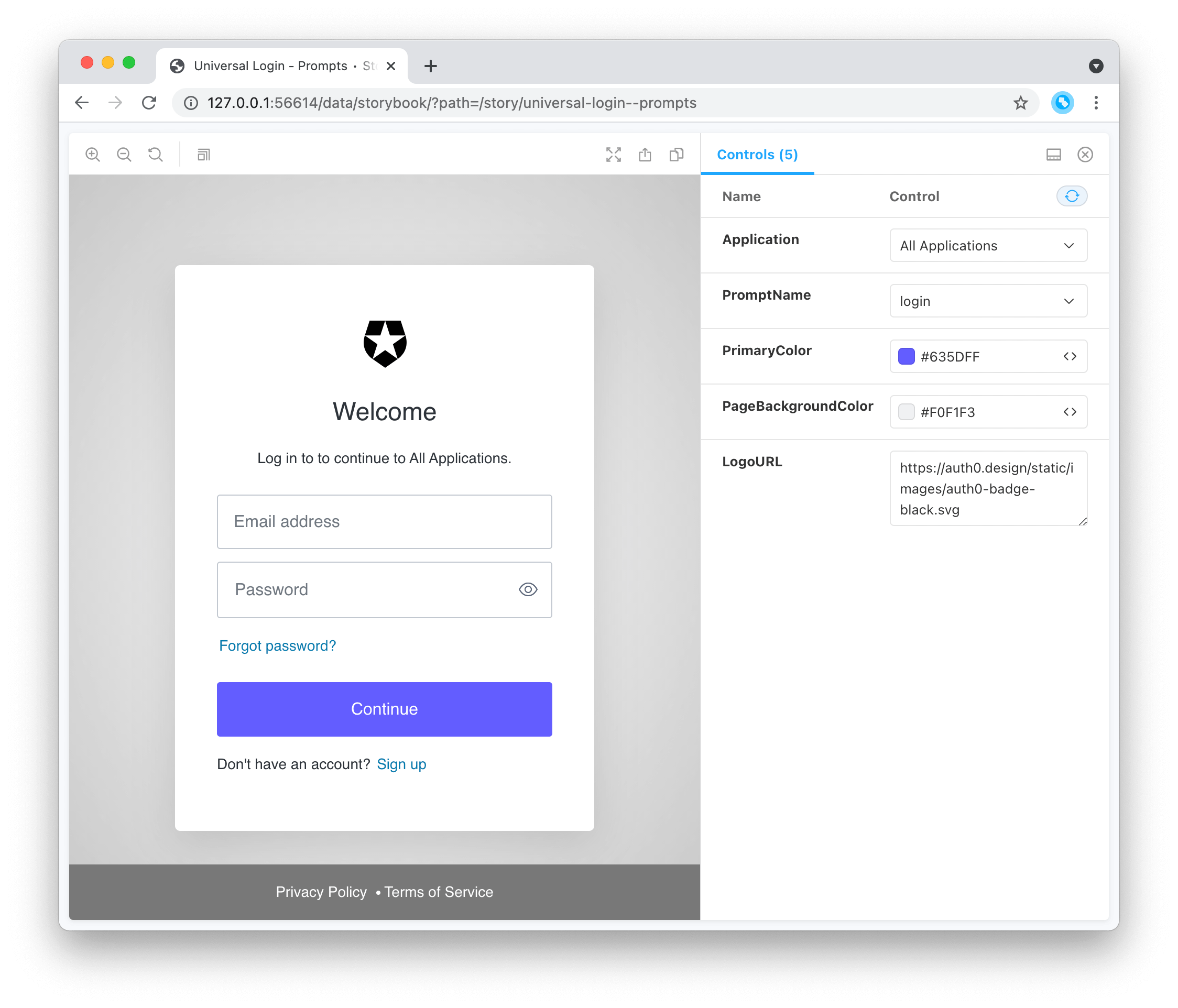
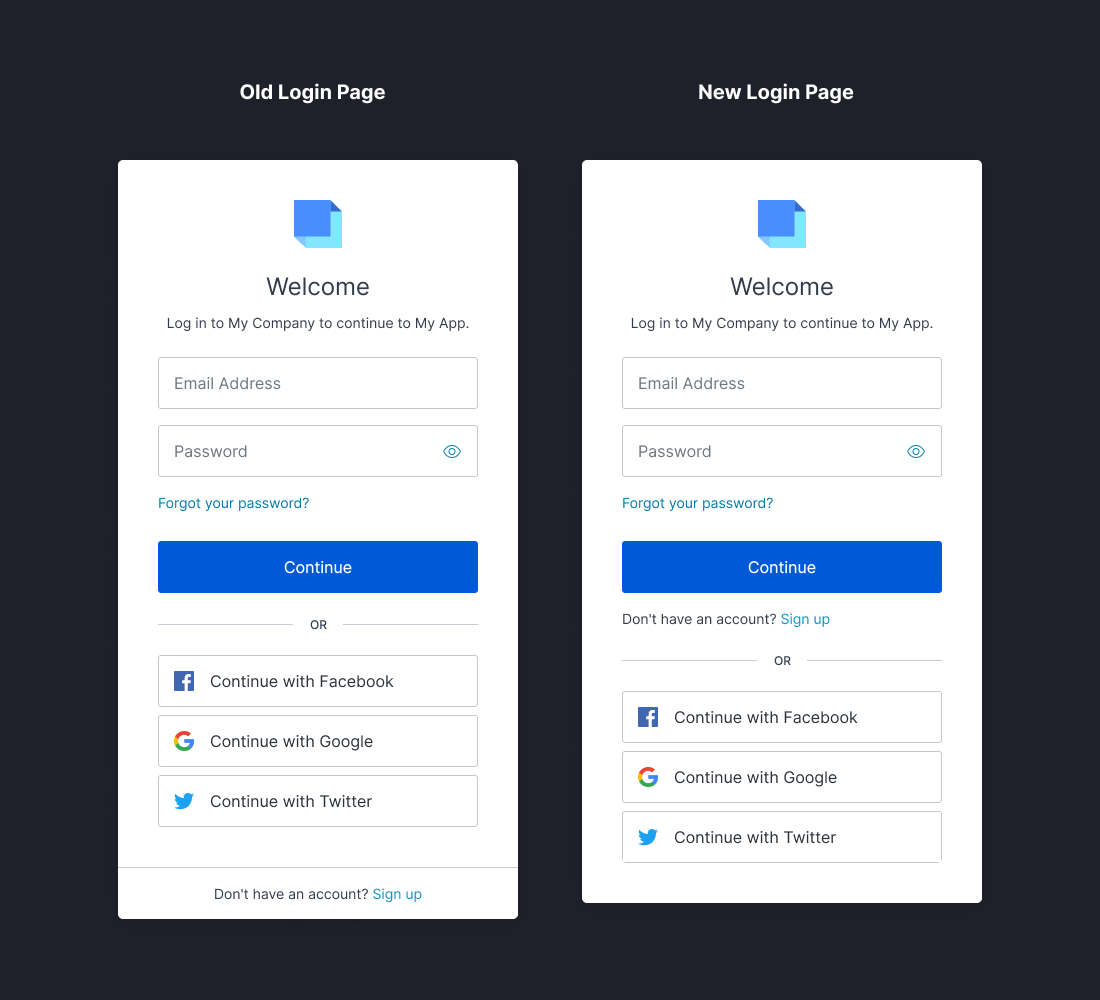
 Did someone order up one Dark Mode Browser extra Hot! Feel free to dim the lights; Teams Dashboard now supports dark mode.
Did someone order up one Dark Mode Browser extra Hot! Feel free to dim the lights; Teams Dashboard now supports dark mode.
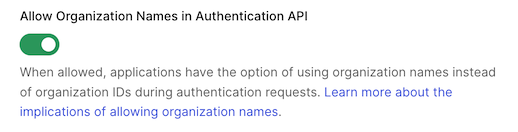
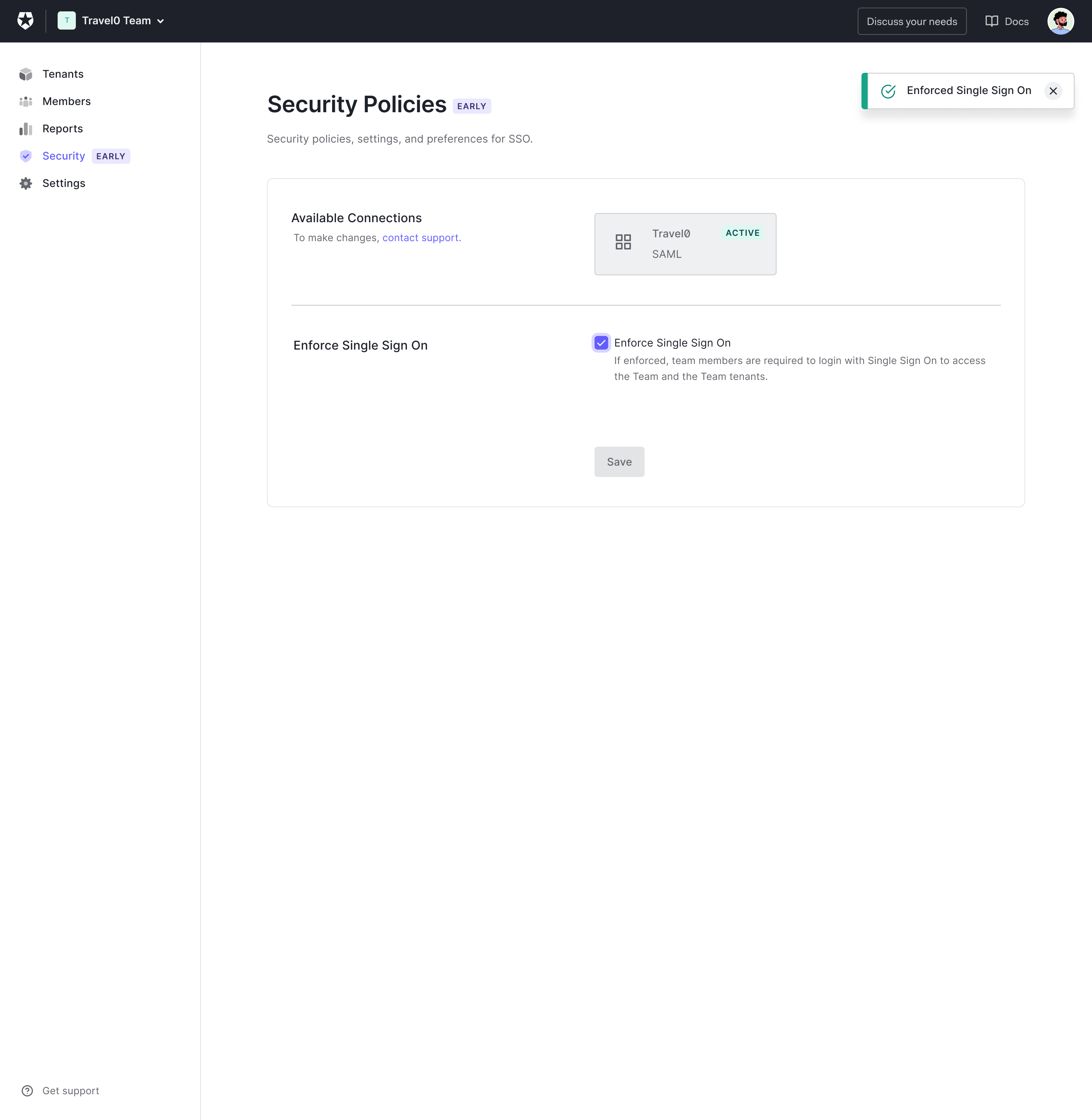
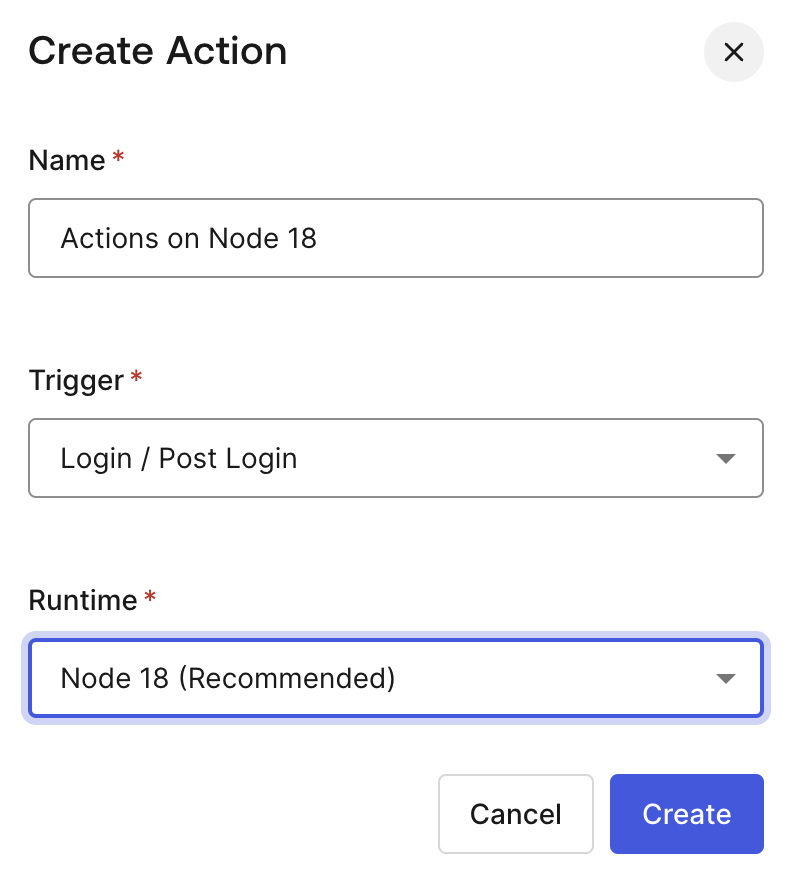
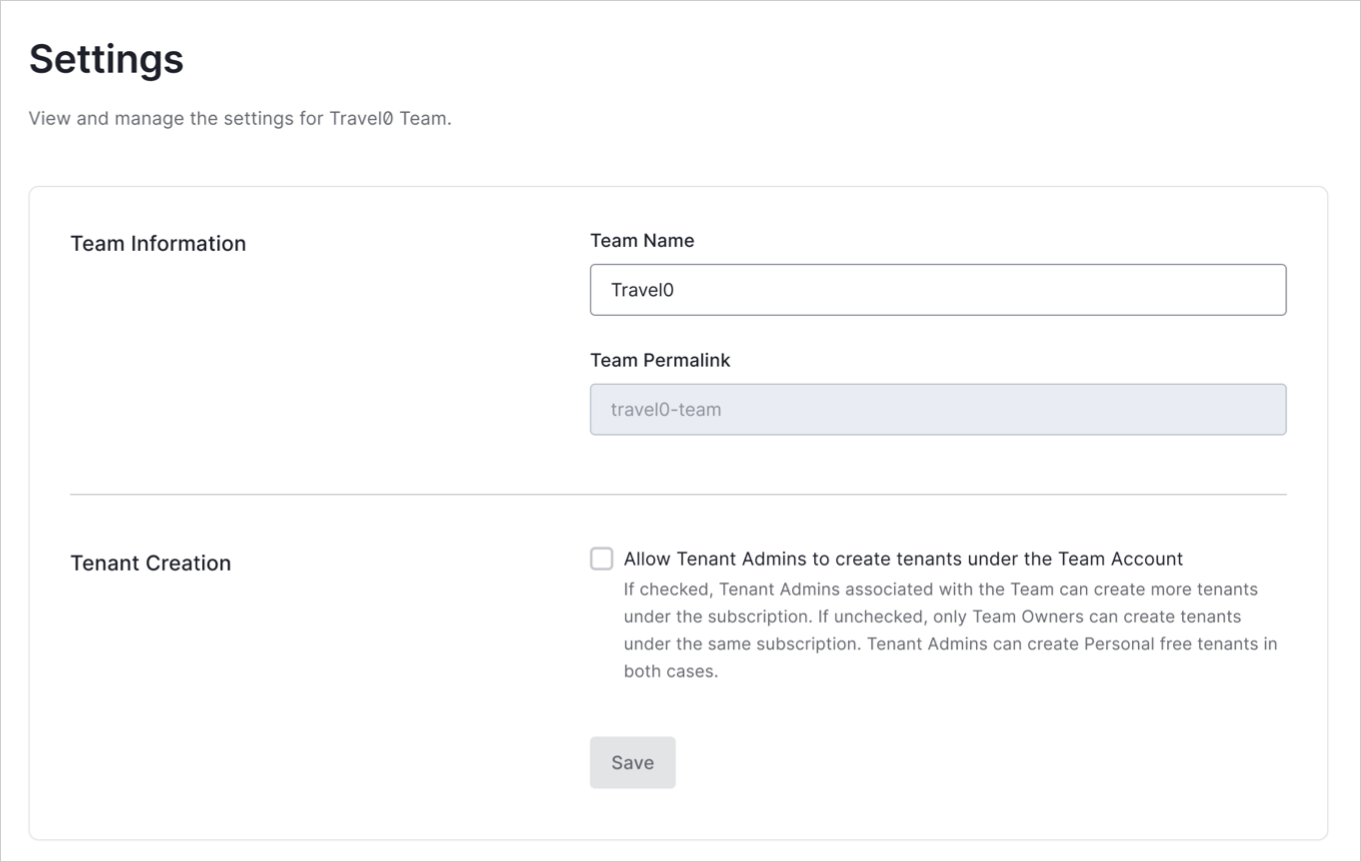
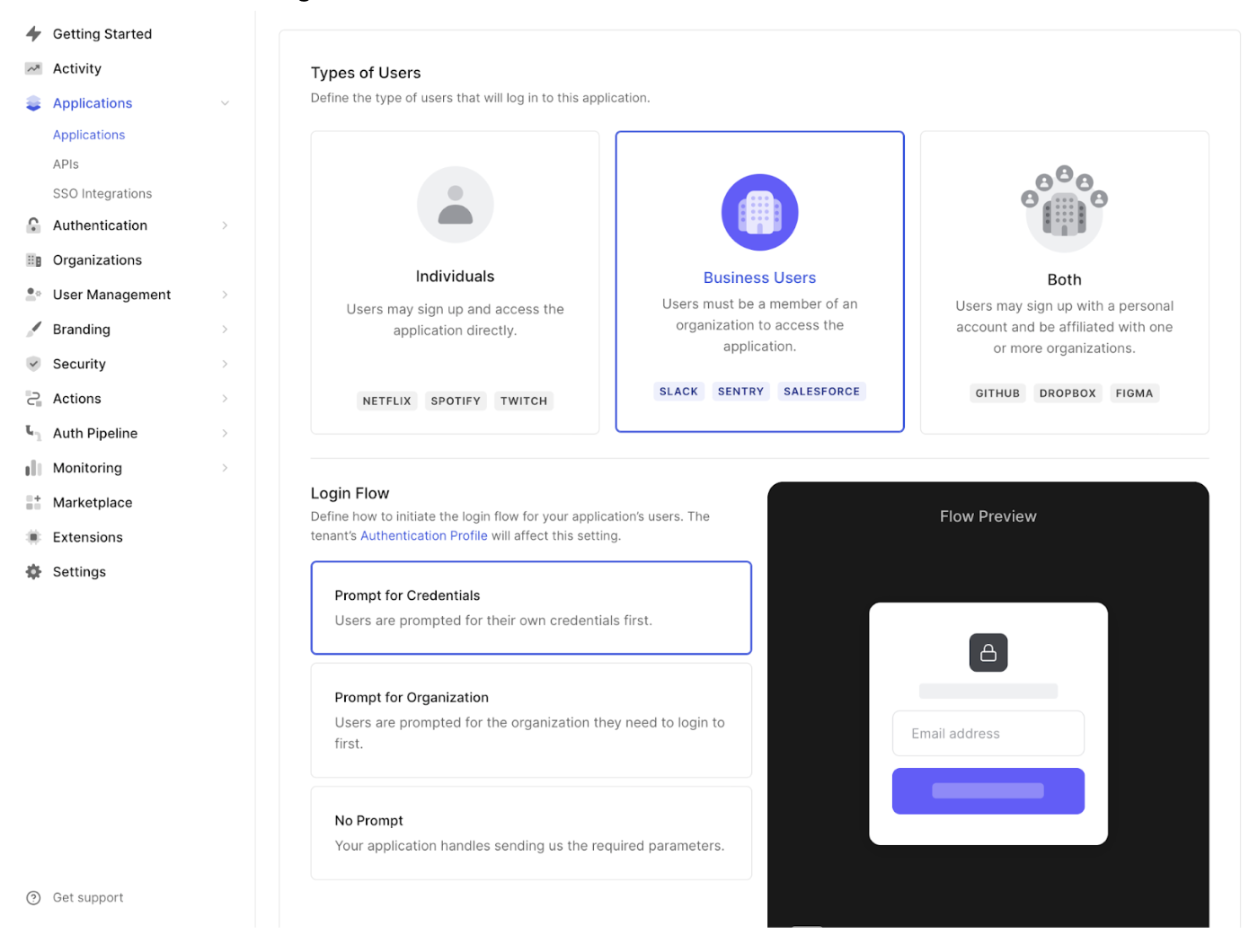
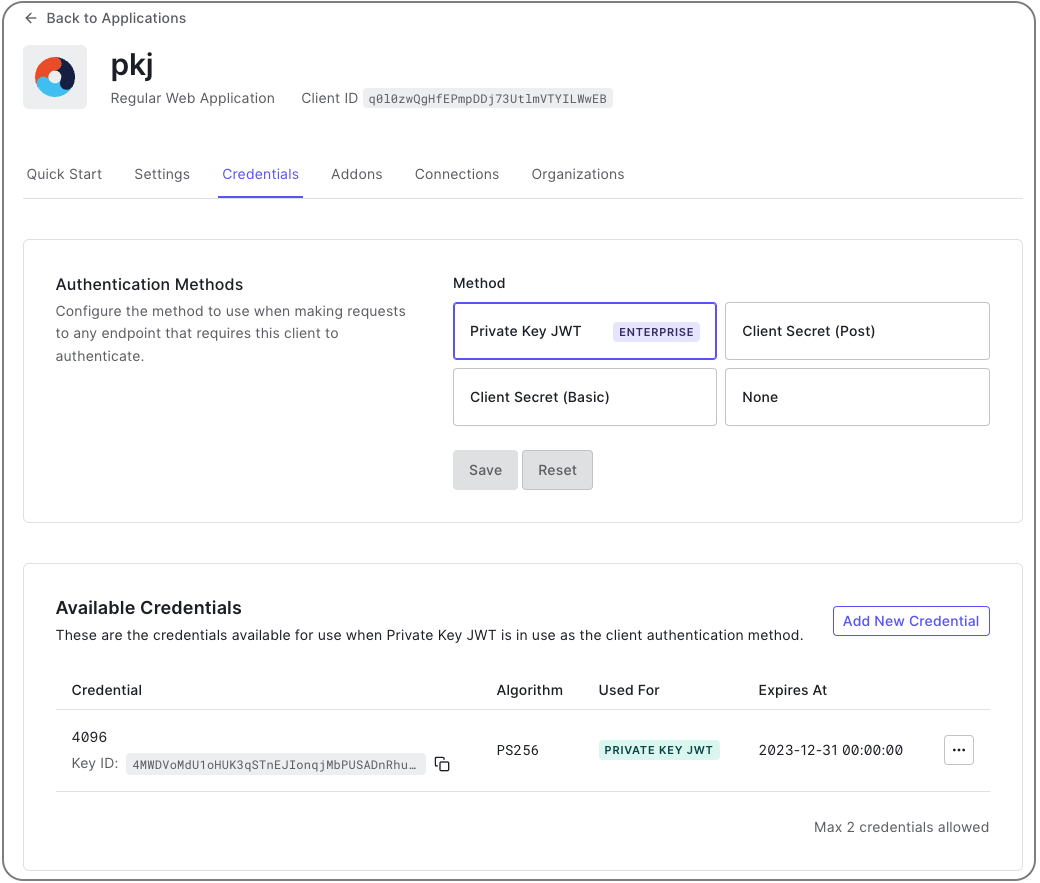
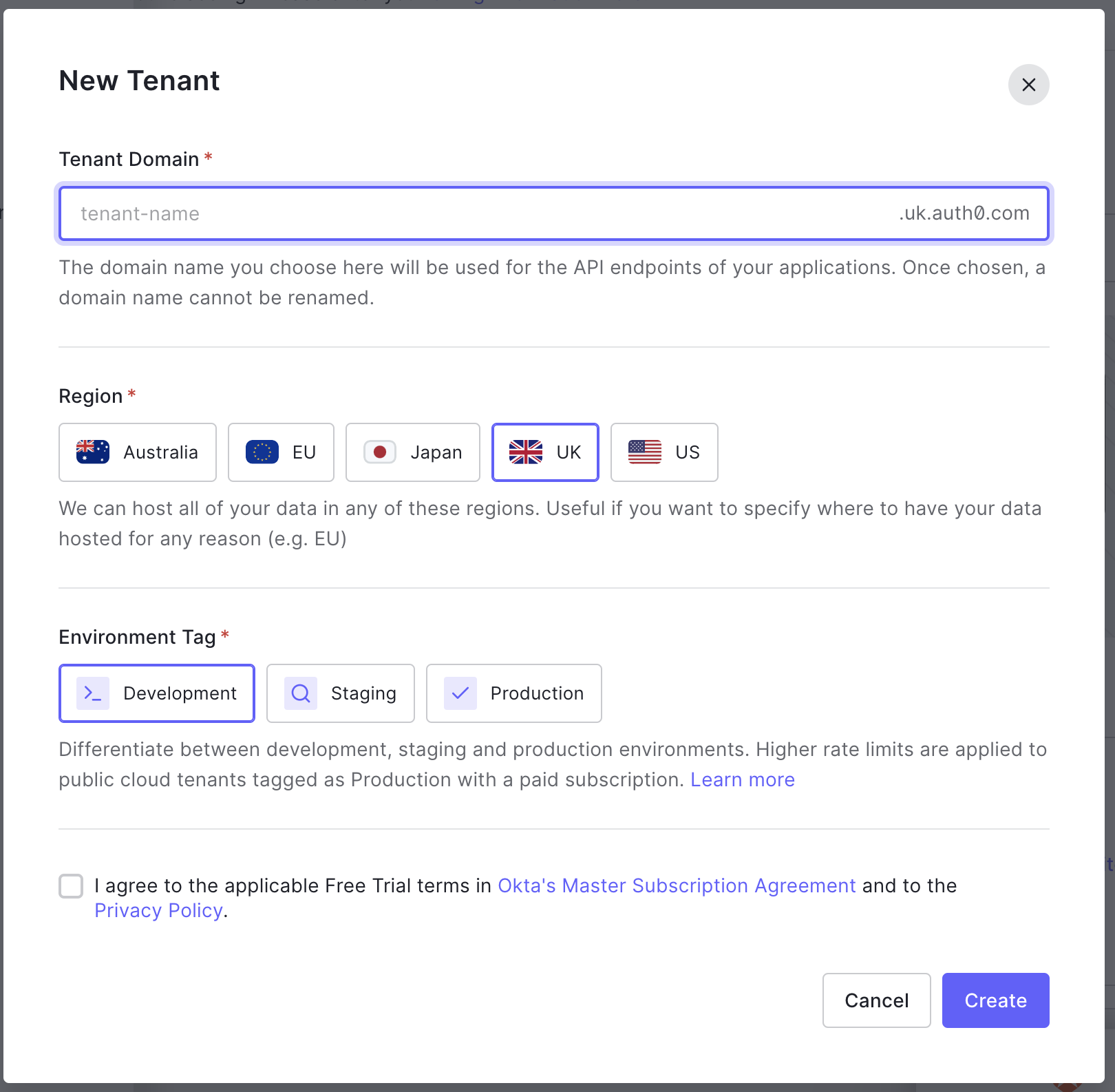
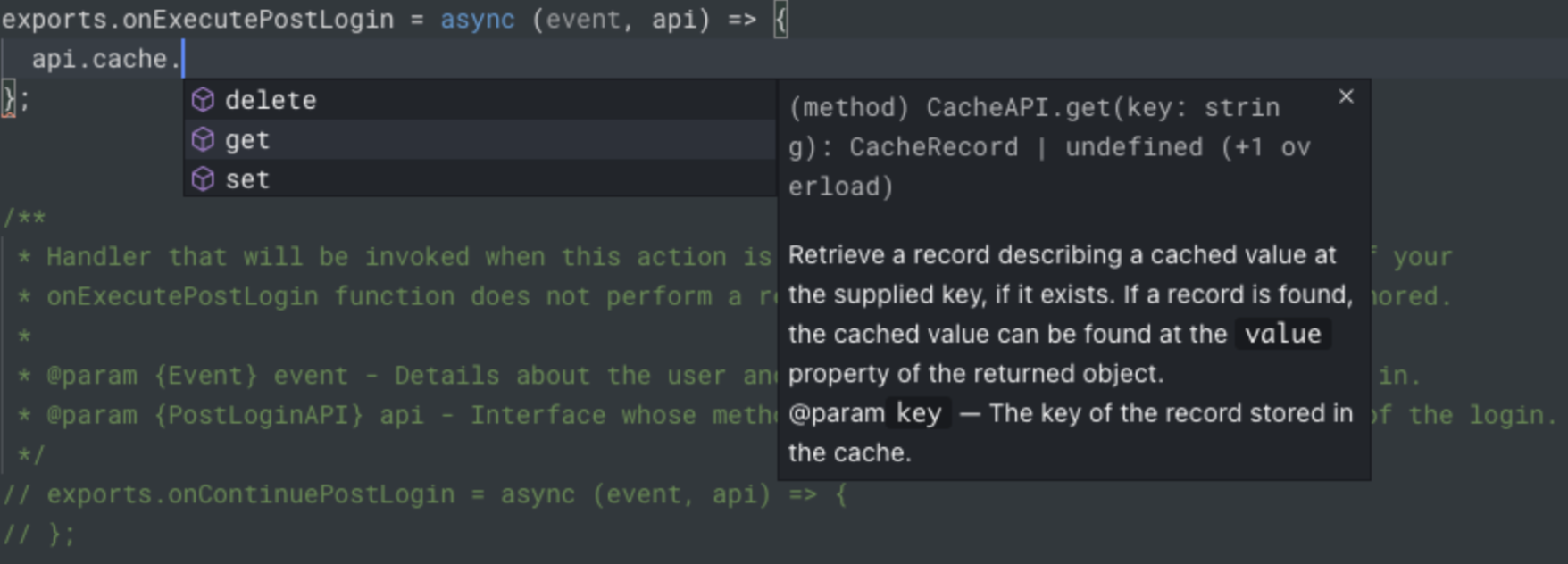
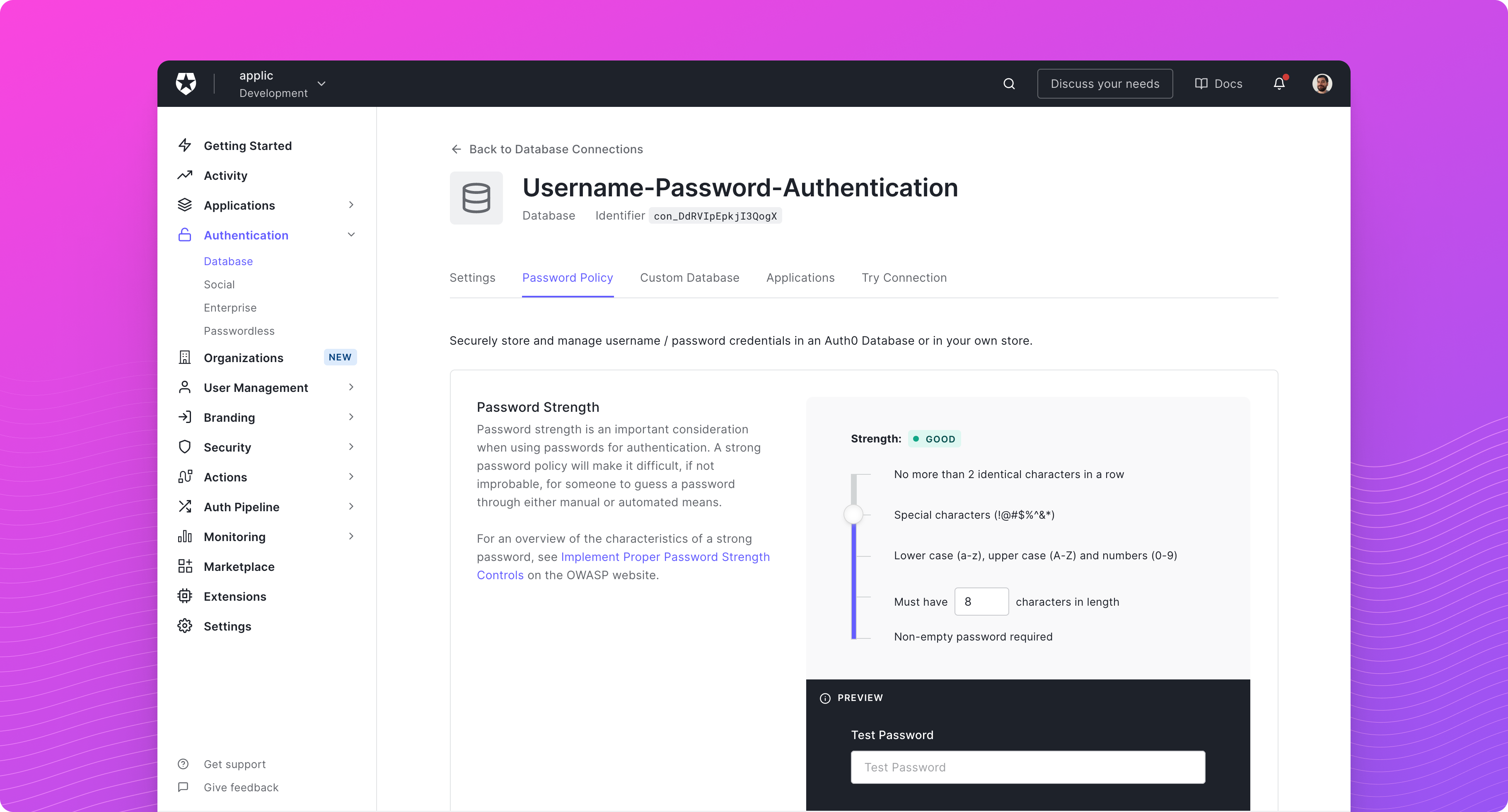
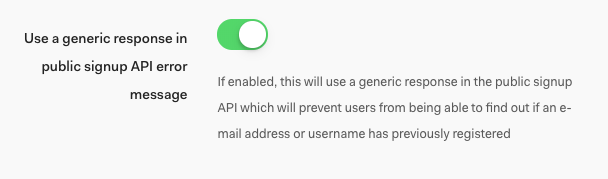
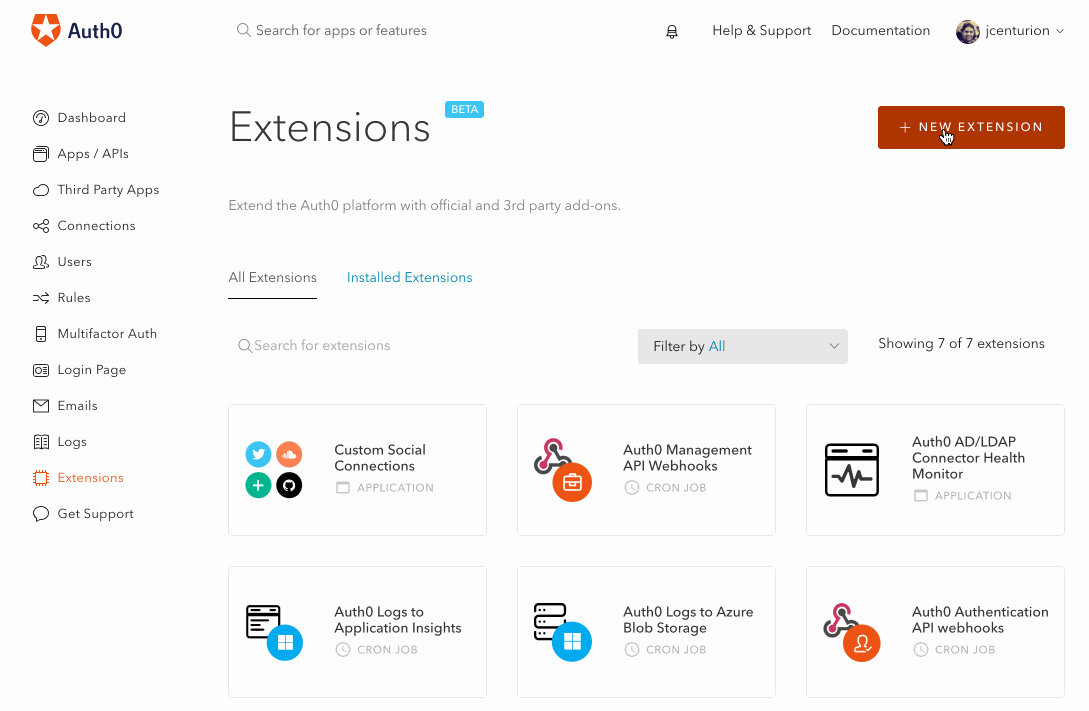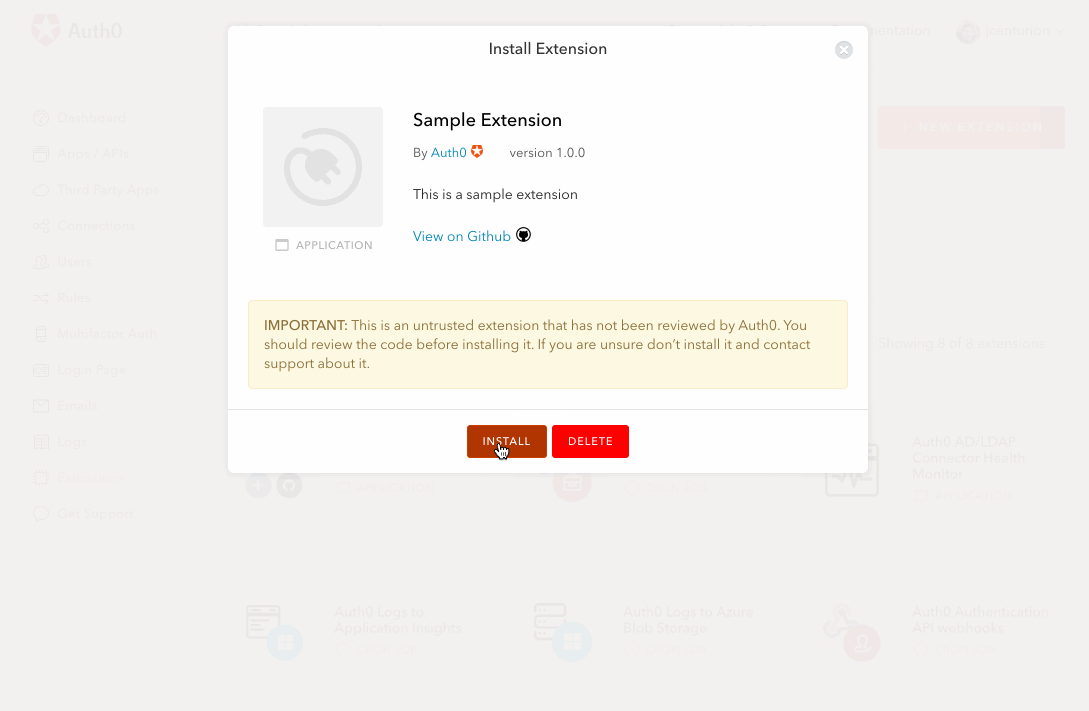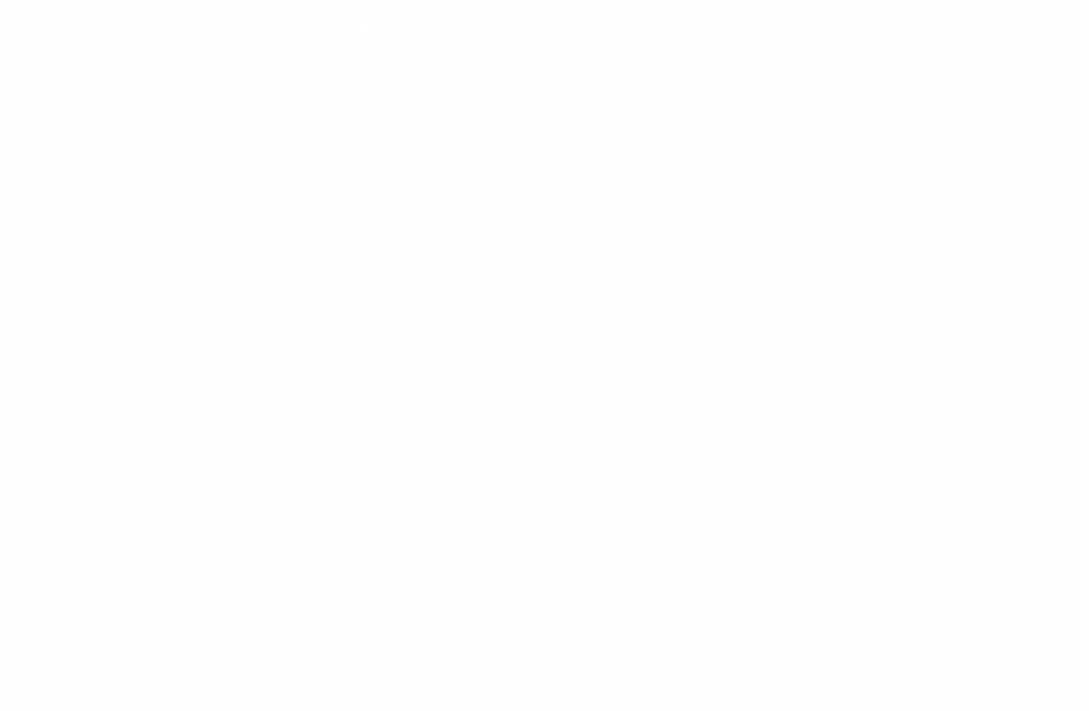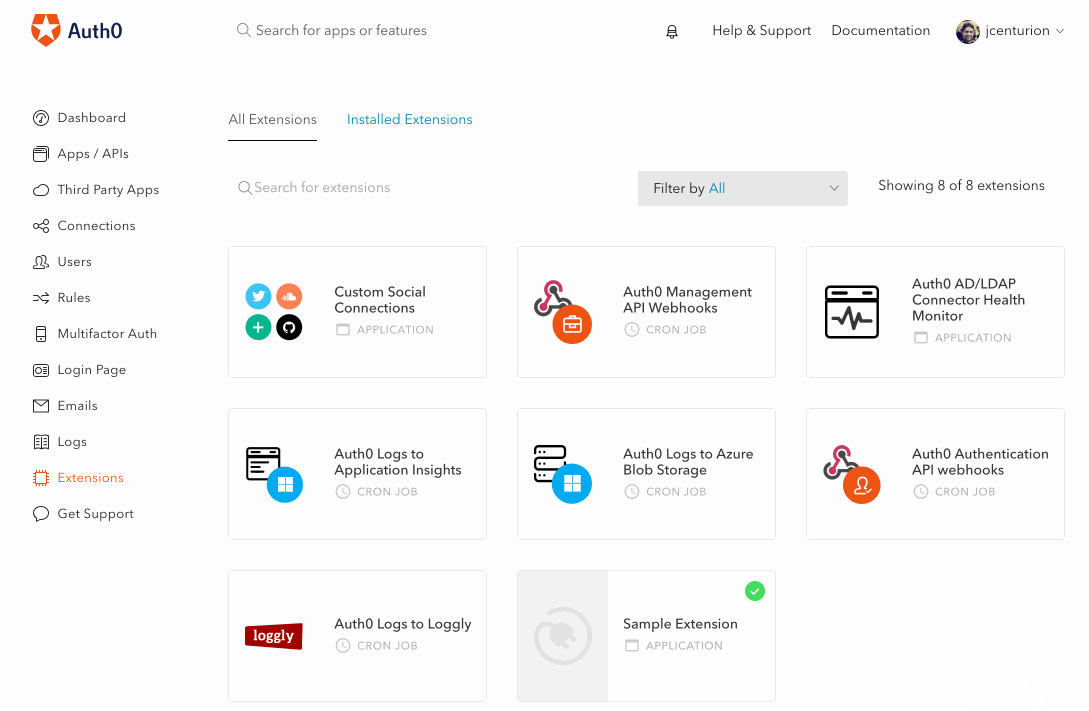
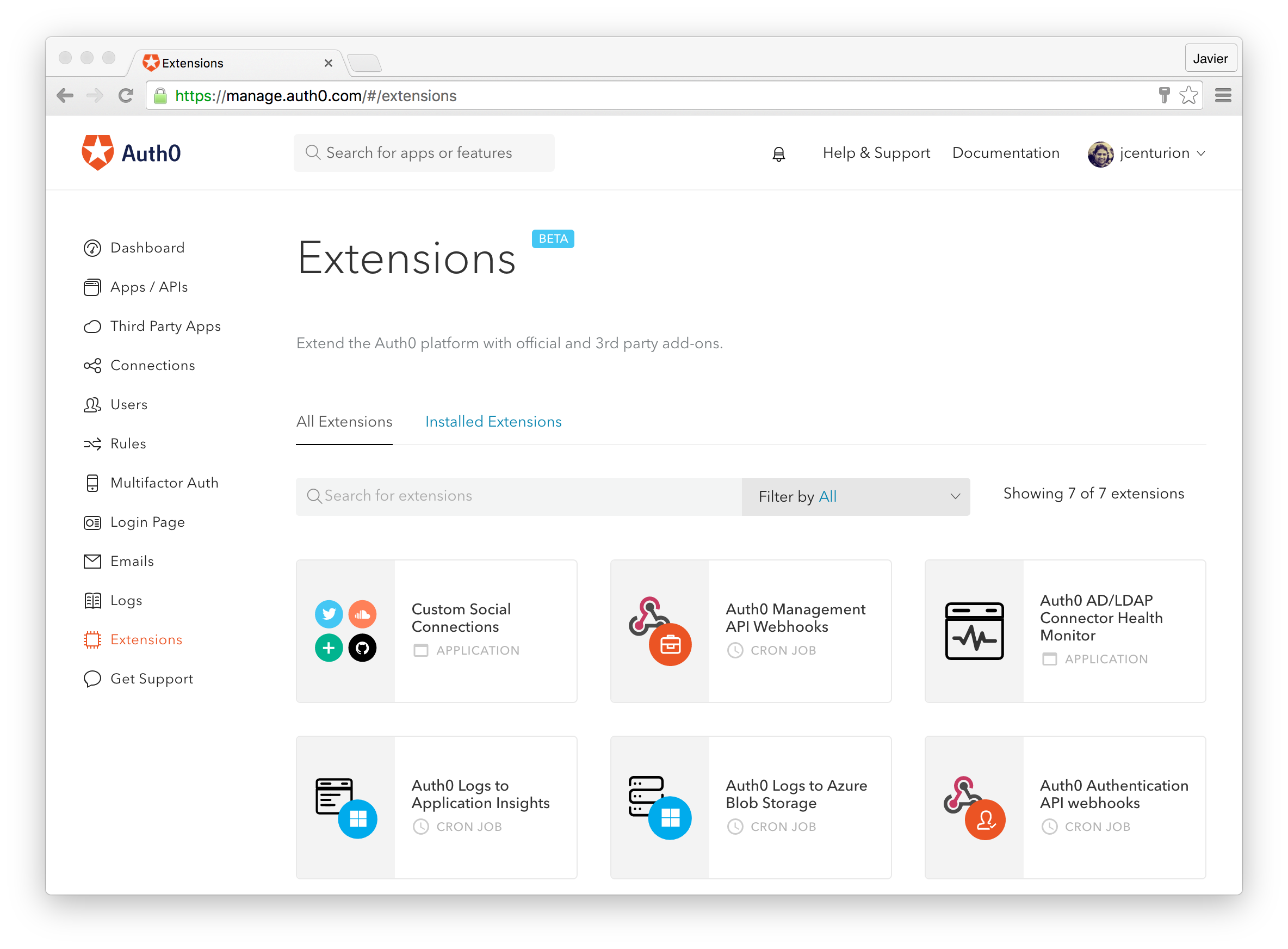
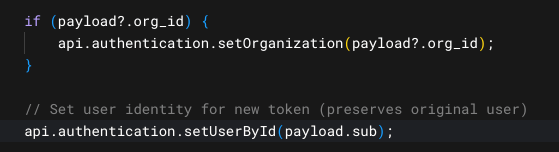
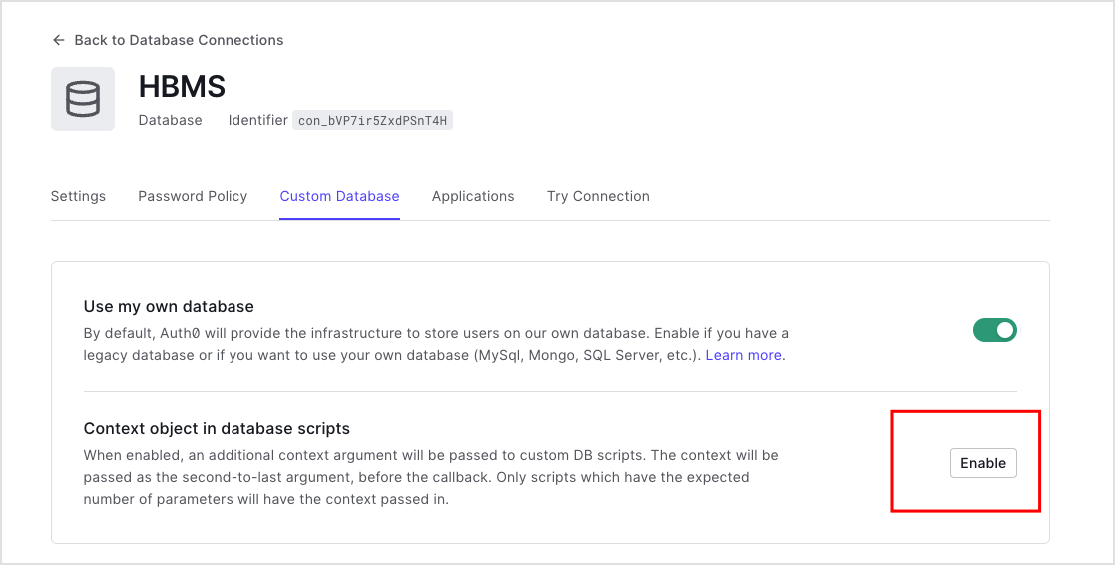 Once enabled, the custom database action script will be passed an extra parameter,
Once enabled, the custom database action script will be passed an extra parameter,