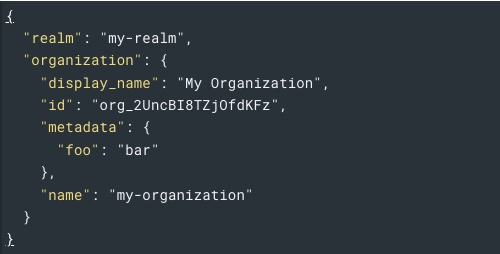
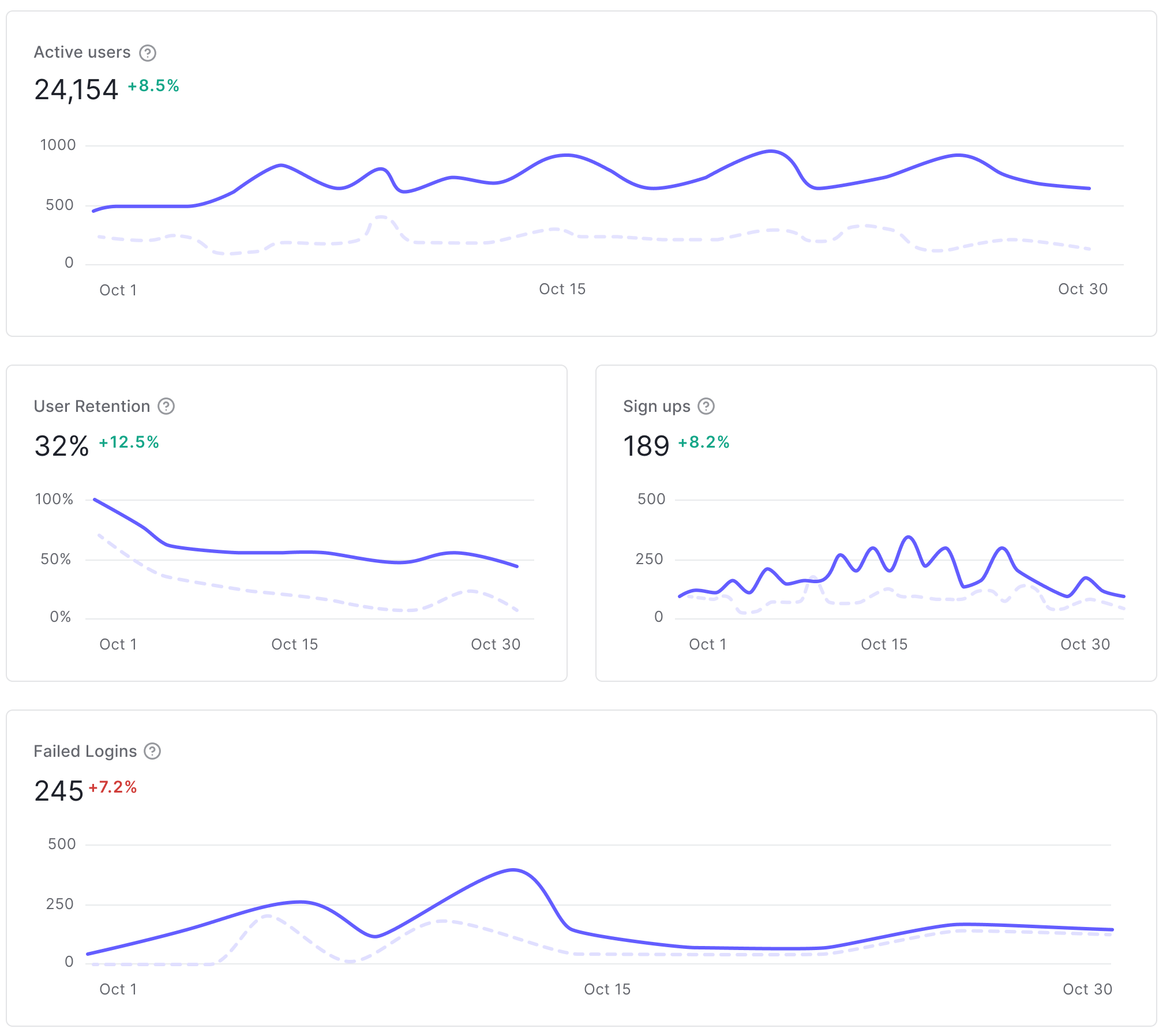
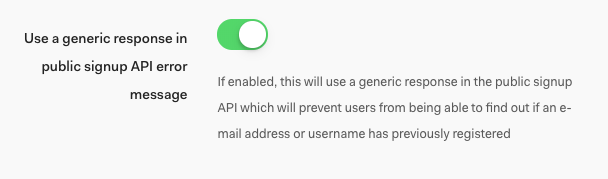
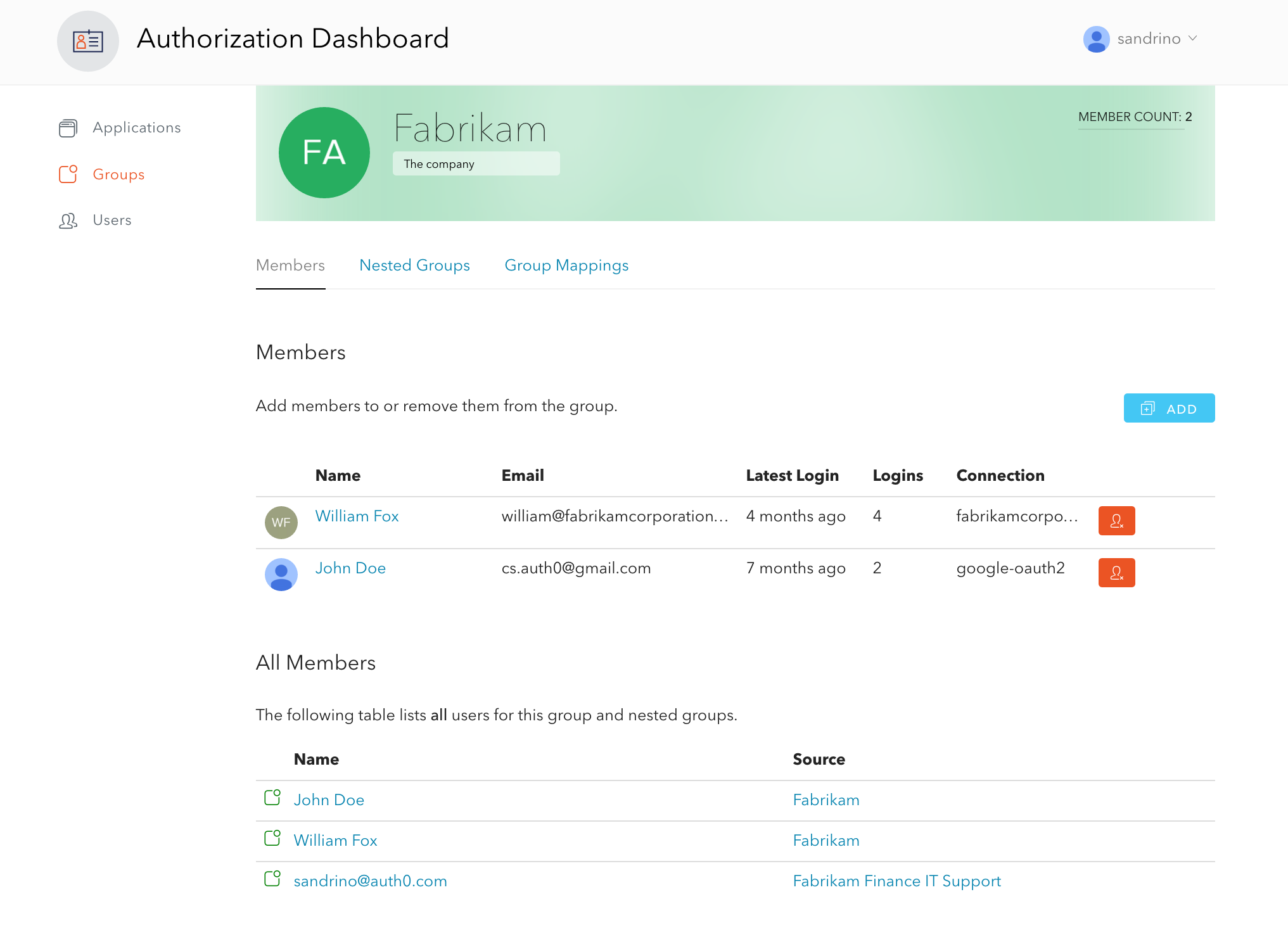
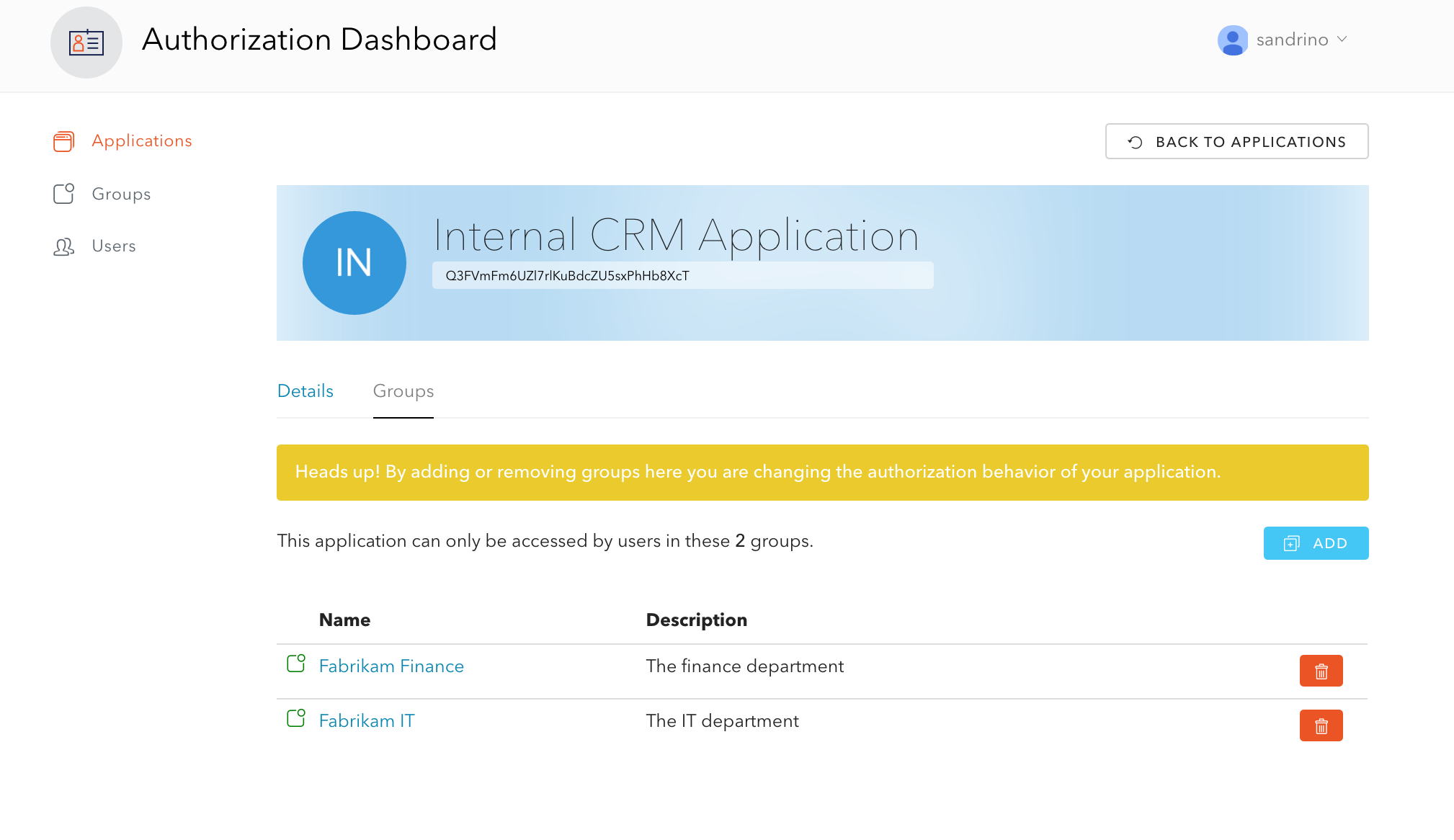
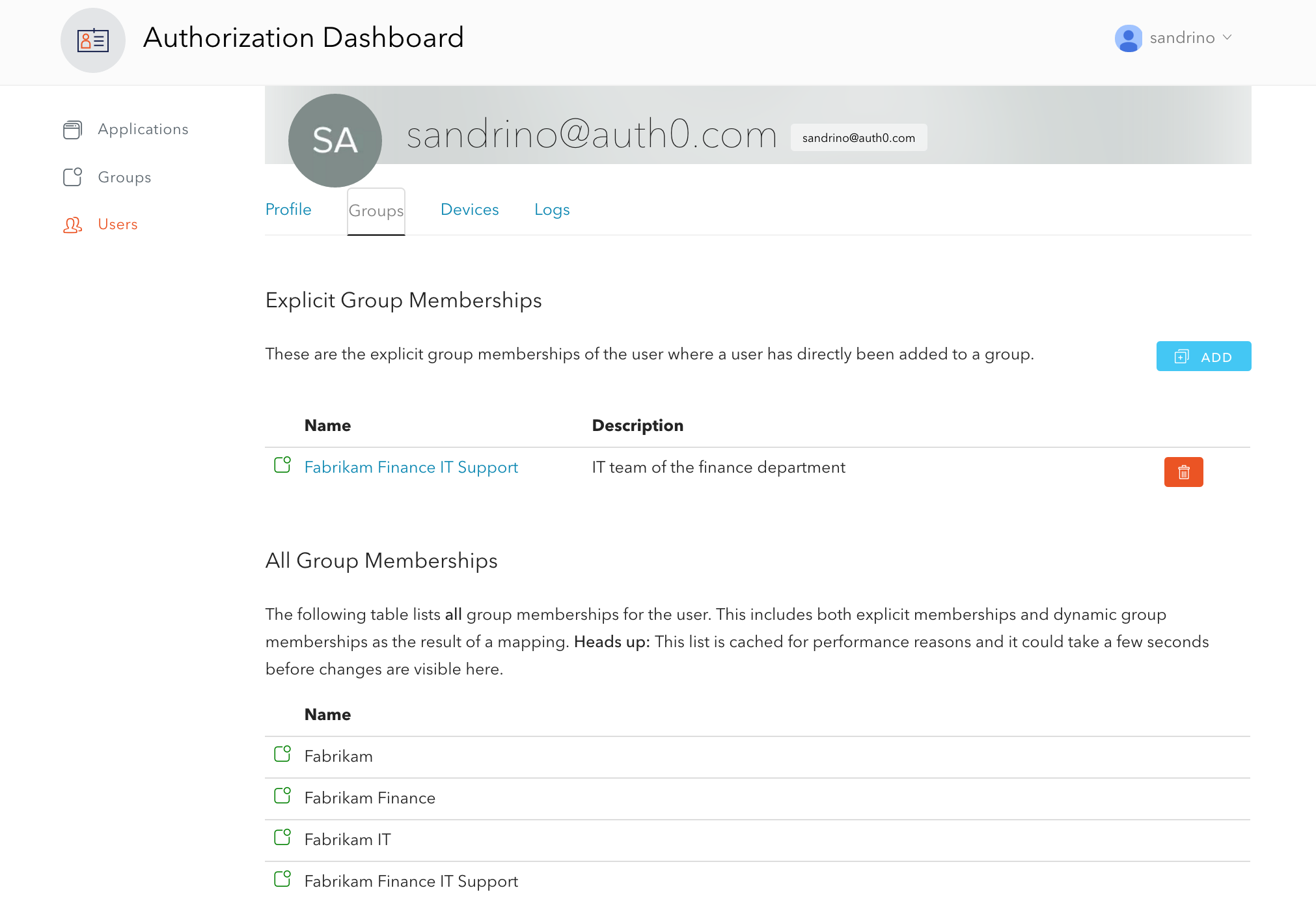
Auth0 is excited to share an updated list of IP addresses for allow listing on Public Cloud regions, as follows. The updates include, but are not limited to, GeoHA enhancements to Australia and Japan Public Cloud regions.
Request your attention if IP allow list is being used or planned to be used for your deployment on Auth0 Public Cloud. Please refer to Auth0 IP Addresses for Allow Lists for further information on when IP allow list could be required.
United States
174.129.105.183 , 18.116.79.126 , 18.117.64.128 , 18.191.46.63 , 18.218.26.94 , 18.232.225.224 , 18.233.90.226 , 3.131.238.180 , 3.131.55.63 , 3.132.201.78 , 3.133.18.220 , 3.134.176.17 , 3.19.44.88 , 3.20.244.231 , 3.21.254.195 , 3.211.189.167 , 34.211.191.214 , 34.233.19.82 , 34.233.190.223 , 35.160.3.103 , 35.162.47.8 , 35.166.202.113 , 35.167.74.121 , 35.171.156.124 , 35.82.131.220 , 44.205.93.104 , 44.218.235.21 , 44.219.52.110 , 52.12.243.90 , 52.2.61.131 , 52.204.128.250 , 52.206.34.127 , 52.43.255.209 , 52.88.192.232 , 52.89.116.72 , 54.145.227.59 , 54.157.101.160 , 54.200.12.78 , 54.209.32.202 , 54.245.16.146 , 54.68.157.8 , 54.69.107.228
Europe
18.197.9.11 , 18.198.229.148 , 3.125.185.137 , 3.65.249.224 , 3.67.233.131 , 3.68.125.137 , 3.72.27.152 , 3.74.90.247 , 34.246.118.27 , 35.157.198.116 , 35.157.221.52 , 52.17.111.199 , 52.19.3.147 , 52.208.95.174 , 52.210.121.45 , 52.210.122.50 , 52.28.184.187 , 52.30.153.34 , 52.57.230.214 , 54.228.204.106 , 54.228.86.224 , 54.73.137.216 , 54.75.208.179 , 54.76.184.103
Australia
13.210.52.131 , 13.238.180.132 , 13.55.232.24 , 16.50.37.252 , 16.51.137.244 , 16.51.49.47 , 54.153.131.0 , 54.252.2.143 , 54.79.31.78
Japan
13.208.85.227 , 15.152.185.222 , 15.152.2.46 , 15.152.28.221 , 15.152.56.146 , 15.152.95.63 , 176.34.22.106 , 35.74.30.168 , 43.206.201.6 , 46.51.243.250 , 54.150.87.80 , 54.248.192.141
UK
18.135.40.36 , 3.10.89.10 , 3.8.59.62

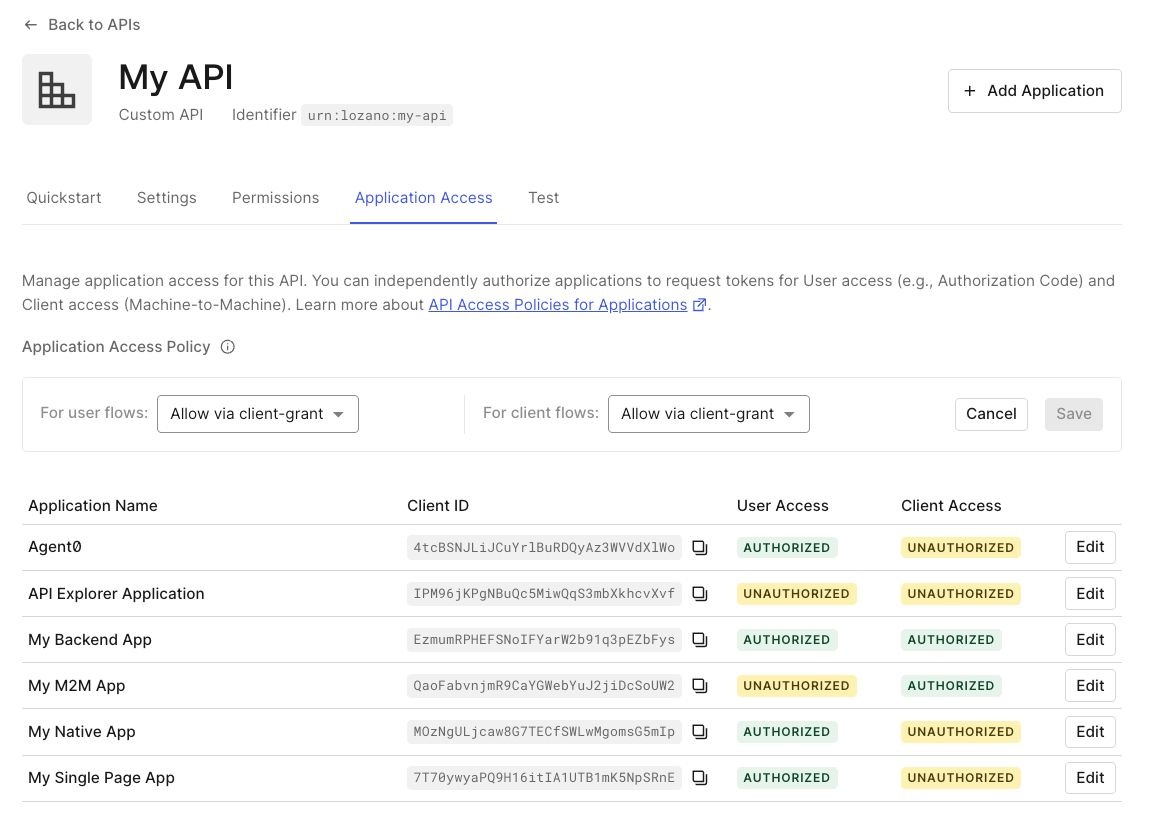

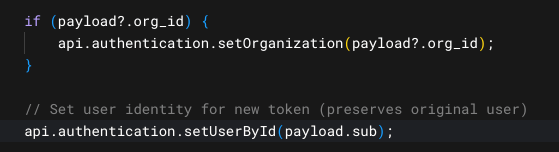
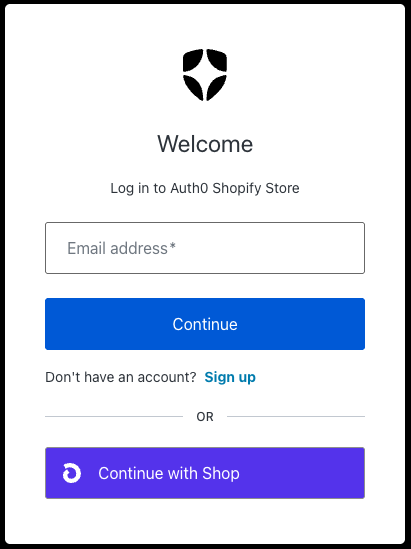
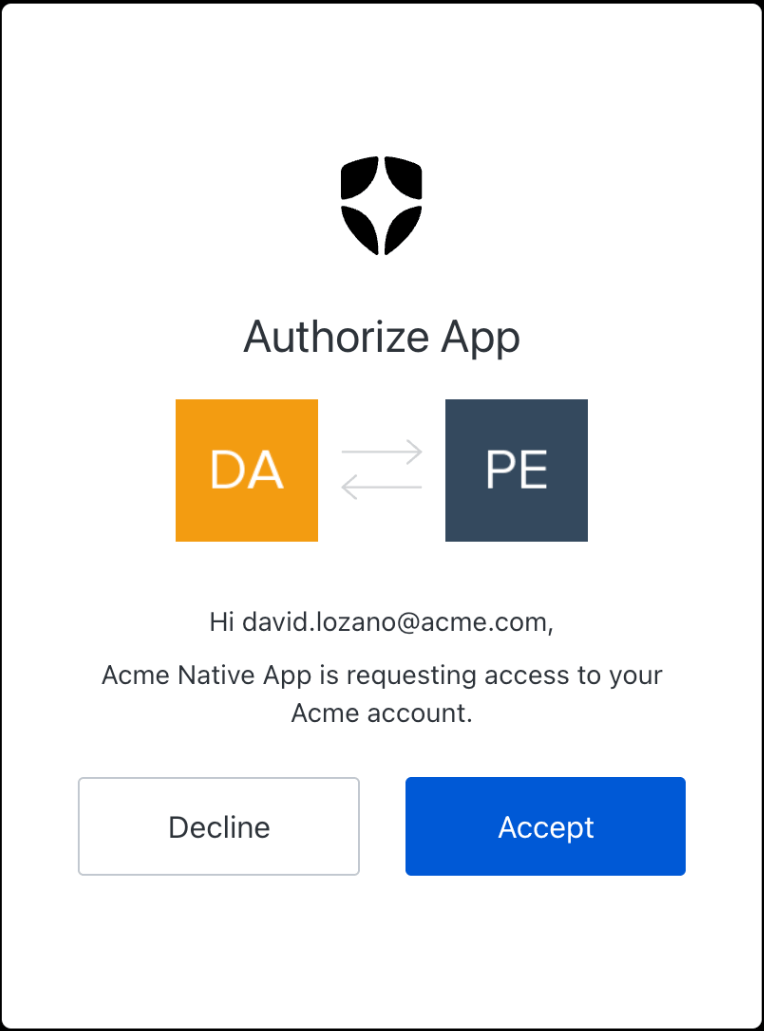
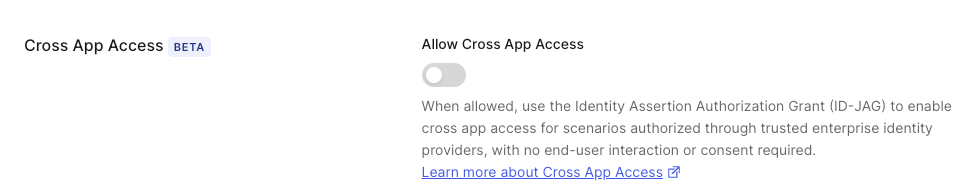
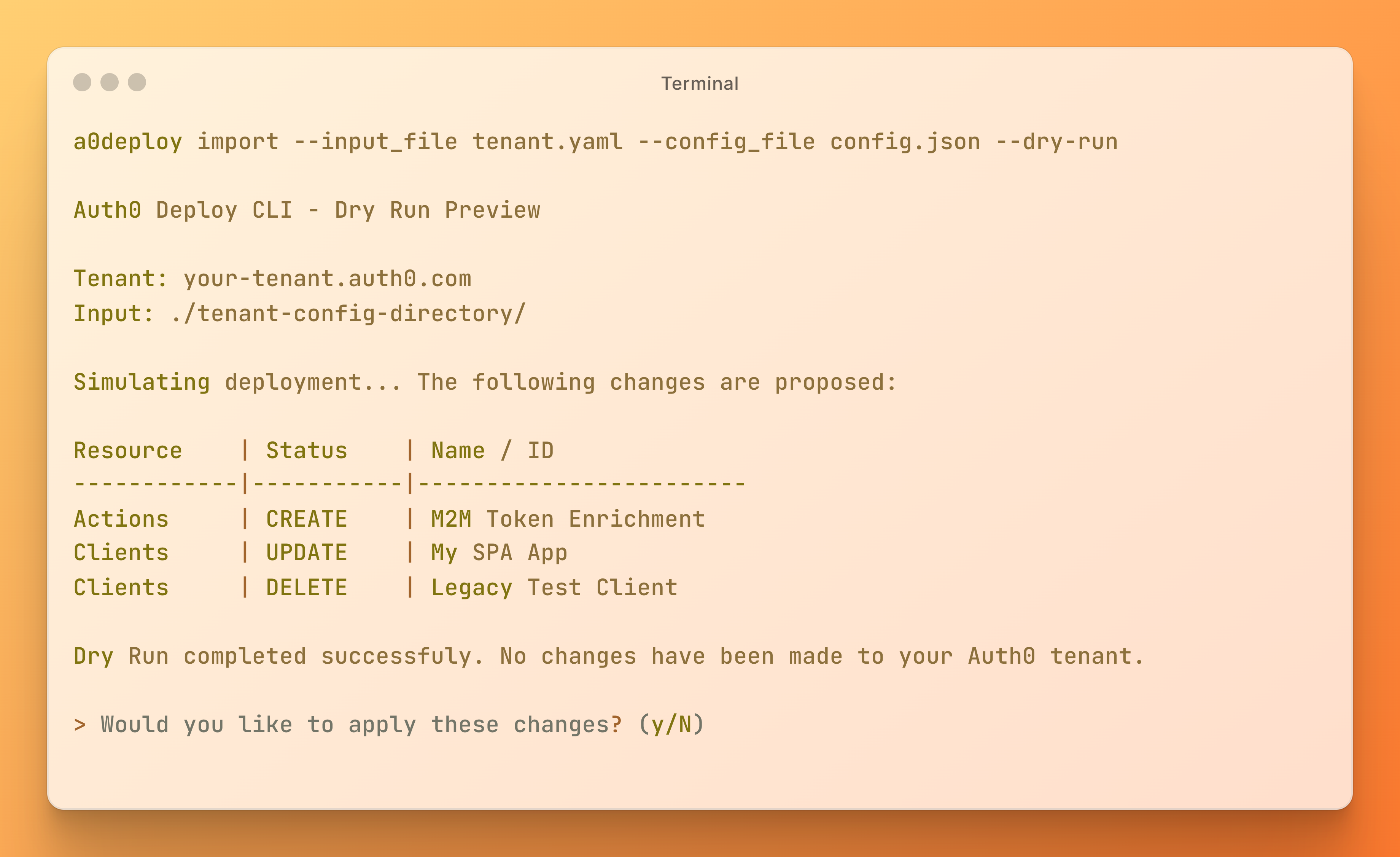


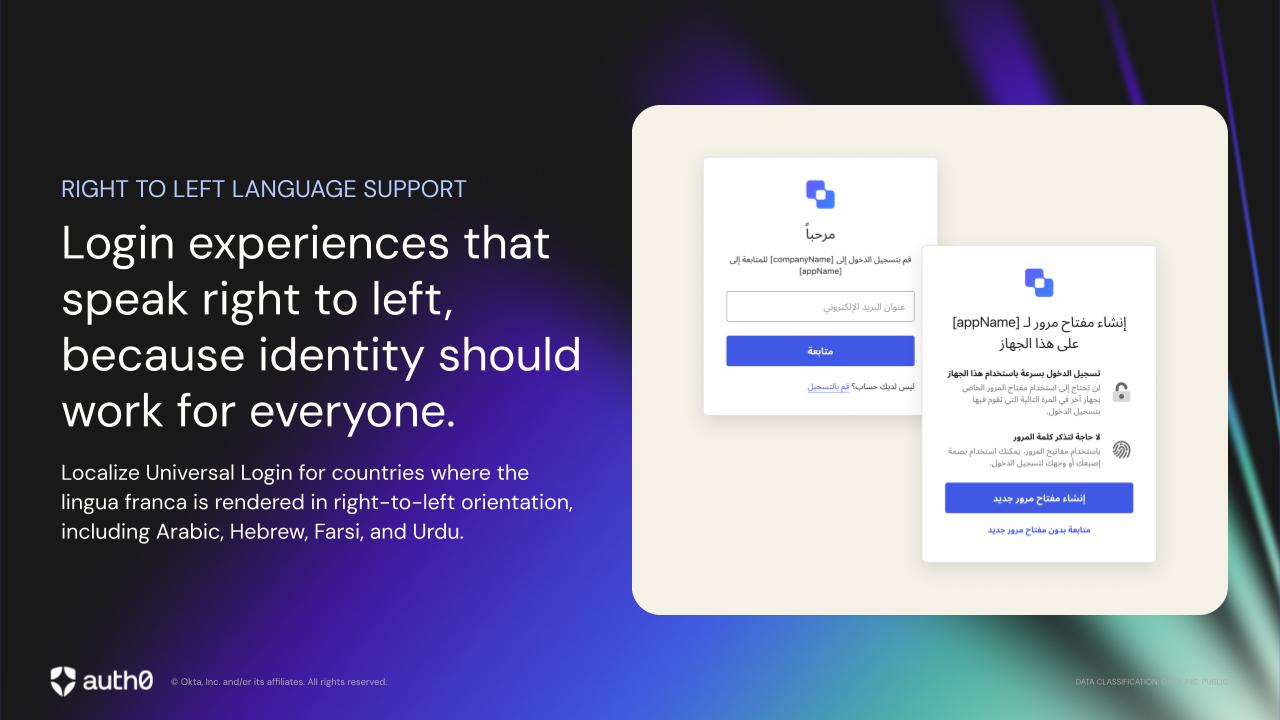

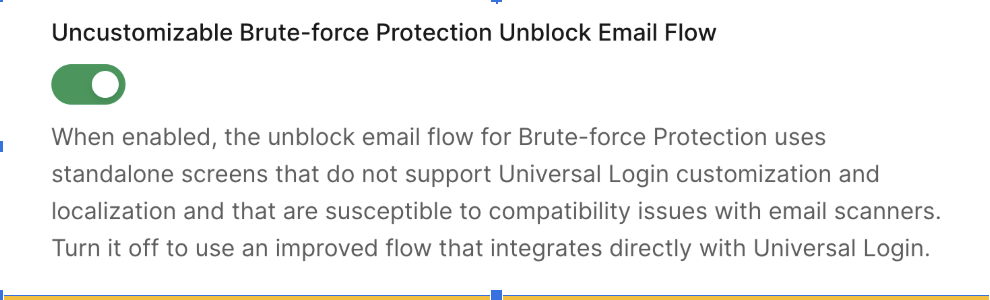
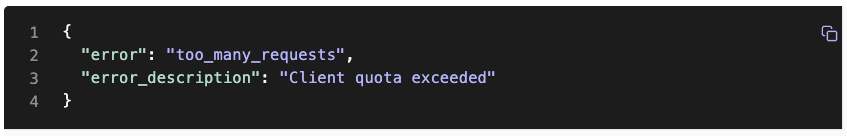
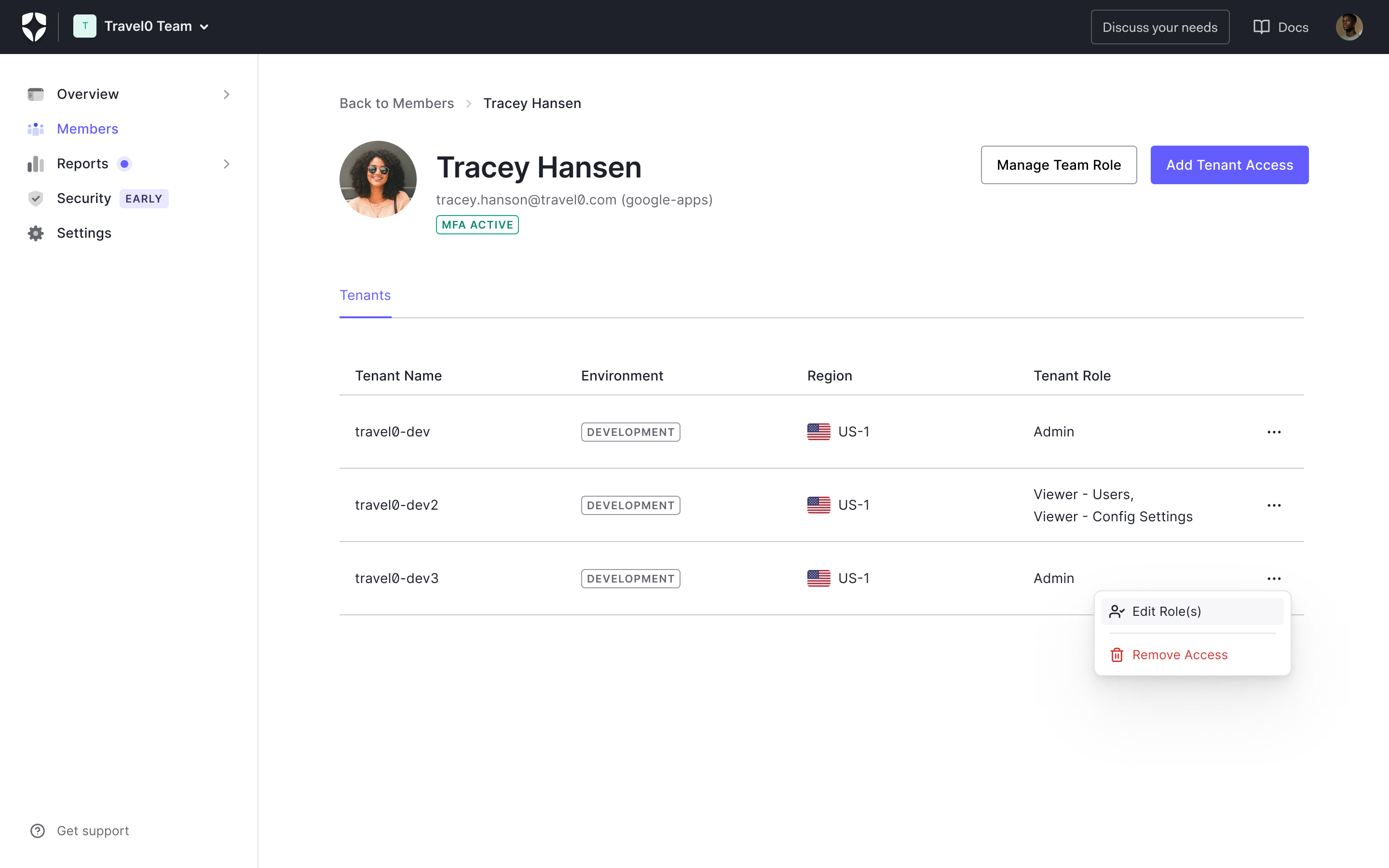








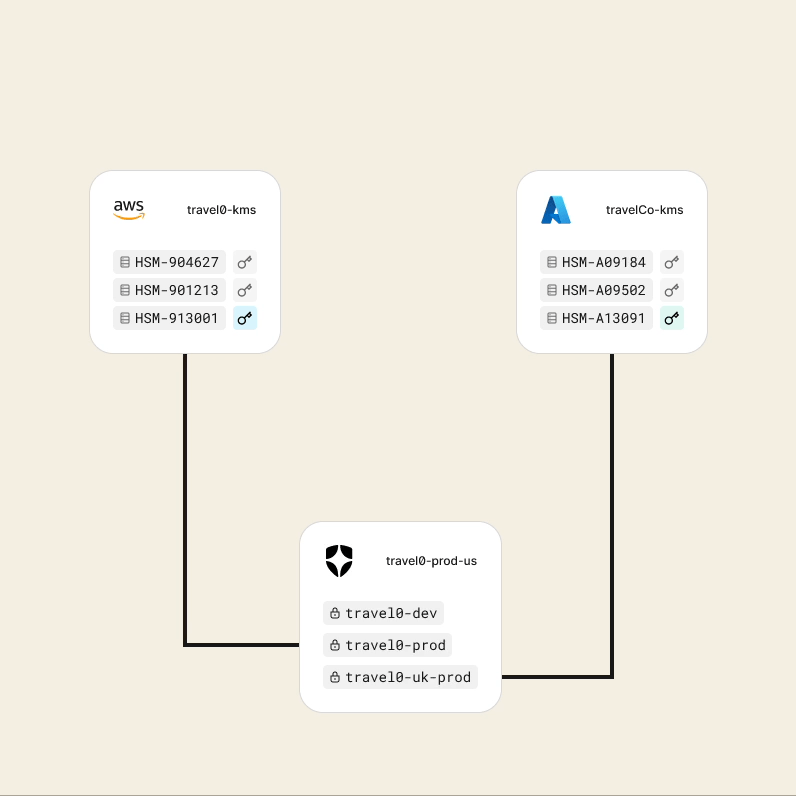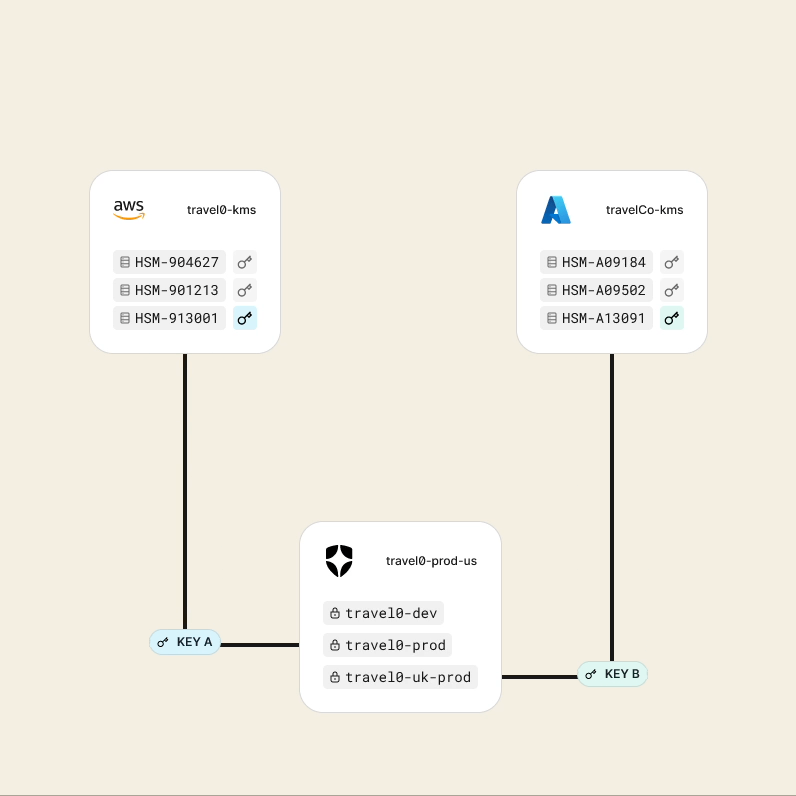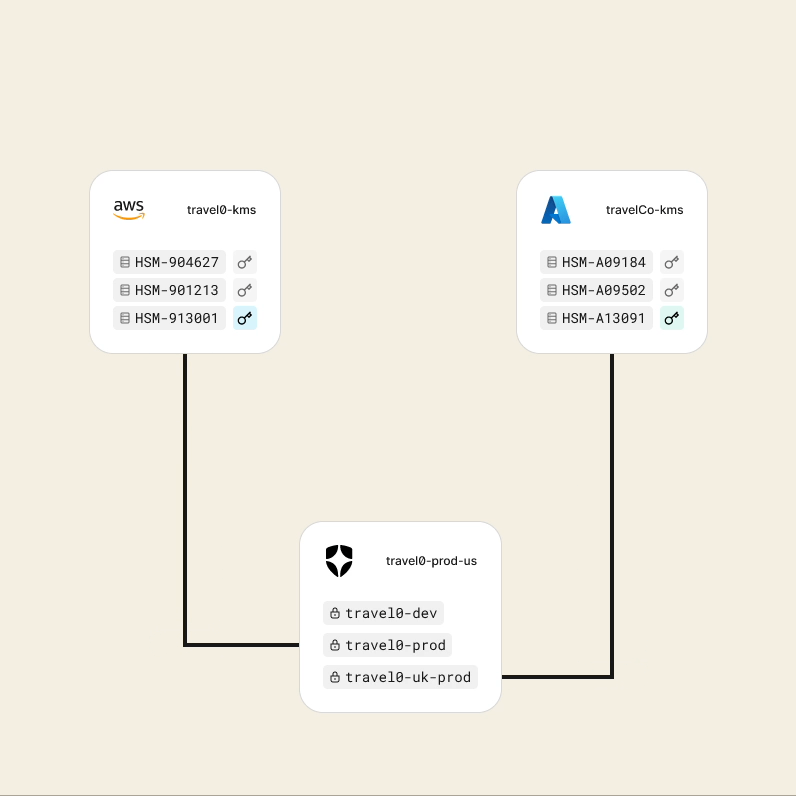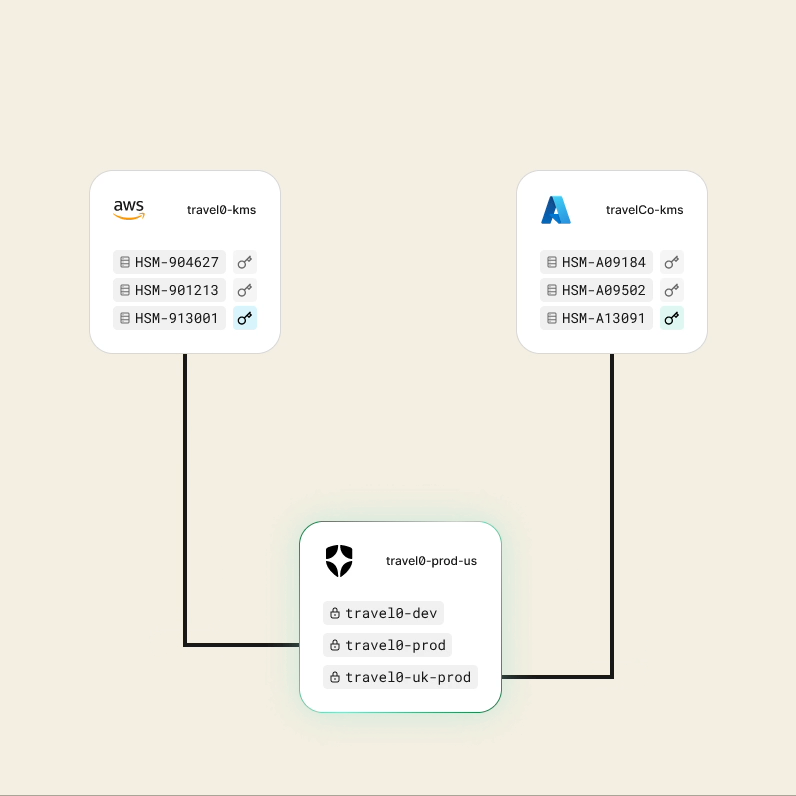

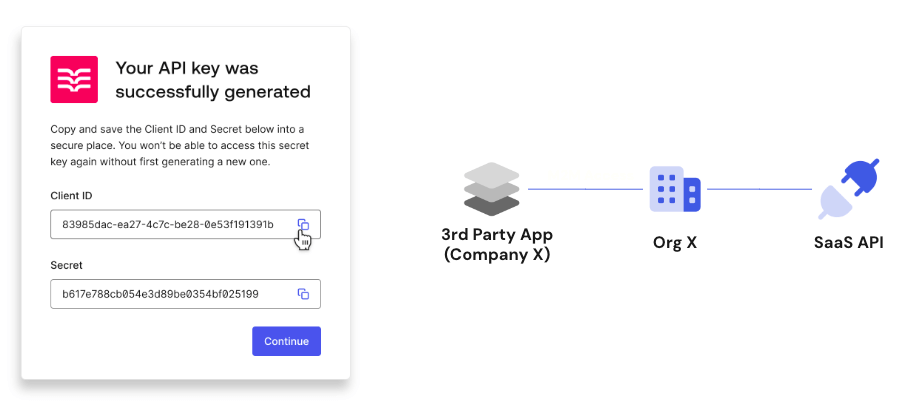

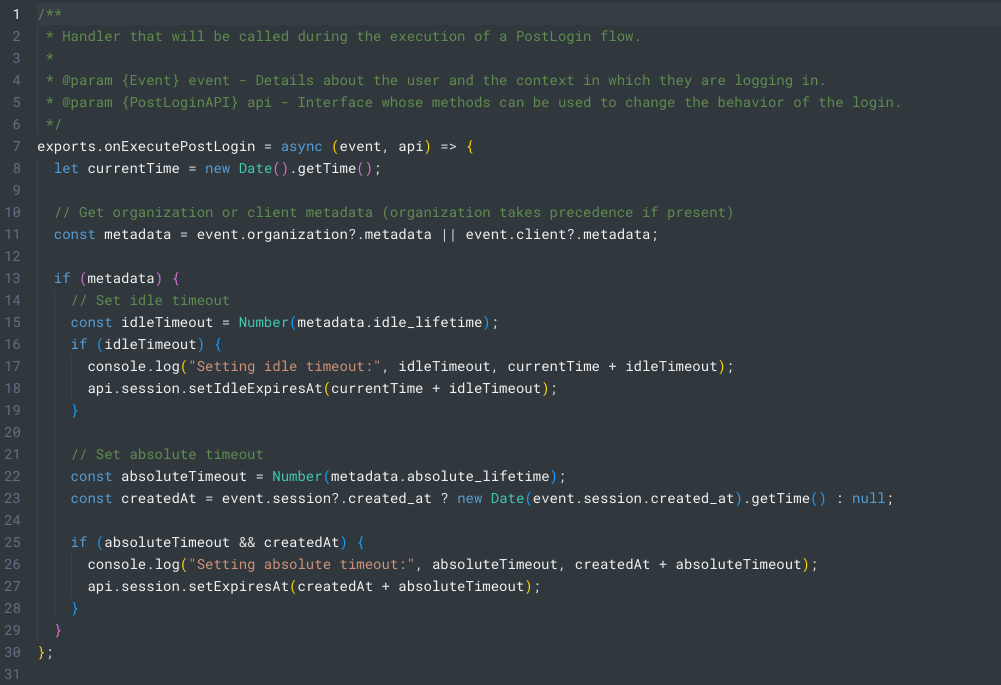




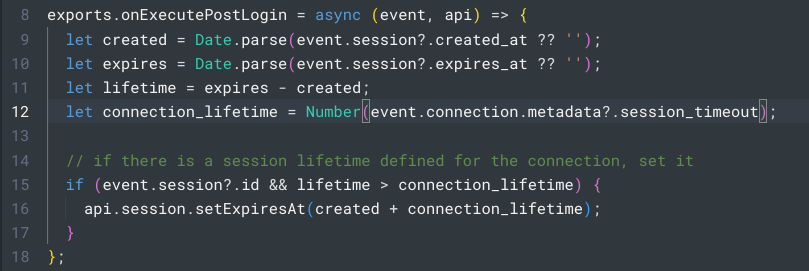


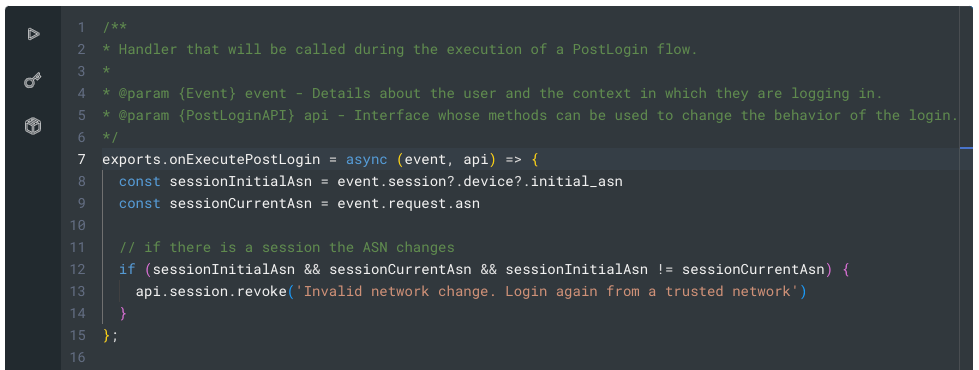
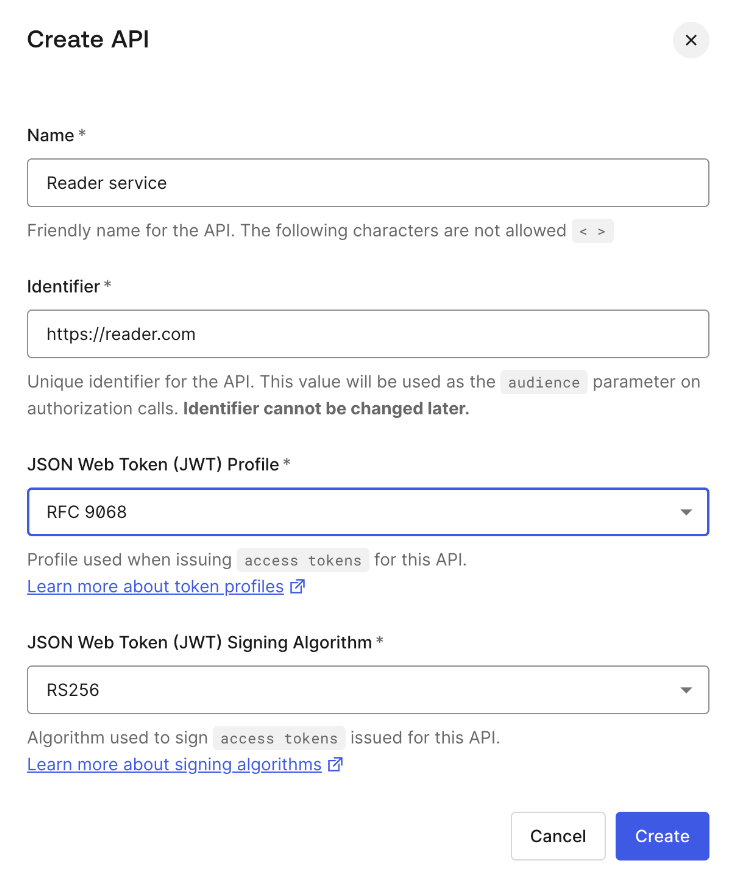


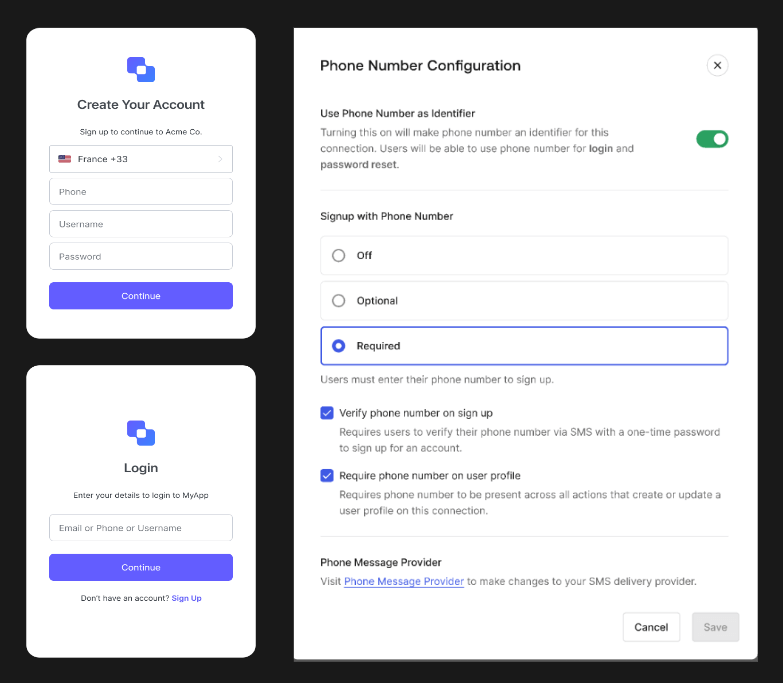
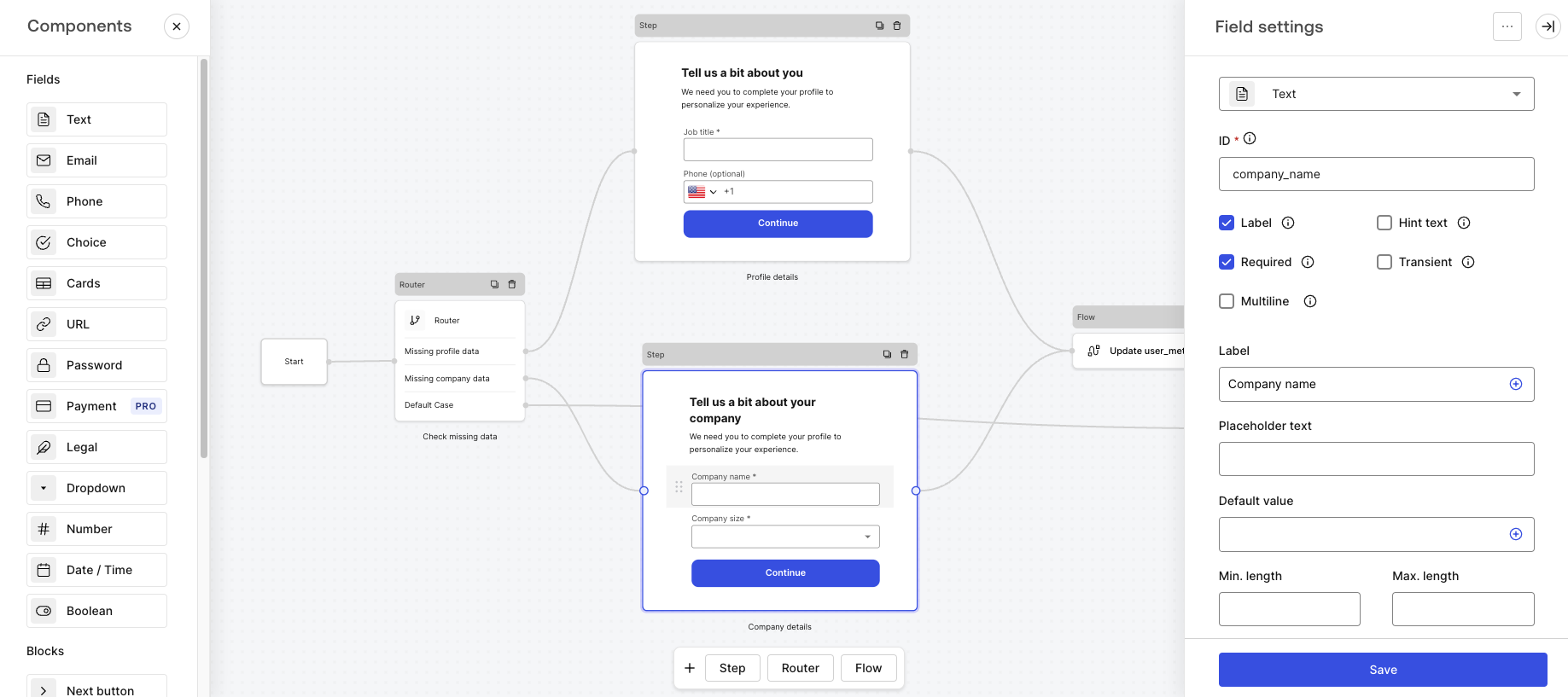


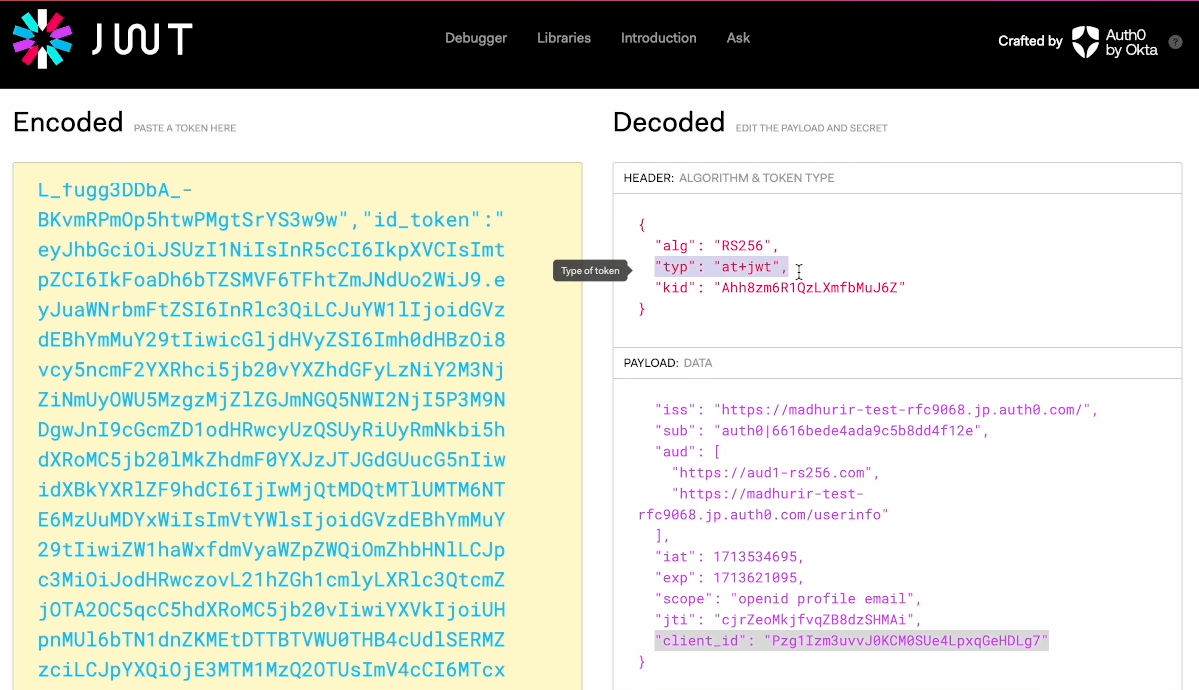
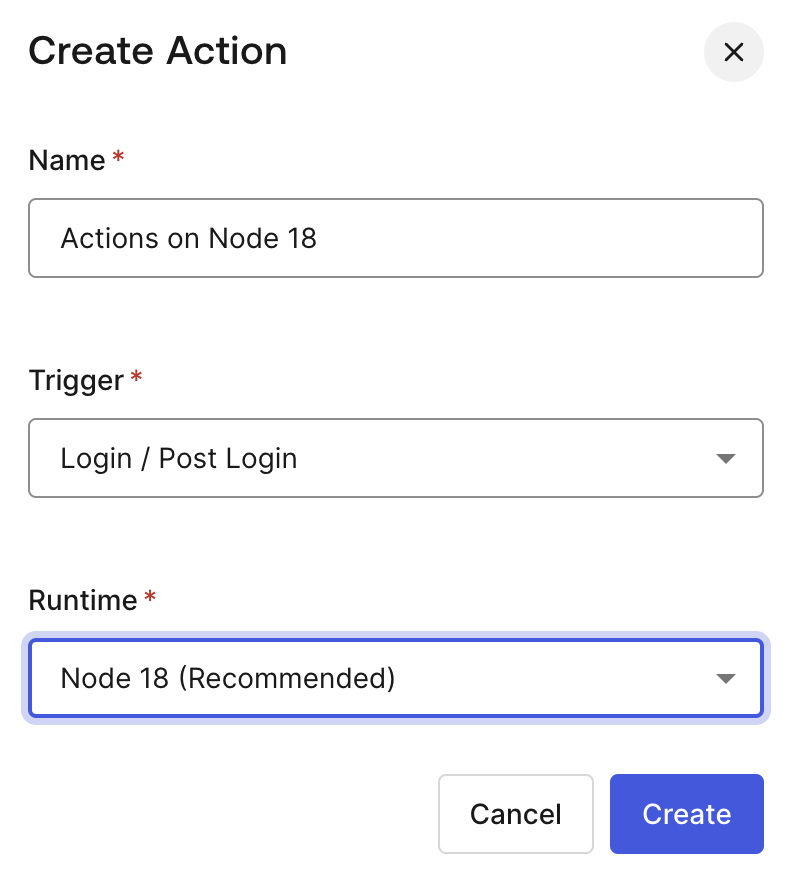
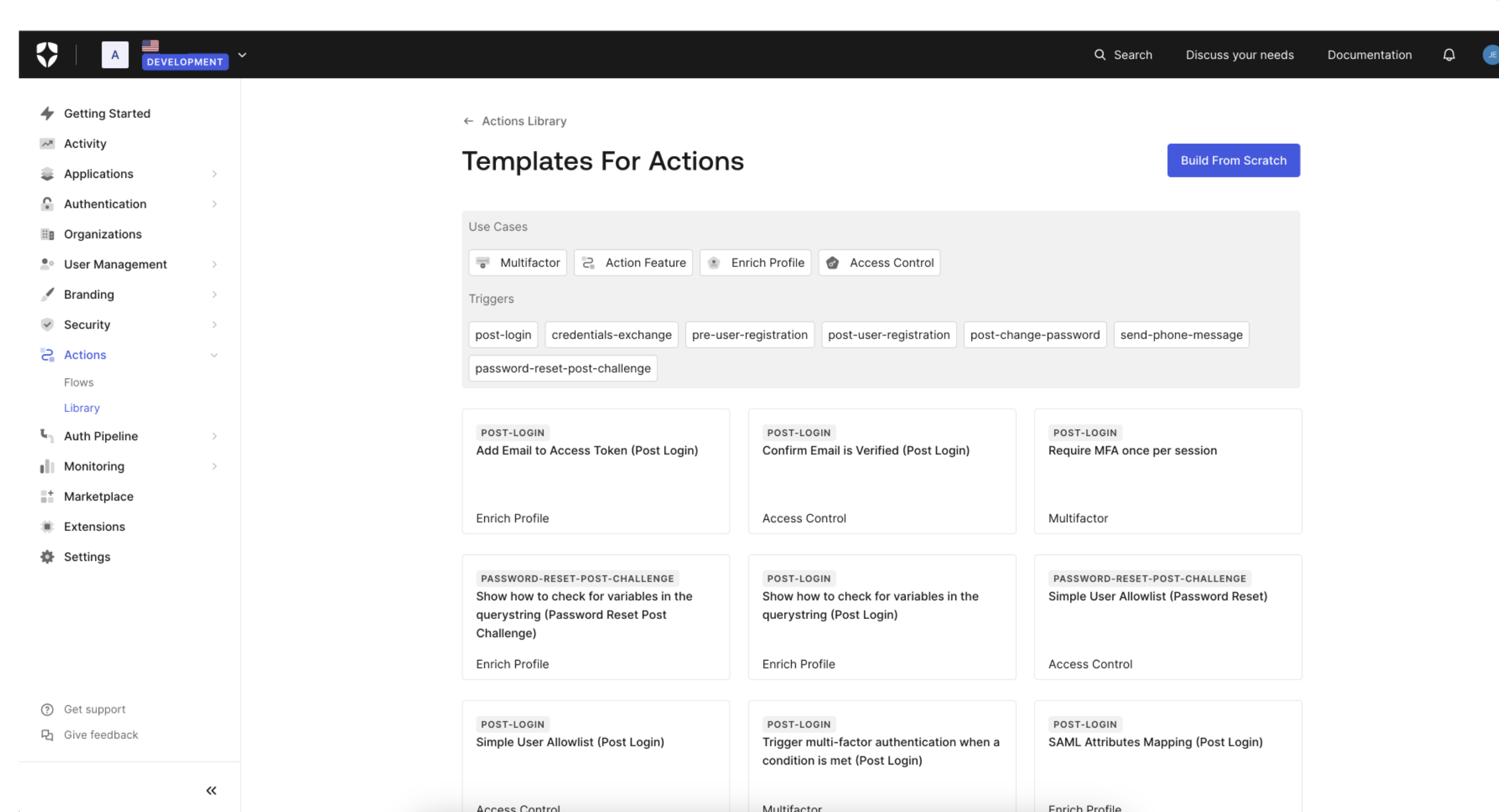 You can learn more about Templates for Actions from our
You can learn more about Templates for Actions from our 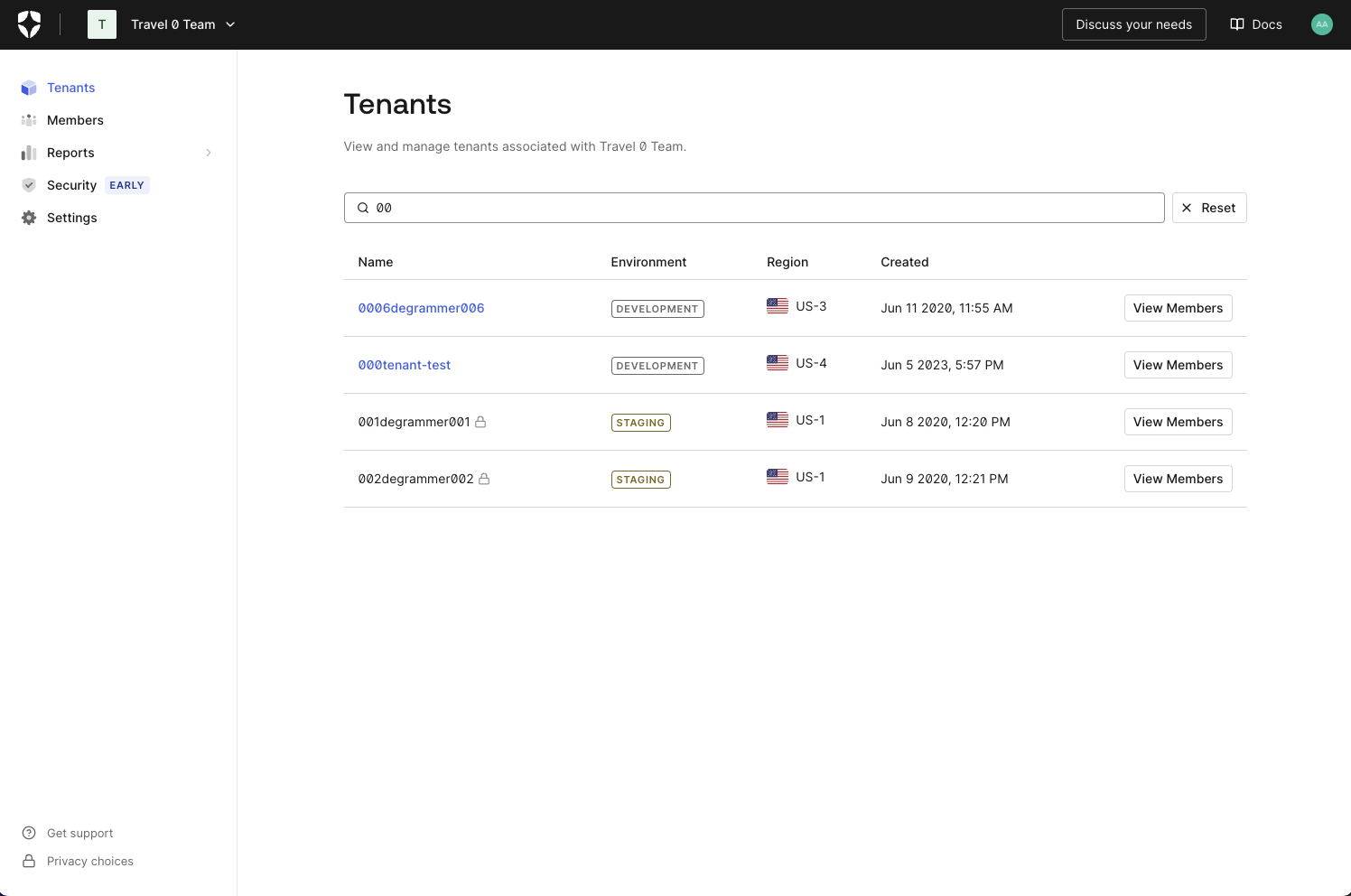
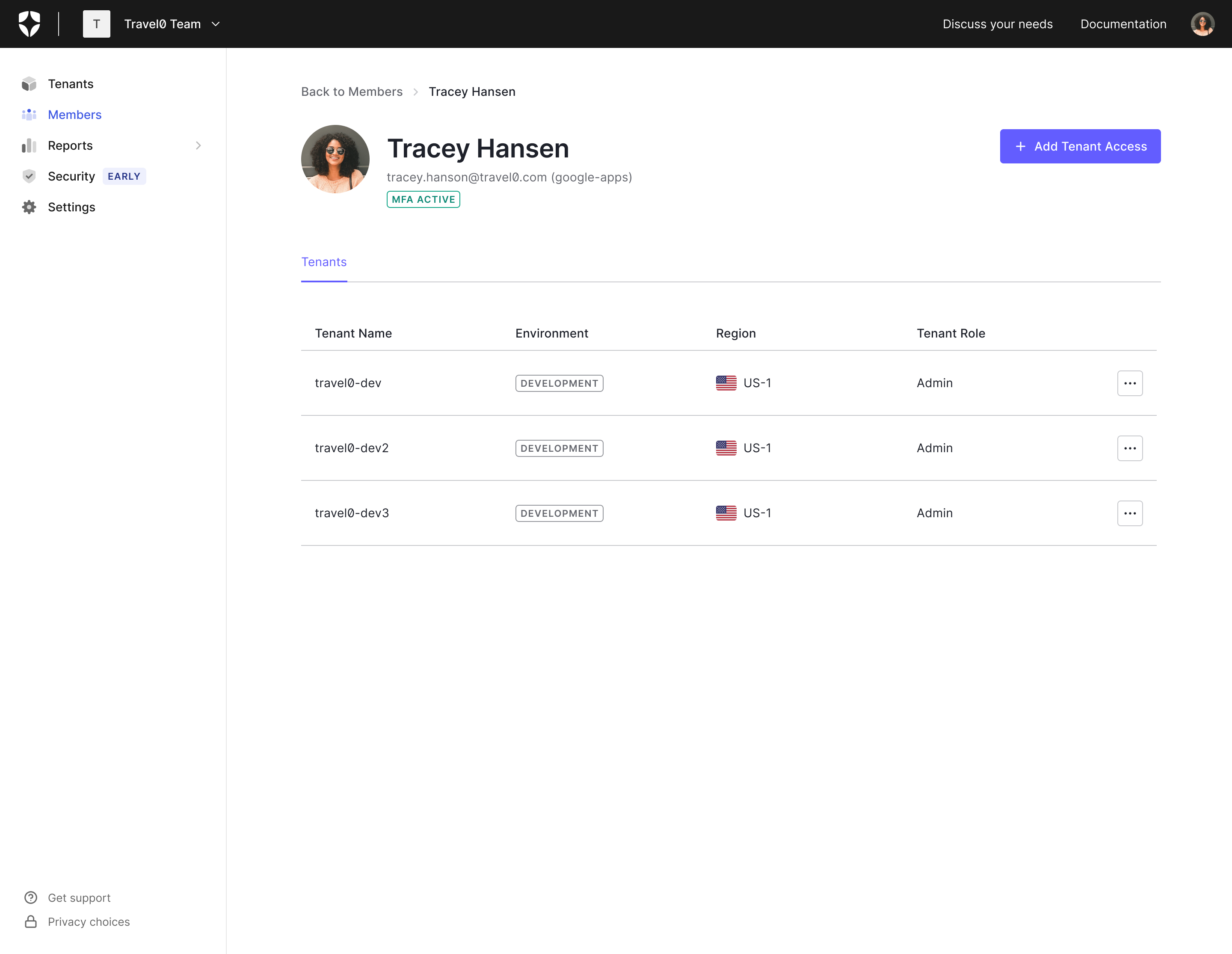
 Did someone order up one Dark Mode Browser extra Hot! Feel free to dim the lights; Teams Dashboard now supports dark mode.
Did someone order up one Dark Mode Browser extra Hot! Feel free to dim the lights; Teams Dashboard now supports dark mode.
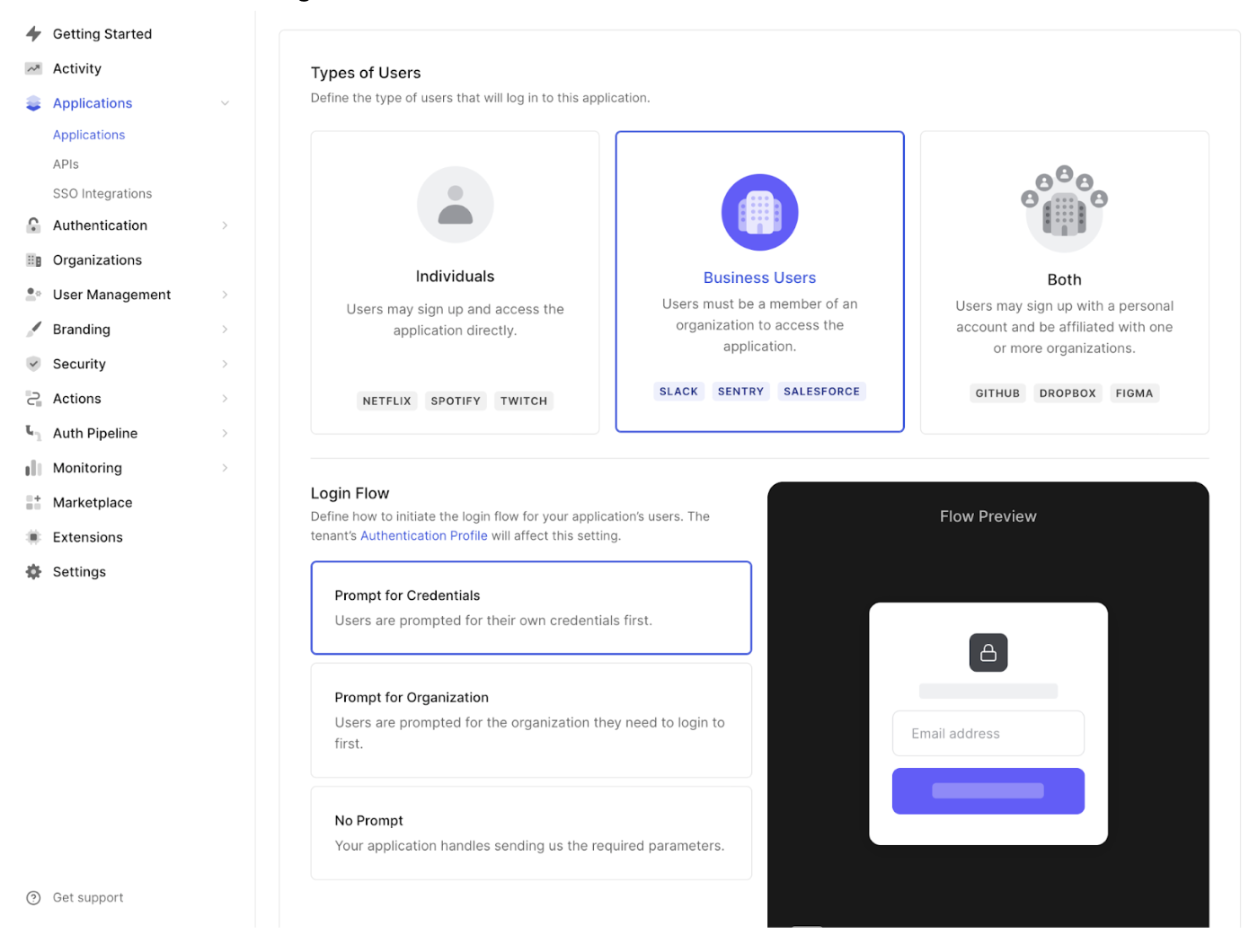
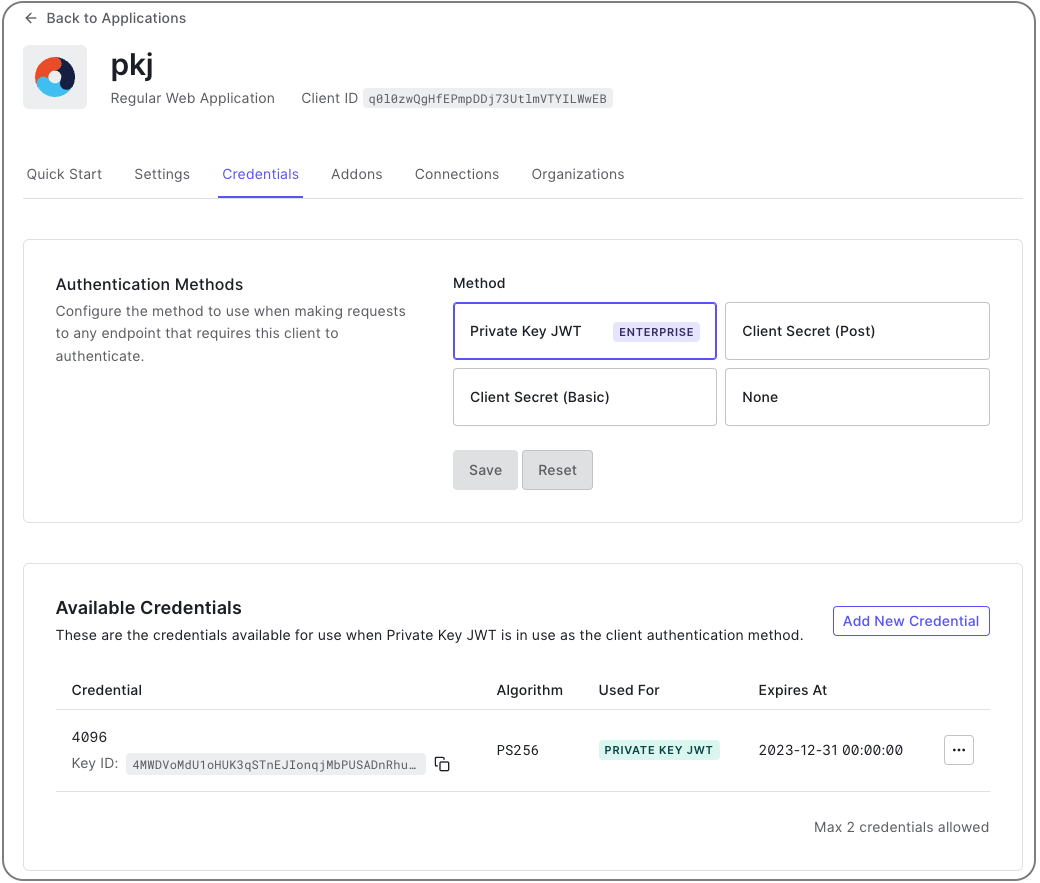
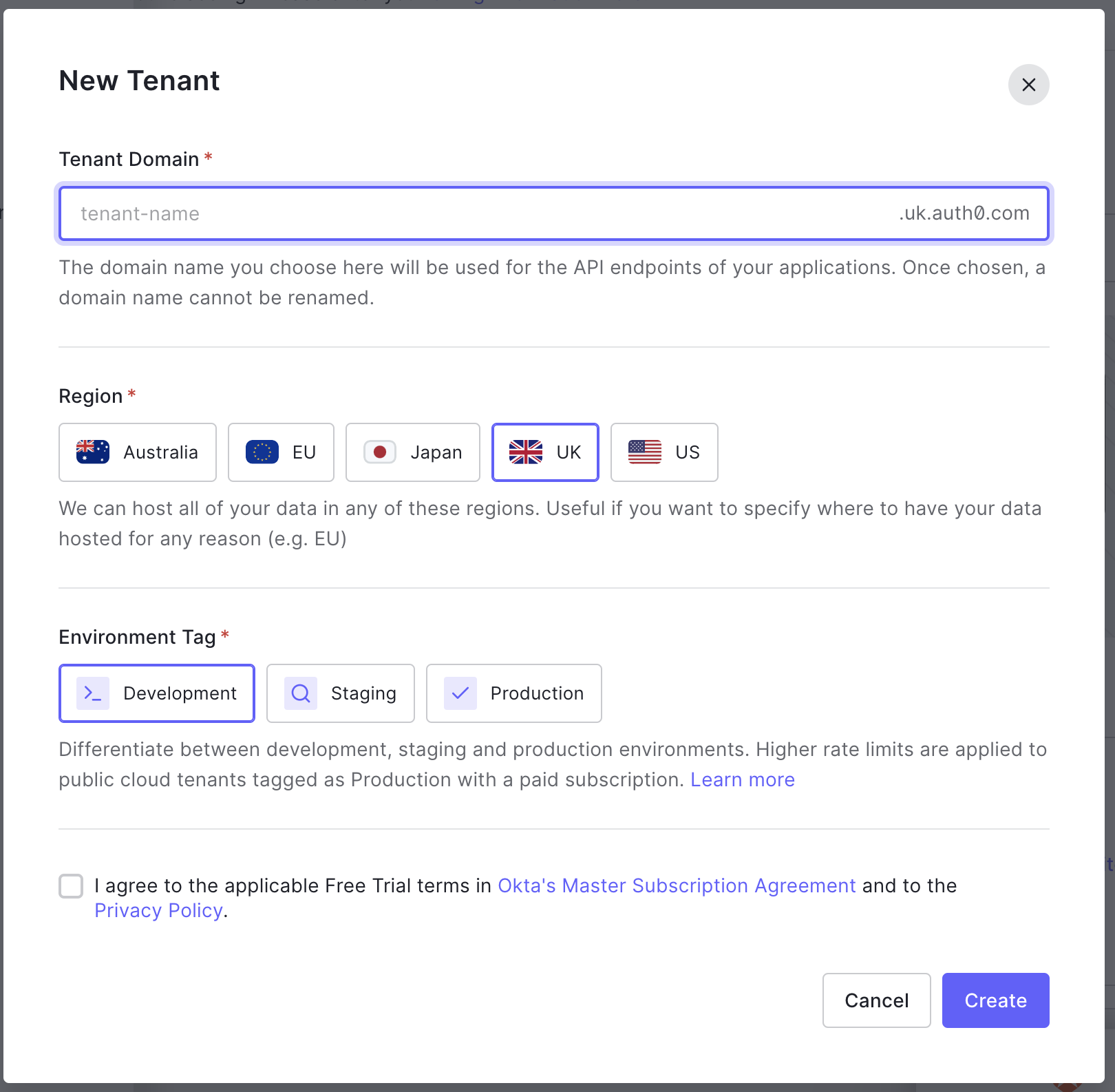
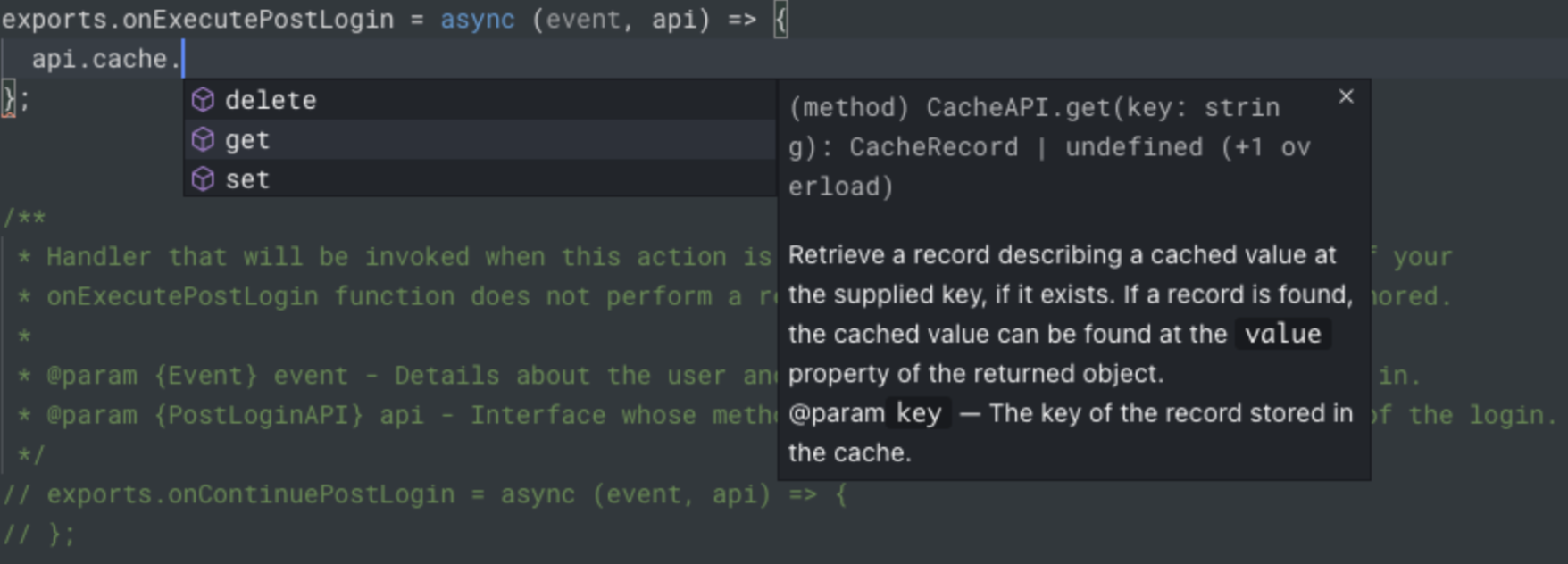
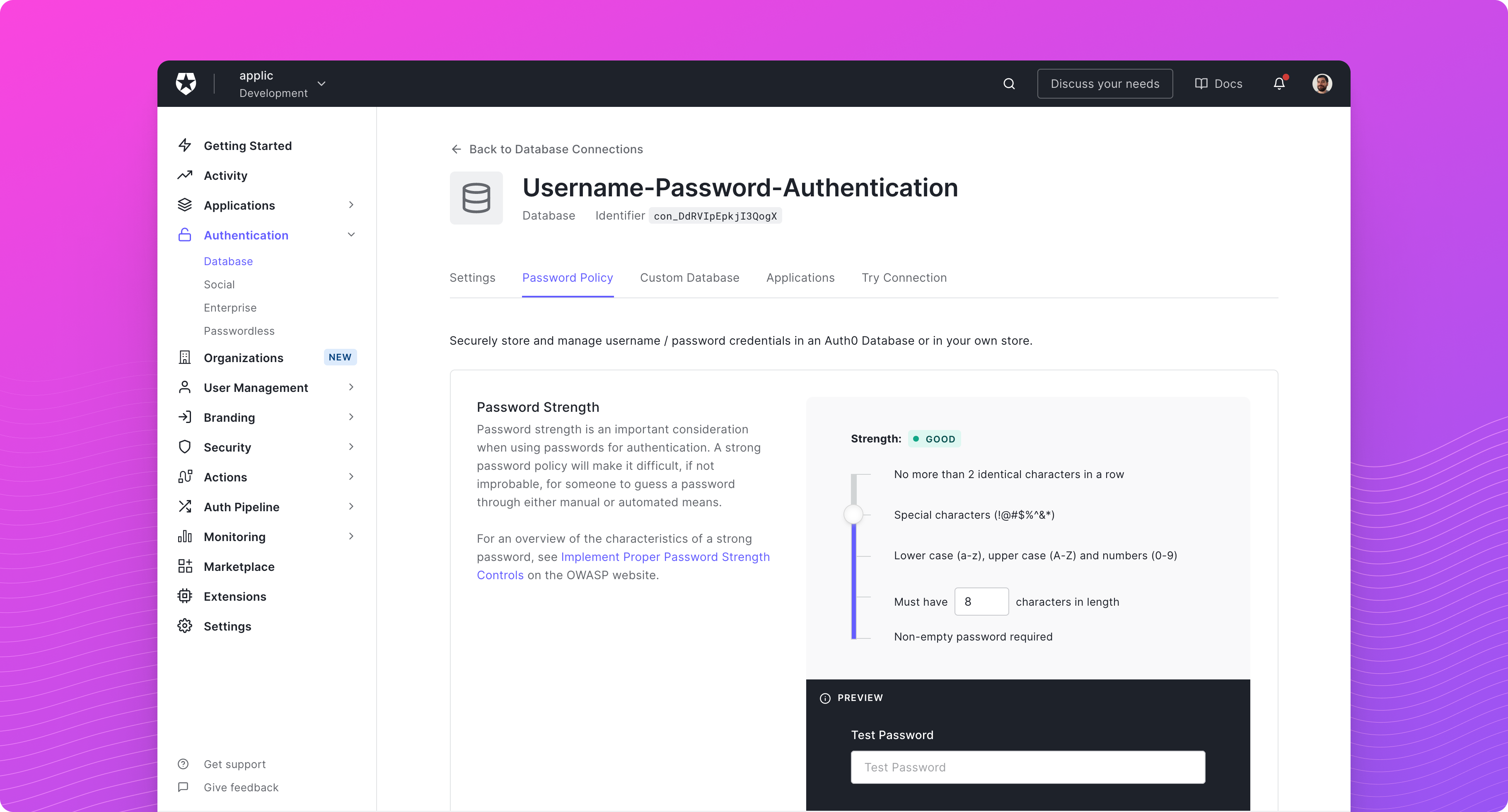
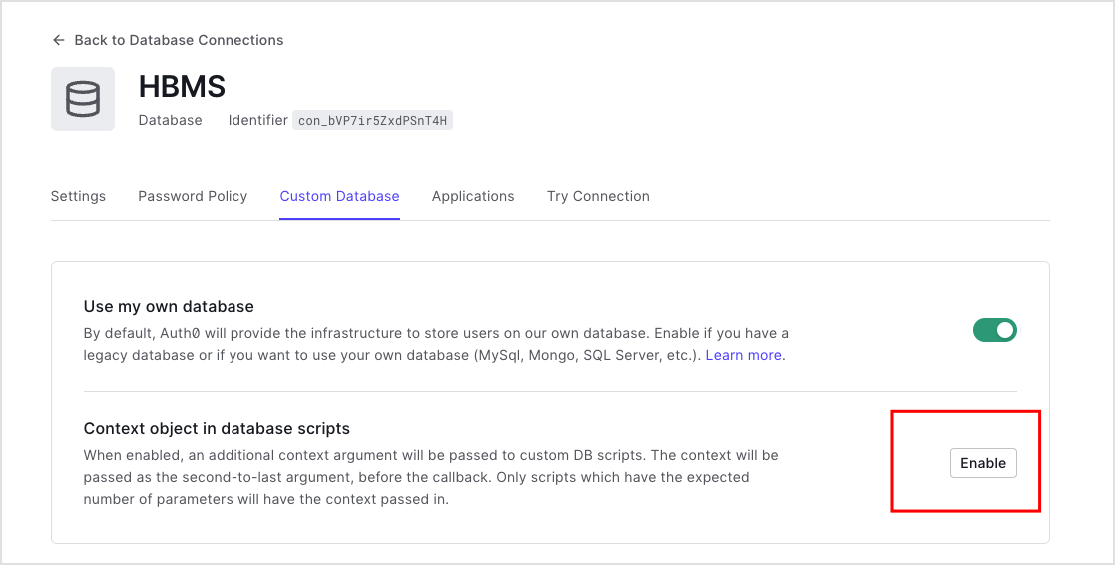 Once enabled, the custom database action script will be passed an extra parameter,
Once enabled, the custom database action script will be passed an extra parameter,