Secure MCP clients and servers using OAuth 2.1 and OpenID Connect, with user authentication, controlled API access, standards-based client registration, and scoped token exchange.
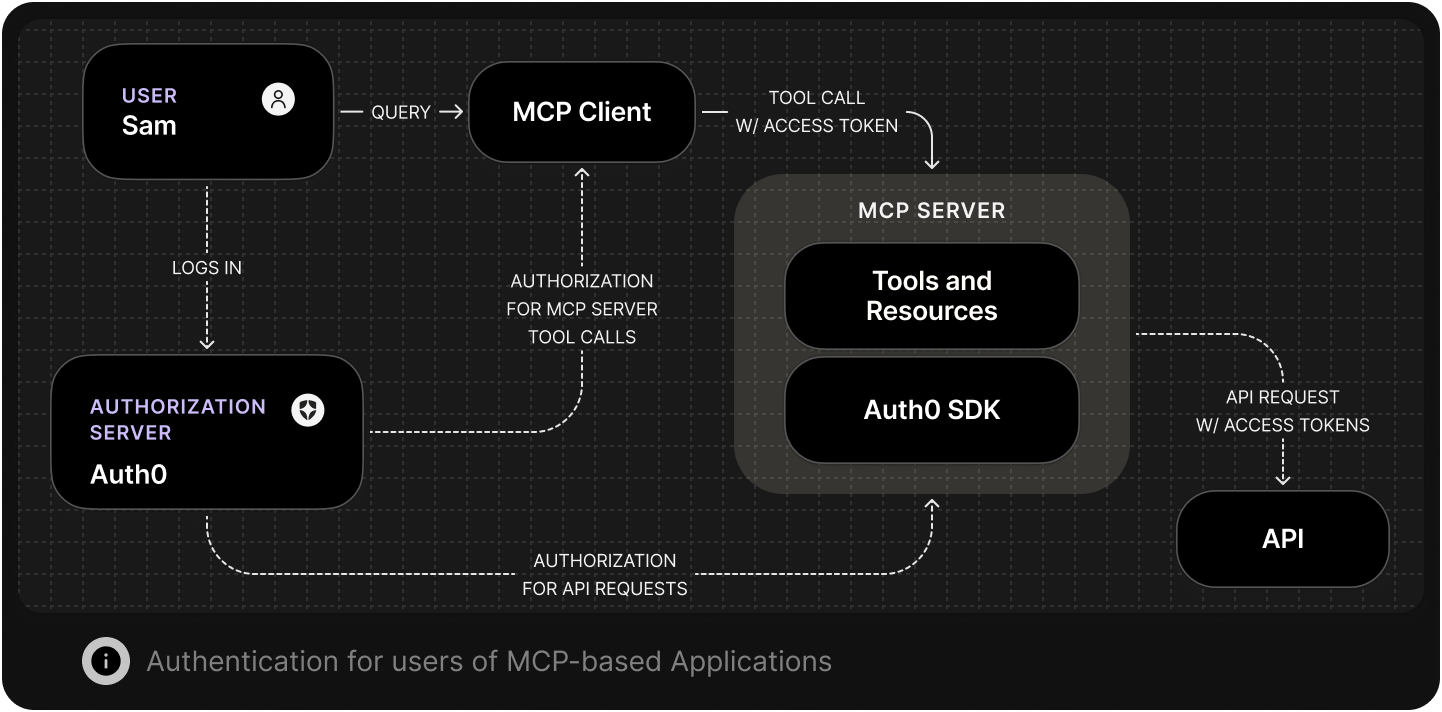
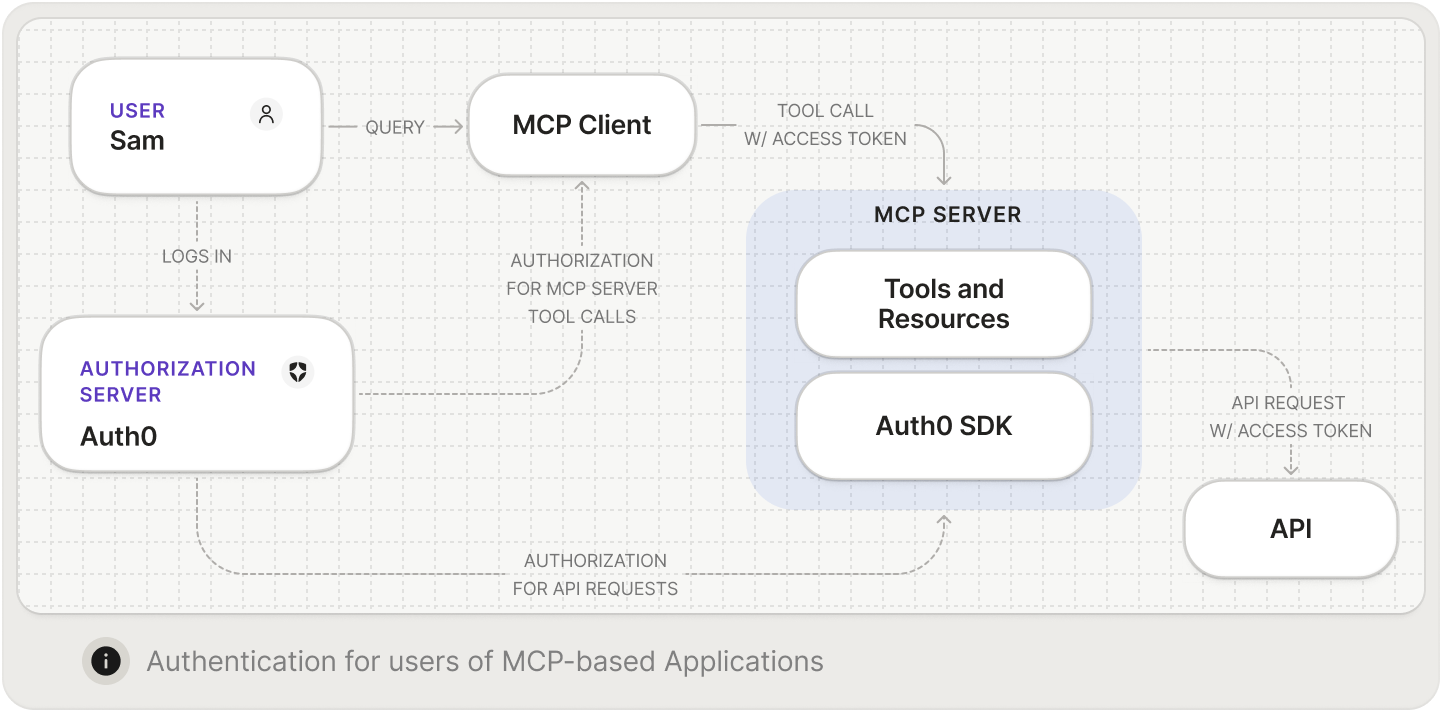
Accessing a Protected MCP Server
When an MCP server is protected with Auth0, clients and AI agents must first obtain an OAuth 2.0 access token to access it. Auth0 manages the authorization flow, ensuring the user authenticates with their chosen identity provider such as Okta, Entra ID, Ping, or Google Workspace, and delegates limited permissions to the agent. The MCP client then uses the issued token to call the server. Auth0 handles authentication, token issuance and delegation of permissions. The MCP server then validates the token and enforces the authorization decisions represented in it.Learn more about the benefits of using Auth for MCP
Metadata Discovery and Client Registration for MCP
Register MCP clients and servers using standards-aligned discovery and registration so agents connect only to approved resources. Auth0 validates client metadata, issues client credentials, and exposes the necessary discovery endpoints. This lets MCP clients find the right authorization server and request tokens without manual configuration.Learn how to register your MCP client application
Call your APIs on a user’s behalf
When an AI agent connects to your MCP server, the server may need to call your internal APIs to read data or trigger workflows. Those APIs need tokens that reflect who the user is and what the server is allowed to do. Auth0 Custom Token Exchange enables that delegation. The MCP server exchanges the token it received from the client for a new, short-lived access token scoped to the internal API. This lets MCP servers call internal APIs on behalf of users while Auth0 issues and governs access centrally.Use this quickstart to call your APIs on a user's behalf from your MCP server
Call third-party APIs on a user’s behalf
MCP Servers often connect AI Agents to third-party services such as Google, Microsoft, Jira, or Notion. Auth0’s Token Vault handles these integrations by managing token issuance, storage, rotation, and revocation for external APIs. Token Vault eliminates manual credential handling and makes it easy to extend MCP connectivity across the modern SaaS ecosystem.Get started
To begin using Auth for MCP in your MCP server, refer to the following resources:Quickstarts
Guides
Registering your MCP Client Application
Resource Parameter Compatibility Profile
Test your MCP Server with MCP Inspector
Cloudflare MCP
Sample apps
SDKs
Early access
Auth for MCP delivers a more secure and scalable authentication and authorization for MCP servers using Auth0. It offers OAuth-compliant solutions for developers building applications that integrate AI agents.Early Access Program
Auth for MCP is currently available in Early Access. To join the Early Access program, please complete this form, and we’ll reach out to you when your request is processed.

