redirect_uri to return control to the application after login. After the URI loads in the device’s browser, the application typically opens automatically to allow the user to continue their journey.
Historically, mobile application used custom URI schemes (e.g., com.mycompany.myapp://oauth2redirect). However, custom URI schemes pose a risk as more than one application on the device can register the same scheme. Mobile OSs do not include built-in mechanisms to ensure the application receiving the redirect is the intended one. In this scenario, malicious apps impersonate legitimate ones and receive the authorization response (including tokens) without user awareness, especially if single sign-on (SSO) is active due to the existence of a previous legitimate session, in which additional user interaction is not required. PKCE doesn’t really help in these scenarios, as the malicious application can initiate the login flow and wait to receive the callback without user interaction.
Applications running on a local machine (e.g., desktop apps, CLIs) use the loopback interface for callbacks (e.g., http://127.0.0.1:51089/callback or http://localhost:61024/callback) are similarly at risk. In this case, another application on the same machine could listen on the same port to intercept the response.
We refer to both custom URI schemes and loopback URIs as Non-Verifiable Callback URIs because the authorization server cannot verify the receiving application in either scenario.
Recommended mitigations for mobile applications
Claimed HTTPS URIs (Universal Links / App Links)
Modern mobile OSs support claimed HTTPS URIs allows you to associate a website domain you control with your mobile app. Claimed HTTPS URIs are known as:- Universal Links on iOS
- App Links on Android
Auth0 strongly recommends using claimed HTTPS URIs as redirect URIs for all native applications.
- For iOS: Review Support Universal Links.
- For Android: Review Android App Links.
Recommended mitigations for all application
Auth0 cannot verify the legitimacy of the application receiving the authentication transaction results if:- Your application is unable to support claimed HTTPS URIs due to required compatibility with older mobile OS versions
- Your application is a desktop or CLI application
- The
redirect_uripresent in the request uses a non-verifiable URI (i.e. a custom URI scheme or a loopback URI). - The user has not been prompted with any other screen in the current login transaction (such as when a consent screen populates for third-party applications, or when MFA is required).
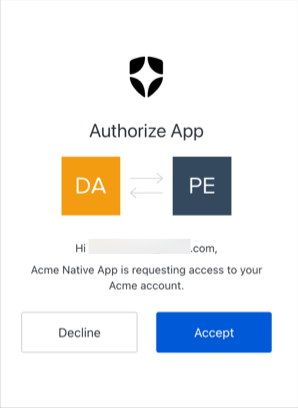
Prompt customization
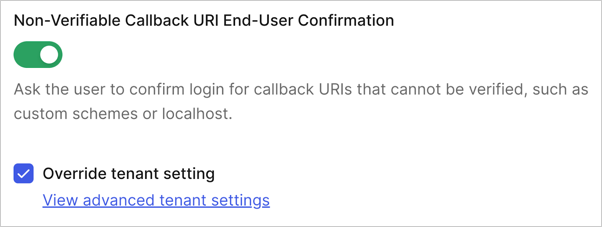
The confirmation prompt uses your custom branding and configurations defined for existing consent screens used for third-party applications. To learn more, review the Prompts section of Customize Universal Login Page Templates. You can configure the confirmation prompt as a global tenant settings or at the application-level. Application-level settings take precedence over the global tenant-level setting. Application-level- Navigate to Auth0 Dashboard > Applications > Application Settings > Advanced > OAuth.
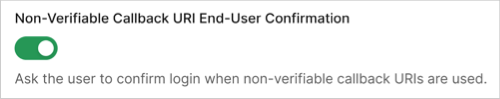
- Scroll to the Non-Verifiable Callback URI End-User Confirmation setting.
- Enable the toggle to activate the prompt or disable the toggle to deactivate the prompt.
- Navigate to Auth0 Dashboard > Settings > Advanced.
- Find the Non-Verifiable Callback URI End-User Confirmation setting.
- Enable the toggle to deactivate the prompt or disable the toggle to activate the prompt.