Today we are announcing the acquisition of Apility.io, an anti-abuse API company. This is our first acquisition, bolstering our security strategy to protect against automated and targeted cyberattacks, including credential stuffing and sophisticated phishing attacks.
Apility.io is now a part of Auth0 Signals, a new collection of dynamic data feeds that fuels Auth0's Anomaly Detection Engine to detect and prevent sophisticated cyberattacks. In addition, part of Auth0 Signals will be made available as a community version via free APIs to help anyone better protect themselves from threat actors.
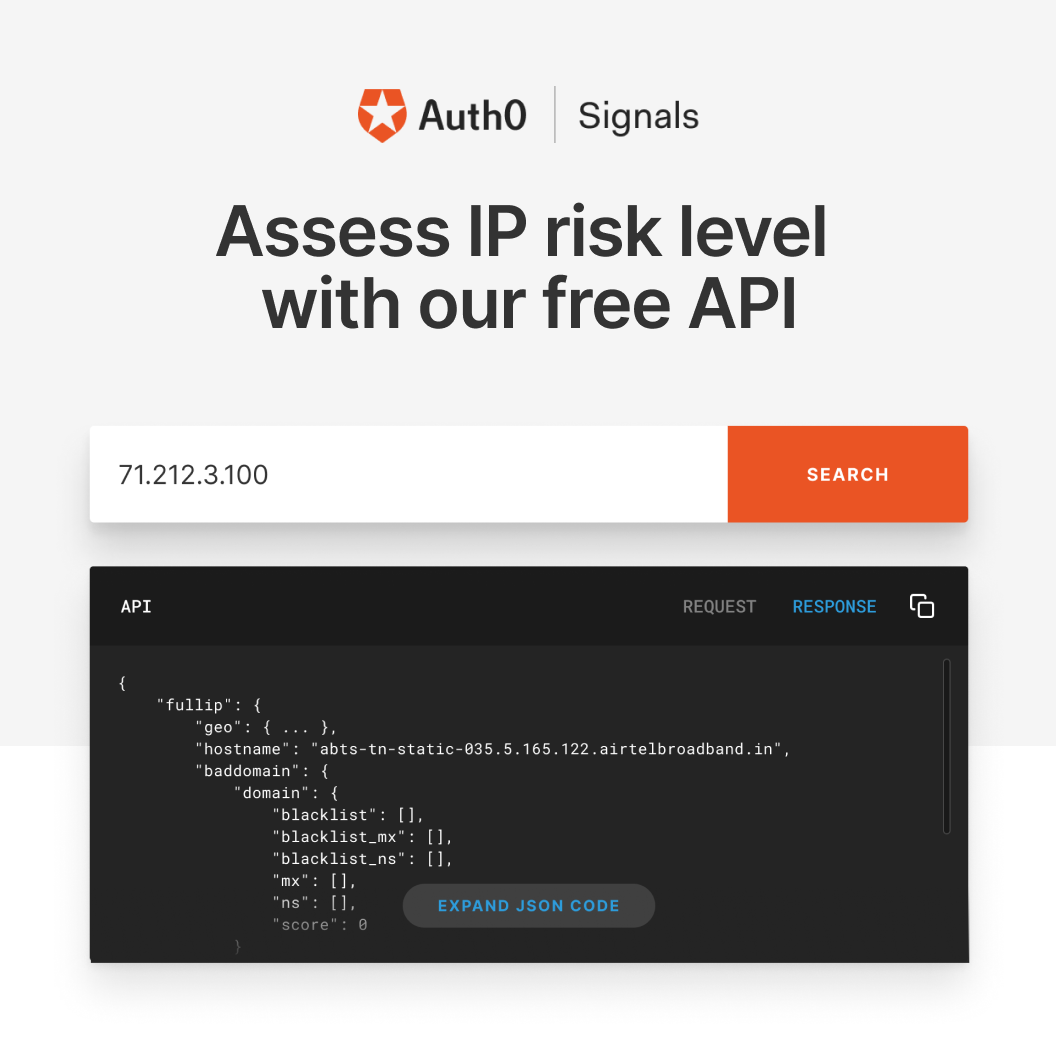
To try out Auth0 IP Signals, our first free Signals API, visit auth0.com/signals/ip
What is Auth0 Signals?
Auth0 Signals is a collection of dynamic data feeds that enable our adaptive authentication pipeline to produce high-quality user confidence scores.
Our authentication pipeline processes an ever-expanding number of Signals to assess the risk of a login attempt, account creation, token refresh, or elevation of privilege. It then produces a confidence score. Using this score, Auth0 and our customers can perform risk-based adaptive authentication decisions.
</div>
Introducing Auth0 Signals Community Version
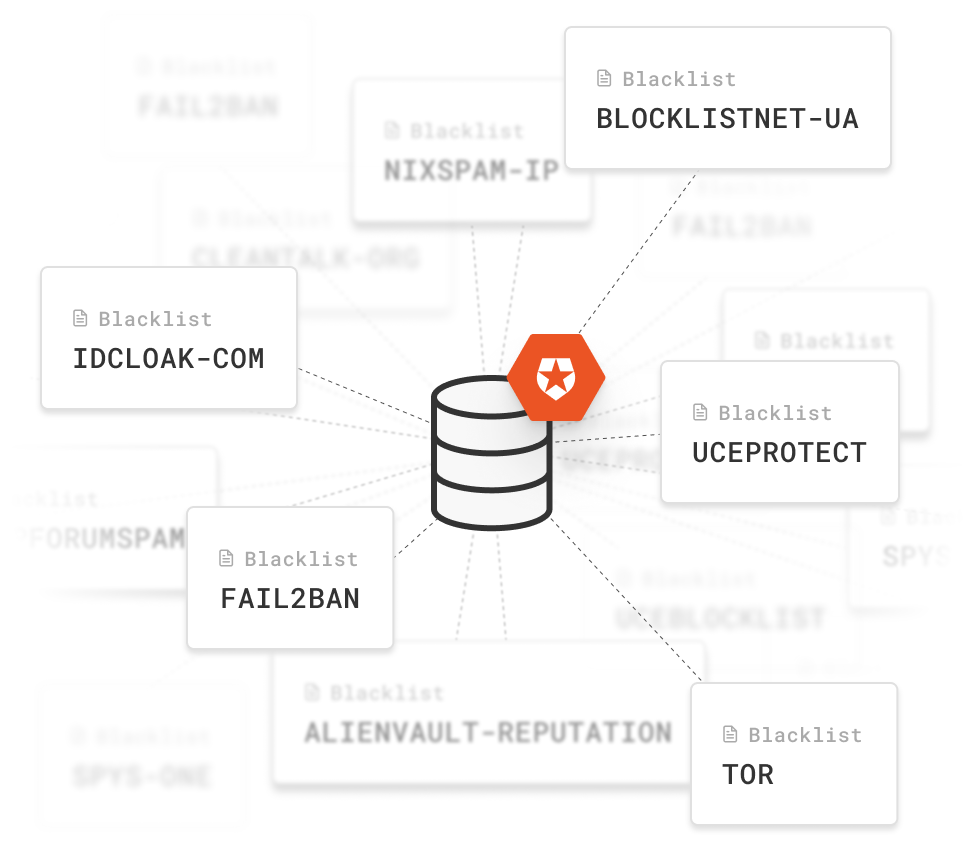
Today we are introducing a standalone community version of part of the signals we use in our pipeline. More specifically, the IP reputation signal. This comes from our acquisition of Apility.io and provides a continually curated and accurate IP, email, and domain reputation data. It takes the hard work out of consuming Open-Source Intelligence (OSINT) by curating, parsing, and normalizing numerous blacklists from across the dark web. We use this data to protect our own infrastructure.
Why Did We Build Auth0 Signals?
Auth0 Signals and anomaly detection are the foundation of developing a robust adaptive authentication system, ultimately enhancing our continuous authentication capabilities. The goal of adaptive authentication is to continually adapt to a changing threat landscape instead of using a simple rules-based system to block specific interactions.
For example, simple brute force protection usually relies on blocking high-velocity requests above a certain threshold, such as 100 authentication attempts per minute for a single IP address. The problem with this approach is threat actors can create scripts to identify this threshold and then adapt their botnet to operate below it. Effective adaptive authentication takes other risk signals into account, such as IP reputation data.
One of the most pressing threats Auth0 Signals will help address is credential stuffing attacks. In credential stuffing attacks, threat actors use stolen credentials from one breach to break into users' other accounts. This is effective because 65% of people reuse passwords across multiple accounts, according to Google. Even the largest companies are vulnerable if they don't have the right preventative measures in place.
As a central authentication service that processes billions of logins per month, we are in a good position to observe trends in credential stuffing attacks targeting our customers' identity implementations. On some days, these attacks originate from more than 50,000 IP addresses and may account for as much as half of all login attempts using our platform.
Auth0 Signals, coupled with the Anomaly Detection Engine, will detect these attacks with a high degree of efficacy early in the authentication pipeline. IP addresses identified as participating in a credential stuffing attack will be forced to solve a CAPTCHA, which addresses the vast majority of these attacks.
Try the API Now. It's Free!
Auth0 IP Signals will assist security analysts with incident response and forensic investigations, as well as provide application security engineers with proactive abuse prevention accessed via an API.
</div>
Incident response and forensics
When a security incident is identified, security analysts begin investigation and response processes to determine if a legitimate security incident occurred, the scope of the incident, and the best way to remediate the threat.
Using the Auth0 IP Signals tool, security analysts can submit IP addresses involved in such incidents to quickly identify traffic from known threat sources.
Abuse prevention
Using Auth0 IP Signals API, security professionals can detect malicious activity proactively, not reactively. For example, automatically checking IP reputation during the authentication flow can help prevent common threats, such as credential stuffing attacks.
Final Thoughts
Last year, I wrote about our vision for our identity platform and how we want to help security professionals by providing them with a single pane of glass that alerts them and self-remediates any sort of identity attack. This is a step towards fulfilling that vision. I am very excited about what's coming this year to help you all making your applications safer.
To try out Auth0 IP Signals, our first free Signals API, visit auth0.com/signals/ip