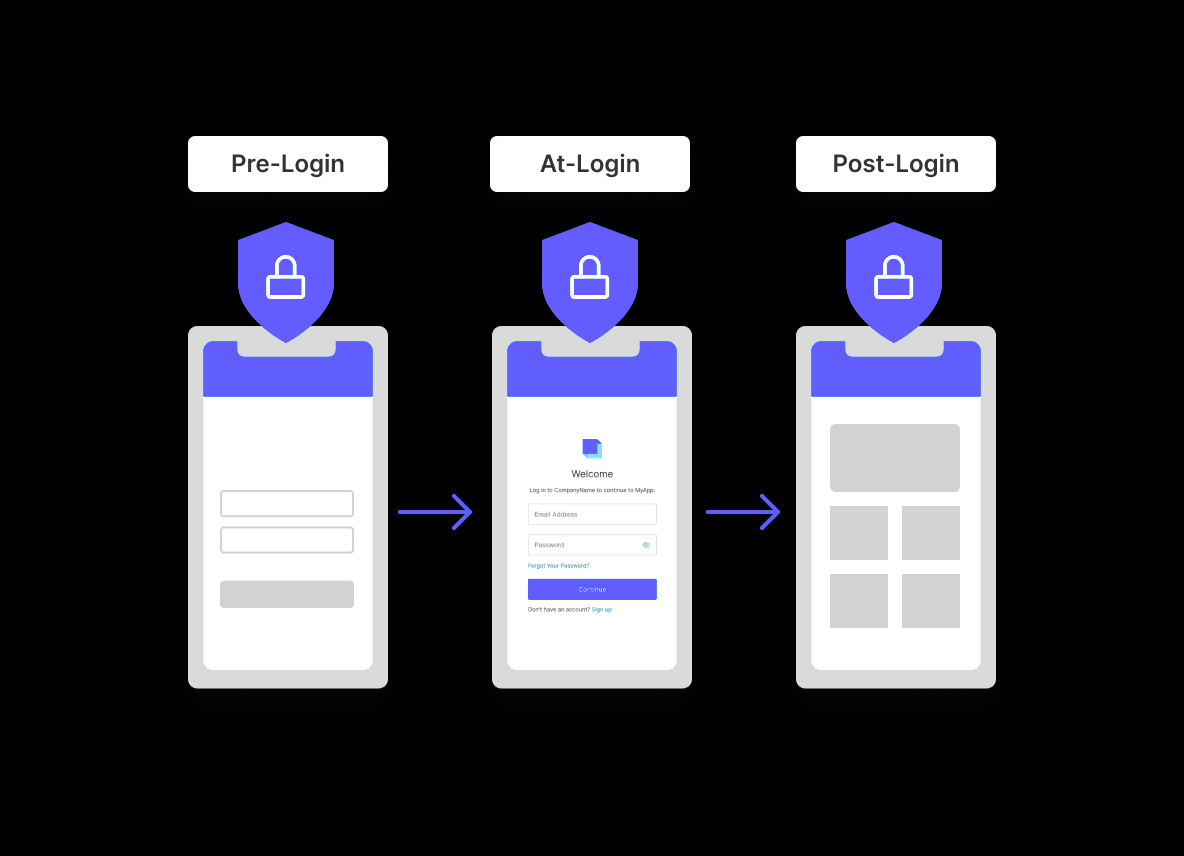
Protect Your Users with Attack Protection
Learn about attack protection and how you can shield your app from suspicious login activity.

What is Attack Protection?
Detecting unusual or alarming login behavior is vital to protecting your users. Attack Protection is the process of implementing controls that place friction in the path of the login experience for potential attackers and bad actors. Typically, this is achieved by identifying potential patterns of misuse, and then placing specifically controlled restrictions which take a variety of different forms. For example, certain outlier patterns detected during login can be identified - such as where access attempts occur from a particular place or device never seen before for a particular user. In such cases, additional controls can be deployed which attempt to restrict access via login challenges utilizing the likes of MFA or CAPTCHA.
Identifying Suspicious Activity
Have you ever received an email asking “was this you?” After logging into a website on a new computer or mobile phone? This is the result of attack protection. And there are a number of different login behaviors that could be considered suspicious - with some being higher risk than others. For example, a user logging in at an unusual time of day is typically a low-risk anomaly. A more threatening anomaly would be dozens of failed login attempts in a very short time. From brute force attack, to secure data breach (such as mass password leaks) and credential stuffing, effective attack protection should be there to notify an application owner of any anomalous behaviour. And also take specific action(s) to protect an end user account.
Implementing Attack Protection with Auth0
Auth0 provides multiple attack protection features - like Bot Detection - that can be easily deloyed right out of the box. And each of these features can be easily configured to detect different anomalous patterns during the login transactions.
Auth0 Attack Protection Features
Auth0 offers a layered approach to attack protection, with a wide range of detection and response tools. Auth0 can detect suspicious activity from bots, or login attempts that come at unusual velocities - e.g. where one or more accounts are the target of numerous brute force attacks within a short space of time. Or even if an attempt is made to use credentials known to be stolen in a data breach.
Stay Informed
Discover helpful CIAM articles that are timely and relevant, whatever your level of experience. Whether you prefer to learn by reading, viewing, listening, cloning repos, copying code, or attending a workshop or conference, our content is everywhere and made for developers like you.
Sign up for free
Start building today and secure your apps with the Auth0 identity platform today.