How it works
The Device Authorization Flow contains two different paths; one occurs on the device requesting authorization and the other occurs in a browser. The browser flow path, wherein a device code is bound to the session in the browser, occurs in parallel to part of the device flow path.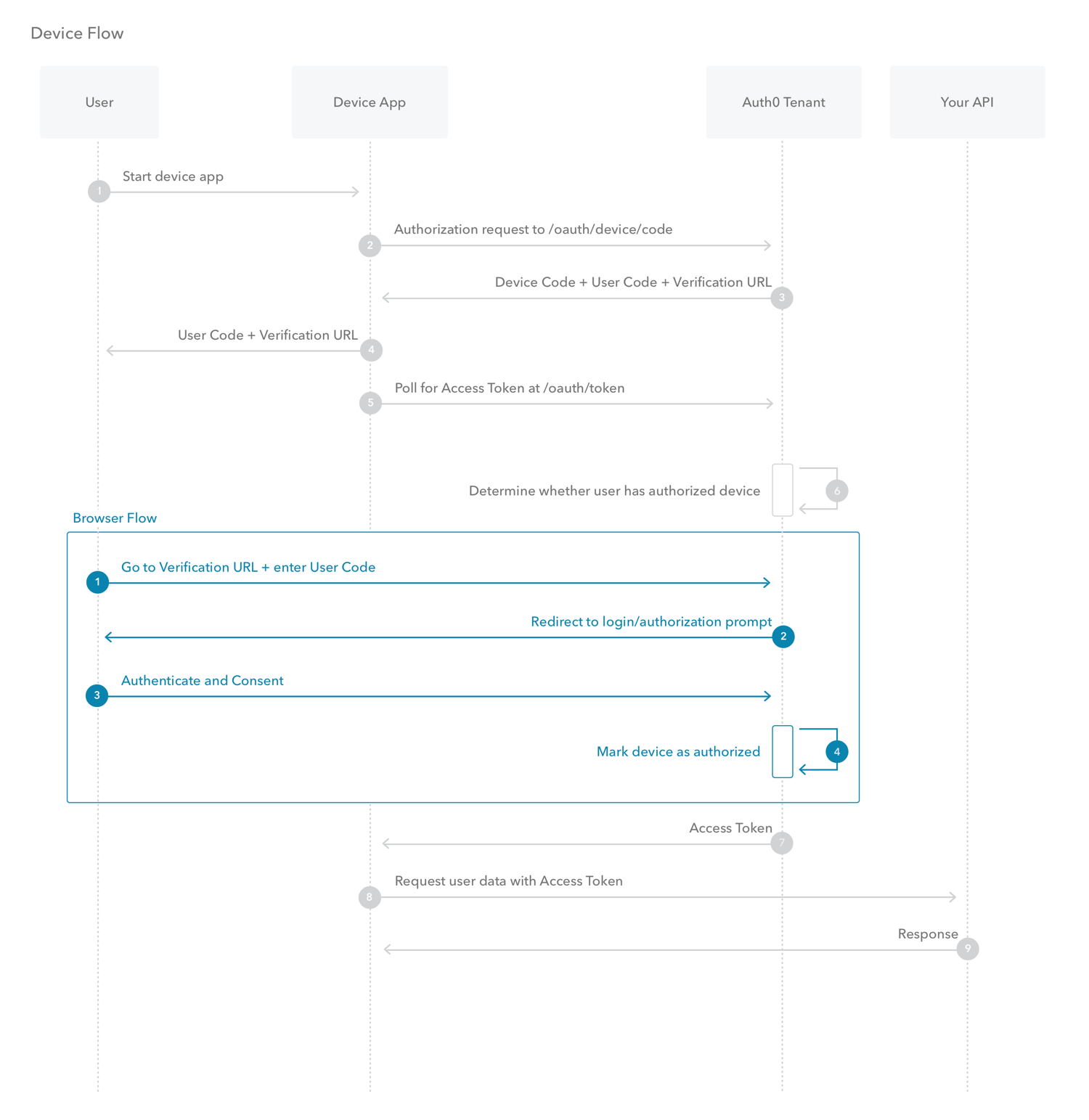
Device Flow
- The user starts the app on the device.
-
The device app requests authorization from the Auth0 Authorization Server using its Client ID (
/oauth/device/codeendpoint). -
The Auth0 Authorization Server responds with a
device_code,user_code,verification_uri,verification_uri_completeexpires_in(lifetime in seconds fordevice_codeanduser_code), and pollinginterval. -
The device app asks the user to activate using their computer or smartphone. The app may accomplish this by:
- asking the user to visit the
verification_uriand enter theuser_codeafter displaying these values on-screen - asking the user to interact with either a QR Code or shortened URL with embedded user code generated from the
verification_uri_complete - directly navigating to the verification page with embedded user code using
verification_uri_complete, if running natively on a browser-based device
- asking the user to visit the
-
The device app begins polling your Auth0 Authorization Server for an Access Token (/oauth/token endpoint) using the time period specified by
intervaland counting from receipt of the last polling request’s response. The device app continues polling until either the user completes the browser flow path or the user code expires. -
When the user successfully completes the browser flow path, your Auth0 Authorization Server responds with an Access Token (and optionally, a Refresh Token). The device app should now forget its
device_codebecause it will expire. - Your device app can use the Access Token to call an API to access information about the user.
- The API responds with requested data.
Browser Flow
- The user visits the
verification_urion their computer, enters theuser_codeand confirms that the device that is being activated is displaying theuser_code. If the user visits theverification_uri_completeby any other mechanism (such as by scanning a QR code), only the device confirmation will be needed. - Your Auth0 Authorization Server redirects the user to the login and consent prompt, if needed.
- The user authenticates using one of the configured login options and may see a consent page asking to authorize the device app.
- Your device app is authorized to access the API.

