- Enable Token Vault for a supported social or enterprise connection.
- Configure your application with the Token Vault grant type.
- Configure the token exchange for your application:
- Manage tokensets within the Token Vault for your connection.
If you have previously set your MFA policy to Always in the Auth0 Dashboard, you need to set it to Never to retrieve an access token from Token Vault. Otherwise, you will receive an error. To learn more about the different MFA policies, read Enable MFA in the Auth0 Dashboard.If you need to trigger MFA challenges for interactive flows, enable Customize MFA Factors using Actions when setting up MFA for your tenant. You can then use an Action to trigger an MFA challenge based on the
event.transaction.protocol property. To learn more, read Customize MFA selection for Universal Login.Configure connection
Use the or to configure a supported social or enterprise connection to retrieve and store access tokens for external APIs in the Token Vault. Once you enable Token Vault for your connection, access and will no longer be stored in the user’sidentities array. Instead, they will be stored in a secure within the Token Vault. To learn more, read Manage tokensets.
- Auth0 Dashboard
- Management API
To enable Token Vault for a supported social and enterprise/custom connection: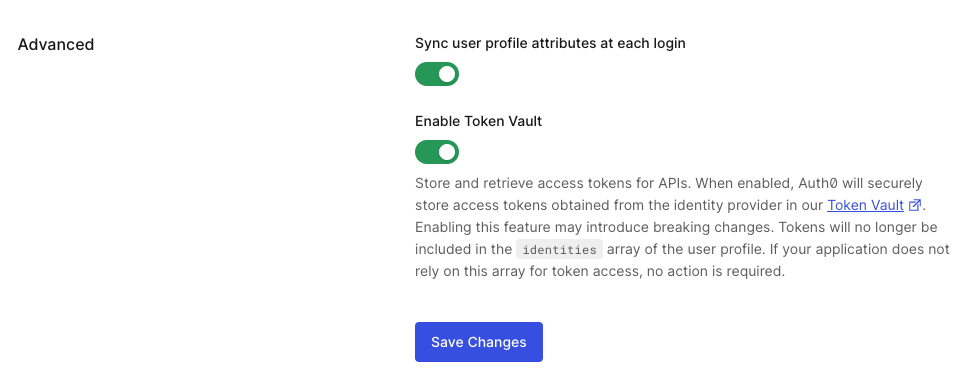
- Navigate to Authentication > Social Connections or Enterprise Connections.
- Select Create Connection or select an existing connection.
- In Permissions, select the desired scopes for your connection. You can filter by scope name or keywords. Whenever the user is redirected to authorize this connection, Auth0 always requests the scopes you selected. At runtime, this list is automatically completed with any additional scopes included in the
connection_scopeparameter of the authorization request. - In Advanced, toggle Enable Token Vault.
- Select Save Changes.

Configure application
Configure your application with the Token Vault grant type using the Auth0 Dashboard or Management API. Only certain types of clients can use the Token Vault grant type:- The client must be a first-party client, i.e. the
is_first_partyproperty istrue. - The client must be a confidential client with a valid authentication mechanism, i.e. the
token_endpoint_auth_methodproperty must not be set tonone. - The client must be OIDC conformant, i.e. the
oidc_conformantmust betrue.
- Auth0 Dashboard
- Management API
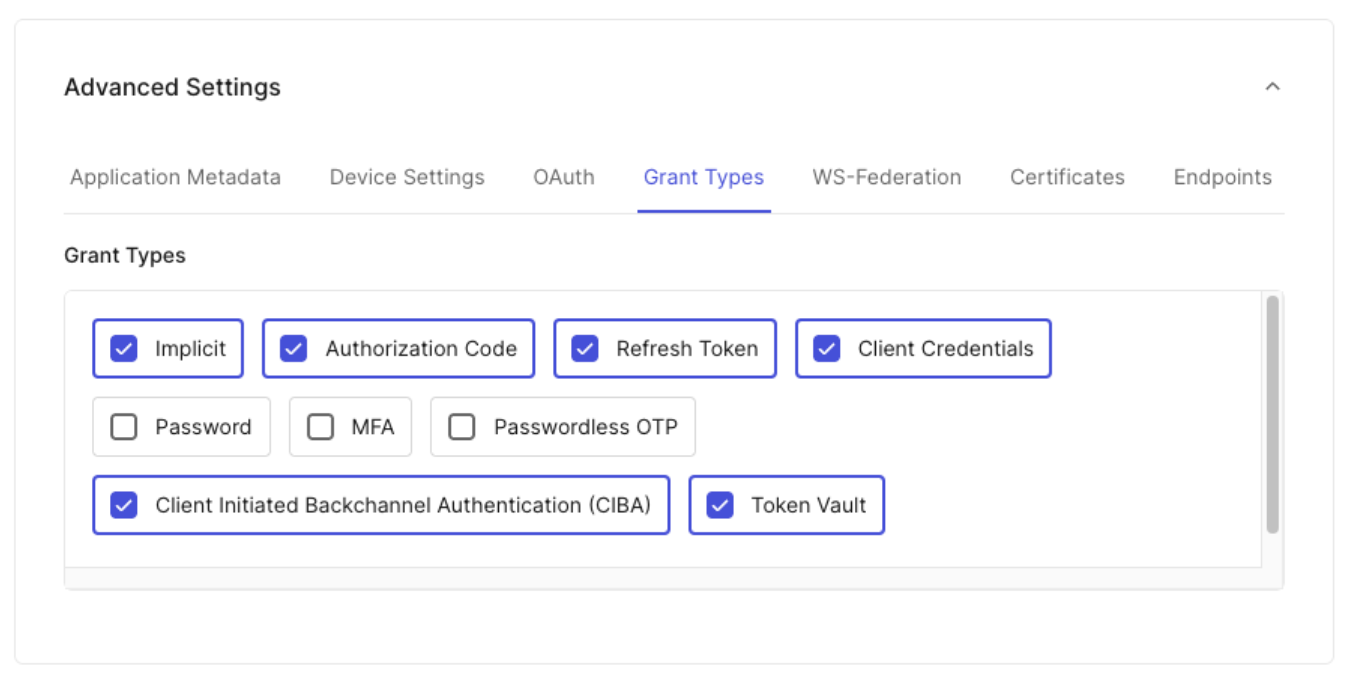
- Navigate to Applications > Applications.
- Select the application you want to configure.
- Under Advanced Settings > Grant Types, select the Token Vault grant type.
- Select Save Changes.
Manage tokensets
For each user’s authorized connection, like Google or Microsoft, Token Vault creates a secure container called a tokenset. A tokenset contains the access and refresh tokens needed to call that external provider’s APIs on the user’s behalf. To manage tokensets for a user, use the Management API:Get user’s tokensets
To get a user’s tokensets, you need a Management API access token with theread:federated_connections_tokensets scope.
Make a GET request to the /federated-connections-tokensets endpoint:
last_used_at is updated max once per day.
Delete a tokenset
To delete a tokenset, you need a Management API access token with theupdate:federated_connections_tokensets scope.
Make a DELETE request to the /tokensets endpoint:

