- Configure sender constraining for a client application
- Configure sender constraining for a resource server
How it works
are sender constrained in Auth0 depending on how you configure sender constraining for your client application and resource server:-
Requested audience: In a token request, whether the requested audience is
/userinfoonly, or only intended to be used with the/userinfoendpoint, or is a custom API that may include/userinfowhen you also request the openid scope, affects whether access tokens are sender constrained. -
Client application: Whether you set sender constraining as
requiredby the client application. -
Resource server: Whether you configure sender constraining for the resource server:
none: You have not configured sender constraining for the resource server.allowed: You have configured sender constraining for the resource server by setting a sender constraining method.required: You have configured sender constraining as required for the resource server, meaning that access tokens must be sender-constrained to an application. Requires a sender constraining method.
-
Proof-of-Possession: Whether the client application sent a proof-of-possession assertion in the token request:
- mTLS sender constraining: The proof of possession is demonstrated through the client’s successful presentation of a specific private key (associated with a client certificate) during the TLS handshake.
- DPoP: The proof of possession is achieved by the client creating a DPoP Proof JWT by cryptographically signing it with its private key and including the
DPoPProof JWT in the DPoP HTTP header of every request where the associated access token is used.
| Requested Audience Type | Client Requires PoP? | Proof-of-Possession (PoP) Sent by Client? | Auth0 Resource Server Policy: None | Auth0 Resource Server Policy: Allowed (Not Required) | Auth0 Resource Server Policy: Required |
|---|---|---|---|---|---|
| Userinfo Only | No | No | Issued, Not Sender-Constrained | N/A | N/A |
| Userinfo Only | No | Yes | Issued, Sender-Constrained | N/A | N/A |
| Userinfo Only | Yes | No | Not Issued | N/A | N/A |
| Userinfo Only | Yes | Yes | Issued, Sender-Constrained | N/A | N/A |
| Custom Audience (may contain Userinfo) | No | No | Issued, Not Sender-Constrained | Issued, Not Sender-Constrained | Not Issued |
| Custom Audience (may contain Userinfo) | No | Yes | Issued, Not Sender-Constrained | Issued, Sender-Constrained | Issued, Sender-Constrained |
| Custom Audience (may contain Userinfo) | Yes | No | Not Issued | Not Issued | Not Issued |
| Custom Audience (may contain Userinfo) | Yes | Yes | Not Issued | Issued, Sender-Constrained | Issued, Sender-Constrained |
Configure sender constraining for a client application
When you require sender constraining for a client application, access tokens are constrained to that application. Auth0 verifies requests to ensure that only the application that requested the token can use it to access the associated resource. Once you configure a client application to require sender constraining, you can set the sender constraining method, either mTLS or DPoP, when configuring your resource server. You can configure sender constraining for a client application with the or .- Auth0 Dashboard
- Management API
- Go to Dashboard > Applications > Applications. Select the application you want to configure.
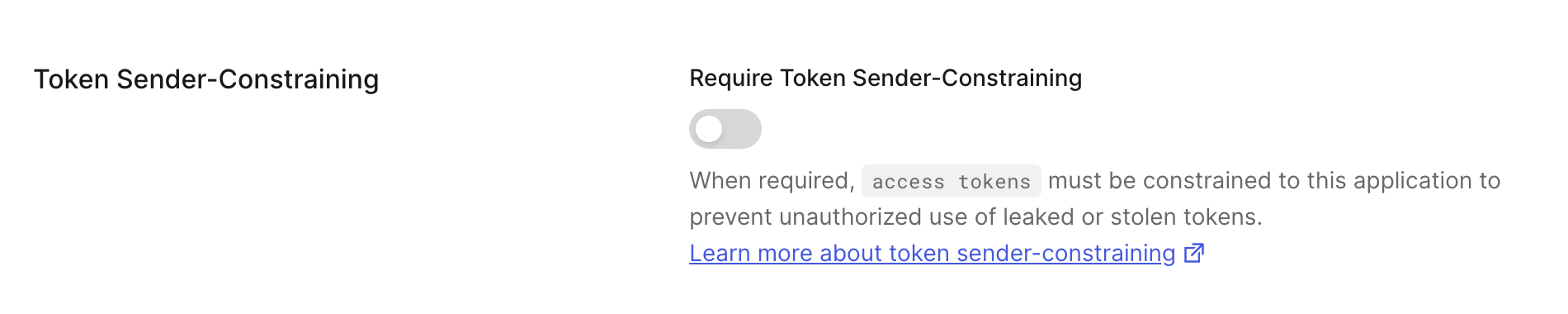
- Under Settings, scroll to Token Sender-Constraining.
- Toggle on to Require Sender Constraining. Toggle off to remove the requirement for Sender Constraining for the application.
Configure sender constraining for a resource server
Access tokens issued by Auth0 can be constrained to the sender (i.e. the client application) that needs to access APIs at a resource server. You can configure sender constraining for a resource server with the Auth0 Dashboard or Management API.- Auth0 Dashboard
- Management API
To enable Token Binding or sender constraining, configure the API Settings of your API.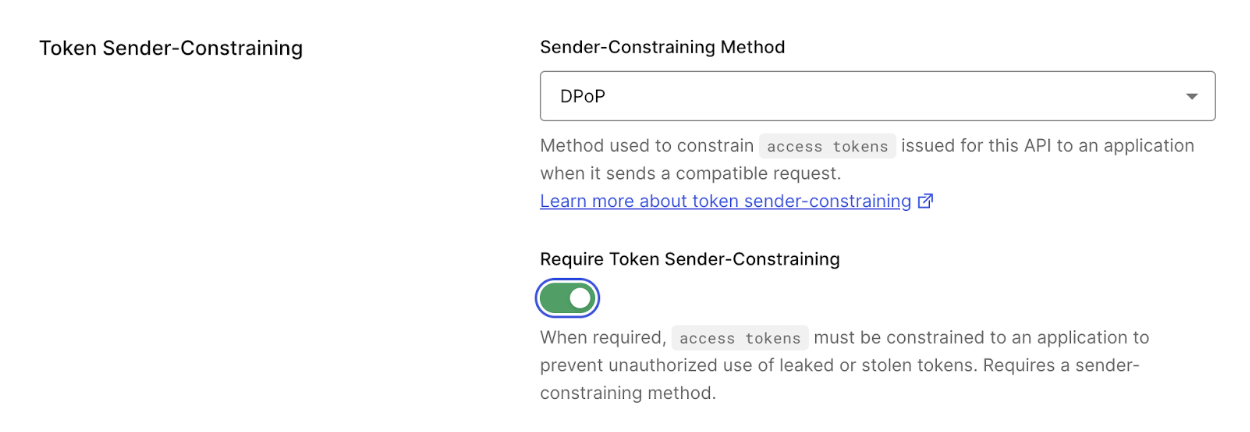
- Navigate to Auth0 Dashboard > Applications > APIs.
- Select the API you want to configure.
- Under the Settings tab, find the Token Sender-Constraining section.
-
Configure the following:
-
Sender Constraining Method:
- None: Don’t enable a sender constraining method for your resource server.
- mTLS: Enable mTLS as the sender constraining method for your resource server.
- DPoP: Enable DPoP as the sender constraining method for your resource server.
-
Sender Constraining Method:


