To use Highly Regulated Identity features, you must have an Enterprise Plan with the Highly Regulated Identity add-on. Refer to Auth0 Pricing for details.
Prerequisites
To implement mTLS sender constraining, you must:- Have an Enterprise Plan with the Highly Regulated Identity add-on for your Auth0 tenant.
- Configure sender constraining for your client application and within Auth0.
- Ensure your client application is a , as only confidential clients support mTLS sender constraining.
How it works
This section outlines the process of obtaining and using an mTLS-bound access token.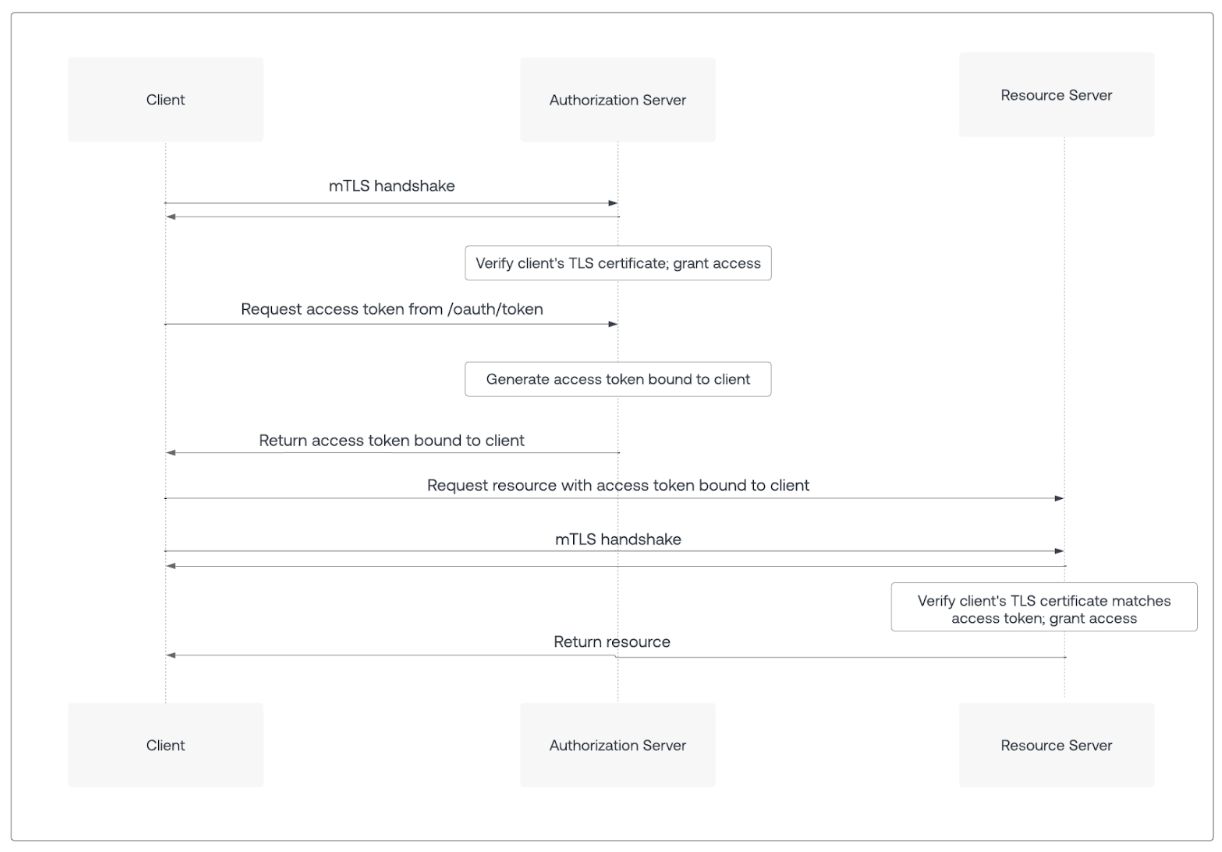
Phase 1: Request an mTLS-bound access token
Step 1: Client application establishes mTLS connection
- Before requesting an access token, your client application initiates a TLS handshake with the Auth0 ’s
/tokenendpoint. - During this handshake, the client application presents its client certificate to the Auth0 Authorization Server as part of the mutual TLS authentication process.
Step 2: Client application requests access token
- The client application sends a standard OAuth 2.0 token request, such as using
grant_type=client_credentialsorauthorization_code, to the Auth0 Authorization Server’s/tokenendpoint. - The token request does not include any special DPoP headers or additional proof for mTLS. The proof of possession is derived directly from the mTLS connection.
Step 3: Auth0 Authorization Server processes request and binds token
When the Auth0 Authorization Server receives the token request over an mTLS connection and the client certificate is successfully validated:- Extracts certificate: The Auth0 Authorization Server extracts the client certificate used in the mTLS handshake.
- Calculates thumbprint: The Auth0 Authorization Server calculates a unique hash (thumbprint) of the client certificate.
-
Binds token: The Auth0 Authorization Server binds this client certificate’s thumbprint to the issued access token by including a confirmation claim (
cnf) in the access token’s payload.- The
cnfclaim contains thex5t#S256parameter, which is the Base64url-encoded SHA-256 thumbprint of the client certificate.
- The
-
Sets
token_type: The Auth0 Authorization Server sets thetoken_typeto DPoP. This differs from traditional Bearer tokens and signals that the token is bound to a specific key. - Issues token: The Auth0 Authorization Server issues the mTLS sender-constrained access token to your client application.
x5t#S256 indicates that the access token is bound to an mTLS client certificate with the SHA-256 thumbprint bwcK0esc3ACC3DB2Y5_lESsXE8o9ltc05O89jdN-dg2.
Phase 2: Call an API with an mTLS-bound access token
Step 4: Client application calls API
- When your client application needs to call an API that enforces mTLS sender constraining, it must establish a new mTLS connection with the resource server.
- During this mTLS handshake, the client application presents the same client certificate that was used to obtain the access token again.
- The client application then includes the mTLS-bound access token in the Authorization header of the API request using the DPoP authentication scheme:
While RFC 8705 allows for a Bearer scheme with mTLS-bound tokens, Auth0 recommends using DPoP to enforce mTLS-bound access tokens. This explicitly signals to the resource server to expect a cryptographically bound token.
Step 5: Resource server verifies token and certificate
When the resource server receives the API request over an mTLS connection:- Requests client certificate: The resource server retrieves the client certificate from the established mTLS connection.
-
Extracts token and cnf claim: The resource server extracts the access token from the
Authorizationheader and decodes its payload to find thecnf(confirmation) claim, specifically thex5t#S256value (the bound certificate’s thumbprint). - Calculates current certificate thumbprint: The resource server calculates the SHA-256 thumbprint of the client certificate received in the current mTLS connection.
-
Compares thumbprints (Proof-of-Possession verification): The resource server compares the newly calculated thumbprint with the
x5t#S256thumbprint from the access token’scnfclaim. -
Authorizes or rejects request:
- If the thumbprints match and other token validations, such as the expiration, audience, and issuer, pass, the request is authorized.
- If the client certificate was not sent, or its thumbprint does not match the one in the
cnfclaim, the resource server rejects the request with anHTTP 401 Unauthorizedstatus code and aninvalid_tokenerror code.
cnf claim, refer to RFC 8705: Mutual-TLS Client Certificate-Bound Access Tokens.
Important considerations
When implementing mTLS sender constraining, consider the following:- Confidential clients only: mTLS sender constraining is designed for and supported only by confidential clients, such as backend services, that can securely manage client certificates and establish mTLS connections. like SPAs and mobile apps should use DPoP.
- Certificate management: The security of your mTLS implementation relies heavily on your certificate management practices, such as how you provision, manage, and rotate client certificates.
- Infrastructure requirements: Implementing mTLS requires specific infrastructure, including proxies, load balancers, and APIs capable of terminating mTLS connections and passing client certificate information to the application or resource server.
- Resource server enforcement: When you enable mTLS sender constraining for an API in Auth0, the resource server must perform the thumbprint verification as described in Step 5.
- Migration strategies: If you are progressively migrating clients to use mTLS, consider exposing your API at two domains: one non-mTLS domain for existing clients and one mTLS-enabled domain for mTLS-capable clients. Alternatively, you could implement logic on a single domain to differentiate between mTLS and non-mTLS requests.
- Error handling: Implement robust error handling on the client and resource server to gracefully manage cases where certificates are missing, invalid, or do not match.

