Password Options in Auth0 Database Connections
When using passwords for authentication, you should enforce the creation of unique passwords. A strong password policy will make it difficult, if not improbable, for a bad actor to guess a password through either manual or automated means.
Important facets of strong passwords are their uniqueness and difficulty to guess. Auth0's password options for database connections allow you to force your users to make better decisions when choosing their passwords.
The Password Options area is located at Auth0 Dashboard > Authentication > Database. Choose the database connection you wish to update and select the Authentication Methods tab. In the Password section, select Configure.
The Password Policy settings page contains the ability to configure the Password Strength Policy as well as the following password options.
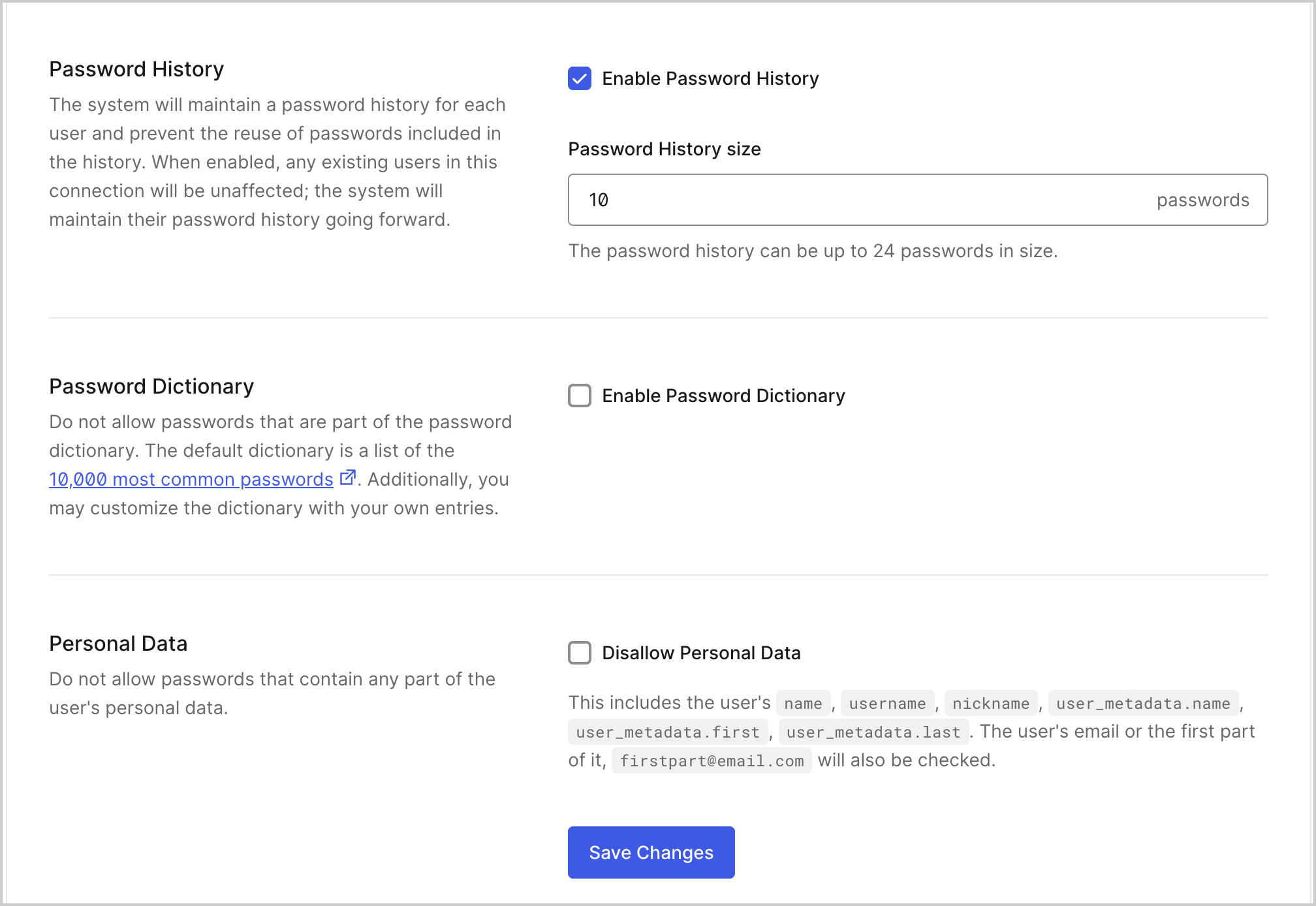
Password history
Enabling this option disallows users from setting passwords that repeat passwords they've used in the recent past. Auth0 can retain a password history for each user, up to a maximum of 24 entries per user. Note that when this option is enabled, only password changes going forward will be affected because the history will not have been kept prior to that point.
Even if you do not have a required password change policy (for example, forcing users to change passwords every six months), you still may want to disallow the use of previous passwords. For example, if a security breach in your organization causes you to force users to change their passwords everywhere, you will want to ensure they aren't just re-using passwords that might be compromised.
Password dictionary
Enabling this option disallows users from setting passwords to common options included in a default dictionary list. You may also include your own prohibited passwords by entering them in the text field in this section.
Note that Auth0 uses case-insensitive comparison with the Password Dictionary feature.
Personal data
Enabling this option disallows users from setting passwords that contain any part of their personal data. This includes:
nameusernamenicknameuser_metadata.nameuser_metadata.firstuser_metadata.lastThe first part of the user's email will also be checked -
firstpart@example.com
For example, if the user's name were "John", the user would not be allowed to include "John" in their password; John1234 would not be allowed.
API access
Because password options are associated with a Database connection, you can access them using the Management API's Connections endpoints. Password-related fields are stored in the options object. Because these fields are not used for non-database connections, they are not required, so if they are not enabled for a connection, they may not appear.
For example, after setting a password policy, a MySQL database connection will look like this:
{
"id": "con_9dKKcib71UMRiHHW",
"options": {
"password_history": {
"enable": true,
"size": 5
},
"password_dictionary": {
"enable": true,
"dictionary": [
"entry1",
"entry2"
]
},
"password_no_personal_info": {
"enable": true
},
"passwordPolicy": "fair"
},
"strategy": "auth0",
"name": "MySQL",
"enabled_clients": [
"smTzlgPEdqGV0i070t6kPhmG98787987",
"ztIyxRuiK7Pr2VTzEGvRqxfuh7DgePbF"
]
}Was this helpful?
In this example, we can see from the options object that all three password options are enabled, password history will store the 5 most recent passwords, and each password will be cross-checked against two dictionaries: entry1 and entry2.
If you are creating a connection or updating an existing connection using the Management API, you can update the password policy for the connection using these fields.