Database Connection
Using our Hoekstra & Associates example, the following diagram illustrates the flow typically encountered when dealing with a user authenticated via an Auth0 Database Connection. Let’s walk through this flow to see what occurs; note that most of the workflow described will typically be handled by using the relevant Auth0 SDK or library associated with your technology stack: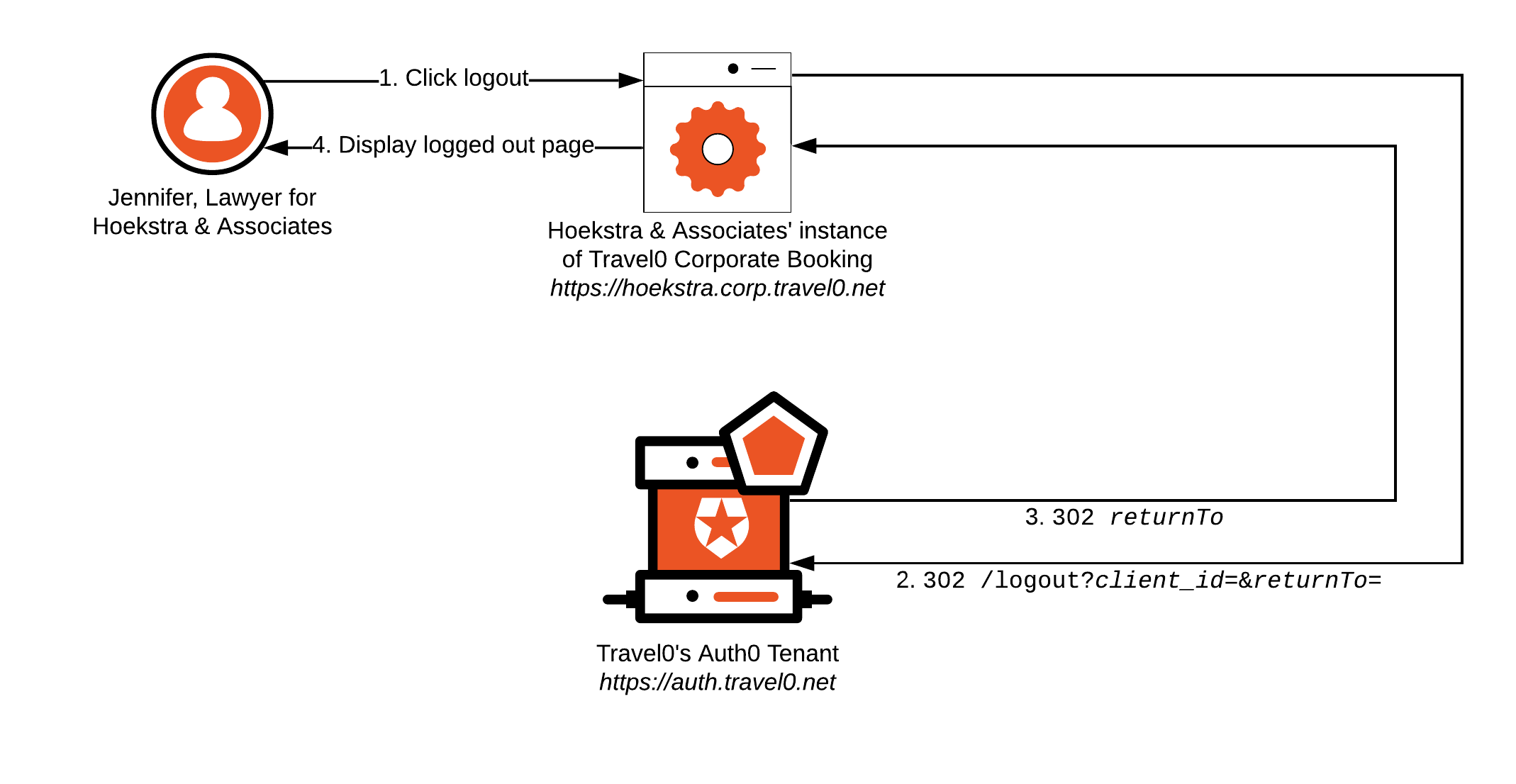
-
Jennifer clicks
logout. -
Hoekstra & Associates’ Instance of Travel0 Corporate Booking redirects the browser to the Travel0 Auth0 Tenant at https://auth.travel0.net with the following parameters:
-
returnTo:https://hoekstra.corp.travel0.net/logoutComplete -
client_id: Client ID associated with the Application created in the Travel0 Auth0 Tenant for the Hoekstra & Associates instance of Travel0 Corporate Booking.Best PracticeDefine Applications independently in Auth0 to make it easier to configure thereturnToURL where the correspondingclient_idis used to provide correct validation of the supplied URL. To learn more, see Provisioning.
-
-
The Travel0 Auth0 Tenant terminates the Auth0 session established on behalf of the user, removing any SSO information, and redirects the browser to the specified
returnToURL. -
The Hoekstra & Associates Instance of Travel0 Corporate Booking renders a page to let Jennifer know that she successfully logged out, likely with a button to log back in if desired.
- At this stage, the Travel0 Corporate Booking instance will typically want to clean up the application session associated with the user, too.
If you do not wish to remove the user’s SSO session with Auth0, then the application can simply terminate the application session without redirecting to the
/logout endpoint on the Auth0 Tenant. While the user will be logged out of the application, they will still have an SSO session with Auth0. In this case, you will likely want to tell the user that they are still logged in to the Auth0 Tenant, and that if they click login again, they may not be challenged to enter first-factor credentials.Enterprise Connection
For this scenario, implementing Logout can be a little more complex than it is when using a Database Connection. You still have the option to either logout from only the application or to have logout from the application result in logout from the Auth0 Tenant, too. However, you may also have the option of allowing logout from the organization’s (IdP), which most applications avoid, especially if users have access to other corporate applications to which they may need to stay logged in. Avoiding this, however, may result in users who subsequently click thelogin button being authenticated automatically without interactively providing first-factor credentials. Such functionality may make for an unexpected user experience, so you should consider communicating this to the user.
Using our MetaHexa Bank example, let’s see how this Logout implementation might flow with a user authenticated via an Enterprise Connection to MetaHexa Bank; again, most of the workflow described will typically be handled by using the relevant Auth0 SDK or library associated with your technology stack:
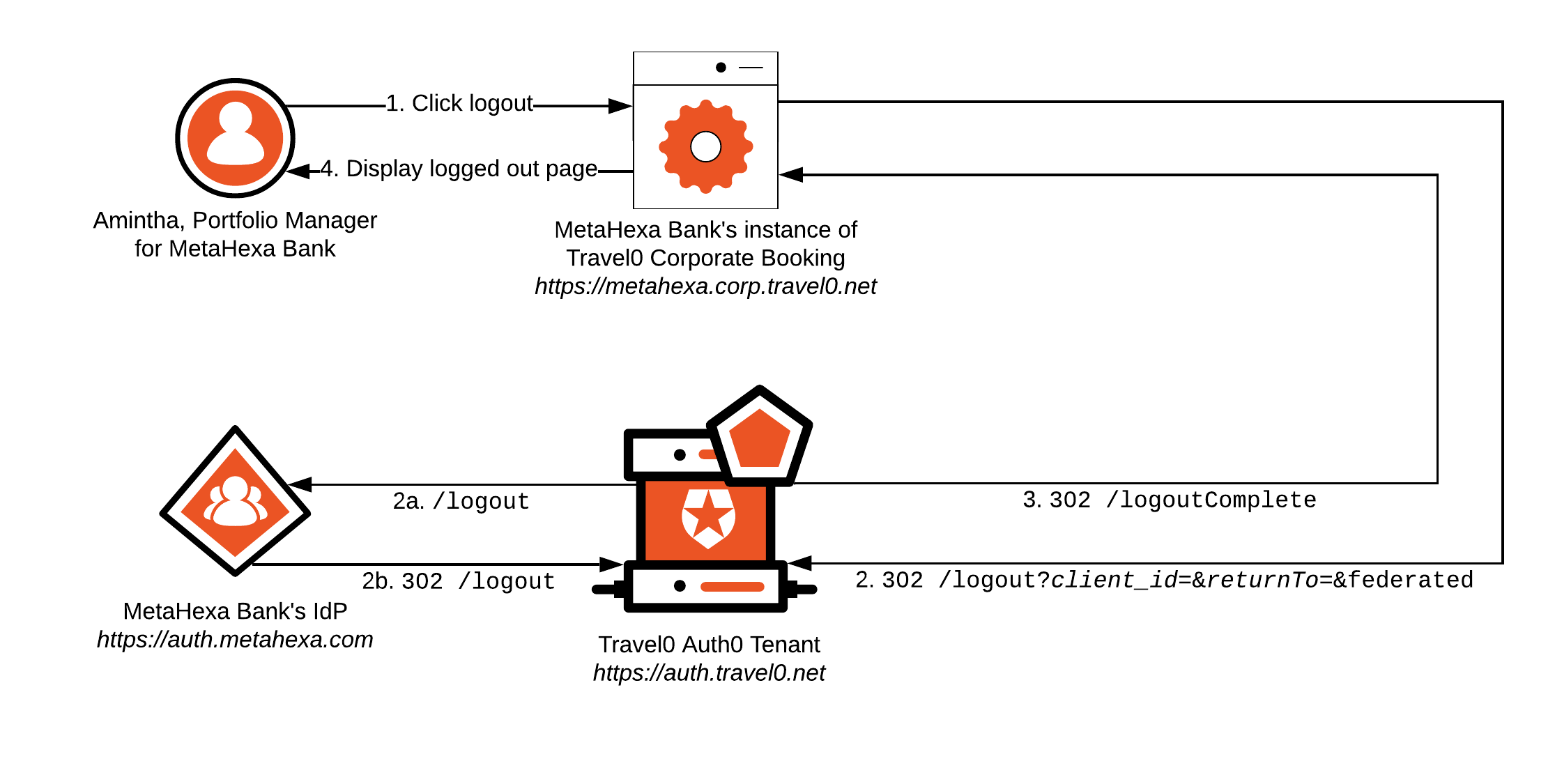
-
Amintha clicks
logout. -
MetaHexa Bank’s Instance of Travel0 Corporate Booking redirects the browser to the Travel0 Auth0 Tenant at https://auth.travel0.net with the following parameters:
-
returnTo:https://metahexa.corp.travel0.net/logoutComplete -
client_id: Client ID associated with the Application created in the Travel0 Auth0 Tenant for the MetaHexa Bank instance of Travel0 Corporate Booking. -
federated: Optional parameter used to log the user out of the MetaHexa Bank IdP. When specified, the browser is redirected to the/logoutendpoint associated with the MetaHexa Bank IdP, which terminates the user’s session before redirecting the browser back to the Travel0 Auth0 Tenant.Best PracticeDefine Applications independently in Auth0 to make it easier to configure thereturnToURL where the correspondingclient_idis used to provide correct validation of the supplied URL. To learn more, see Provisioning.
-
metahexa.corp.travel0.net) in place of Hoekstra & Associates.

