FIDO Authentication with WebAuthn
The Web Authentication API (also known as WebAuthn) is a specification written by the W3C and FIDO, with the participation of Google, Mozilla, Microsoft, Yubico, and others. The API allows users to be authenticated using public key cryptography.
WebAuthn is the most secure and usable authentication method on the web. Some key reasons for this are:
It minimizes login friction. A simple and familiar gesture lets users authenticate.
It's the only web authentication method that is phishing resistant.
It's standard based and implemented across browsers and operating systems
WebAuthn let users authenticate with two types of authenticators:
Roaming authenticators are removable and cross-platform, like a Yubikey, and can be used on multiple devices. To authenticate with a roaming authenticator, you need to connect it to the device (through USB, NFC, or Bluetooth), provide proof of presence (by touching it, for example), and optionally provide user verification, for example, by entering a PIN.
Platform authenticators are attached to a device and only work on that device. Some examples are MacBook’s TouchBar, Windows Hello, iOS Touch/FaceId, and Android’s fingerprint/face recognition. Biometric data is stored on the device and never sent to the server. When biometrics cannot be used, alternative authentication methods are usually provided. For example, if you are wearing a mask, instead of using Face ID you can enter your passcode.
WebAuthn and Web Origins
WebAuthn works by generating a private/public key pair for each web origin which are registered in the device or security key.
Since the key pair is bound to the domain, users are protected from phishing attacks. If the attacker tricks them into using WebAuthn in a different domain, the WebAuthn authenticator will not have a key pair for that domain and authentication will fail. The attacker will not get any data that can identify the user.
Roaming Authenticators
To learn how to enable roaming authenticators in Auth0, check the WebAuthn with Security Keys documentation.
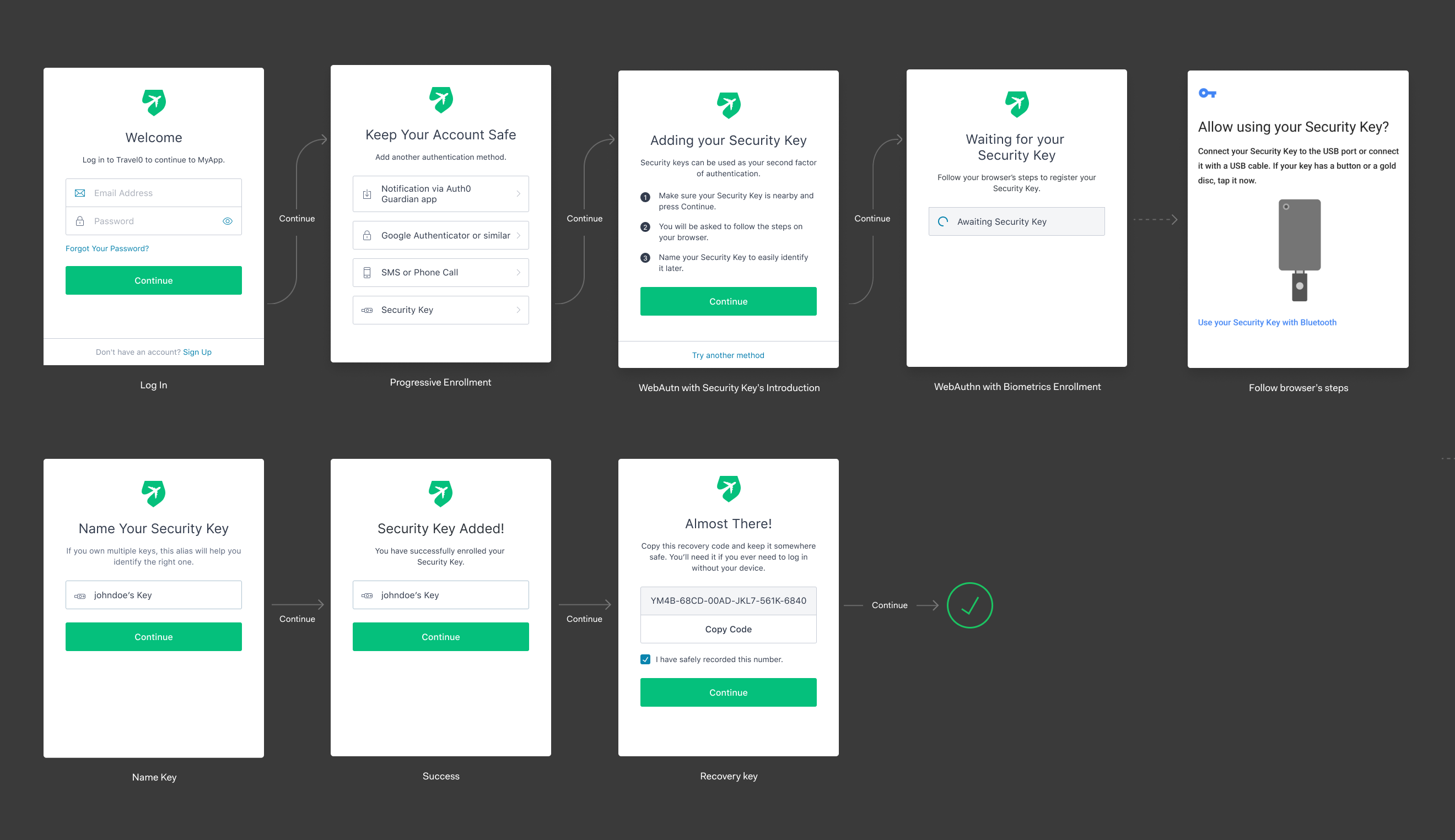
The default enrollment flow for security keys in Android displayed below and has the following steps:
Users authenticate with username/password.
They are prompted to select the authentication method they want to enroll.
If they pick Security Keys, they are shown a list of instructions.
They are then prompted to enter their security key.
The device shows their native UI to complete the security key challenge.
Users can name the key to later identify it, in case they enroll multiple ones.
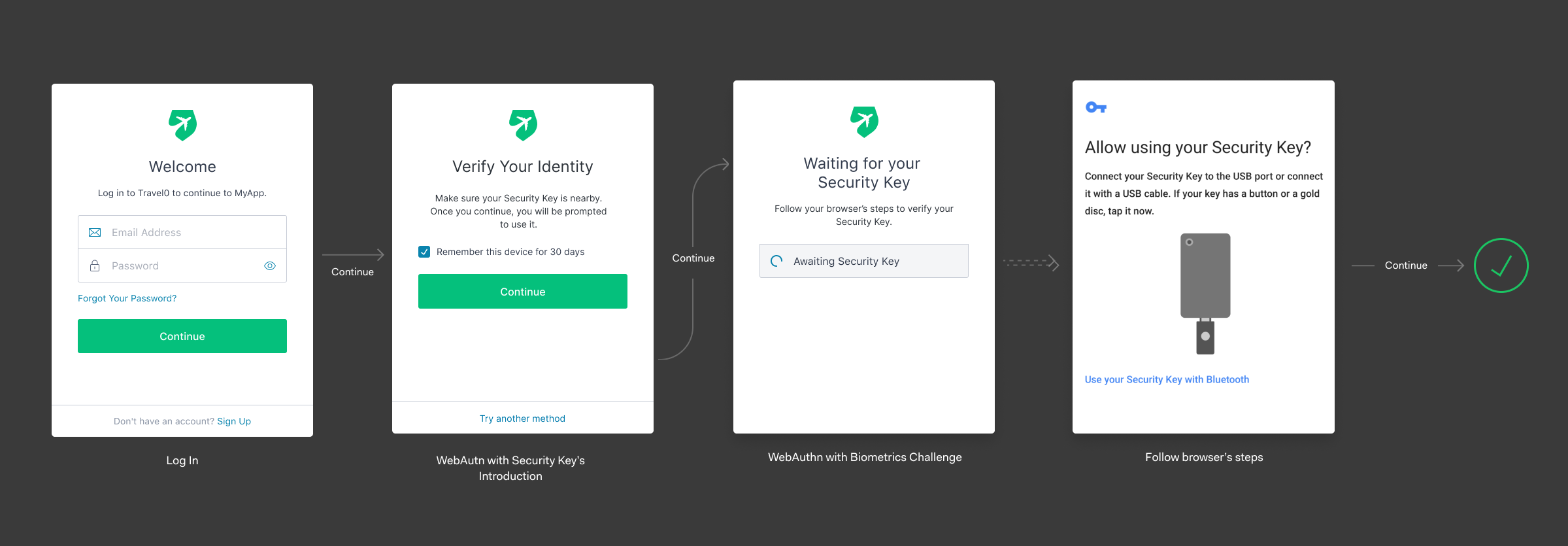
In the challenge flow, the user is prompted for the security key and then it calls the native user interface for the device, which in this example is Android:
Platform Authenticators
To learn how to enable platform authenticators, check the Webauthn with Device Biometrics documentation.
Given platform authenticators can only be used in a single device, it should not be the only factors that users enroll. To make sure users are not locked out from their accounts, Auth0 will prompt users to enroll with platform authenticators after they succesfuly authenticated using another authentication method.
Auth0 will try to progressively enroll all users' devices. Users will be prompted to enroll their devices' platform authenticators in each device they use.
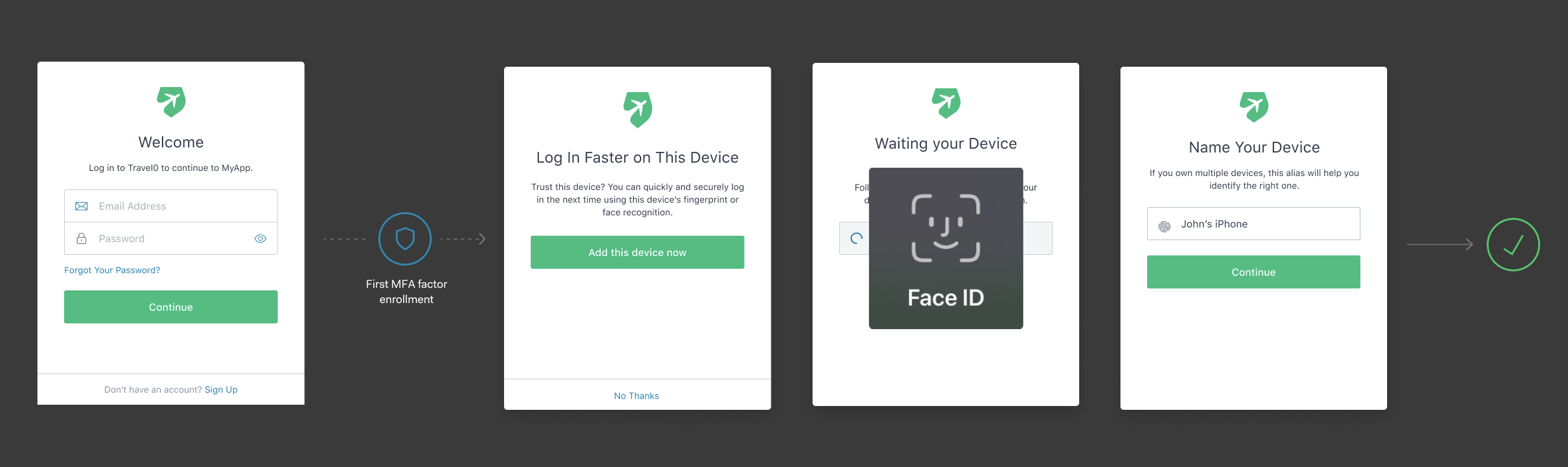
The default enrollment flow for Face ID in iOS is displayed below and has the following steps:
Users authenticate with username/password.
They enroll another MFA authentication method, like SMS, Push or Time-Based OTP.
They name their device, to identify it later.
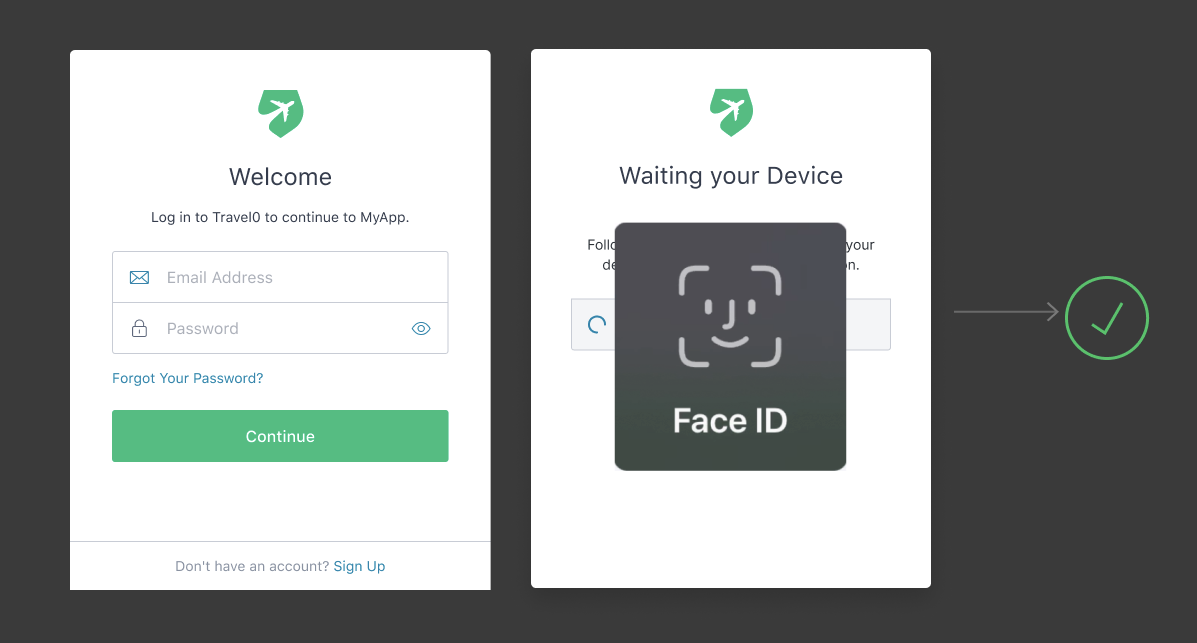
The next time they login from that device, users enter their username/password and complete MFA with their device biometric authenticator.
WebAuthn as Multi Factor Authentication
Webauthn.me
Auth0 maintains webauthn.me, which has detailed information about WebAuthn and an up-to-date list of browsers supporting WebAuthn.