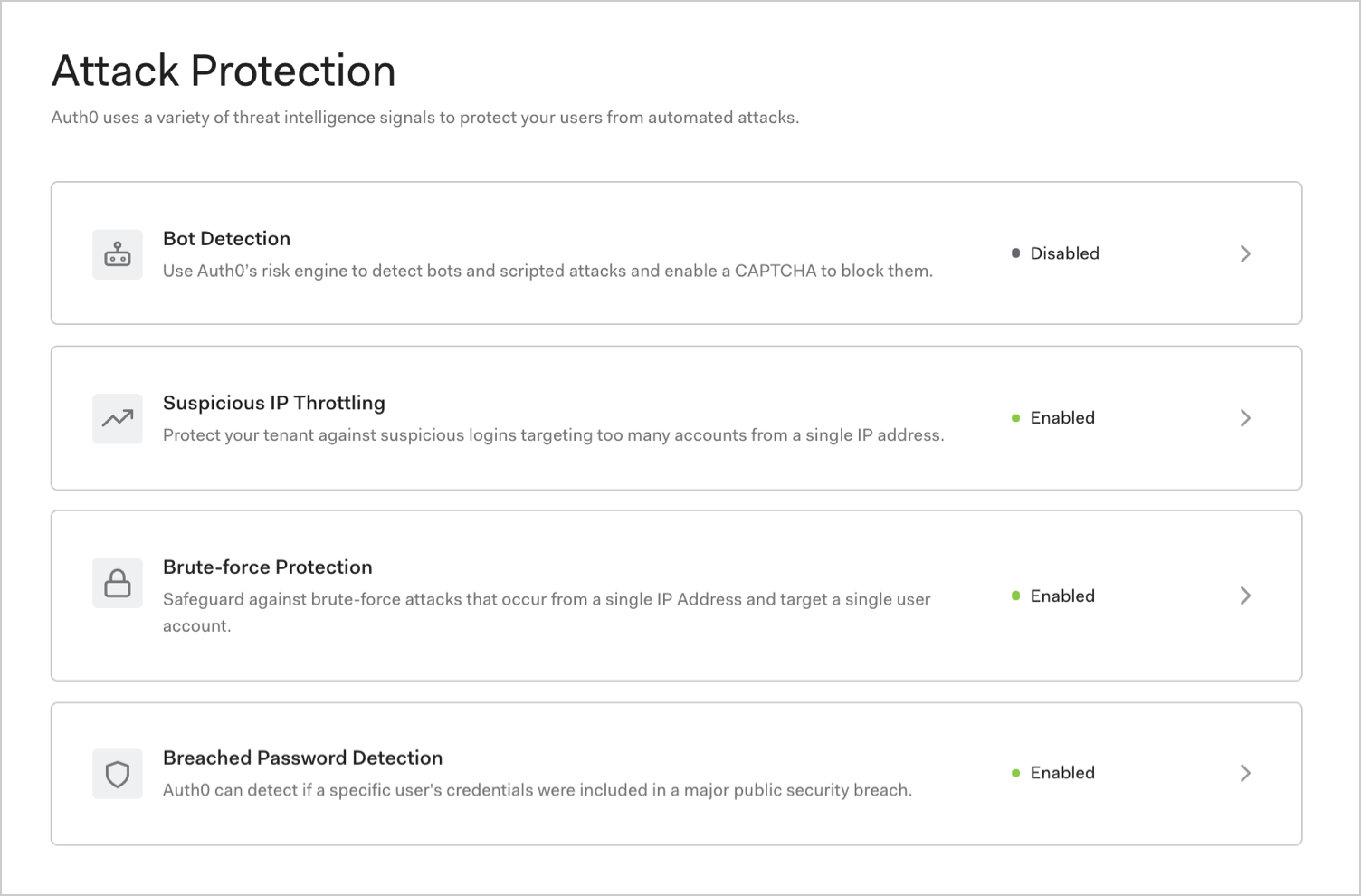
How it works
When it comes to combatting abuse, there is no silver bullet. Auth0 supports the principle of layered protection in security that uses a variety of signals to detect and mitigate attacks.| Feature | Risk signal | How it works |
|---|---|---|
| Bot Detection | IP reputation computed by analyzing the quality of traffic seen for each IP. | Triggers a CAPTCHA step when a login attempt comes from an IP suspected of use by a bot. |
| Suspicious IP Throttling | Velocity of login attempts from an IP for any number of accounts against a tenant. | Detects when a bot/script tries too many identifier/password combinations within a short period of time. |
| Brute-force Protection | Velocity of login attempts from an IP for a particular account. | Detects when a bad actor tries to login to an account too many times within a period of time. |
| Breached Password Detection | Use of a breached password that appears in lists of breached passwords on the dark web. | Stops users from using passwords that are known to be breached in some third-party sites. |
Notification
In the event of an attack, users will be notified by email once per hour regardless of the number of logins. For example, if a user tries to log in 200 times in 1 hour and 30 minutes, we will send 2 emails. Password reset links are valid for 5 days. You can customize the emails sent to your users.If you reset the block and it encounters another attack, it will send another email.

