- Block new users from signing up with stolen credentials. Entirely blocks the username/password combination.
- Block anyone from logging in with stolen credentials. Entirely blocks the account and prevents bad actors from accessing your application. The user can’t log in until they change their password.
- Send an email to the user when a login attempt happens. The email informs users about the risk and instructs them to change their password immediately. You can customize the message sent to users. To learn more, read Customize Blocked Account Emails.
Detect breaches faster with Credential Guard
Breached password detection relies on breach data released to the public. Credential Guard is an additional Auth0 service you can add to breach password detection that screens for breaches to allow faster notification of compromised credentials.| Breached Password Protection | Credential Guard | |
|---|---|---|
| Plans included | B2B / B2C Professional and Enterprise | Part of Attack Protection add-on in Enterprise plan |
| Data collection method | Web scanners and scrapers search for user credentials in published security breaches | Dedicated security team infiltrates criminal communities and gains access to breach data that isn’t otherwise available |
| Typical detection time | Up to 7-13 months | 12-36 hours |
| Coverage | English only | 200+ countries and territories |
Configure breached password detection
When enabled, you can customize breached password detection preferences, such as the detection method, response scenarios, and notifications.-
Go to Dashboard > Security > Attack Protection and select Breached Password Detection.
-
To turn on breached password detection, enable the switch at the top-right corner of the page.
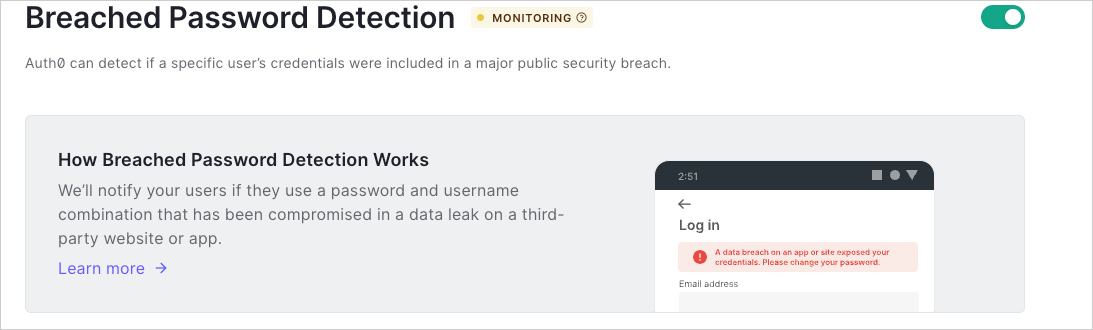 If you cannot see the toggle to enable tenant logs for Risk Assessment, you may need to upgrade your plan.
If you cannot see the toggle to enable tenant logs for Risk Assessment, you may need to upgrade your plan.
Configure detection method
Based on features available with your plan, you can configure the detection method used to identify compromised credentials.- Go to Dashboard > Security > Attack Protection and select Breached Password Detection.
- In the Detection section, locate Breached Password Detection Method.
- If your agreement with Auth0 includes Credential Guard, select As soon as possible based on data received from the dark web, with Credential Guard.
- Otherwise, leave When breach data is published selected.
- Select Save to apply changes.
Configure response scenarios
You can configure how Auth0 responds to different scenarios when users may provide compromised credentials.- Go to Dashboard > Security > Attack Protection and select Breached Password Detection.
-
Locate the Response section.
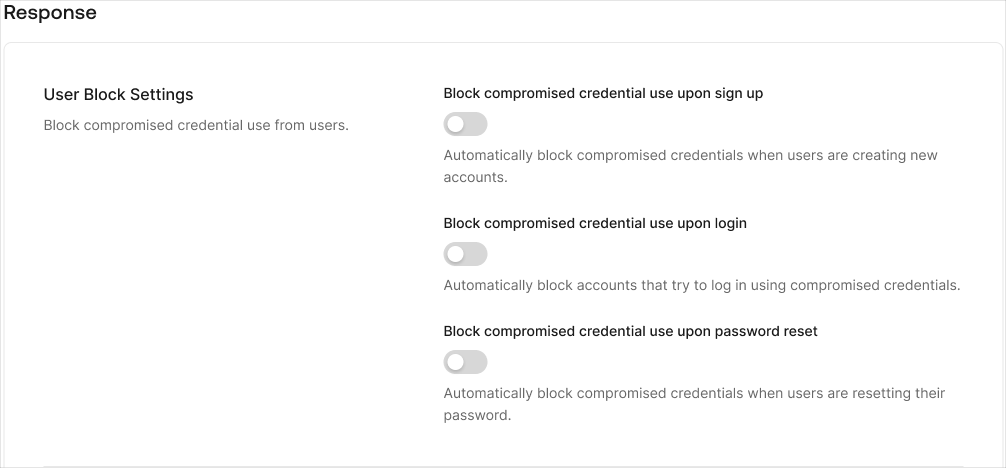
- Enable the Block compromised credentials for new accounts toggle to block users from using compromised credentials during signup.
- Enable the Block compromised user accounts toggle to block users from using compromised credentials during login.
- Enable the Block compromised credentials use for password reset toggle to block users from using compromised credentials upon password reset.
Configure notifications
You can configure how Auth0 notifies users and admins about the use of compromised credentials.- Go to Dashboard > Security > Attack Protection and select Breached Password Detection.
- Locate the Notifications section.
- Enable the Send notifications to users with compromised credentials toggle to send an email to a user when Auth0 detects their credentials may have been compromised.
- Enable the Compromised user accounts toggle to send an email to administrators when a user signs up with compromised credentials.
- Enable the Compromised user accounts toggle to send an email to administrators when a user logs in with compromised credentials.
- Choose the notification frequency: Immediately, Daily, Weekly, or Monthly.
- Select Save.
Customize email notifications to users
You can configure the notification Auth0 sends to your users when compromised credentials are used for login.- Navigate to Dashboard > Branding > Email Templates.
- In the Template dropdown menu, select Password Breach Alert.
- Update the template accordingly. You can use any of the available common variables to customize the message.
Verify detection configuration
You can verify your configuration by testing signup and login flows with an Auth0-provided breached password.Any password starting with
AUTH0-TEST- triggers Breached Password Detection for testing purposes.Signup flow
Verify a user’s signup experience when Auth0 detects a breached password:- Go through your signup flow and try to register a new account with a test breached password (
Paaf213XXYYZZorPaat739!!WWXXYYZZ) or any password starting withAUTH0-TEST-. - If Block compromised credentials for new accounts is enabled, you will receive an error message, preventing you from using the breached password.
- Navigate to Dashboard > Monitoring > Logs.
- Search the logs for
type: "signup_pwd_leak"to verify Auth0 blocked the signup.
Login flow
Verify a user’s login experience when Auth0 detects a breached password:- Create a test user in Dashboard > User Management > User, and assign a test breached password (
Paaf213XXYYZZorPaat739!!WWXXYYZZ) or any password starting withAUTH0-TEST-. - Go through your login flow and submit the identifier and password that you assigned.
- If Block compromised user accounts is enabled, the user will receive an error message, preventing them from logging in and advising to reset their password.
- Navigate to Dashboard > Monitoring > Logs.
- Search the logs for
type: "pwd_leak"to verify Auth0 blocked the login. - Navigate to Dashboard > User Management > User to delete the test user.
Reset flow
Verify a user’s password reset experience when Auth0 detects a breached password:- Create a test user in Dashboard > User Management > User.
- Go through your password reset flow and submit one of the test breached passwords (
Paaf213XXYYZZorPaat739!!WWXXYYZZ) or any password starting withAUTH0-TEST-. - If Block compromised user accounts is enabled, the end-user will receive an error message, preventing them from resetting their password and advising them to use another password.
- Navigate to Dashboard > Monitoring > Logs.
- Search the logs for
type: “reset_pwd_leak"to verify Auth0 blocked the password reset. - Navigate to Dashboard > User Management > User to delete the test user.

