Best PracticeWhile numerous authentication workflows are supported within Auth0, workflows using Auth0 Universal Login are considered both industry and Auth0 best practice because they provide optimal functionality and security. In particular, Universal Login provides Single Sign On (SSO) out of the box and helps mitigate attacks such as phishing and bucket brigade; for this reason, it should be preferred wherever password credentials are supplied by a user. Crucially, the New Universal Login Experience is also the only mechanism supported when using the Auth0 Organizations feature.
Auth0 supports only one authenticated user context per Auth0 Tenant; tenants cannot selectively switch between authenticated user contexts. Changing user context has an impact on any active SSO session, and this extends to the Auth0 Organizations feature. If per-organization contexts are absolutely necessary, then multiple Auth0 Tenants will need to be deployed to production. Because using multiple tenants has ramifications that affect Single Sign-On (SSO), user profile management, and so on, you should carefully consider before going down this route.
Database Connection
Using our Hoekstra & Associates example, let’s see how this Authentication implementation might flow with a user authenticated via an Auth0 Database Connection; most of the workflow described will typically be handled by using the relevant Auth0 SDK or library associated with your technology stack: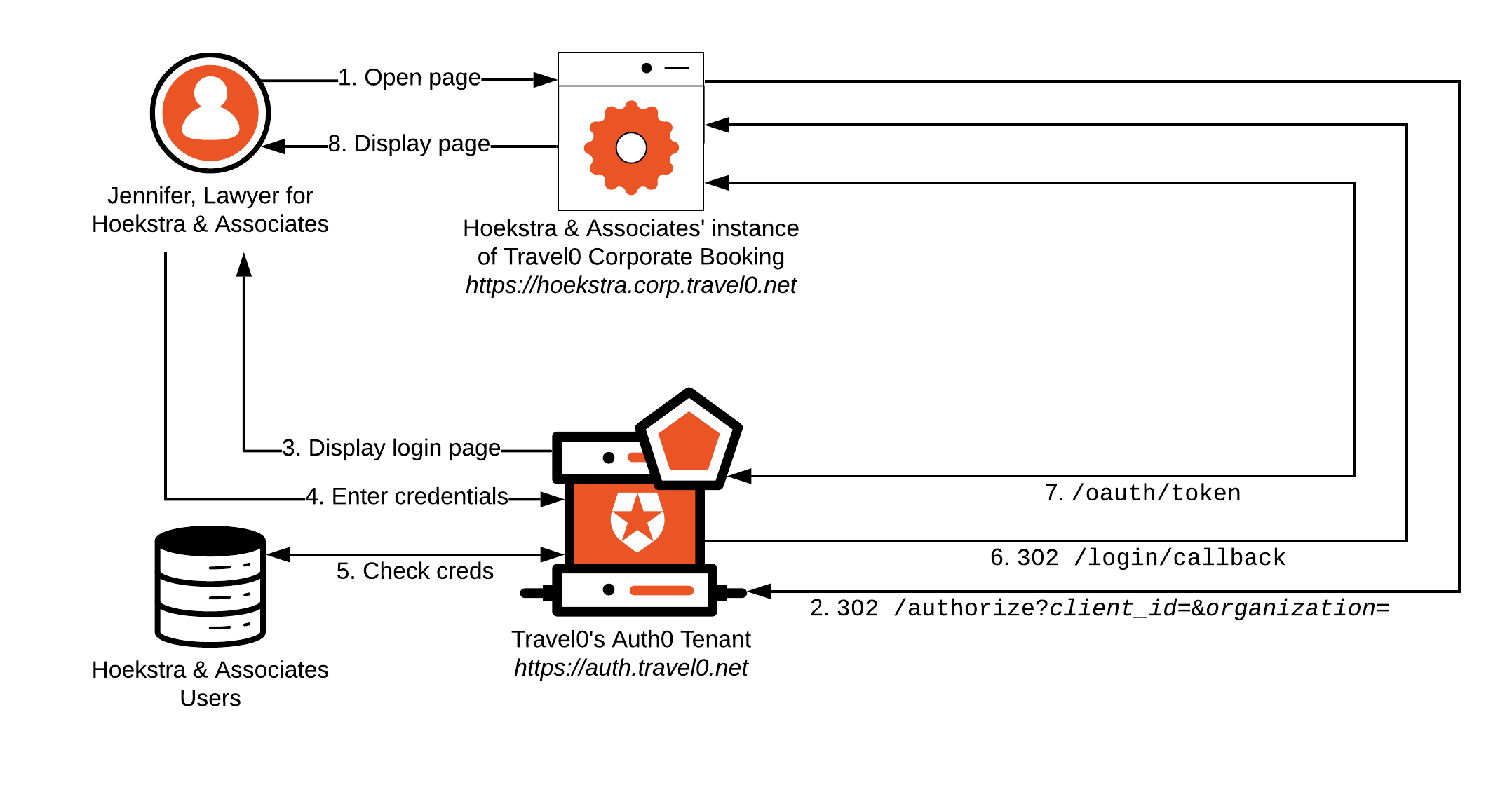
-
Jennifer from Hoekstra & Associates opens her browser and navigates to Hoekstra & Associates’ instance of Travel0 Corporate Booking.
- If Jennifer already has a session cookie with Hoekstra & Associates’ instance of Travel0 Corporate Booking, then she will typically be logged in to the system, and we will exit here. For more information, see Single Sign-On.
-
Hoekstra & Associates’ instance of Travel0 Corporate Booking redirects to the Travel0 Auth0 Tenant using Authorization Code Flow (with or without PKCE) by calling the
/authorizeendpoint and passing parameters, typically via use of an Auth0 SDK or third-party library:-
redirect_uri:https://hoekstra.corp.travel0.net/login/callback -
response_type:code -
state: Unique state generated in this session -
scope:openid profile… - any necessary additional OIDC Scopes, depending on the information required about the user.
-
client_id: Client ID associated with the Application created in the Travel0 Auth0 Tenant for Hoekstra & Associates’ instance of Travel0 Corporate Booking. -
organization: Auth0 Organization to use. Where the organization is known ahead of time, a request to/authorizecan include this parameter, which is specified in the formorganization=organization_id, where organization_id is set to the identifier associated with the corresponding Auth0 Organization definition in your Auth0 Tenant. Alternatively, you can omit theorganizationparameter from the call to/authorizeand configure your Auth0 Tenant to prompt the user to select the appropriate organization as part of first-factor authentication. For more information, see Define Organization Behavior.
-
-
The Travel0 Auth0 Tenant redirects to
/loginto collect credentials from the user. If Jennifer already has a Database session with Hoekstra & Associates, then steps 3a and 4 will be skipped. For more information, see Single Sign-On.- The Universal Login Page, which you can configure to include organization-specific brand collateral as described in Branding, is displayed.
-
The user enters their credentials and clicks
login. -
The Travel0 Auth0 Tenant checks the credentials for the user; if valid, the Rules pipeline executes. Rules can be used to handle access control as described in Authorization. If credentials for the user are invalid, then the user will be prompted to re-enter them.
Automatic membership assignment will be performed if this option has been specified. For more information, see Grant Just-In-Time Membership to an Organization Connection. For manually-assigned Membership, validation will fail if the user is not already assigned as a member of the Organization.
-
Upon successful first-factor authentication and Rules execution, the user is redirected to the
redirect_uri(https://hoekstra.corp.travel0.net/login/callback) with thestatepassed in step 2, as well as acode. -
Hoekstra & Associates’ instance of Travel0 Corporate Booking validates the
stateand then calls the Travel0 Auth0 Tenant athttps://auth.travel0.net/oauth/token, passing thecodeand itsclient idandclient secretin exchange for the ID Token. The ID Token is then used to generate a session forhttps://hoekstra.corp.travel0.net. - Hoekstra & Associates’ instance of Travel0 Corporate Booking instance displays the appropriate page to the user.
Enterprise Connection
Authenticating via an Enterprise Connection follows a very similar process. Using our MetaHexa Bank example, let’s see how this Authentication implementation might flow with a user authenticated via the Enterprise Connection to MetaHexa Bank; again, most of the workflow described will typically be handled by using the relevant Auth0 SDK or library associated with your technology stack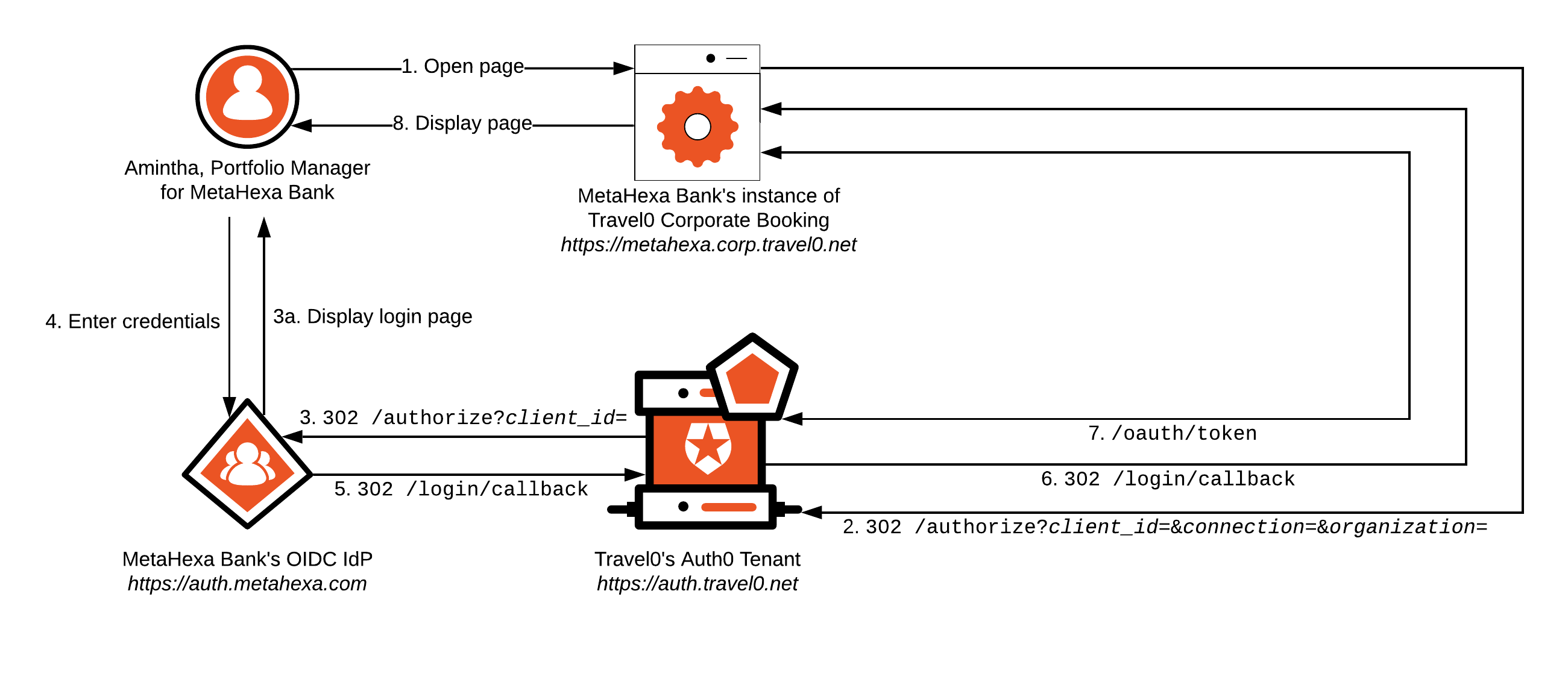
-
Amintha from MetaHexa Bank opens her browser and navigates to MetaHexa Bank’s instance of Travel0 Corporate Booking.
- If Amintha already has a session cookie with MetaHexa Bank’s instance of Travel0 Corporate Booking, then she will typically be logged in to the system, and we will exit here. For more information, see Single Sign-On.
-
MetaHexa Bank’s instance of Travel0 Corporate Booking redirects to the Travel0 Auth0 Tenant using Authorization Code Flow (with or without PKCE) by calling the
/authorizeendpoint and passing parameters, typically via use of an Auth0 SDK or third-party library:-
redirect_uri:https://metahexa.corp.travel0.net/login/callback -
response_type:code -
state: Unique state generated in this session -
scope:openid profile… - any necessary additional OIDC Scopes, depending on the information required about the user.
-
client_id: Client ID associated with the Application created in the Travel0 Auth0 Tenant for MetaHexa Bank’s instance of Travel0 Corporate Booking. -
organization: Auth0 Organization to use. Where the organization is known ahead of time, a request to/authorizecan include this parameter, which is specified in the formorganization=organization_id, where organization_id is set to the identifier associated with the corresponding Auth0 Organization definition in your Auth0 Tenant. Alternatively, you can omit theorganizationparameter from the call to/authorizeand configure your Auth0 Tenant to prompt the user to select the appropriate organization as part of first-factor authentication. For more information, see Define Organization Behavior. -
connection: Name of the configured Auth0 Enterprise Connection for MetaHexa Bank.Best PracticeAlways supply theconnectionparameter. When not provided, the user is prompted to select the Enterprise Connection associated with the upstream Identity Provider (IdP), which is an extra step from a UX perspective.
-
-
The Travel Auth0 Tenant redirects to the MetaHexa IdP to authenticate first-factor credentials.
- The login page is displayed, and the user enters credentials. If Amintha already has a session with the MetaHexa IdP, then steps 3a and 4 will be skipped. For more information, see Single Sign-On (SSO).
-
The user enters their credentials and clicks
login. - Upon successful first-factor authentication, the Rules pipeline executes. Rules can be used to handle access control as described in Authorization. If credentials for the user are invalid, then the user will be prompted to re-enter them.
Automatic membership assignment will be performed if this option has been specified. For more information, see Grant Just-In-Time Membership to an Organization Connection. For manually-assigned Membership, validation will fail if the user is not already assigned as a member of the Organization.
metahexa.corp.travel0.net) will be used in place of Hoekstra & Associates.

