What is identity and access management (IAM)?
Identity and access management provides control over user validation and resource access. Commonly known as IAM, this technology ensures that theright people access the right digital resources at the right time and for the right reasons.IAM basic concepts
To understand IAM, you must be familiar with some fundamental concepts:- A digital resource is any combination of applications and data in a computer system. Examples of digital resources include web applications, APIs, platforms, devices, or databases.
- The core of IAM is identity. Someone wants access to your resource. It could be a customer, employee, member, participant, and so on. In IAM, a user account is a . User accounts can also represent non-humans, such as software, Internet of Things devices, or robotics.
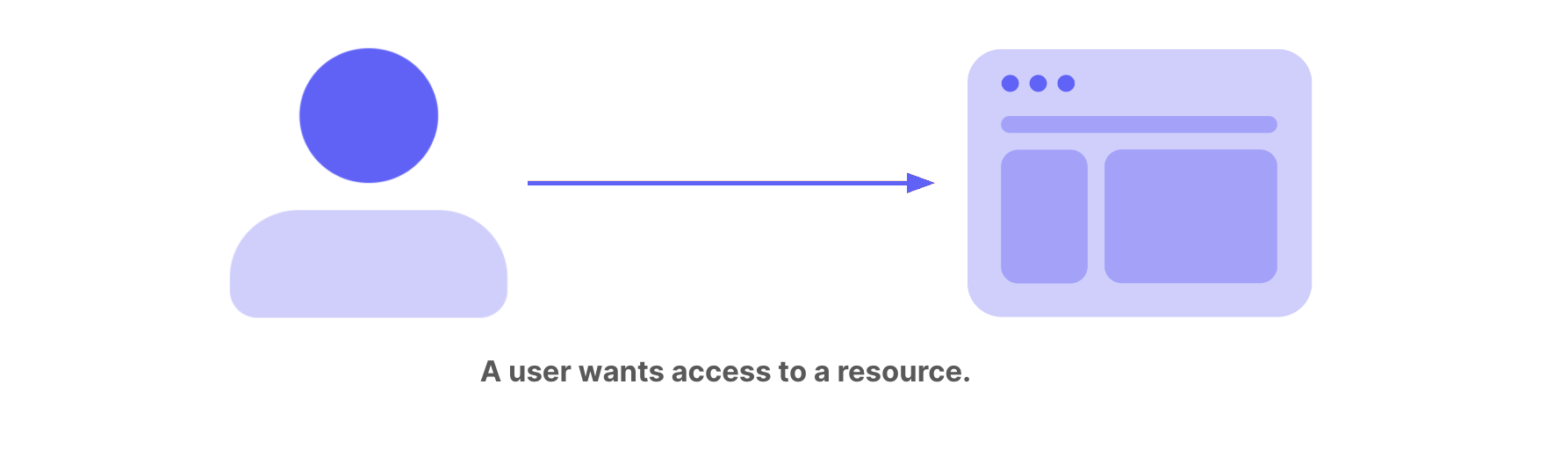
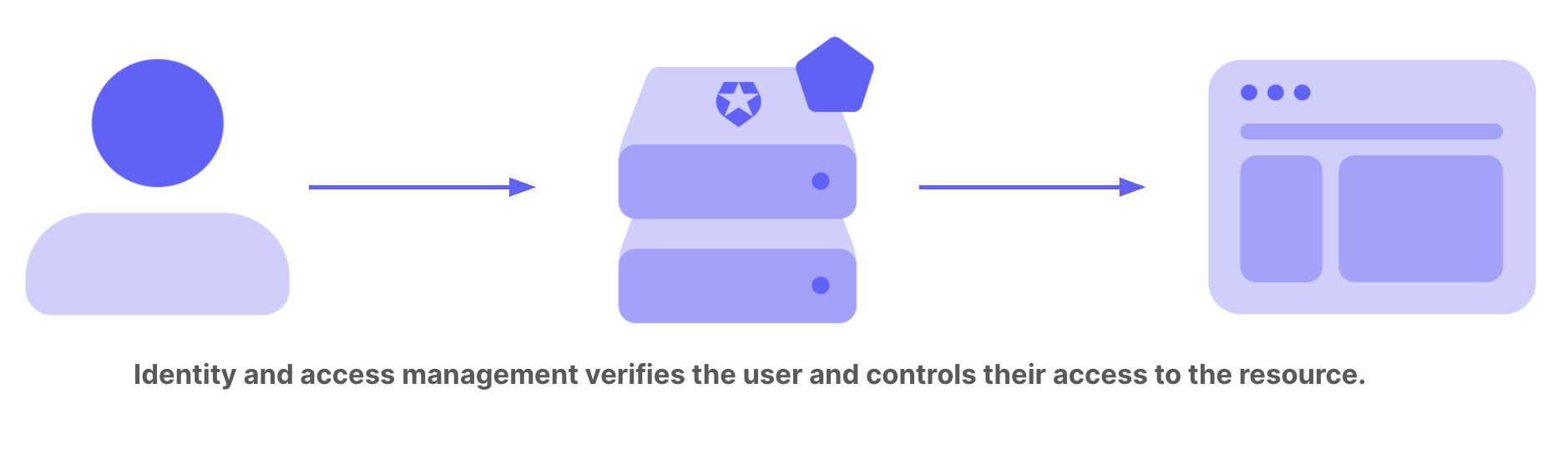
- Authentication is the verification of a digital identity. Someone (or something) authenticates to prove that they’re the user they claim to be.
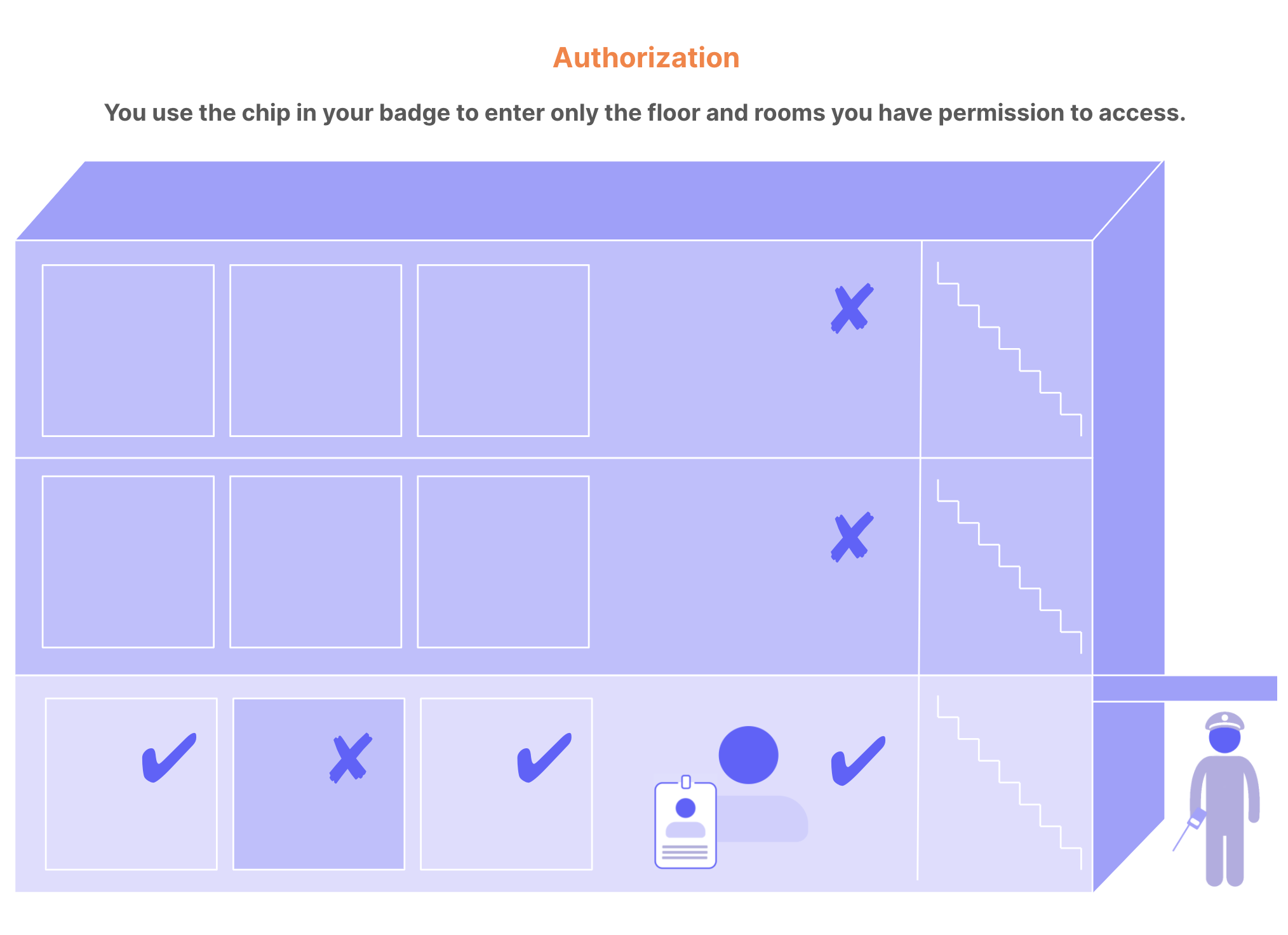
- Authorization is the process of determining what resources a user can access.
The difference between authentication and authorization
It’s common to confuse authentication and authorization because they seem like a single experience to users. They are two separate processes: authentication proves a user’s identity, while authorization grants or denies the user’s access to certain resources. You can think of authentication and authorization as the security system for an office building. Users are the people who want to enter the building. Resources that people want to access are areas in the building: floors, rooms, and so on. Authentication: When you enter the building, you must show your photo ID badge to the security guard. The guard compares the photo on the badge to your face. If they match, the guard lets you through the door to try to access different areas of the building. The guard doesn’t tell you what rooms you can access; they only get proof that you are who you claim to be. This is authentication: confirming user identity.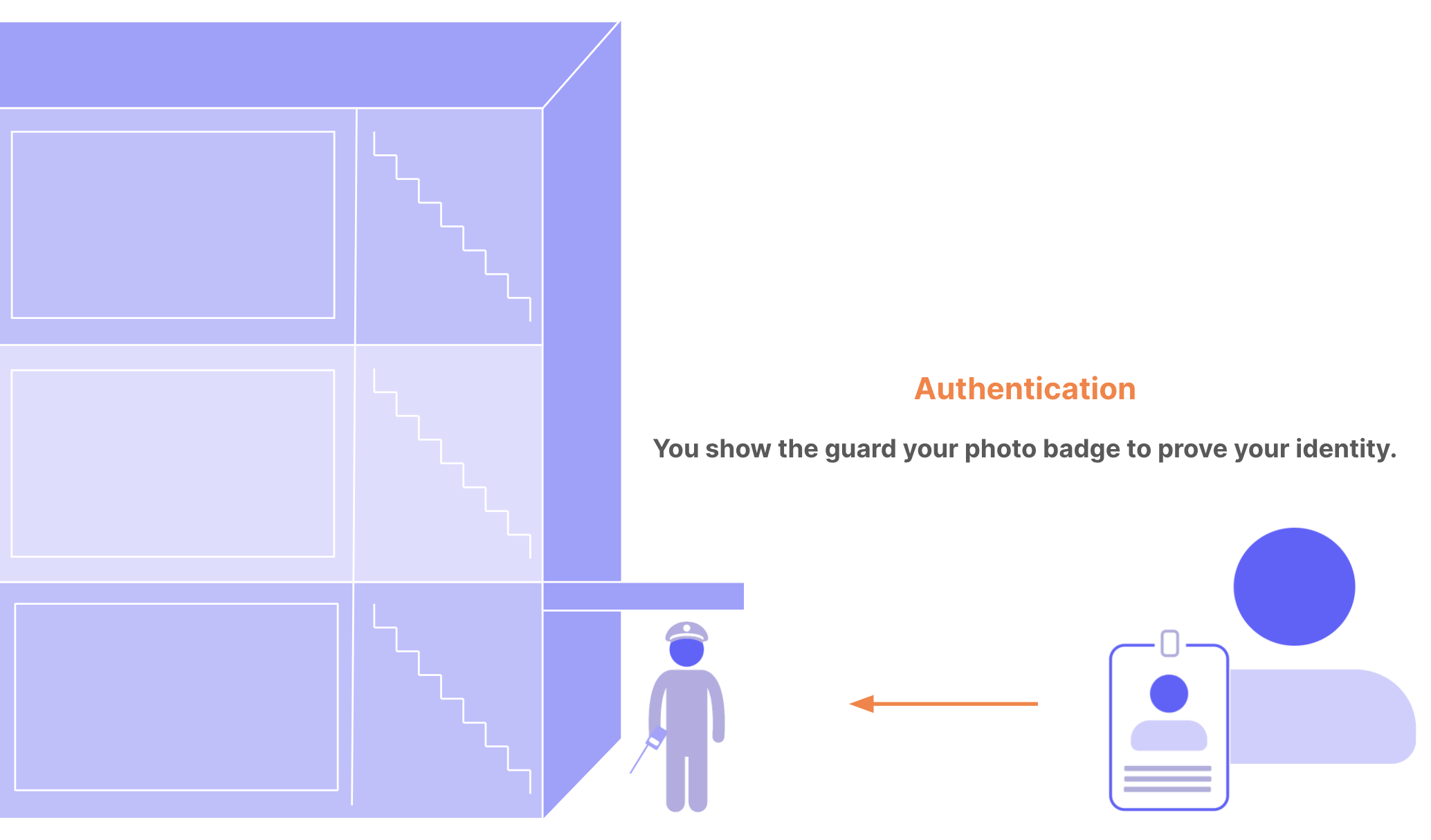
What does IAM do?
Identity and access management gives you control over user validation and resource access:- How users become a part of your system
- What user information to store
- How users can prove their identity
- When and how often users must prove their identity
- The experience of proving identity
- Who can and cannot access different resources
- Seamless signup and login experiences: Smooth and professional login and signup experiences occur within your app, with your brand’s look and language.
- Multiple sources of user identities: Users expect to be able to log in using a variety of social (such as Google or Linkedin), enterprise (such as Microsoft Active Directory), and other identity providers.
- (MFA): In an age when passwords are often stolen, requiring additional proof of identity is the new standard. Fingerprint authentication and one-time passwords are examples of common authentication methods. To learn more, read Multi-Factor Authentication (MFA).
- Step-up authentication: Access to advanced capabilities and sensitive information require stronger proof of identity than everyday tasks and data. Step-up authentication requires additional identity verification for selected areas and features. To learn more, read Add Step-up Authentication.
- : Preventing bots and from breaking into your system is fundamental to cybersecurity. To learn more, read Attack Protection.
- Role-based access control (RBAC): As the number of users grows, managing the access of each individual quickly becomes impractical. With RBAC, people who have the same role have the same access to resources. To learn more, read Role-Based Access Control.
- (FGA): When you need more options to manage user access to your resources or technologies, you can use relationship-based access control to go beyond role-based. You can give individual users access to certain resources and determine the best solution for your specific use case. To learn more, read What Is Fine-Grained Authorization?
How does IAM work?
“Identity and access management” is not one clearly defined system. IAM is a discipline and a type of framework for solving the challenge of secure access to digital resources. There’s no limit to the different approaches for implementing an IAM system. This section explores elements and practices in common implementations.Identity providers
In the past, the standard for identity and access management was for a system to create and manage its own identity information for its users. Each time a user wanted to use a new web application, they filled in a form to create an account. The application stored all of their information, including login credentials, and performed its own authentication whenever a user signed in. As the internet grew and more and more applications became available, most people amassed countless user accounts, each with its own account name and password to remember. There are many applications that continue to work this way. But many others now rely on to reduce their development and maintenance burden and their users’ effort. An identity provider creates, maintains, and manages identity information, and can provide authentication services to other applications. For example, Google Accounts is an identity provider. They store account information such as your user name, full name, job title, and email address. Slate online magazine lets you log in with Google (or another identity provider) rather than go through the steps of entering and storing your information anew.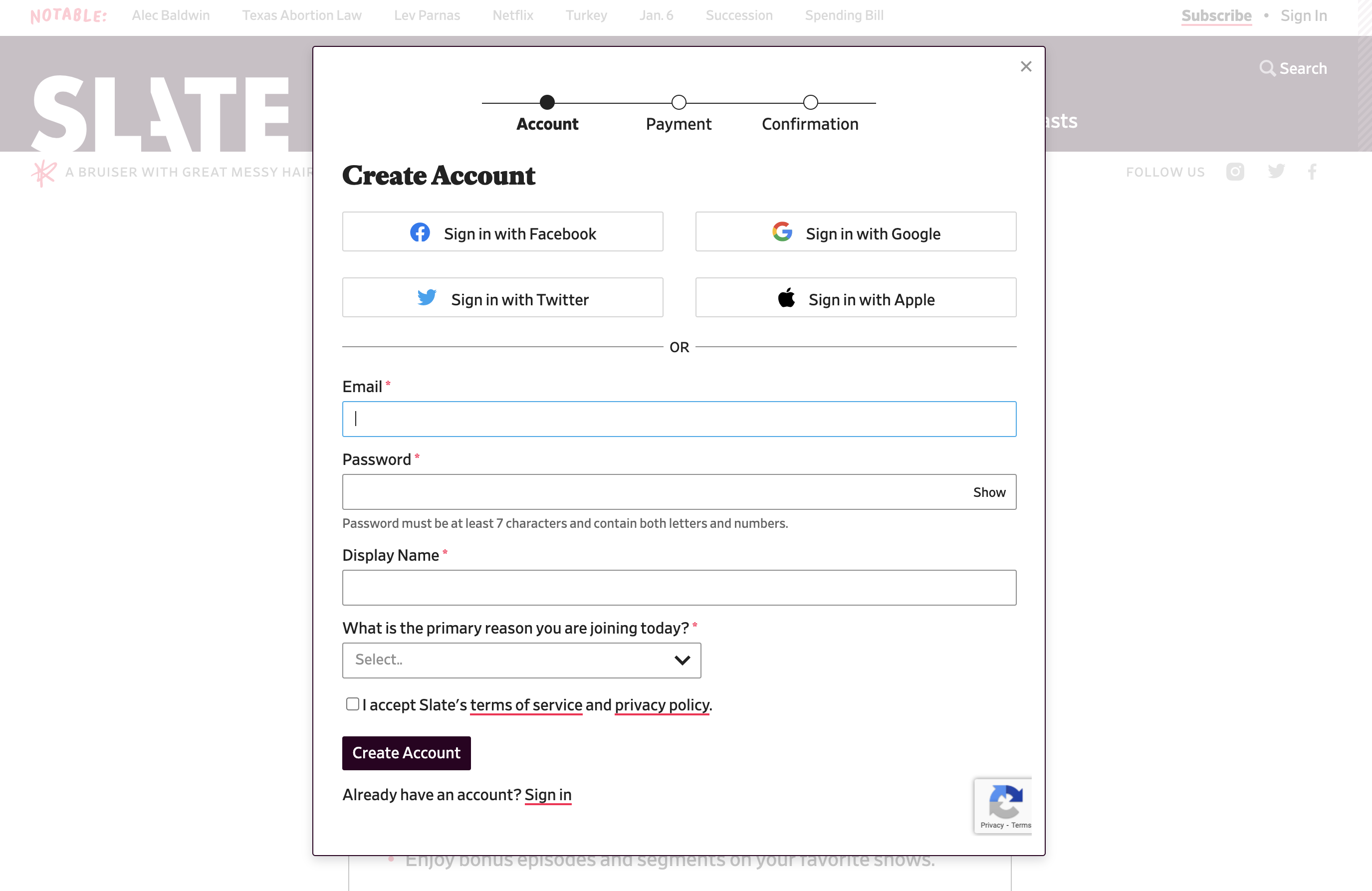
Authentication factors
Authentication factors are methods for proving a user’s identity. They commonly fall into these basic types:| Factor type | Examples |
|---|---|
| Knowledge (something you know) | Pin, password |
| Possession (something you have) | Mobile phone, encryption key device |
| Inherence (something you are) | Fingerprint, facial recognition, iris scan |
Authentication and authorization standards
Authentication and authorization standards are open specifications and protocols that provide guidance on how to:- Design IAM systems to manage identity
- Move personal data securely
- Decide who can access resources

