By David Patrick
This tutorial demonstrates how to add authorization to an Express.js API.We recommend that you log in to follow this quickstart with examples configured for your account.New to Auth0? Learn how Auth0 works and read about implementing API authentication and authorization using the OAuth 2.0 framework.
Configure Auth0 APIs
Create an API
In the APIs section of the Auth0 dashboard, click Create API. Provide a name and an identifier for your API, for example,https://quickstarts/api. You will use the identifier as an audience later, when you are configuring the Access Token verification. Leave the Signing Algorithm as RS256.
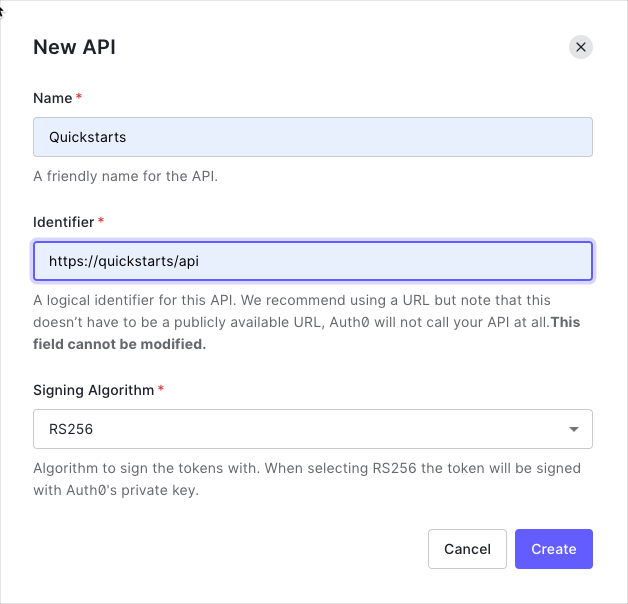
We recommend using the default RS256 signing algorithm for your API. If you need to use the HS256 algorithm, see the HS256 integration sample.
Define permissions
Permissions let you define how resources can be accessed on behalf of the user with a given access token. For example, you might choose to grant read access to themessages resource if users have the manager access level, and a write access to that resource if they have the administrator access level.
You can define allowed permissions in the Permissions view of the Auth0 Dashboard’s APIs section.
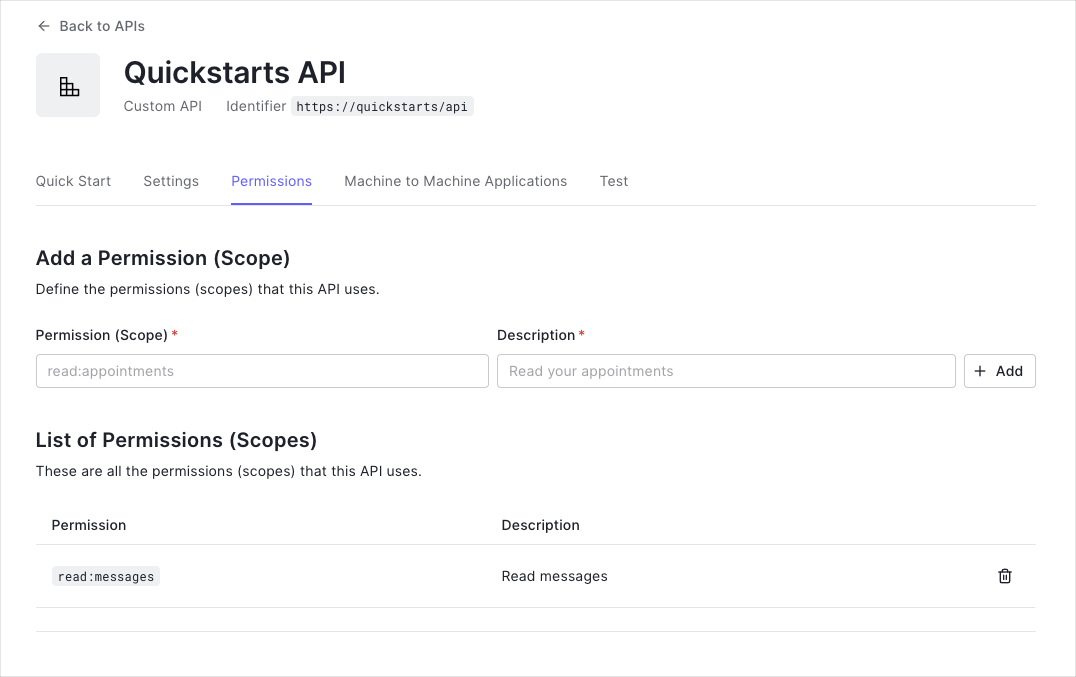
This example uses the
read:messages scope.- How to check for a JSON Web Token (JWT) in the
Authorizationheader of an incoming HTTP request. - How to check if the token is valid, using the JSON Web Key Set (JWKS) for your Auth0 account. To learn more about validating Access Tokens, see Validate Access Tokens.
Validate Access Tokens
Install dependencies
This guide shows you how to protect an Express API using the express-oauth2-jwt-bearer middleware. First install the SDK using npm.Configure the middleware
Configureexpress-oauth2-jwt-bearer with your Domain and API Identifier.
The checkJwt middleware shown above checks if the user’s Access Token included in the request is valid. If the token is not valid, the user gets a 401 Authorization error when they try to access the endpoints. The middleware doesn’t check if the token has the sufficient scope to access the requested resources.
Protect API Endpoints
The routes shown below are available for the following requests:GET /api/public: available for non-authenticated requestsGET /api/private: available for authenticated requests containing an access token with no additional scopesGET /api/private-scoped: available for authenticated requests containing an access token with theread:messagesscope granted
checkJwt express-oauth2-jwt-bearer middleware.
requiresScope method. Provide the required scopes and apply the middleware to any routes you want to add authorization to.
Pass the checkJwt and requiredScopes middlewares to the route you want to protect.
read:messages scope can access the endpoint.

