By Frederik Prijck
This tutorial demonstrates how to add user login with Auth0 to a .NET Android or iOS application.We recommend that you log in to follow this quickstart with examples configured for your account.This quickstart focusses on .NET Android and iOS, as they are the next generation of
Xamarin.Android and Xamarin.iOS. If you are still using Xamarin.Android and Xamarin.iOS, you can follow this guide as well as integration is identical and the SDKs are compatible.New to Auth? Learn How Auth0 works, how it integrates with Native Applications and which protocol it uses.
Configure Auth0
Get Your Application Keys
When you signed up for Auth0, a new application was created for you, or you could have created a new one. You will need some details about that application to communicate with Auth0. You can get these details from the Application Settings section in the Auth0 dashboard.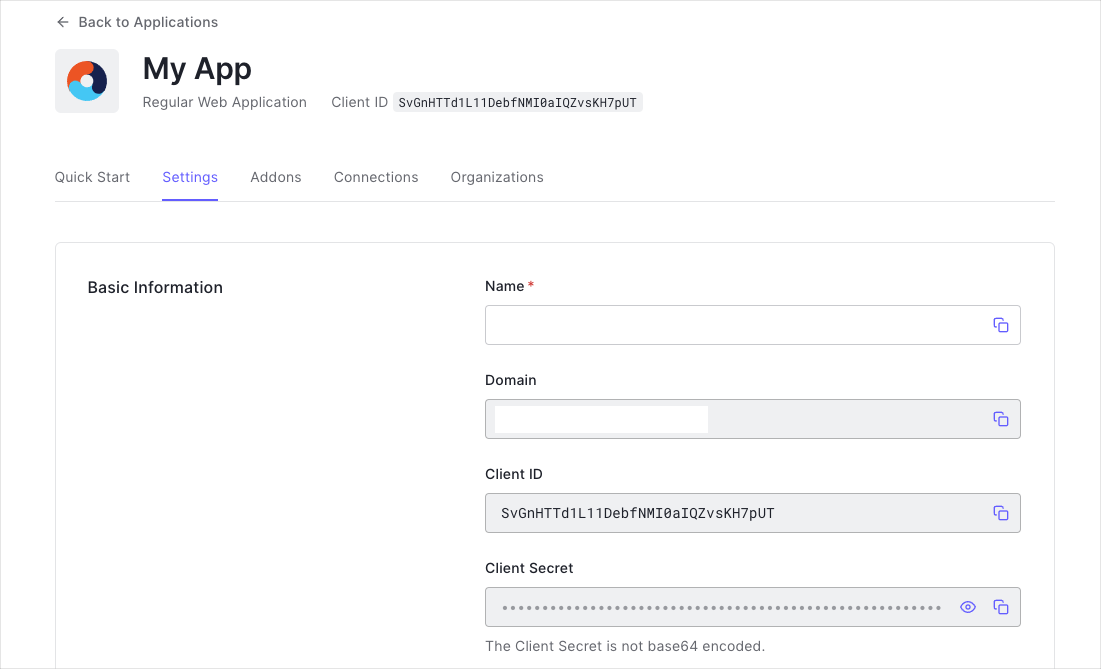
When using the Default App with a Native or Single Page Application, ensure to update the Token Endpoint Authentication Method to
None and set the Application Type to either SPA or Native.- Domain
- Client ID
If you download the sample from the top of this page, these details are filled out for you.
Configure Callback URLs
A callback URL is a URL in your application where Auth0 redirects the user after they have authenticated. The callback URL for your app must be added to the Allowed Callback URLs field in your Application Settings. If this field is not set, users will be unable to log in to the application and will get an error. Callback URLs are the URLs that Auth0 invokes after the authentication process. Auth0 routes your application back to this URL and appends additional parameters to it, including an access code which will be exchanged for an ID Token, Access Token, and Refresh Token. Since callback URLs can be manipulated, you will need to add your application’s URL to your application’s Allowed Callback URLs for security. This will enable Auth0 to recognize these URLs as valid. If omitted, authentication will not be successful.-
For Android, the callback URL will be in the format
where
YOUR_ANDROID_PACKAGE_NAMEis the Package Name for your application, such ascom.mycompany.myapplication. -
For iOS, the callback URL will be in the format
where
YOUR_BUNDLE_IDENTIFIERis the Bundle Identifier for your application, such ascom.mycompany.myapplication.
Configure Logout URLs
A logout URL is a URL in your application that Auth0 can return to after the user has been logged out of the authorization server. This is specified in thereturnTo query parameter. The logout URL for your app must be added to the Allowed Logout URLs field in your Application Settings. If this field is not set, users will be unable to log out from the application and will get an error.
If you are following along with the sample project you downloaded from the top of this page, the logout URL you need to add to the Allowed Logout URLs field is the same as the callback URL.
Install Dependencies
If you are using Visual Studio, simply open the Package Manager Console (View -> Other Windows -> Package Manager Console), and install the package: For Android:- With the project loaded in Visual Studio for Mac, Ctrl+click (or right click) on the Packages folder of the project in the Solution Pad, and select Add Packages…
- The Add Packages dialog will appear. Search and locate the package called
Auth0.OidcClient.AndroidXorAuth0.OidcClient.iOSdepending on your platform. - Tick the checkbox next to the package to select it, and click the Add Package button
Trigger Authentication
To integrate Auth0 login into your application, instantiate an instance of theAuth0Client class, configuring the Auth0 Domain and Client ID:
Then, call the LoginAsync method which will redirect the user to the login screen. You will typically do this in the event handler for a UI control such as a Login button.
Handing the callback URL
After a user has logged in, they will be redirected back to your application at the Callback URL that was registered before. In both Android and iOS you need to handle this callback to complete the authentication flow.Android
Register an intent which will handle this callback URL. An easy way to do this is to register the intent on the same activity from which you called theLoginAsync method to initiate the authentication flow.
Replace YOUR_ANDROID_PACKAGE_NAME in the code sample above with the actual Package Name for your application, such as com.mycompany.myapplication. Also ensure that all the text for the DataScheme, DataHost, and DataPathPrefix is in lower case. Also, set LaunchMode = LaunchMode.SingleTask for the Activity, otherwise the system will create a new instance of the activity every time the Callback URL gets called.
Now write code to handle the intent. You can do this by overriding the OnNewIntent method. Inside the method you need to call the Send method on the ActivityMediator to complete the authentication cycle:
iOS
Register the URL scheme for your Callback URL which your application should handle:- Open your application’s
Info.plistfile in Visual Studio for Mac, and go to the Advanced tab. - Under URL Types, click the Add URL Type button
- Set the Identifier as
Auth0, the URL Schemes the same as your application’s Bundle Identifier, and the Role asNone
info.plist file after you have added the URL Type:
OpenUrl event in your AppDelegate class. You need to notify the Auth0 OIDC Client to finish the authentication flow by calling the Send method of the ActivityMediator singleton, pass along the URL that was sent in:
Run the application
With the above code in place, a user can log in to your application using Auth0.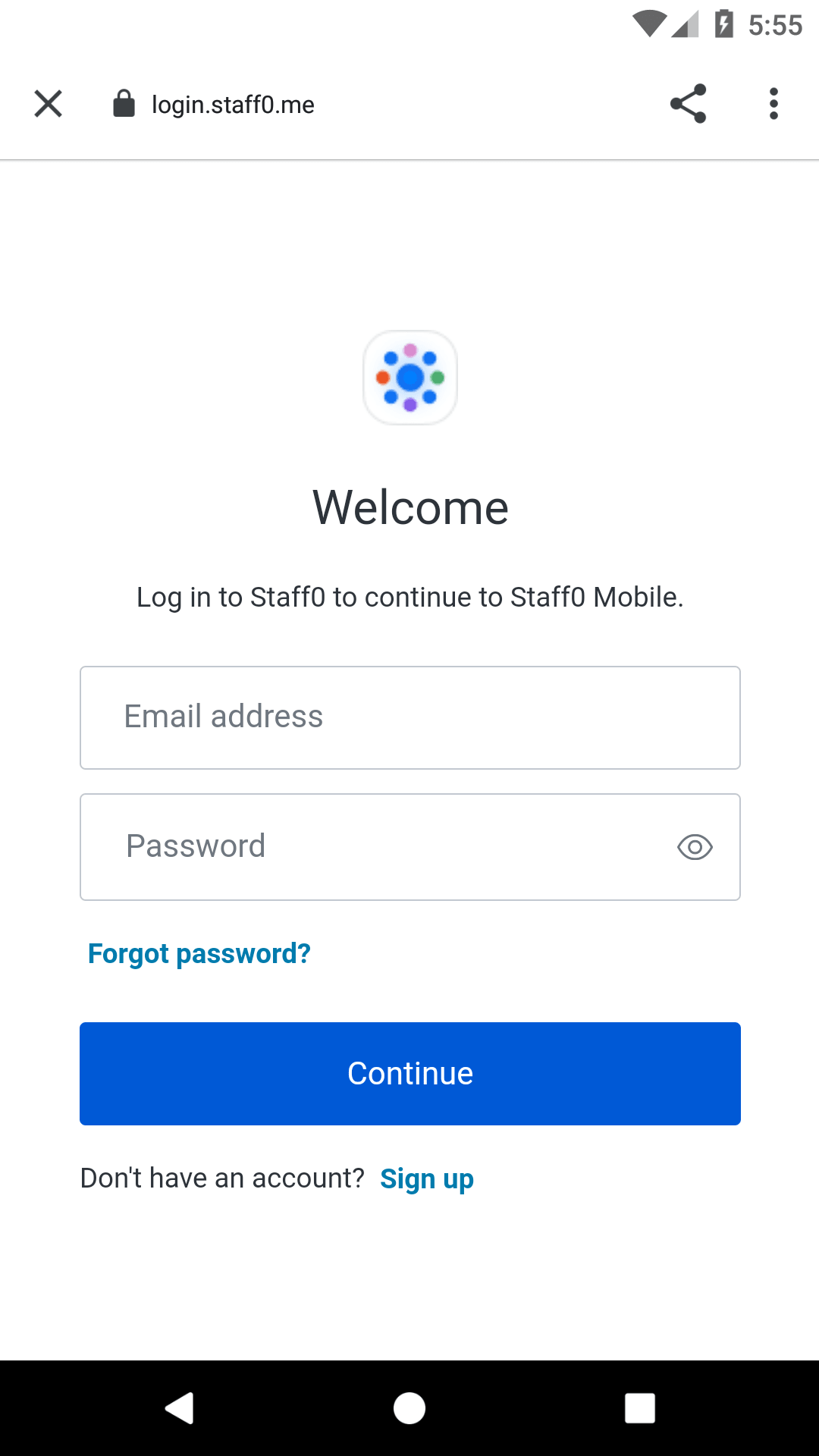
Accessing the User’s Information
The returned login result will indicate whether authentication was successful and if so contain the tokens and claims of the user.Authentication Error
You can check theIsError property of the result to see whether the login has failed. The ErrorMessage will contain more information regarding the error which occurred.
Accessing the tokens
On successful login, the login result will contain the ID Token and Access Token in theIdentityToken and AccessToken properties respectively.
Obtaining the User Information
On successful login, the login result will contain the user information in theUser property, which is a ClaimsPrincipal.
To obtain information about the user, you can query the claims. You can, for example, obtain the user’s name and email address from the name and email claims:
The exact claims returned will depend on the scopes that were requested. For more information see the Using Scopes in the Auth0 OIDC Application documentation.
Claims collection:
Logout
To log the user out call theLogoutAsync method.

