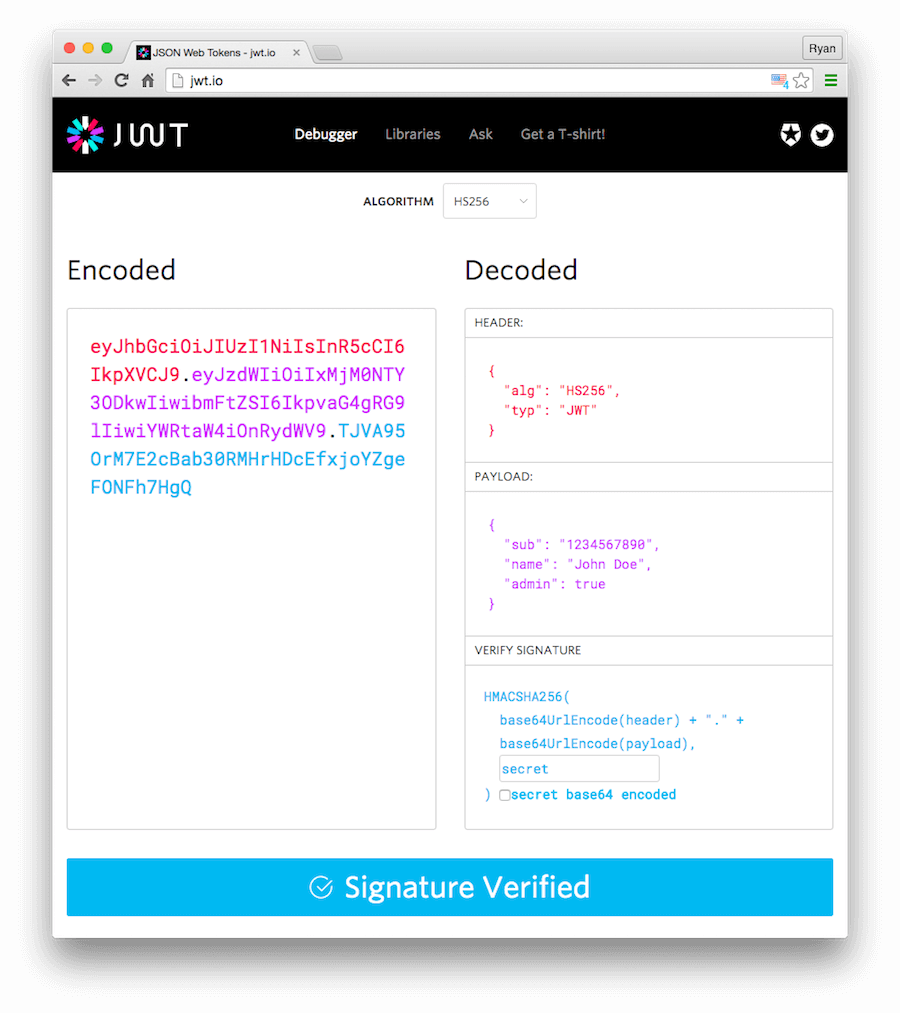
.):
- JOSE Header: contains metadata about the type of token and the cryptographic algorithms used to secure its contents.
- JWS payload (set of claims): contains verifiable security statements, such as the identity of the user and the permissions they are allowed.
- JWS signature: used to validate that the token is trustworthy and has not been tampered with. When you use a JWT, you must check its signature before storing and using it.