Configure Database connection as custom
Create a Database connection, and then set it to custom.- Go to Auth0 Dashboard > Authentication > Database and select the database to view.
-
Select the Custom Database view, and toggle on Use my own database.
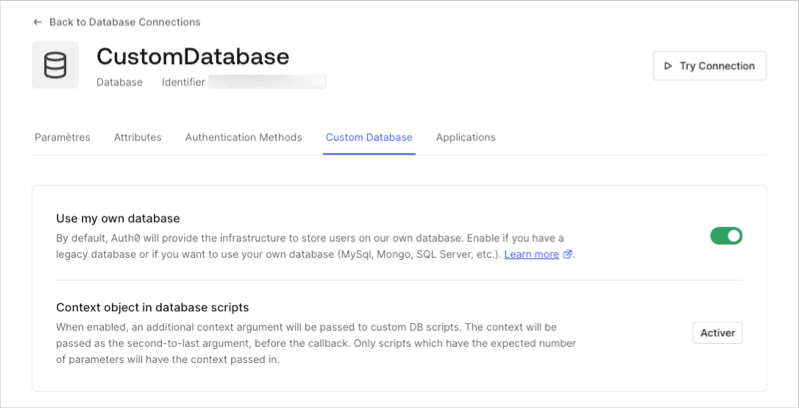
- Select the Settings view, toggle on Import Users to Auth0, and select Save.
Configure Database Action Scripts
Select the Custom Database view, and then locate Database Action Scripts.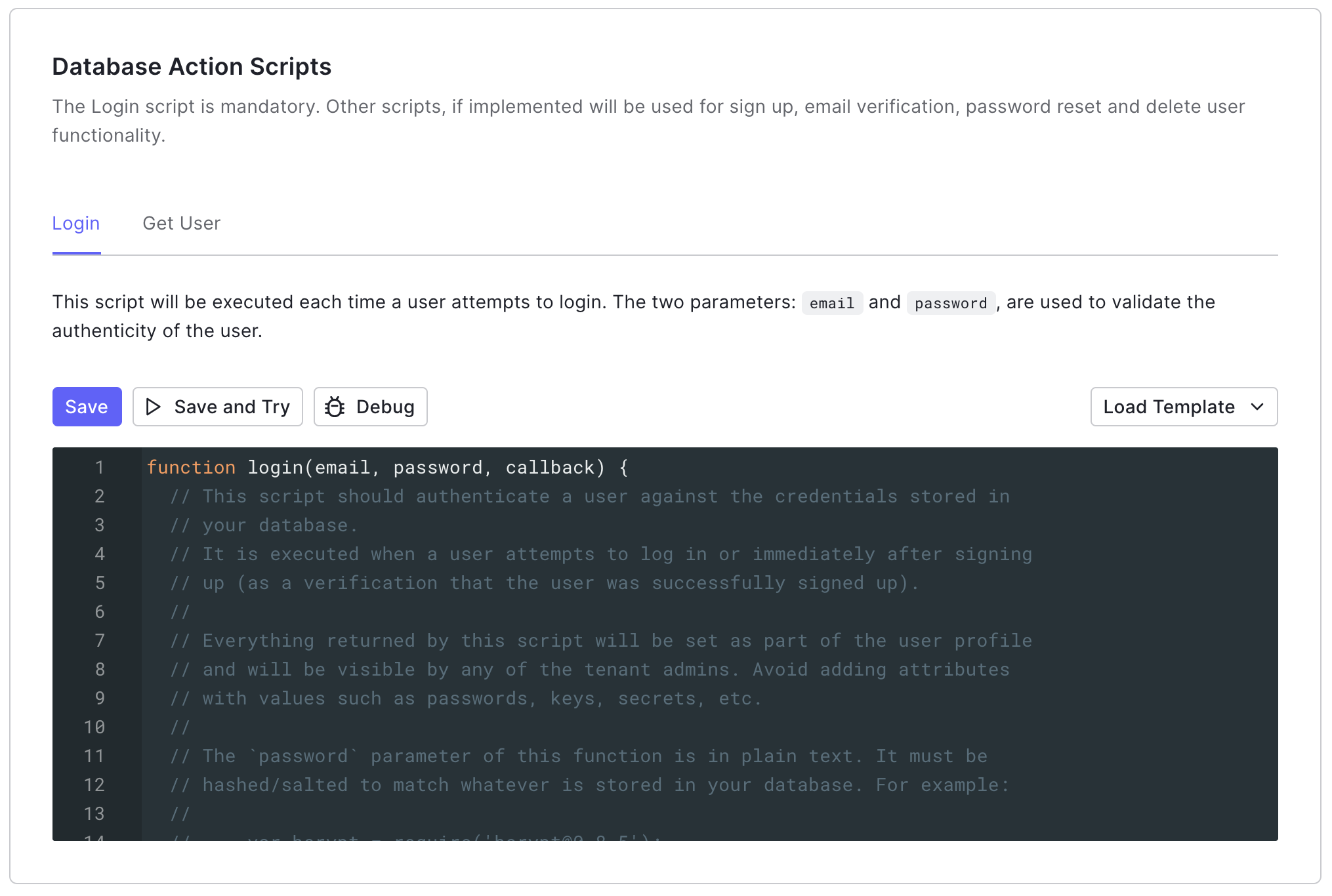
Login
The Login script executes each time a user who is not found in the Auth0 attempts to log in. It verifies that the user exists in the external user store without reprompting the user for their password.Get User
The Get User script executes after any of the following scenarios:- A user initiates signup attempt.
- A user initiates a change password flow.
- A user enters their login identifier when using Identifier First + Biometrics.
- The Update a User’s Email or Username or Create User endpoint is called.
Verify user migration is complete
Verify that all users have been migrated to the Auth0 user store using the or the Auth0 Management API.- Go to Auth0 Dashboard > User Management > Users, and review the list of users.
- Use the Management API List or Search Users endpoint.
Disconnect external user store
Reconfigure the Database Action Scripts as no operation functions. This will prevent Auth0 from reaching out to your external user store to authenticate users.Make sure to leave the Import Users to Auth0 option turned on. If you turn this option off Auth0 will only use the scripts to authenticate and perform other user actions instead of using the users that were imported locally.
- Go to Auth0 Dashboard > Authentication > Database, and then select your Database connection.
- Switch to the Custom Database view, and then locate Database Action Scripts.
-
Update the Login script.
-
Update the Get User script.
Troubleshoot user migration issues
If you encounter any issues with automatic migration, first read Custom Database Connection and Action Script Best Practices.User already exists
The most common scenarios when you may encounter this issue:- You delete a user from your Database connection and then try to recreate the user.
- You attempt to create a new user on your Database connection when the user already exists in your external user store.
- A user’s migration process was interrupted.
The user already exists error.
You can usually resolve this issue by deleting the user from the Database connection, deleting the user from the internal user store, and then reattempting the migration process.
- Check the
console.log()statements with the Actions Real-time Logs. - Delete the user with the Management API Delete a User endpoint.
- Delete the user with the Management API Delete a Connection User endpoint.
- Instruct the user to log in or change their password to reattempt migration.
Missing metadata
If a user is interrupted during the login or change password flow that initiates the migration process, Auth0 may not be able to transfer their metadata (user_metadata or app_metadata) along with their other profile data.
You can mitigate this scenario by creating an Action that verifies the user’s profile is missing metadata, retrieves it from the external use store, and then stores it in Auth0.

