Overview
Swift SDK for iOS, macOS, tvOS, and watchOS that enables you to seamlessly integrate Auth0 into your apps. Add login and logout, store credentials securely, and access user information.See the GitHub repositoryMigrating from v1? Check the Migration Guide
Documentation
- Quickstart: Shows how to integrate Auth0.swift into an iOS / macOS app from scratch.
- Sample App: A complete, running iOS / macOS app you can try.
- Examples: Explains how to use most features.
- API Documentation: Documentation auto-generated from the code comments that explains all the available features.
- FAQ: Answers some common questions about Auth0.swift.
- Auth0 Documentation: Explore our docs site and learn more about Auth0.
Getting started
Requirements
- iOS 13.0+ / macOS 11.0+ / tvOS 13.0+ / watchOS 7.0+
- Xcode 14.x
- Swift 5.7+
Installation
Swift Package Manager
Open the following menu item in Xcode: File > Add Packages… In the Search or Enter Package URL search box enter this URL:Cocoapods
Add the following line to yourPodfile:
pod install.
Carthage
Add the following line to yourCartfile:
carthage bootstrap --use-xcframeworks.
Configure the SDK
Go to the Auth0 Dashboard and create a new Native application. Auth0.swift needs the and Domain of the Auth0 application to communicate with Auth0. You can find these details in the Settings page of your Auth0 application. If you are using a custom domain, use the value of your instead of the value from the Settings page.Configure Client ID and Domain with a plist
Create aplist file named Auth0.plist in your app bundle with the following content:
Configure Client ID and Domain programmatically
For Web Auth
For the Authentication API client
For the Management API client (Users)
Configure Web Auth (iOS / macOS)
Configure callback URL and logout URL
The callback URL and logout URL are the URLs that Auth0 invokes to redirect back to your application. Auth0 invokes the callback URL after authenticating the user, and the logout URL after removing the . Since the callback URL and logout URL can be manipulated, you will need to add your URLs to the Allowed Callback URLs and Allowed Logout URLs fields in the Settings page of your Auth0 application. This will enable Auth0 to recognize these URLs as valid. If the callback URL and logout URL are not set, users will be unable to log in and out of the application and will get an error. Go to the Settings page of your Auth0 application and add the corresponding URL to Allowed Callback URLs and Allowed Logout URLs, according to the platform of your application. If you are using a custom domain, replace{yourAuth0Domain} with the value of your custom domain instead of the value from the Settings page.
iOS
macOS
com.example.MyApp and your Auth0 Domain was example.us.auth0.com, then this value would be:
Configure custom URL scheme
In Xcode, go to the Info tab of your app target settings. In the URL Types section, click the + button to add a new entry. There, enterauth0 into the Identifier field and $(PRODUCT_BUNDLE_IDENTIFIER) into the URL Schemes field.
This registers your bundle identifier as a custom URL scheme, so the callback URL and logout URL can reach your app.
Web Auth login (iOS / macOS)
Import theAuth0 module in the file where you want to present the login page.
Using async/await
Using Combine
Web Auth logout (iOS / macOS)
Logging the user out involves clearing the session cookie and then deleting the user’s credentials from your application. Call theclearSession() method in the action of your Logout button. Once the session cookie has been cleared, delete the user’s credentials.
Using async/await
Using Combine
SSO alert box (iOS / macOS)
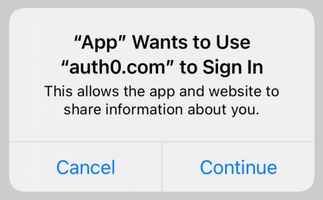
See also How to Create a Seamless Mobile SSO (Single Sign-On) Experience in iOS for a detailed overview.
Next steps
Learn about most features in Examples:- Store credentials: Store the user’s credentials securely in the Keychain.
- Check for stored credentials: Check if the user is already logged in when your app starts up.
- Retrieve stored credentials: Get the user’s credentials from the Keychain, automatically renewing them if they have expired.
- Clear stored credentials: Delete the user’s credentials to complete the logout process.
- Retrieve user information: Get the latest user information from the
/userinfoendpoint.

