This tutorial will help you call your own API from an input-constrained device using the Device Authorization Flow. If you want to learn how the flow works and why you should use it, see Device Authorization Flow.
- Authentication API: Keep reading to learn how to call our API directly. For an interactive experience, read Device Flow Playground.
Prerequisites
Before beginning this tutorial:- Check limitations (below) to be sure the Device Authorization flow is suitable for your implementation.
-
Register the Application with Auth0.
- Select an Application Type of Native.
- If necessary, set Allowed Web Origins. You can use this to allow localhost as an origin for local development, or to set an allowed origin for specific TV software with architecture subject to CORS (e.g., HTML5 + JS). Most applications will not use this setting.
- Ensure that the OIDC Conformant toggle is enabled. This setting is in the Dashboard under Applications > Application > Advanced Settings > OAuth.
- Make sure the Application’s Grant Types include Device Code. To learn how, read Update Grant Types.
- If you want your Application to be able to use Refresh Tokens, make sure the Application’s Grant Types include Refresh Token. To learn how, read Update Grant Types. To learn more about Refresh Tokens, read Refresh Tokens.
- Set up and enable at least one connection for the Application: Database connections, Social connections
-
Register your API with Auth0
- If you want your API to receive Refresh Tokens to allow it to obtain new tokens when the previous ones expire, enable Allow Offline Access. To learn more about Refresh Tokens, read Refresh Tokens.
- Configure Device User Code Settings to define the character set, format, and length of your randomly-generated user code.
Steps
- Request device code (Device Flow): Request a device code that the user can use to authorize the device.
- Request device activation (Device Flow): Request that the user authorize the device using their laptop or smartphone.
- Request tokens (Device Flow): Poll the token endpoint to request a token.
- Authorize user (Browser Flow): The user authorizes the device, so the device can receive tokens.
- Receive tokens (Device Flow): After the user successfully authorizes the device, receive tokens.
- Call API (Device Flow): Use the retrieved Access Token to call your API.
- Refresh tokens (Device Flow): Use a Refresh Token to request new tokens when the existing ones expire.
Request device code
Once the user has started their device app and wants to authorize the device, you’ll need to get a device code. When the user begins their session in their browser-based device, this code will be bound to that session. To get the device code, your app must request a code from the device code URL, including the .Example POST to device code URL
Device code parameters
Note that when requesting a device code to call a custom API, you:- must include an parameter
- can include additional scopes supported by the target API
If your app wants an Access Token only to retrieve info about the authenticated user, then no audience parameter is required.
| Parameter Name | Description |
|---|---|
client_id | Your application’s Client ID. You can find this value in your Application Settings. |
scope | The scopes for which you want to request authorization. These must be separated by a space. You can request any of the standard OIDC scopes about users, such as profile and email, custom claims conforming to a namespaced format, or any scopes supported by the target API (e.g., read:contacts). Include openid to get an ID Token or to be able to use the /userinfo endpoint to retrieve profile information for the user. Include offline_access to get a Refresh Token (make sure that the Allow Offline Access field is enabled in the API Settings). Note that this must be URL encoded. |
audience | The unique identifier of the API your app wants to access. Use the Identifier value on the Settings tab for the API you created as part of the prerequisites for this tutorial. Note that this must be URL encoded. |
Device code response
If all goes well, you’ll receive anHTTP 200 response with a payload containing device_code, user_code, verification_uri, and expires_in, interval, and verification_uri_complete values:
device_codeis the unique code for the device. When the user goes to theverification_uriin their browser-based device, this code will be bound to their session.user_codecontains the code that should be input at theverification_urito authorize the device.verification_uricontains the URL the user should visit to authorize the device.verification_uri_completecontains the complete URL the user should visit to authorize the device. This allows your app to embed theuser_codein the URL, if you so choose.expires_inindicates the lifetime (in seconds) of thedevice_codeanduser_code.intervalindicates the interval (in seconds) at which the app should poll the token URL to request a token.
You can configure the character set, format, and length of your randomly-generated user code in your tenant settings.To prevent brute force attacks, we enforce the following limits on
user_code:Minimum length:- BASE20 Letters: 8 characters
- Numbers: 9 characters
- 20 characters (including hyphens and spaces, which may be added as separators for readability)
- 15 minutes
Request device activation
Once you have received adevice_code and user_code, you must ask the user to go to the verification_uri on their laptop or smartphone and enter the user_code:
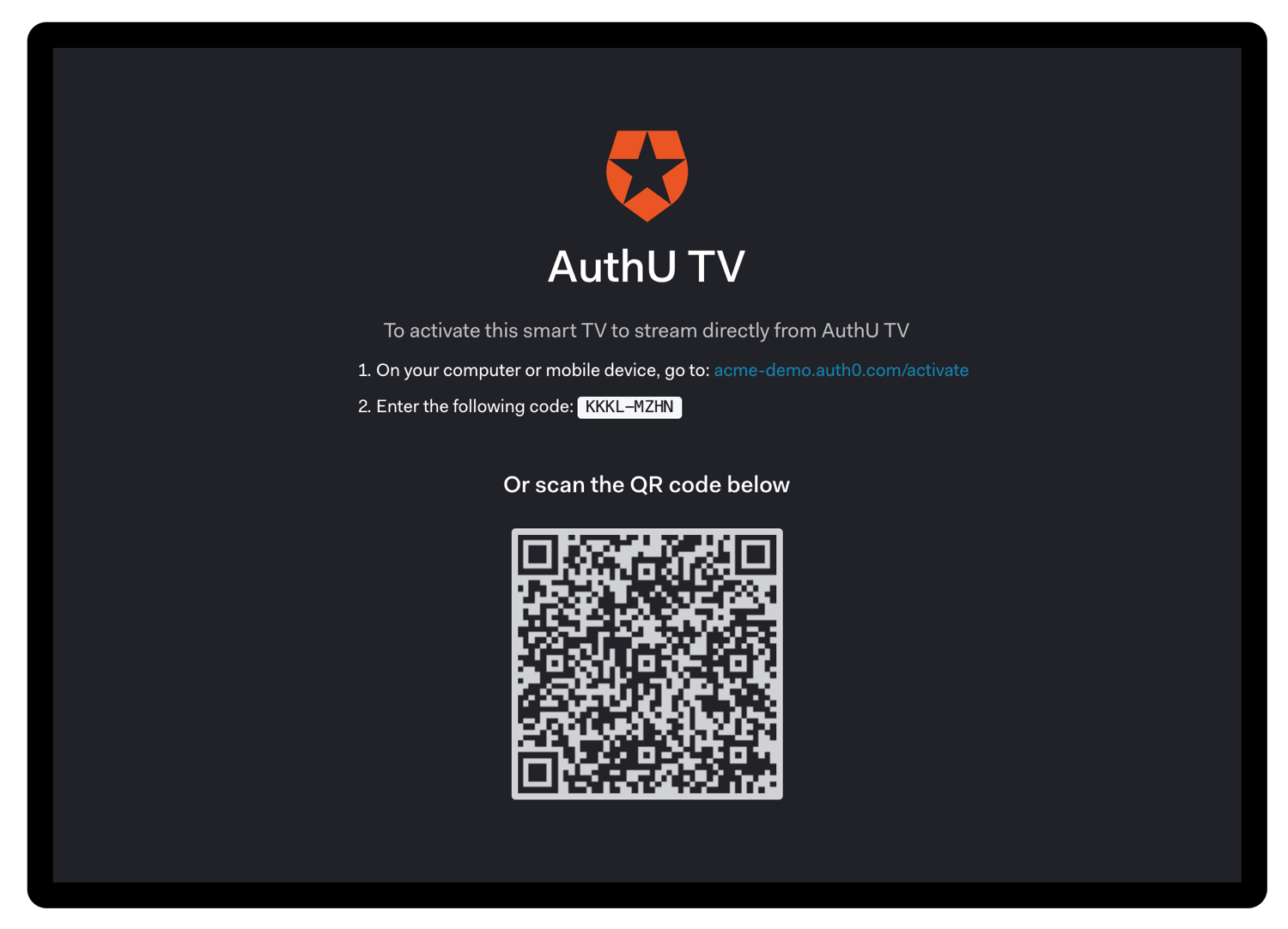
device_code is not intended for the user directly and should not be displayed during the interaction to avoid confusing the user.
When building a CLI, you could skip this step and immediately open the browser with
verification_uri_complete.Request tokens
While you are waiting for the user to activate the device, begin polling the token URL to request an . Using the extracted polling interval (interval) from the previous step, you will need to POST to the token URL sending along the device_code.
To avoid errors due to network latency, you should start counting each interval after receipt of the last polling request’s response.
Example request token POST to token URL
Token request parameters
| Parameter Name | Description |
|---|---|
grant_type | Set this to “urn:ietf:params:oauth:grant-type:device_code”. This is an extension grant type (as defined by Section 4.5 of RFC6749). Note that this must be URL encoded. |
device_code | The device_code retrieved in the previous step of this tutorial. |
client_id | Your application’s Client ID. You can find this value in your Application Settings. |
Token responses
While you wait for the user to authorize the device, you may receive a few differentHTTP 4xx responses:
Authorization pending
You will see this error while waiting for the user to take action. Continue polling using the suggested interval retrieved in the previous step of this tutorial.Slow down
You are polling too fast. Slow down and use the suggested interval retrieved in the previous step of this tutorial. To avoid receiving this error due to network latency, you should start counting each interval after receipt of the last polling request’s response.Expired token
The user has not authorized the device quickly enough, so thedevice_code has expired. Your application should notify the user that the flow has expired and prompt them to reinitiate the flow.
Access denied
Finally, if access is denied, you will receive:- the user refused to authorize the device
- the denied the transaction
- a configured rule denied access (To learn more, read Auth0 Rules.)
Authorize user
The user will either scan the QR code, or else will open the activation page and enter the user code: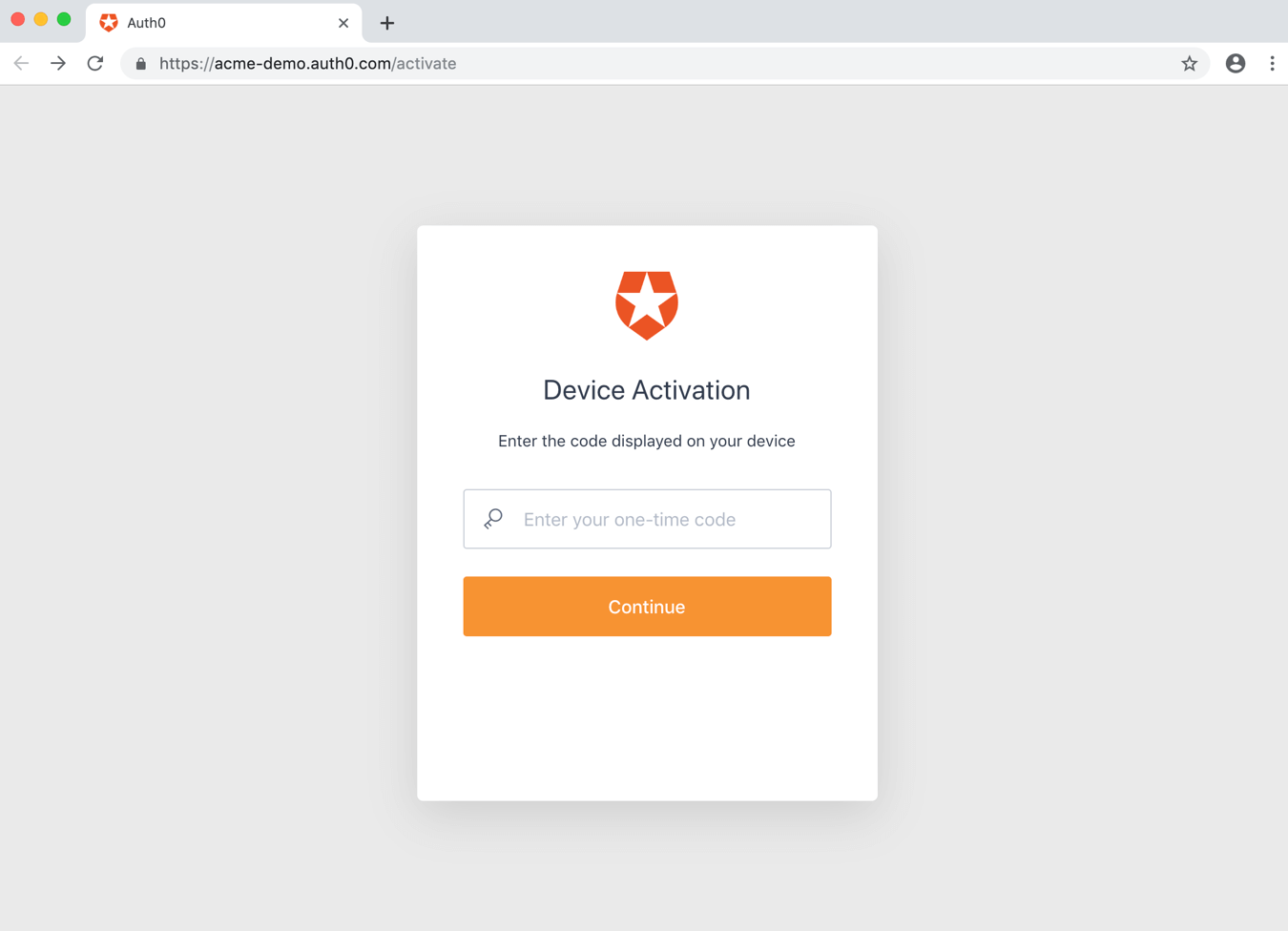
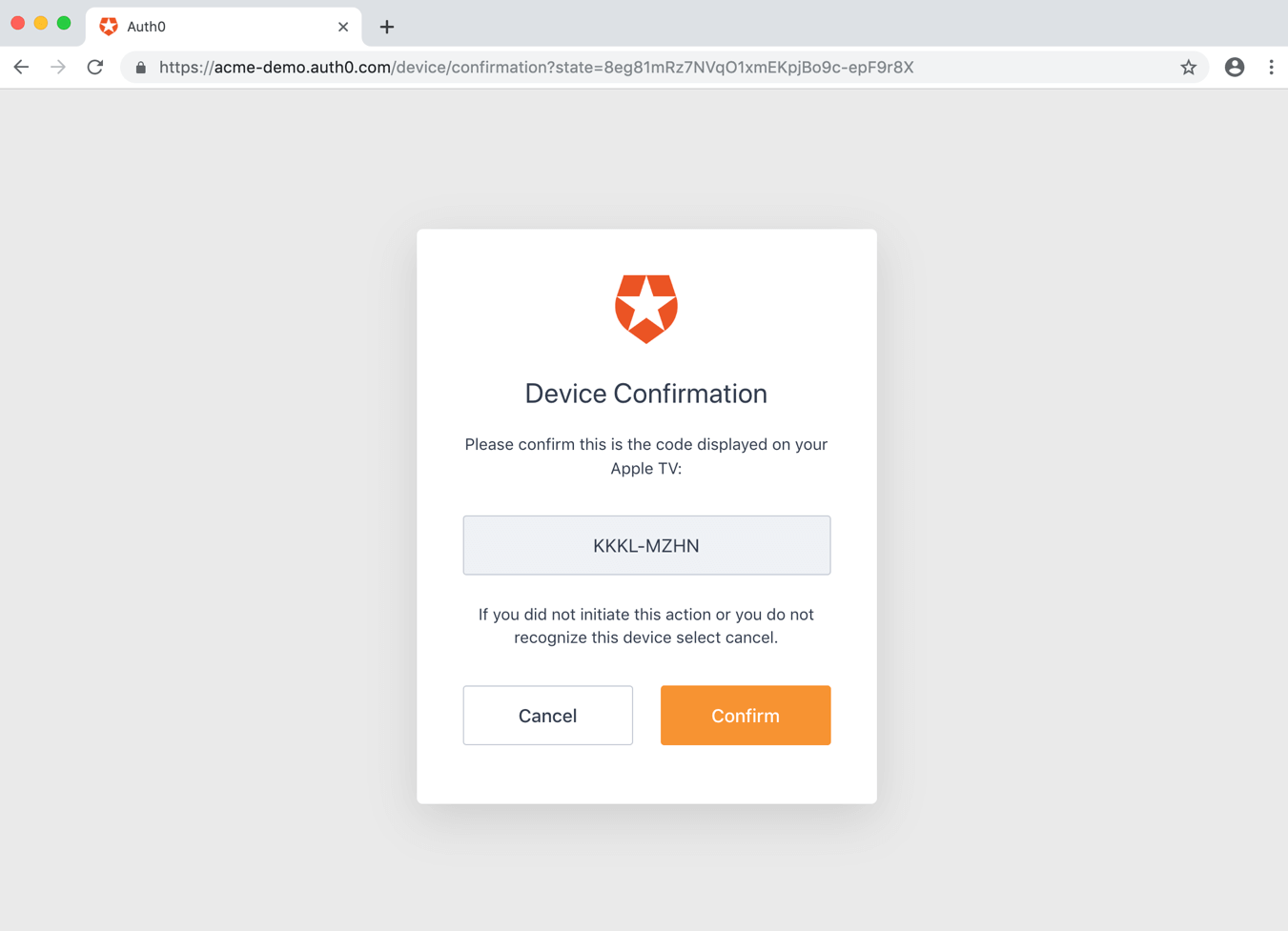
- Authenticating the user;
- Redirecting the user to an to handle authentication;
- Checking for active sessions;
- Obtaining user consent for the device, unless consent has been previously given.
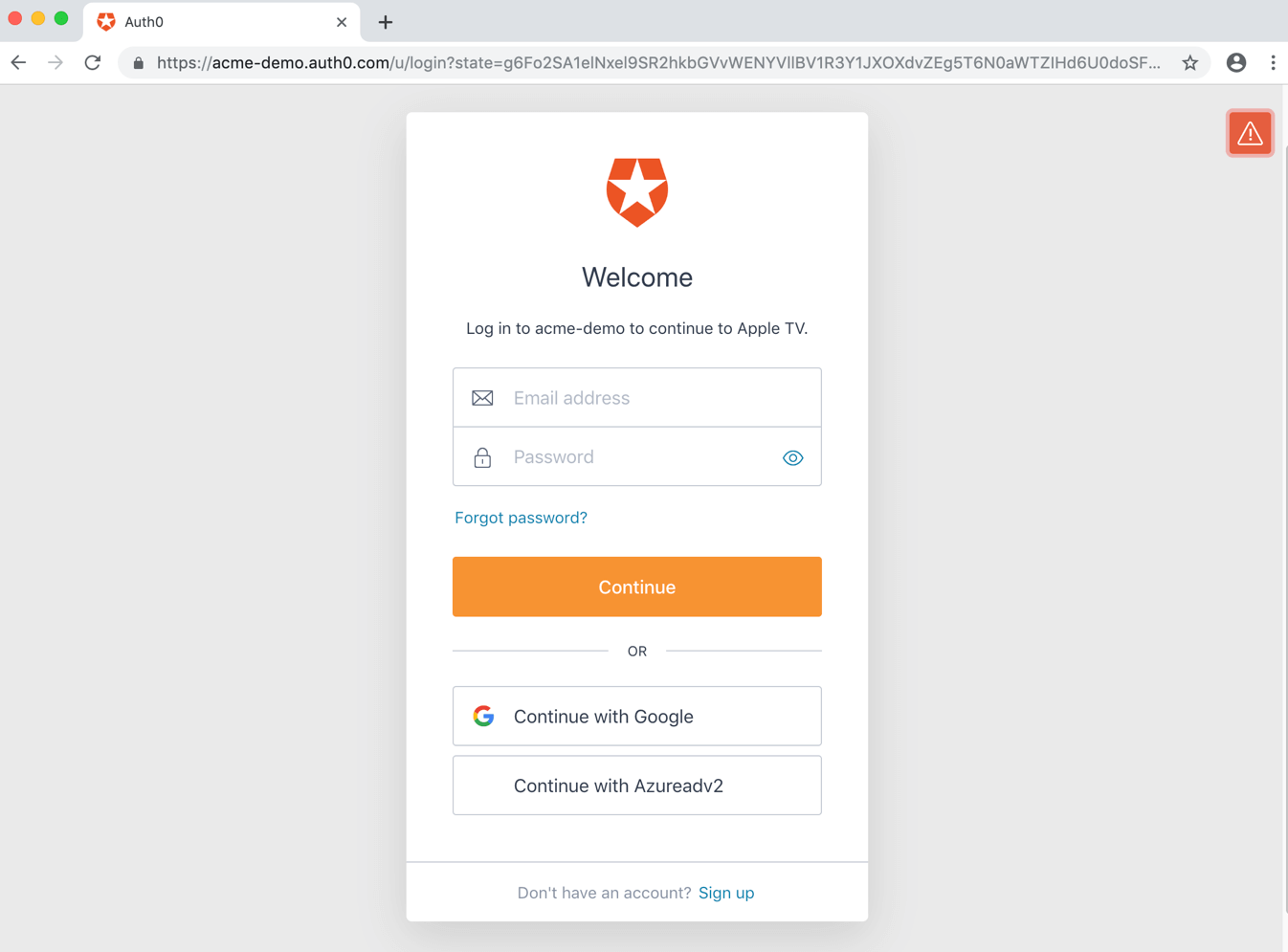
Receive tokens
While the user has been authenticating and authorizing the device, the device app has continued to poll the token URL to request an Access Token. Once the user has successfully authorized the device, you’ll receive anHTTP 200 response with a payload containing access_token, refresh_token (optionally), id_token (optionally), token_type, and expires_in values:
/userinfo endpoint or another API. (To learn more about Access Tokens, read Access Tokens.) You will be able to use the Access Token to call /userinfo only if you included the openid scope. If you are calling your own API, the first thing your API will need to do is verify the Access Token.
contain user information that must be decoded and extracted. (To learn more about ID Tokens, read ID Tokens.) The id_token will only be present in the response if you included the openid scope.
are used to obtain a new Access Token or ID Token after the previous one has expired. (To learn more about Refresh Tokens, read Refresh Tokens.) The refresh_token will only be present in the response if you included the offline_access scope and enabled Allow Offline Access for your API in the Dashboard.
Call your API
To call your API, the application must pass the retrieved Access Token as a Bearer token in the Authorization header of your HTTP request.Refresh tokens
You have already received a Refresh Token if you’ve been following this tutorial and completed the following:- configured your API to allow offline access
- included the
offline_accessscope when you initiated the authentication request through the authorize endpoint
POST request to the /oauth/token endpoint in the Authentication API, using grant_type=refresh_token.
Example refresh token POST to token URL
Refresh token request parameters
| Parameter Name | Description |
|---|---|
grant_type | Set this to “refresh_token”. |
client_id | Your application’s Client ID. You can find this value in your Application Settings. |
client_secret | Your application’s Client Secret. You can find this value in your Application Settings. |
refresh_token | The Refresh Token to use. |
scope | (Optional) A space-delimited list of requested scope permissions. If not sent, the original scopes will be used; otherwise you can request a reduced set of scopes. Note that this must be URL encoded. |
Refresh token response
If all goes well, you’ll receive anHTTP 200 response with a payload containing a new access_token, id_token (optionally), token lifetime in seconds (expires_in), granted scope values, and token_type:
Sample use cases
Detect device authorization flow use
You can use Rules to detect whether the current transaction is using the Device Authorization Flow. (To learn more about rules, read Auth0 Rules.) To do so, check thecontext object’s protocol property:
Sample implementations
- Device Authorization Playground
- AppleTV (Swift): Simple application that shows how Auth0 can be used with the Device Authorization Flow from an AppleTV.
- CLI (Node.js): Sample implementation of a CLI that uses the Device Authorization Flow instead of the Authorization Code Flow. The major difference is that your CLI does not need to host a web server and listen on a port.
Troubleshoot
Tenant logs are created for any interaction that takes place and can be used to troubleshoot issues. To learn more, read Logs.Error codes
| Code | Name | Description |
|---|---|---|
fdeaz | Failed device authorization request | |
fdeac | Failed device activation | |
fdecc | User canceled the device confirmation | |
fede | Failed Exchange | Device Code for Access Token |
sede | Success Exchange | Device Code for Access Token |
Limitations
To use the Device Authorization Flow, devices must:- Support Server Name Indication (SNI) when Custom Domains are used
- Have an Auth0 application type of Native
- Have the Token Endpoint Authentication Method set to None
- Be OIDC-conformant
- Not be created through Dynamic Client Registration
- Social Connections using Auth0 developer keys unless you are using the Universal Login experience
- Query string parameters to be accessed from hosted login page or Rules or Actions
- User account linking

