Imagine if you could charge every single one of your devices with one, single charger.
Your smartphone, the family printer, your kiddo’s tablet, and your work computer. How great would this be? You’d no longer be searching your junk drawer for that one, specific cord.
Similarly, access tokens are the lifeblood of an IAM (Identity and Access Management) infrastructure, impacting gateways, microservices and teams. Consequently, changing access token formats can be costly, time-consuming, and a pain.
This issue led to the IETF standards community brainstorming and then publishing a new standard detailing how to encode and validate an OAuth 2.0 JWT access token. The standardization process, led by Vittorio Bertocci, has been captured in this insightful blog.
We’re happy to announce that RFC 9068 is now Generally Available on Auth0 for all customers. We continue to focus on enabling everyone to safely use any technology, and we hope that RFC 9068 supports you and your team’s Identity solutions. Let’s talk about how to use it.
Access Token Profiles in Auth0
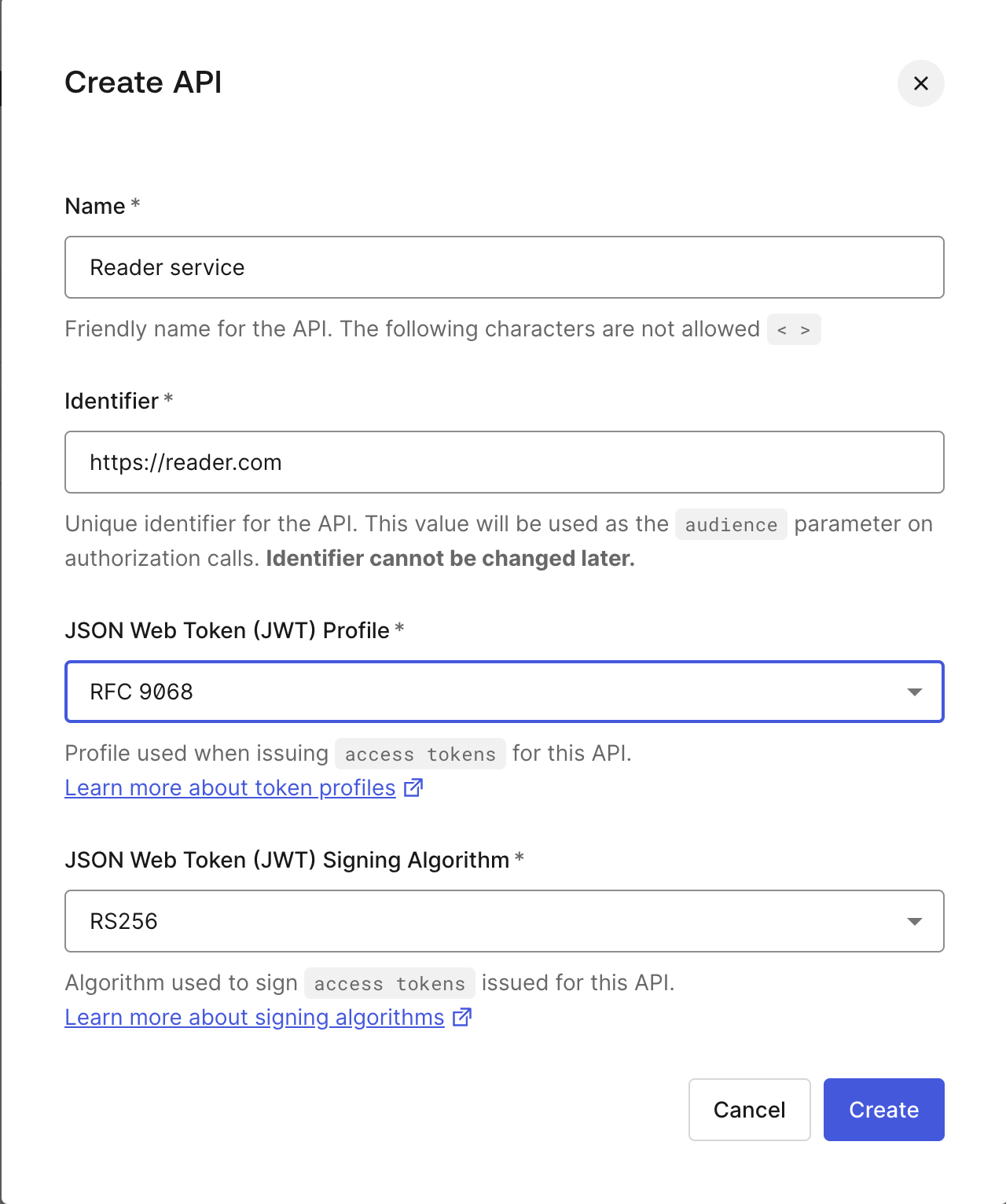
Auth0 now offers the option to choose, on a per-API basis, between two access token profiles: the Auth0 token profile, which remains the default, and RFC 9068.
Based on the selected access token profile for an API, the format of the generated JWT access token changes. The main differences are:
- The RFC 9068 profile incorporates the jti claim, providing a unique identifier for the JWT.
- The Auth0 profile uses the azp claim to represent the client ID, whereas the RFC 9068 profile uses the client_id claim.
- The RFC 9068 profile does not use the gty claim, which is an Auth0-specific claim that represents the authentication flow.
Adopting the RFC 9068 profile offers several advantages. Your Auth0 access tokens will be directly interoperable with API gateways and servers that follow the standard, eliminating the need for custom token validation. This flexibility facilitates changing Identity Providers if you need to at some point. Additionally, you can leverage SDKs and tools that support RFC 9068, aligning with well-vetted Identity standards and evolving best practices.
Generate a RFC 9068-Compliant Access Token
The RFC 9068 token profile is Generally Available and supported across all tenants and plans. You can generate an RFC 9068-compliant access token using the same process as obtaining any access token: create a client, configure an API, and request a token.
To create a client, you can simply follow the normal process as explained in our Get Started guide. The RFC 9068 profile works for all application types and grant-types.
Configure an API
Go to Dashboard > Applications > APIs, and select + Create API.
The JSON Web Token (JWT) Profile field determines the format of the API access tokens issued. The available values are Auth0 and RFC 9068.
Image snapshot of the API creation page where the user can configure an access token profile. To learn more, refer to Register APIs
Get an access token
As an example, let's see how you can request an access token with client_credentials grant via cURL:
curl --request POST \
--url https://YOUR_AUTH0_DOMAIN/oauth/token \
--header 'content-type: application/json' \
--data '{"client_id":"YOUR_CLIENT_ID","client_secret":"YOUR_CLIENT_SECRET","audience":"https://your-api-endpoint","grant_type":"client_credentials"}'
Replace the placeholders YOUR_AUTH0_DOMAIN, YOUR_CLIENT_ID, and YOUR_CLIENT_SECRET with the respective values from your client configuration.
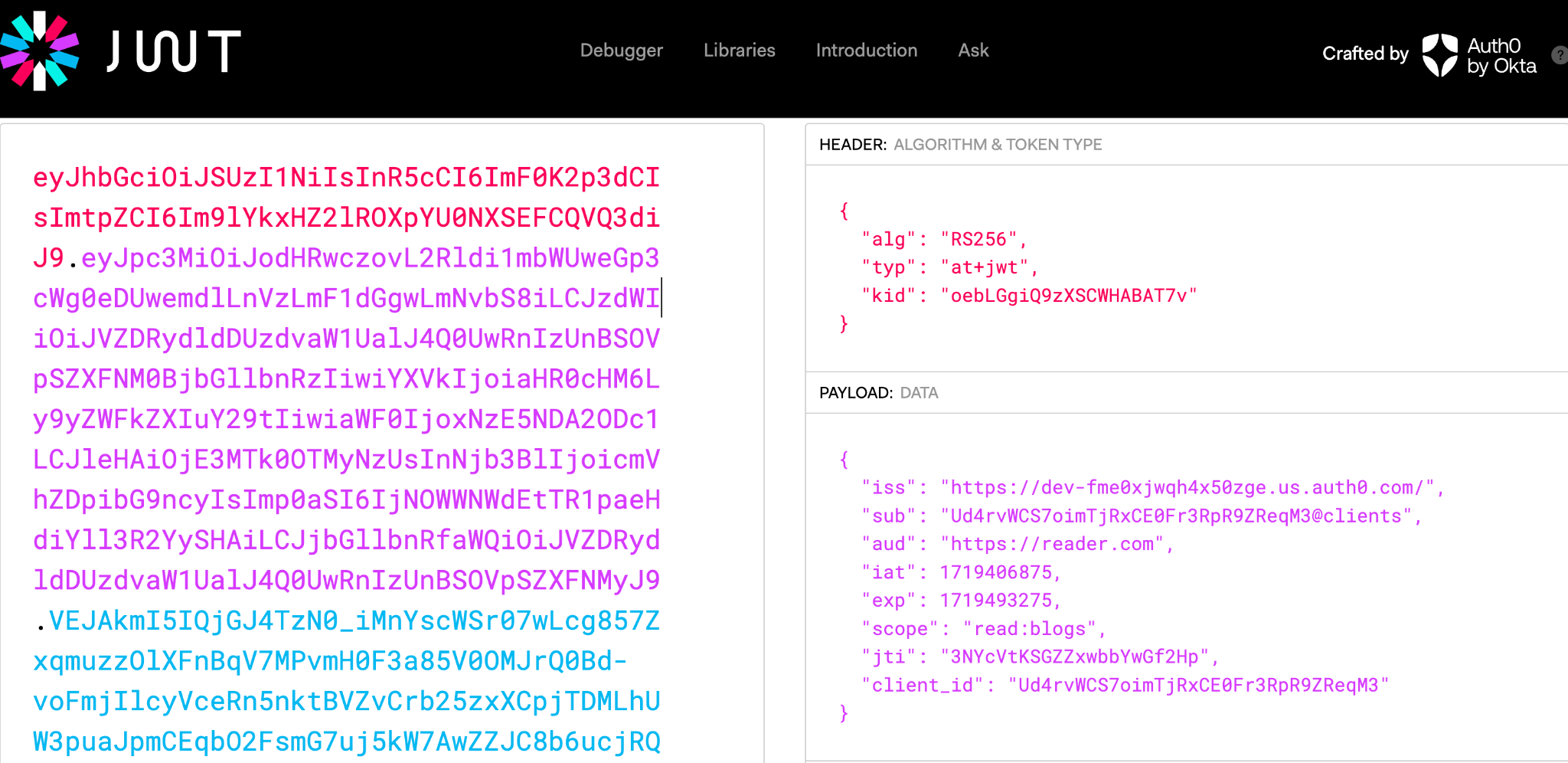
This request generates a response as the following:
{
"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCI6Im...",
"scope":"read:blogs",
"expires_in":86400,
"token_type":"Bearer"
}
The generated access_token will be RFC 9068 compatible.
This works for all grant-types for the API. Simply follow the normal flow of a grant-type and you will get RFC 9068 compliant access tokens. Easy!
client_credentials grant type
An Ode to the Great...
Now, this post wouldn’t be complete without taking some time to acknowledge the brains behind RFC 9068, Vittorio Bertocci.
Vittorio was and will continue to be a titan of the Identity industry. Not only was Vittorio a luminary genius in his own right, but he was a funny, witty and authentic human being. His legacy will forever be woven into the work we, and our fellow Identity friends, create for the next years, decades, and beyond. (To read a bit more about our beloved Vittorio, take a look at our celebratory blog about his life here).
To continue Vittorio’s legacy and his passion for giving back to the community, we’d love to share two causes that were incredibly important to Vittorio:
- Questbridge: providing higher education to lower income students.
- Pancan: pancreatic cancer research.