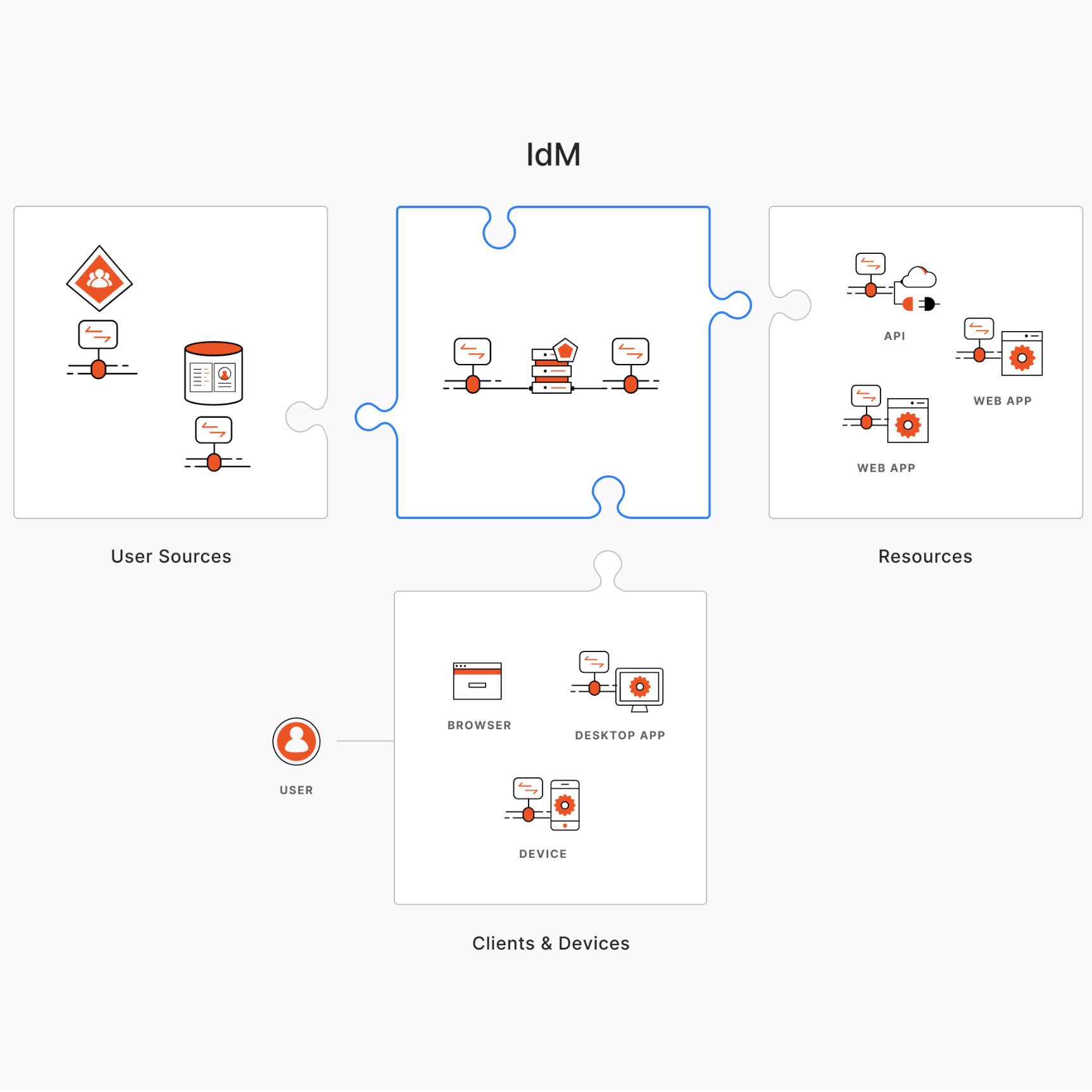
Every identity professional is familiar with that vaguely frustrating feeling arising from working on a scenario that is almost perfect. If only that user store could support OpenID Connect… If only that legacy app could be slightly modified… Similar deviations from the canonical scenarios are the true norm, making it hard to provide a solution that only relies on the out of the box features commonly found in identity products.
Businesses, system integrators, and software vendors deal with those challenges following what looks like a disjointed set of different strategies. Some take a brute force approach and code every identity functionality from scratch. Others implement their identity functions deploying installable instances of server products, or rely on operating system features, and take advantage of the degree of control that can be achieved by running your private instance. Yet others rely on IDaaS (Identity-as-a-Service) offerings, leveraging whatever extensibility technology is offered to adapt the defaults to the specific needs of their particular scenarios.
“How do you know if the identity solution you are evaluating will give you the power and flexibility your scenarios require? The answer is in their extensibility features.#taoofextensibility”
Tweet This
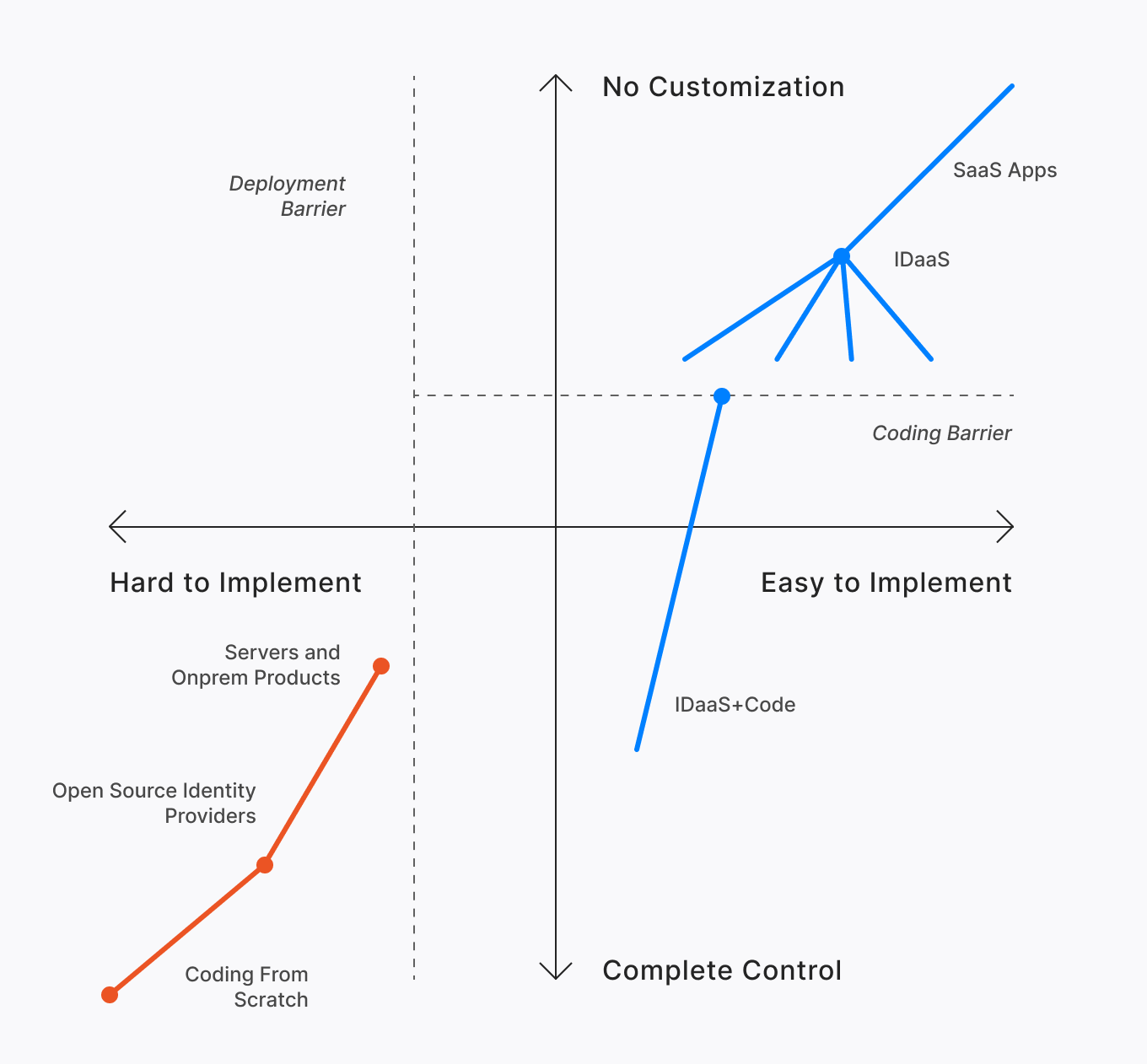
In that apparent chaos, choosing the strategy that best fits your requirements isn’t easy. To help with that difficult task, we authored a whitepaper that compares and contrasts the main approaches to identity customization. By placing every strategy on a continuum based on the expressive power and ease of implementation dimensions, we expose individual strengths and weaknesses while offering you a logical progression you can use as a reference when considering hybrid approaches. Here’s the chart that summarizes it all:
The strategies considered cluster around two macro approaches, one which favors full control at the price of taking more responsibility in the implementation (lower left quadrant) and one where most functionality is outsourced to a service, with the expressive power bounded by the extensibility choices of the selected service (top right quadrant). You’ll have to download the whitepaper to find out the whole story, but let me give you a spoiler alert here.
At Auth0 we believe in the power of outsourcing identity concerns to a service run by professionals, but we are also strong believers in the power of code. This is why we deem the IDaaS+code approach to be the one offering the absolute best compromise: identity essentials taken care of by an easy to use service while retaining the ability to address last-mile customizations with code — the same control and power you’d have if you would have coded everything from scratch.
Download the Identity in the Real Word: the Tao of Extensibility whitepaper.
Auth0 Principal Architect Vittorio Bertocci’s new whitepaper can help CTOs, architects, and developers understand the trade-offs between the different customization strategies offered by today’s identity solutions, explaining how to pick the right one for each scenario in the “Tao of Extensibility.”
“Today’s identity products approach customization with many different strategies. Auth0 Principal Architect @vibronet evaluates the strengths of each approach. #taoofextensibility”
Tweet This
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Vittorio Bertocci
Principal Architect