Mobile initiatives are a top priority for many organizations these days because research shows that increases in mobility help enterprises improve operations and productivity.
However, increases in organizational mobility typically result in an increase in the number of mobile devices that are accessing your systems from a remote location. And for your security teams, this means a growing variety of endpoints and threats they need to secure in order to protect your organization from a data breach.
As in the past, the most common threats to mobile security include mobile malware. However, as Verizon’s 2020 Mobile Security Index Report shows, there are new threats organizations need to consider as well in order to ensure they’re protected.
Below are the most common and critical mobile security threats that organizations face in 2021.
4 Different Types of Mobile Security Threats
Mobile security threats are commonly thought of as a single, all-encompassing threat. But the truth is, there are four different types of mobile security threats that organizations need to take steps to protect themselves from:
- Mobile Application Security Threats. Application-based threats happen when people download apps that look legitimate but actually skim data from their device. Examples are spyware and malware that steal personal and business information without people realizing it’s happening.
- Web-Based Mobile Security Threats. Web-based threats are subtle and tend to go unnoticed. They happen when people visit affected sites that seem fine on the front-end but, in reality, automatically download malicious content onto devices.
- Mobile Network Security Threats. Network-based threats are especially common and risky because cybercriminals can steal unencrypted data while people use public WiFi networks.
- Mobile Device Security Threats. Physical threats to mobile devices most commonly refer to the loss or theft of a device. Because hackers have direct access to the hardware where private data is stored, this threat is especially dangerous to enterprises.
Below are the most common examples of these threats, as well as steps organizations can take to protect themselves from them.
1. Social Engineering
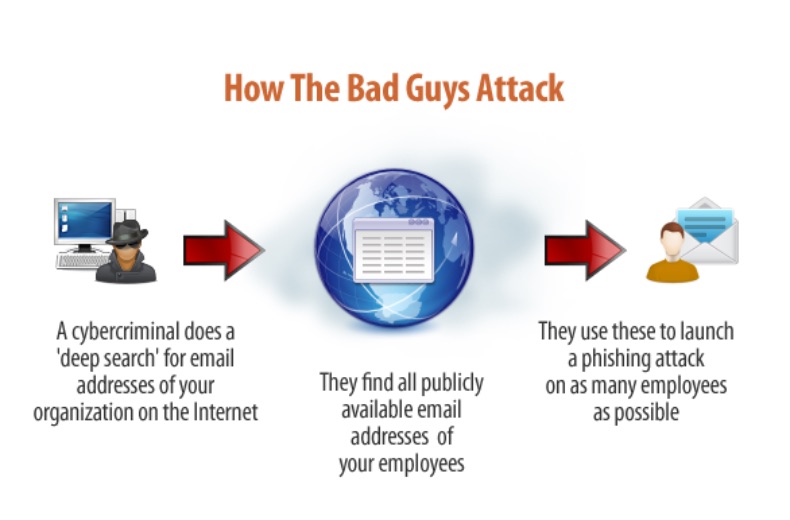
Social engineering attacks are when bad actors send fake emails (phishing attacks) or text messages (smishing attacks) to your employees in an effort to trick them into handing over private information like their passwords or downloading malware onto their devices.
Reports by cybersecurity firm Lookout and Verizon show a 37% increase in enterprise mobile phishing attacks and that phishing attacks were the top cause of data breaches globally in 2020.
Phishing Attack Countermeasures
The best defense for phishing and other social engineering attacks is to teach employees how to spot phishing emails and SMS messages that look suspicious and avoid falling prey to them altogether. Reducing the number of people who have access to sensitive data or systems can also help protect your organization against social engineering attacks because it reduces the number of access points attackers have to gain access to critical systems or information.
2. Data Leakage via Malicious Apps
As Dave Jevans, CEO and CTO of Marble Security, explains, “Enterprises face a far greater threat from the millions of generally available apps on their employees’ devices than from mobile malware.”
That’s because 85% of mobile apps today are largely unsecured. Tom Tovar, CEO of Appdome, says, “Today, hackers can easily find an unprotected mobile app and use that unprotected app to design larger attacks or steal data, digital wallets, backend details, and other juicy bits directly from the app.”
For example, when your employees visit Google Play or the App Store to download apps that look innocent enough, the apps ask for a list of permissions before people are allowed to download them. These permissions generally require some kind of access to files or folders on the mobile device, and most people just glance at the list of permissions and agree without reviewing them in great detail.
However, this lack of scrutiny can leave devices and enterprises vulnerable. Even if the app works the way it’s supposed to, it still has the potential to mine corporate data and send it to a third party, like a competitor, and expose sensitive product or business information.
How to Protect Against Data Leakage
The best way to protect your organization against data leakage through malicious or unsecured applications is by using mobile application management (MAM) tools. These tools allow IT admins to manage corporate apps (wipe or control access permissions) on their employees’ devices without disrupting employees’ personal apps or data.
3. Unsecured Public WiFi
Public WiFi networks are generally less secure than private networks because there’s no way to know who set the network up, how (or if) it’s secured with encryption, or who is currently accessing it or monitoring it. And as more companies offer remote work options, the public WiFi networks your employees use to access your servers (e.g., from coffee shops or cafes) could present a risk to your organization.
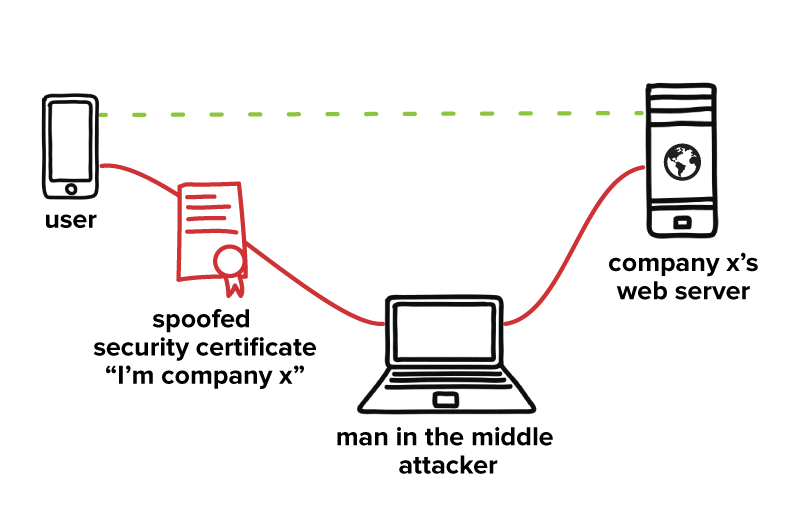
For example, cybercriminals often set up WiFi networks that look authentic but are actually a front to capture data that passes through their system (a “man in the middle” attack). Here's what that looks like:
If this seems far-fetched, it isn’t. Creating fake WiFi hotspots in public spaces with network names that look completely legit is incredibly simple, and people are very willing to connect, as shown by experiments run at the Democratic and Republican conventions in 2016 and by an experiment run by a researcher in 2019 from Magic.
How to Reduce Risks Posed By Unsecured Public WiFi
The best way for you to protect your organization against threats over public WiFi networks is by requiring employees to use a VPN to access company systems or files. This will ensure that their session stays private and secure, even if they use a public network to access your systems.
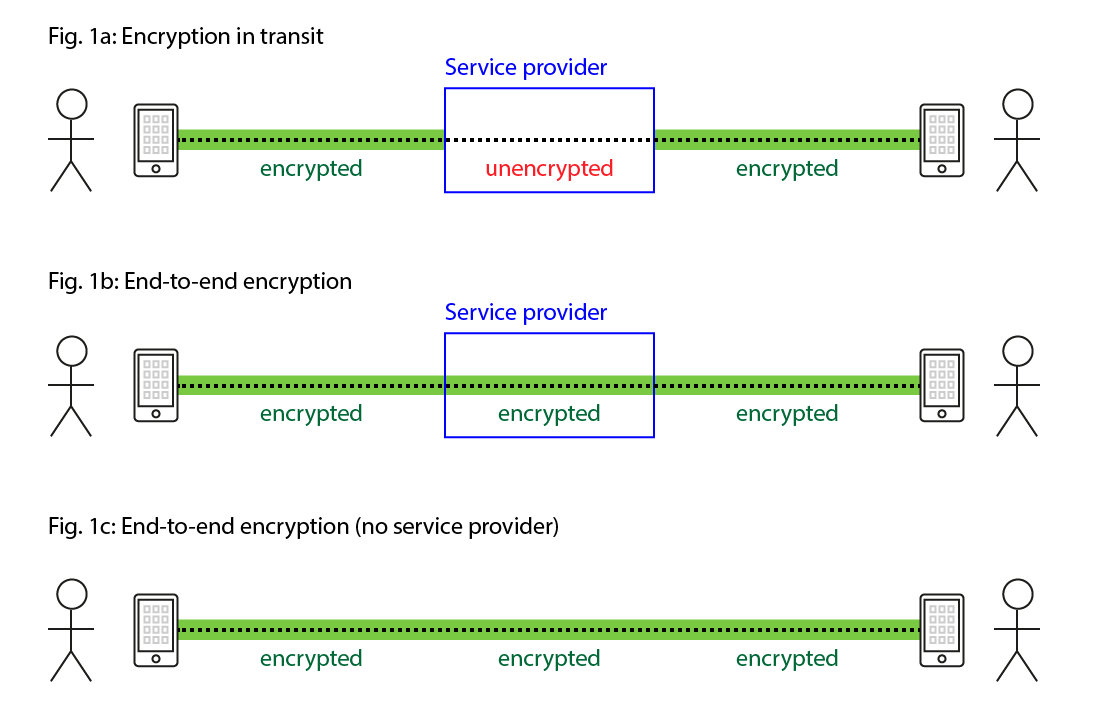
4. End-to-End Encryption Gaps
An encryption gap is like a water pipe with a hole in it. While the point where the water enters (your users’ mobile devices) and the point where the water exits the pipe (your systems) might be secure, the hole in the middle lets bad actors access the water flow in between.
Unencrypted public WiFi networks are one of the most common examples of an encryption gap (and it’s why they’re a huge risk to organizations). Since the network isn’t secured, it leaves an opening in the connection for cybercriminals to access the information your employees are sharing between their devices and your systems.
However, WiFi networks aren’t the only thing that poses a threat—any application or service that’s unencrypted could potentially provide cybercriminals with access to sensitive company information. For example, any unencrypted mobile messaging apps your employees use to discuss work information could present an access point for a bad actor.
Solution: Ensure Everything is Encrypted
For any sensitive work information, end-to-end encryption is a must. This includes ensuring any service providers you work with encrypt their services to prevent unauthorized access, as well as ensuring your users’ devices and your systems are encrypted as well.
5. Internet of Things (IoT) Devices
The types of mobile devices that access your organization’s systems are branching out from mobile phones and tablets to include wearable tech (like the Apple Watch) and physical devices (like Google Home or Alexa). And since many of the latest IoT mobile devices have IP addresses, it means bad actors can use them to gain access to your organizations’ network over the internet if those devices are connected to your systems.
Statistically, there are probably more IoT devices connected to your networks than you realize. For example, 78% of IT leaders from four different countries reported in a study by Infoblox that over 1,000 shadow IoT devices accessed their networks each day.
How to Combat Shadow IoT Threats
Mobile device management (MDM) tools can help you combat shadow IoT threats, as well as identity and access management (IAM) tools like Auth0. However, IoT/Machine-to-Machine (M2M) security is still in a bit of a “wild west” phase at the moment. So it’s up to each organization to put the appropriate technical and policy regulations in place to ensure their systems are secure.
6. Spyware
Spyware is used to survey or collect data and is most commonly installed on a mobile device when users click on a malicious advertisement (“malvertisement”) or through scams that trick users into downloading it unintentionally.
Whether your employees have an iOS or Android device, their devices are targets ripe for data mining with spyware—which could include your private corporate data if that device is connected to your systems.
How to Protect Against Spyware
Dedicated mobile security apps (like Google’s Play Protect) can help your employees detect and eliminate spyware that might be installed on their devices and be used to access company data. Ensuring your employees keep their device operating systems (and applications) up to date also helps ensure that their devices and your data are protected against the latest spyware threats.
7. Poor Password Habits
A 2020 study by Balbix found that 99% of the people surveyed reused their passwords between work accounts or between work and personal accounts. Unfortunately, the passwords that employees are reusing are often weak as well.
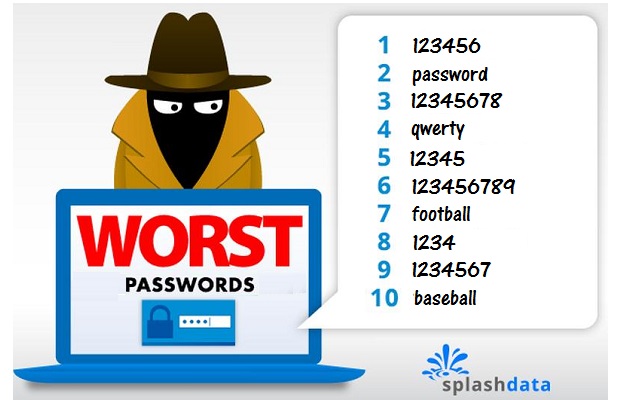
For example, a 2019 study by Google found that 59% of the people they surveyed used a name or a birthday in their password, and 24% admitted to using a password like one of these below:
These bad password habits present a threat to organizations whose employees use their personal devices to access company systems. Since both personal and work accounts are accessible from the same device with the same password, it simplifies the work a bad actor has to do in order to breach your systems.
However, these behaviors also provide opportunities for credential-based brute force cyberattacks like credential stuffing or password spraying because cybercriminals can use weak or stolen credentials to access sensitive data through company mobile apps.
How to Reduce or Eliminate Mobile Password Threats
The NIST Password Guidelines are widely regarded as the international standard for password best practices. Following these guidelines—and insisting your employees do the same—will help protect you against threats from weak or stolen passwords. Password managers can simplify the work required for your employees to follow these guidelines.
Requiring your employees to use more than one authentication factor (multi-factor authentication or MFA) to access mobile company applications will also help reduce the risk that a bad actor could gain access to your systems since they’d need to verify their identity with additional authentication factors in order to log in.
Finally, implementing passwordless authentication will help you eliminate password risks altogether. For example, in the event that a mobile device is stolen or accessed illegally, requiring a facial scan as a primary (or secondary) authentication factor could still prevent unauthorized access.
8. Lost or Stolen Mobile Devices
Lost and stolen devices aren’t a new threat for organizations. But with more people working remotely in public places like cafes or coffee shops and accessing your systems with a wider range of devices, lost and stolen devices pose a growing risk to your organization.
How to Protect Against Lost or Stolen Device Threats
First and foremost, you’ll want to ensure employees know what steps to take if they lose their device. Since most devices come with remote access to delete or transfer information, that should include asking employees to make sure those services are activated.
Mobile device management (MDM) tools can also help you secure, encrypt, or wipe sensitive company information from a device that’s lost or stolen, so long as those tools were installed before the device went missing.
9. Out of Date Operating Systems
Like other data security initiatives, mobile security requires continuous work to find and patch vulnerabilities that bad actors use to gain unauthorized access to your systems and data.
Companies like Apple and Google address a lot of these vulnerabilities with operating system updates. For example, in 2016, Apple realized it had three zero-day vulnerabilities that left its devices open for spyware attacks and released a patch to protect users against these vulnerabilities.
However, these patches only protect your organization if your employees keep their devices up to date at all times. And according to Verizon’s Mobile Security Index Report, operating system updates on 79% of the mobile devices used by enterprises are left in the hands of employees.
How To Keep Mobile Operating Systems Up To Date
Google and Apple both allow organizations to push updates to managed Android and iOS devices. Third-party MDM tools (for example, Jamf) often provide this functionality as well.
IAM Tools Can Help Secure Company Mobile Applications
Identity and Access Management (IAM) tools can help organizations secure the apps and data that users access from their mobile devices, including:
- Restricting which devices and users can access enterprise applications and data, as well as which parts of those applications they’re allowed to access.
- Tracking user behavior and securing access in the event that something looks suspicious with security features like multi-factor authentication (MFA),brute force attack protection, and more.
Auth0 simplifies the work required to implement secure authentication for mobile enterprise applications—learn more about Auth0’s IDaaS platform here.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0 (Auth0 Alumni)
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile