When it comes to handling identity and access management in the .NET platform, ASP.NET Core Identity is a fantastic starting point. It provides a full-featured, out-of-the-box solution for managing users, roles, and authentication in ASP.NET Core applications that is simple to set up and use. However, as applications grow in complexity and authentication and authorization requirements become more challenging, ASP.NET Core Identity may start showing its limitations.
This article explores the limitations of ASP.NET Core Identity, the technical reasons behind these challenges, and discusses alternative solutions.
Why ASP.NET Core Identity?
Before diving into its limitations, let’s first understand why ASP.NET Core Identity is so popular. ASP.NET Core Identity is a membership system that provides common features like user registration, login, role management, and claims-based authentication. It is tightly integrated with the ASP.NET Core ecosystem and supports both cookie-based and token-based authentication (starting with .NET 8). It offers several key features out of the box:
- User Registration and Login. ASP.NET Core Identity simplifies user registration and login processes, including options for password recovery, email confirmation, and Multi-Factor Authentication (MFA).
- Role-based Authorization. The system allows for granular control over user roles and permissions, which is essential for access control.
- External Authentication. ASP.NET Core Identity supports various external authentication providers, such as Google, Facebook, and Microsoft, allowing users to sign in using their existing credentials from these platforms.
- Customizability. Developers can customize the system to fit their needs, adding additional fields to the user model, integrating with other services, and defining custom password policies.
While ASP.NET Core Identity is highly effective for small to medium-sized applications with basic authentication needs, its limitations become apparent in more advanced scenarios.
Limitations of ASP.NET Core Identity
What are the limitations you may encounter when your application needs to grow in the context of security and user management? Let's explore some of the main scenarios.
Support for Standard Authentication Protocols
One of the primary limitations of ASP.NET Core Identity is its lack of support for advanced authentication protocols, such as OAuth 2.0, OpenID Connect (OIDC), and SAML. These protocols are crucial for implementing Single Sign-On (SSO) across multiple applications and integrating with third-party Identity providers.
While it can integrate with an external authentication service, this requires external libraries or a separate service to handle the authentication and authorization, adding complexity to the application.
Single Sign-On and Federation
SSO is an essential feature for many organizations. It allows users to log in once and access multiple systems without needing to authenticate again. This is particularly important for enterprises with multiple applications that rely on centralized authentication.
ASP.NET Core Identity is designed primarily for a single application context. While it’s possible to set up SSO in ASP.NET Core Identity by manually configuring external authentication providers (like Google, Microsoft, Facebook, or other enterprise systems), doing so is cumbersome and doesn’t scale well.
Setting up SSO with complex protocols like SAML 2.0 or OpenID Connect can be challenging. You often need to rely on third-party libraries and write a lot of boilerplate code, which can be time-consuming and error-prone.
In addition, if your application totally relies on an external Identity provider, the ASP.NET Core infrastructure, including the user database, becomes useless.
Token Management
While .NET 8 introduced token-based authentication endpoints for Single-Page Applications (SPAs), these endpoints are limited in functionality compared to full-fledged OIDC or OAuth 2.0 implementations. For instance:
- By default, the tokens generated by ASP.NET Core Identity are not configured as JSON Web Tokens (JWTs).
- Advanced OAuth flows like client credentials or device authorization are not natively supported.
- Handling token refresh, revocation, or issuing custom tokens for various clients can be cumbersome with ASP.NET Core Identity.
Microservices and Distributed Architectures
In modern application architectures, microservices are becoming increasingly popular. A key challenge in microservices is managing authentication and authorization across multiple services, each potentially using a different technology stack.
ASP.NET Core Identity isn’t designed with microservices in mind. While it can work in monolithic applications, when dealing with a microservices architecture, you often need a solution that can provide centralized authentication and authorization, preferably using token-based authentication.
In a microservices-based system, you might need to authenticate users once (e.g., OpenID Connect) and propagate tokens across multiple services (e.g., using OAuth 2.0). ASP.NET Core Identity is not ideal for this setup as it’s typically used for stateful session management, which is not optimal for distributed systems.
Scalability and Performance
For high-traffic applications with millions of users, the default ASP.NET Core Identity database schema might become a bottleneck. While adequate for smaller applications, it isn't optimized for high-volume scenarios. Customizing the schema or implementing caching strategies is necessary but requires a deep understanding of the underlying database.
Multitenancy
ASP.NET Core Identity is inherently designed for single-tenant applications, i.e., an application that manages a single set of users, typically belonging to one organization. A multi-tenant application is one in which a single instance serves multiple organizations or customers, each with its own set of users. This is a common scenario in SaaS (Software-as-a-Service) applications, where each customer (tenant) has different users, roles, and permissions.
ASP.NET Core Identity does not provide built-in support for multi-tenant architectures. While it is possible to configure the system to work in a multi-tenant environment by creating separate user stores for each tenant, this approach can be cumbersome to manage and doesn’t scale well.
Advanced Security Features
Implementing advanced security features like MFA with complex policies, FIDO2 credentials and passkeys, adaptive authentication, or risk-based authentication requires significant custom development. While ASP.NET Core Identity supports basic MFA, it lacks the flexibility to implement dynamic policies based on user behavior or risk profiles.
Also, exposing protected APIs to third-party applications with ASP.NET Core Identity is possible, but it requires careful implementation of JWT-based authentication and authorization. Managing token issuance, validation, and revocation becomes critical, and inconsistencies can lead to security vulnerabilities. This is definitely a task for OAuth 2.0 and OIDC-compliant identity providers.
Advanced Customization Requirements
ASP.NET Core Identity's default implementation often requires significant customization to meet unique business requirements:
- Customizing the Identity API endpoints is challenging. For example, you cannot easily modify the data required for user registration or add unsupported authentication methods like WebAuthn.
- The default UI for identity management forces you to use server-rendered pages unless you override them entirely.
- Managing hierarchical roles or permissions is not natively supported.
- Implementing fine-grained authorization for specific resources requires significant additional work.
Security Concerns
Security is a major consideration when building any authentication system. While ASP.NET Core Identity provides some basic security features, the default configuration of ASP.NET Core Identity may expose vulnerabilities:
Endpoints like
/registerare not natively protected, allowing unauthorized access if not explicitly secured.Without careful configuration, token expiration and refresh mechanisms can introduce security risks.
Also, it does not cover all the advanced security needs that modern applications require. Features like brute-force protection, IP whitelisting, user account lockouts, and MFA are important for securing an application’s authentication system. While ASP.NET Core Identity does provide some of these features (like MFA and account lockouts), more sophisticated threat protection features are often needed in high-risk environments.
Self-Hosted Alternative Solutions
When you encounter one or more of the limitations discussed in the previous section, it is time to look for alternative solutions. A first option could be to replace ASP.NET Core Identity with a self-hosted standards-based Identity and access management solution.
Among the most popular self-hosted solutions in the .NET ecosystem, we can mention Identity Server and Keycloak. Both offer more advanced identity and access management capabilities than ASP.NET Core Identity. Specifically:
- They support standard protocols, such as OpenID Connect and OAuth 2.0. Both products are OIDC-certified, which means they passed the tests that ensure compliance with the OIDC specifications. In terms of SAML support, while Keycloak supports it natively, Identity Server supports SAML via a specific component.
- They offer a centralized authentication solution enabling SSO and Federated Identity.
- Support for mutitenancy depends on the specific product you are going to use. While Keycloak has native support for mutitenancy through realms, supporting robust mutitenancy with Identity Server requires careful planning and implementation.
- Support for advanced authentication mechanisms like passkeys is natively available in recent versions of Keycloak while it requires specific integration of third-party libraries in Identity Server.
Using a self-hosted solution like Identity Server or Keycloak certainly overcomes some of ASP.NET Core Identity's major limitations, especially regarding SSO and standards compliance. In terms of other features, much depends on the specific product and your needs in protecting your users' identities.
Cloud-Based Solutions
Using a self-hosted solution, you still have to deal with issues that can become problematic as your application and its needs grow.
Leaving aside the features that your specific scenario requires, you still have to deal with your application's performance, high availability, and security. In other words, maintaining the efficiency and security of the Identity management solution is entirely up to you. You will have to follow the evolutions of the chosen self-hosted solution and apply updates promptly after verifying them. You will have to deal with scaling the authentication system as the number of users and concurrent requests grows. You will have to learn to do a job that is probably not yours.
Cloud-based solutions such as Auth0 offer you significant benefits in this regard.
In addition to features that certainly go beyond those offered by self-hosted solutions and advanced customization possibilities, a cloud solution like Auth0 allows you to delegate the task of taking care of the security and maintenance of the Identity management of your application. No need to keep the system updated and take care of configuring the entire infrastructure to keep the identity of your users safe. In addition, you can take advantage of advanced security tools such as Anomaly Protection, Brute Force Protection, Bot Detection, and other features to armor your application's authentication system.
Try out Auth0 authentication for free.
Get started →Wrapping Up
Choosing the right IAM solution depends on your specific needs and priorities. If you're building a simple application and need basic user management, ASP.NET Core Identity might be sufficient. For complex scenarios requiring SSO, federation, or advanced security features, IdentityServer or Keycloak are excellent self-hosted alternatives. If you prefer to offload the complexities of IAM and prioritize scalability and ease of use, a managed solution like Auth0 is a great option.
Here is a table that summarizes the main features supported by ASP.NET Core Identity compared with Identity Server, Keycloak, and Auth0 for your quick reference:
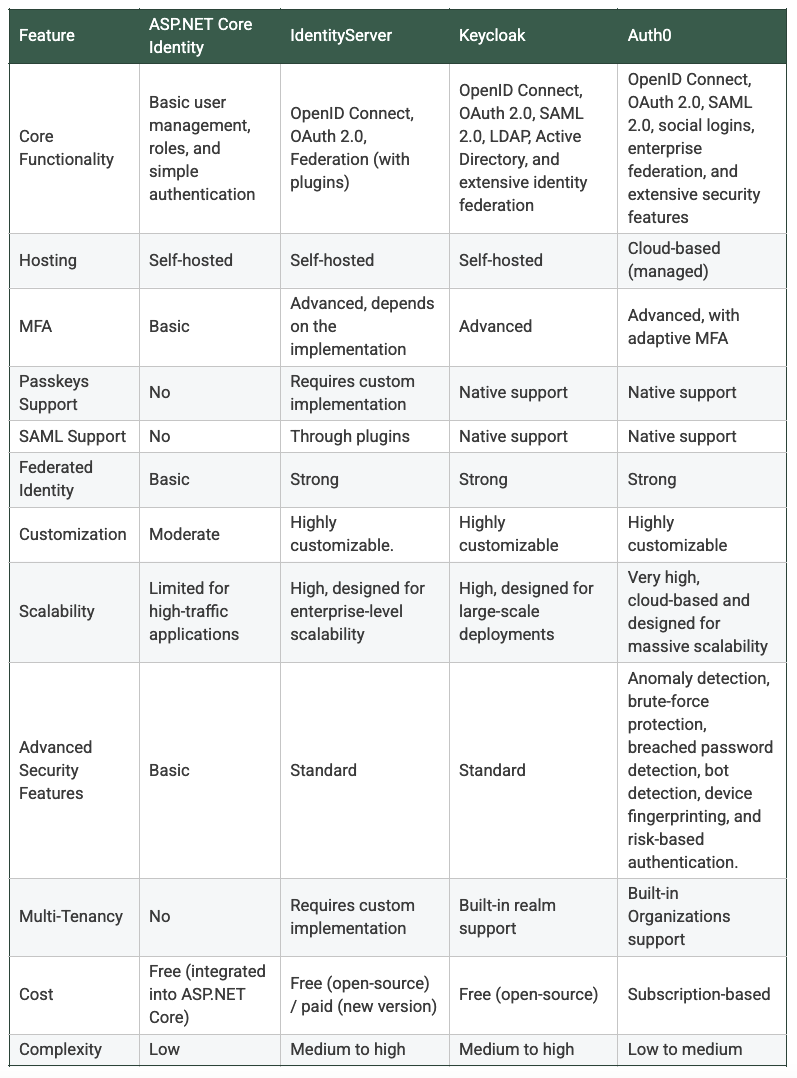
Remember to carefully evaluate your requirements and consider the tradeoffs between cost, complexity, and control before making a decision.
About the author

Andrea Chiarelli
Principal Developer Advocate
I have over 20 years of experience as a software engineer and technical author. Throughout my career, I've used several programming languages and technologies for the projects I was involved in, ranging from C# to JavaScript, ASP.NET to Node.js, Angular to React, SOAP to REST APIs, etc.
In the last few years, I've been focusing on simplifying the developer experience with Identity and related topics, especially in the .NET ecosystem.
