Consent dialog
If a user authenticates through a third-party application and the application requests authorization to access the user’s information or perform some action at an API on their behalf, the user will see a consent dialog. For example, this request: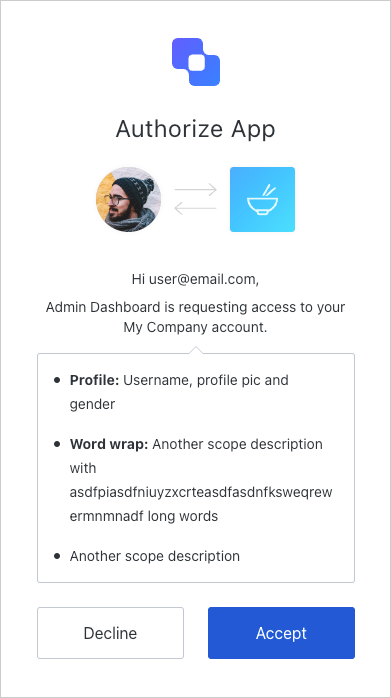
Scope descriptions
By default, the consent page will use the scopes’ names to prompt for the user’s consent. As shown below, you should define scopes using theaction:resource_name format.
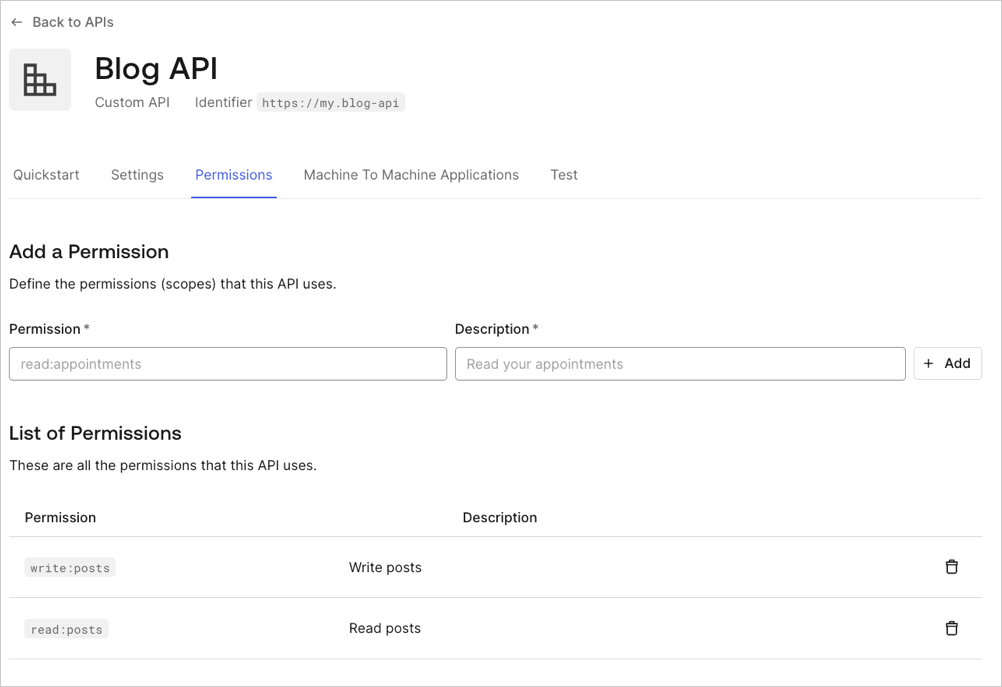
use_scope_descriptions_for_consent to true. This will affect consent prompts for all of the APIs on that tenant.
To set the use_scope_descriptions_for_consent flag, you will need to make the appropriate call to the API:
Handle rejected permissions
If a user decides to reject consent to the application, they will be redirected to theredirect_uri specified in the request with an access_denied error:
Skip consent for first-party applications
First-party applications can skip the consent dialog, but only if the API they are trying to access on behalf of the user has the Allow Skipping User Consent option enabled. To navigate to the Allow Skipping User Consent toggle, select Applications > APIs > (select the api) > Settings > Access Settings.User consent and applications
Note that this option only allows verifiable first-party applications to skip consent at the moment. As
localhost is never a verifiable first-party (because any malicious application may run on localhost for a user), Auth0 will always display the consent dialog for applications running on localhost regardless of whether they are marked as first-party applications. During development, you can work around this by modifying your /etc/hosts file to add an entry such as the following:127.0.0.1 myapp.exampleSimilarly, you cannot skip consent (even for first-party applications) if localhost is used in the application’s redirect_uri parameter and is present in any of the application’s Allowed Callback URLs (found in Dashboard > Applications > Settings).Revoke consent
If a user has provided consent but you would like to revoke it:- Go to Auth0 Dashboard > User Management > Users, and click the user for whom you would like to revoke consent.
- Click the Authorized Applications tab,
- Click Revoke next to the appropriate application.
Password-based flows
When using the Resource Owner Password Flow, no consent dialog is involved because the user directly provides their password to the application, which is equivalent to granting the application full access to the user’s account.Force users to provide consent
When redirecting to the/authorize endpoint, including the prompt=consent parameter will force users to provide consent, even if they have an existing user grant for the application and requested scopes.

