Private Key JWT is available for customers on the Enterprise plan. To upgrade, contact Auth0 pricing.
private_key_jwt or enable existing applications to use private key pairs for authentication.
Prerequisites
Before configuring an application that authenticates using Private Key JWT, you must generate an RSA key pair.Configure Private Key JWT
- Auth0 Dashboard
- Management API
You can use the Auth0 Dashboard to create a new application and configure the credentials or update an existing application.We recommend you securely store the current Configure a new application for
client_secret parameter before you set your application credential method to Private Key JWT. The client_secret parameter will be hidden once the Private Key JWT configuration is complete.Configure a new application for private_key_jwt
- Navigate to Auth0 Dashboard > Applications > Application.
- Select Create Application.
- Choose your application type.
- Under the application settings, select the Credentials tab.
-
Under Authentication Methods, select Private Key JWT.
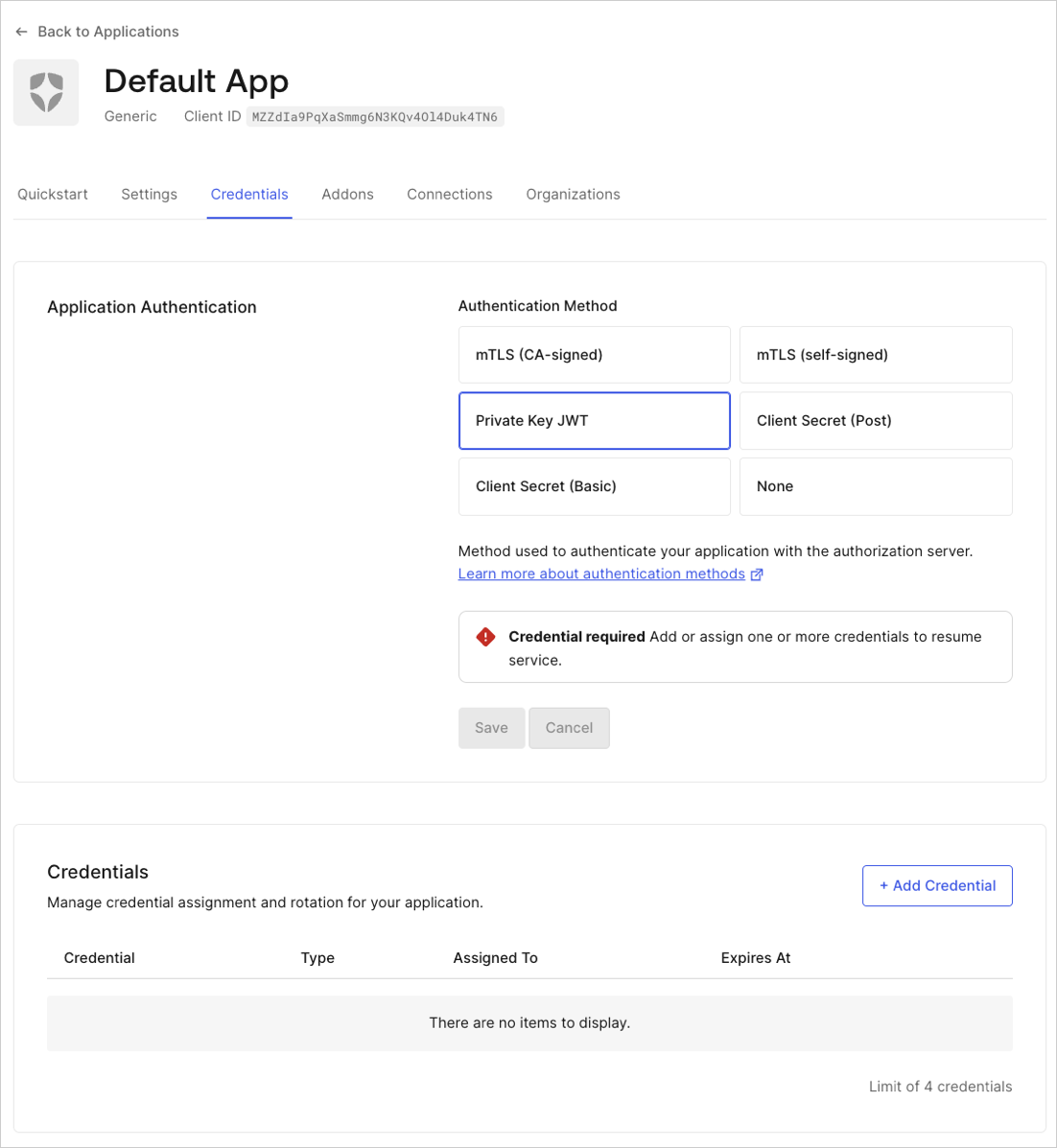
-
Configure credential details:
- Enter a name for the credential.
- Upload your PEM format or X.509 certificate.
- Select the algorithm to sign the assertions.
- Optional: Enable custom expiration. Select Set an explicit expiry date for this Credential and set a future date.
- Select Add Credential.
Configure an existing application
- Navigate to Auth0 Dashboard > Applications.
- Select the application you want to update.
- Select the Credentials tab.
- Choose Private Key JWT.
-
Configure credential details:
- Enter a name for the credential.
- Upload your PEM format or X.509 certificate.
- Select the algorithm to sign the assertions.
- Optional: Enable custom expiration. Select Set an explicit expiry date for this Credential and set a future date.
- Select Add Credential.
Configure an application to use Client Secret authentication
- Navigate to Auth0 Dashboard > Applications > Applications and select the application you want to update.
- Select the Credentials tab.
- Choose Client Secret (Post) or Client Secret (Basic).
- Select Save.
Update credential expiration
You can update an existing credential with an expiration date with Auth0 Dashboard.- Navigate to Auth0 Dashboard > Applications > Applications and select the application you want to update.
- Select the Credentials tab.
-
Choose the credential you want to update and select Edit Credential.
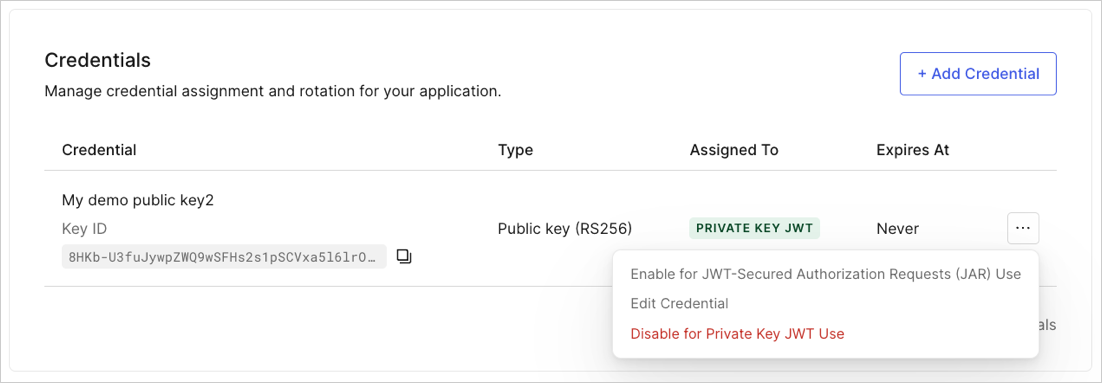
- Select Set an explicit expiry date for this Credential and set a future date.
- Select Update Credential.

