scope claim of the includes an intersection of the requested permissions and the permissions assigned to the user, regardless of whether permissions are also included in the access token. When RBAC is disabled, an application can request any permission defined for the API, and the scope claim includes all requested permissions.
If you configure any Actions that modify access token scopes, they will override the scopes set by RBAC.
Dashboard
-
Go to Dashboard > Applications > APIs and click the name of the API to view.
-
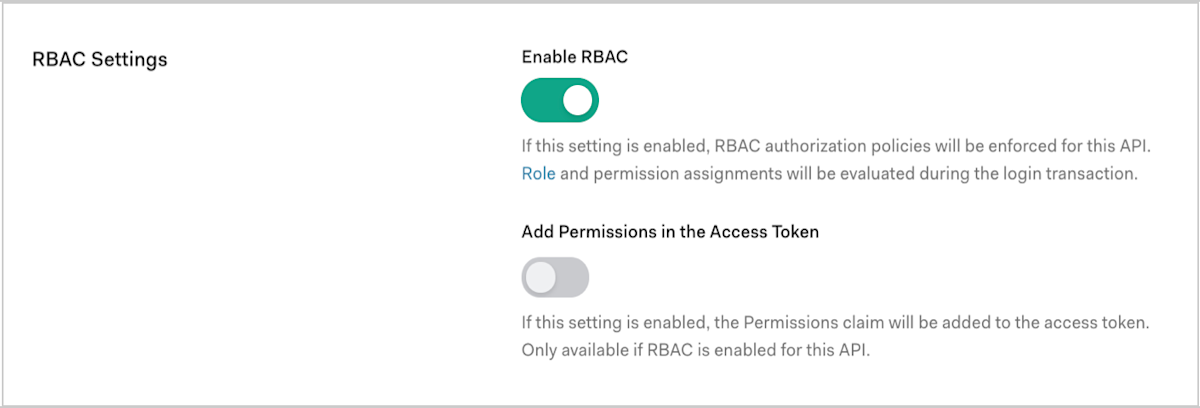
Scroll to RBAC Settings and enable the Enable RBAC toggle.
-
To include all permissions assigned to the user in the
permissionsclaim of the access token, enable the Add Permissions in the Access Token toggle, and click Save. Including permissions in the access token allows you to make minimal calls to retrieve permissions, but increases token size. Once you’ve enabled the Add Permissions in the Access Token toggle, Auth0 also updates your token dialect based on the access token profile you’ve set for the API:- If your token dialect is
access_token, Auth0 updates it toaccess_token_authz, which is equivalent to theaccess_tokenprofile with thepermissionsclaim included. - If your token dialect is
rfc9068_profile, Auth0 updates it torfc9068_profile_authz, which is equivalent to therfc9068_profilewith thepermissionsclaim included.
- If your token dialect is
Management API
To enable RBAC using the Management API, make a PATCH request to the Update a resource server endpoint. In the PATCH request, setenforce_policies to true:
Replace API_ID, MGMT_API_ACCESS_TOKEN, and TOKEN_DIALECT with their respective values, as shown in the following table:
| Parameter | Description |
|---|---|
API_ID | ID of the API for which you want to enable RBAC. |
MGMT_API_ACCESS_TOKEN | Access Token for the Management API with the scope update:resource_servers. |
TOKEN_DIALECT | Dialect of the access token for the specified API. To learn more, read Token dialect options. |
Token dialect options
Auth0 supports the following token dialects:| Value | Description |
|---|---|
access_token | The Auth0 default token profile generates an access token formatted as a JSON Web Token (JWT). In the scope claim of the access token, includes an intersection of the requested permissions and the permissions assigned to the user. No permissions claim is passed. To learn more, read Access Token Profiles. |
access_token_authz | The Auth0 default token profile (access_token) with the permissions claim. In the scope claim of the access token, includes an intersection of the requested permissions and the permissions assigned to the user. In the permissions claim of the access token, includes all permissions assigned to the user. Allows you to make minimal calls to retrieve permissions, but increases token size. |
rfc9068_profile | The RFC 9068 token profile generates an access token formatted as a JWT following the IETF JWT Profile for OAuth 2.0 Access Tokens (RFC 9068). In the scope claim of the access token, includes an intersection of the requested permissions and the permissions assigned to the user. No permissions claim is passed. To learn more, read Access Token Profiles. |
rfc9068_profile_authz | The RFC 9068 token profile (rfc9068_profile) with the permissions claim. In the scope claim of the access token, includes an intersection of the requested permissions and the permissions assigned to the user. In the permissions claim of the access token, includes all permissions assigned to the user. Allows you to make minimal calls to retrieve permissions, but increases token size. |

