To use Highly Regulated Identity features, you must have an Enterprise Plan with the Highly Regulated Identity add-on. Refer to Auth0 Pricing for details.
Generate RSA key pair
Before configuring an API to use JWE, you must generate an RSA key pair. The private key must be kept secret. Upload the public key to Auth0 encoded in PEM format as described in Generate RSA Key Pair. Only the resource server or API server can securely access the private key to decrypt the access token.Configure JWE for an API
- Auth0 Dashboard
- Management API
Use the Auth0 Dashboard to configure JWE for your API. To begin, enable the JSON Web Encryption (JWE) toggle under Token Settings for your API.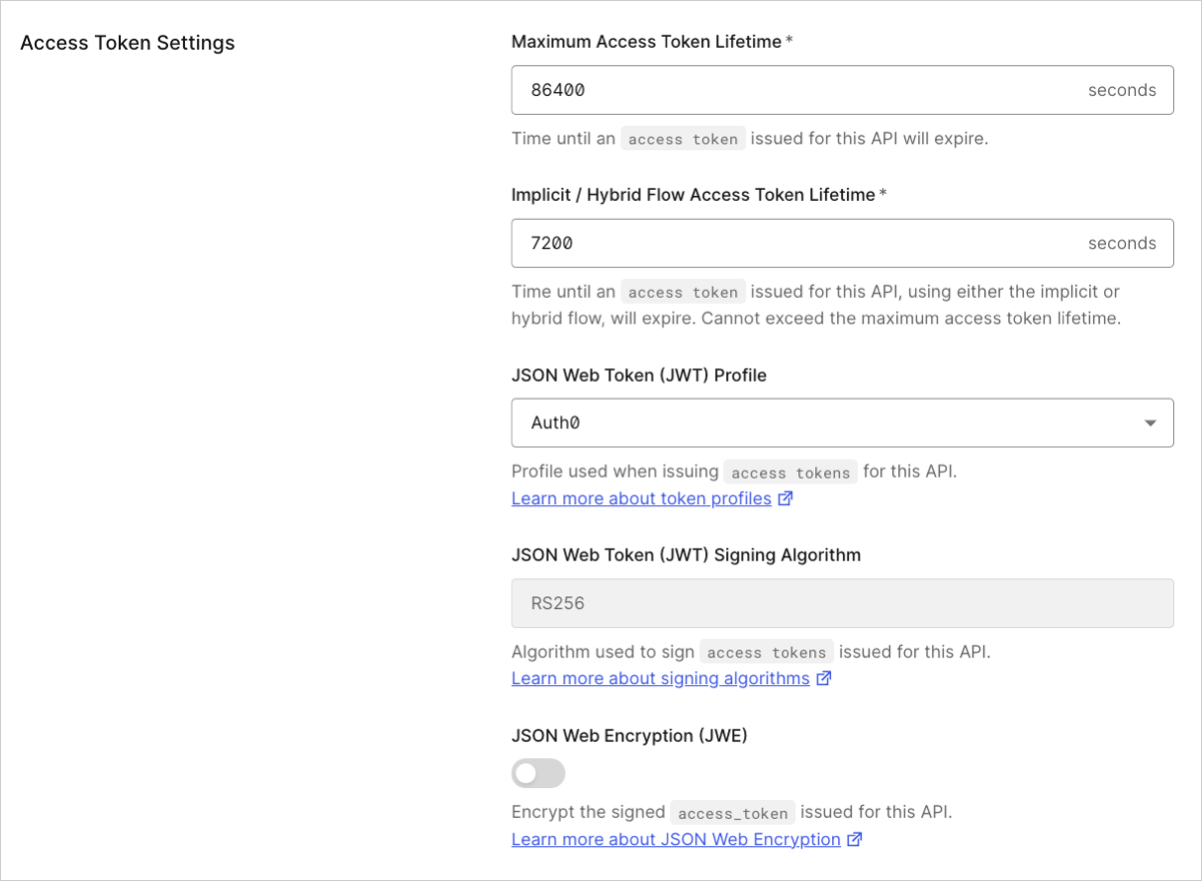 When prompted, add a JSON Web Encryption (JWE) key:
When prompted, add a JSON Web Encryption (JWE) key:

- Enter a friendly name for easy identification.
- Upload a certificate with the public key encoded in PEM format.
- Select the encryption algorithm.
- (Optional) Enter a key identifier.

