Before you start
To use one of the supported third-party CAPTCHA provider integrations, you need the provider’s configuration details. To learn more, read Configure third-party CAPTCHA provider integrations.
Configure Bot Detection
When enabled, you can customize Bot Detection preferences, such as the detection model, and response actions, which applies to all connections in your tenant. If you do not configure Response actions with Bot Detection enabled, Bot Detection operates in Monitoring mode. Monitoring mode records related events, including risk assessment details, in your tenant logs for review. To learn more, read View Attack Protection Log Events. You can enable tenant logs for Risk Assessment in the Auth0 Dashboard.- Go to Dashboard > Security > Attack Protection and select Bot Detection.
-
In the Detection section, enable the toggle.
 If you cannot see the toggle to enable tenant logs for Risk Assessment, you may need to upgrade your plan.
If you cannot see the toggle to enable tenant logs for Risk Assessment, you may need to upgrade your plan. -
In the Response section, choose a bot detection response.
When using Auth Challenge, the Fail open toggle is disabled by default.
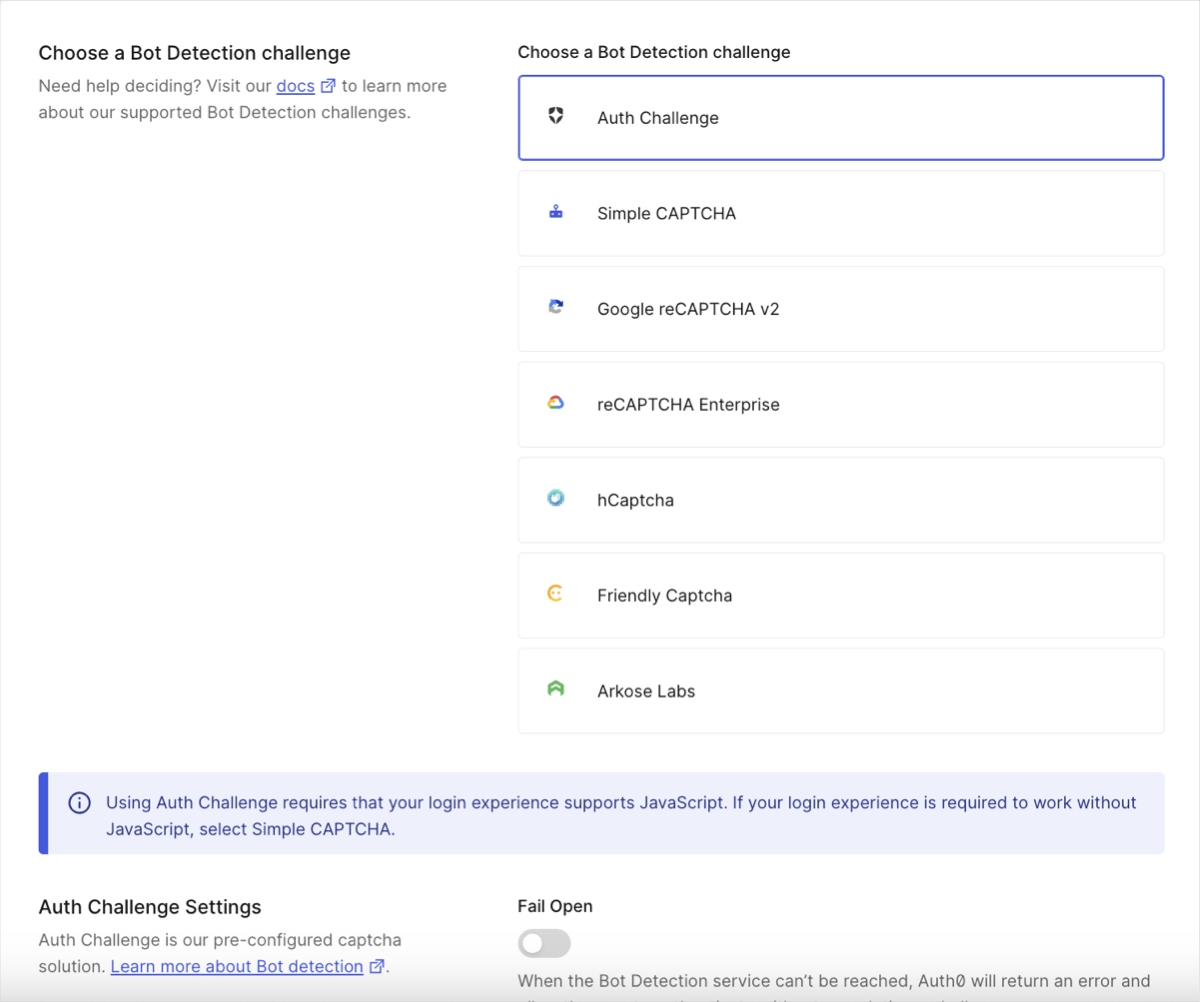 Auth Challenge is the default bot detection response, offering a CAPTCHA-free web experience with stronger privacy and a better user experience.As noted on the dashboard, this login experience requires Javascript; if your login experience is required to work without Javascript, select Simple CAPTCHA.
Auth Challenge is the default bot detection response, offering a CAPTCHA-free web experience with stronger privacy and a better user experience.As noted on the dashboard, this login experience requires Javascript; if your login experience is required to work without Javascript, select Simple CAPTCHA. -
Select when you want to require CAPTCHA for password flows, passwordless flows, and password reset flows.
- Never: Never require your users to complete a CAPTCHA to log in.
- When Risky: Only require your users to complete a CAPTCHA if the login matches your Bot Detection Level setting.
- Always: Always require your users to complete a CAPTCHA to log in.
-
If you choose When Risky or Always, the CAPTCHA Providers field will appear in the Response section. Select Auth Challenge (provided by Auth0), Simple CAPTCHA (provided by Auth0), or one of the supported third-party provider integrations (requires external setup and registration).
- If you choose Auth Challenge or Simple CAPTCHA, you are done. If your login experience does not support JavaScript, you must select Simple CAPTCHA.
- If you choose one of our third-party provider integrations, enter the provider’s configuration details. To learn more, read Configure third-party CAPTCHA provider integrations.
- If you choose Simple CAPTCHA, the CAPTCHA image is not legible to screen readers.
- If you choose When Risky, the Bot Detection Level field will appear in the Response section. Select the security level that best fits your use case. For more information, read Configure Bot Detection Level.
- Select Save.
Configure Bot Detection Level
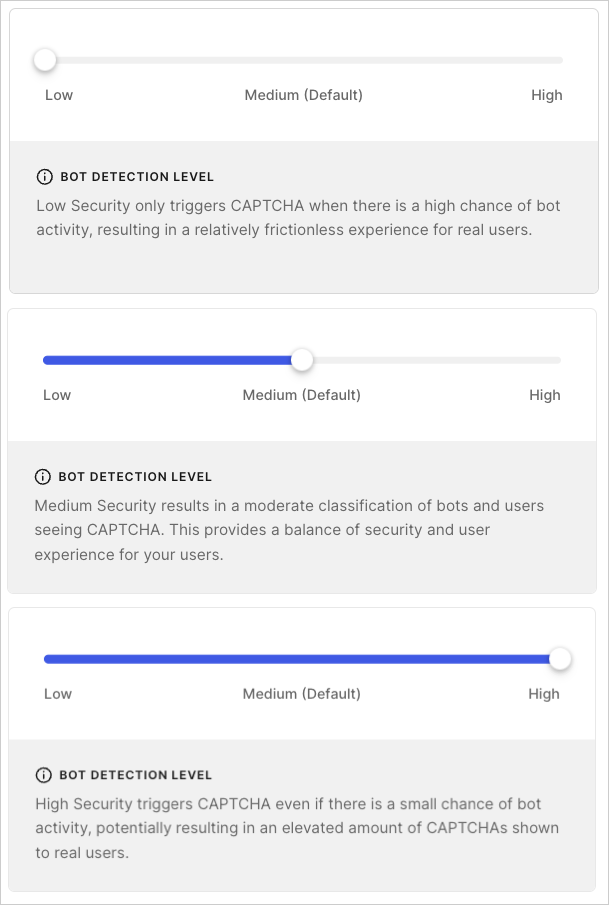
Configure the Bot Detection Level setting to match your risk tolerance and business needs. There are three settings to choose from:- Low: Triggers CAPTCHA when there is a high chance of bot activity, providing a relatively frictionless experience for real users.
- Medium: Default. Triggers CAPTCHA when there is a moderate chance of bot activity, providing a balance of security and experience for real users.
- High: Triggers CAPTCHA when there is a small chance of bot activity, providing more security but potentially more friction for real users.
Allow trusted IP addresses to bypass Bot Detection
You can allow up to 100 discrete IP addresses and/or CIDR ranges (IPv4 or IPv6) to bypass Bot Detection by adding them to the IP AllowList field. Auth0 does not enforce blocking and does not send alerts for IP addresses or CIDR ranges on this list.- Go to Dashboard > Security > Attack Protection, and select Bot Detection.
- In the IP AllowList field, enter the IP addresses and/or CIDR ranges you want to bypass Bot Detection. Separate multiple addresses or ranges with commas.
Configure signup detection model for Custom Login Page and Classic Login Experience
Auth0 provides a signup detection machine-learning model, distinct from the login model, that addresses different attack types by analyzing unique signals. This model allows CAPTCHA to behave differently between signup and login flows to provide stronger protection against signup attacks and align with the latest security advancements. You can configure the detection model that Bot Detection uses for signup flows when using a Custom Login Page or the Classic Login Experience in the .- Go to Dashboard > Security > Attack Protection, and select Bot Detection.
- Locate the Detection Models section.
- Enable the toggle for Signup detection models for custom and classic login pages.
Restrictions and limitations
Flow limitations
Bot Detection works for web and mobile applications that use Auth0 Universal Login. For applications that do not use , levels of support are limited, in particular for flows that cannot support a CAPTCHA or reCAPTCHA challenge. Ensure all of your login experiences are supported before you enable Bot Detection, or you may introduce errors into your application.| Flow | Limitation |
|---|---|
| Universal Login | Supported by default. |
| Classic Login (no customizations) | Supported by default. |
| Classic Login (Custom Login Page using Lock template) | Supported if using lock.js SDK version 12.4.0 or higher. |
| Classic Login (Custom Login Page using Custom Login Form template) | Supported if using auth0.js SDK version 9.24 or higher, and you enhance your code to handle a CAPTCHA or reCAPTCHA challenge. |
| Native applications | Supported if using one of the following SDKs:
|
| Regular Web or Native applications using Resource Owner Password Flow | Supported in a limited capacity. Bot Detection Response such as CAPTCHA requires an interactive flow and therefore is not supported. If the requires_verification error is returned by the SDK, you must trigger a web-based login flow for the user to complete authentication. |
Flows not hosted by Auth0 using lock.js or auth0.js SDK which perform cross-origin authentication (co/authenticate endpoint) | Not supported. |
Connection type limitations
Depending on the types of connections you use, Bot Detection has the following limitations.| Connection Type | Limitation |
|---|---|
| Database | Supported if the login uses a compatible login flow as described in the Flow limitations table. |
| Custom database | Supported if the login uses a compatible login flow as described in the Flow limitations table. |
| Active Directory/LDAP | Supported if the login uses a compatible login flow as described in the Flow limitations table. |
| Enterprise | Not supported. |
| Social Login | Not supported. |
| Passwordless | Supported if the login uses a compatible login flow as described in the Flow limitations table. |

