Basic settings
When you edit an existing application’s settings or create a new application, you enter information about the application in the Settings view.Basic Information
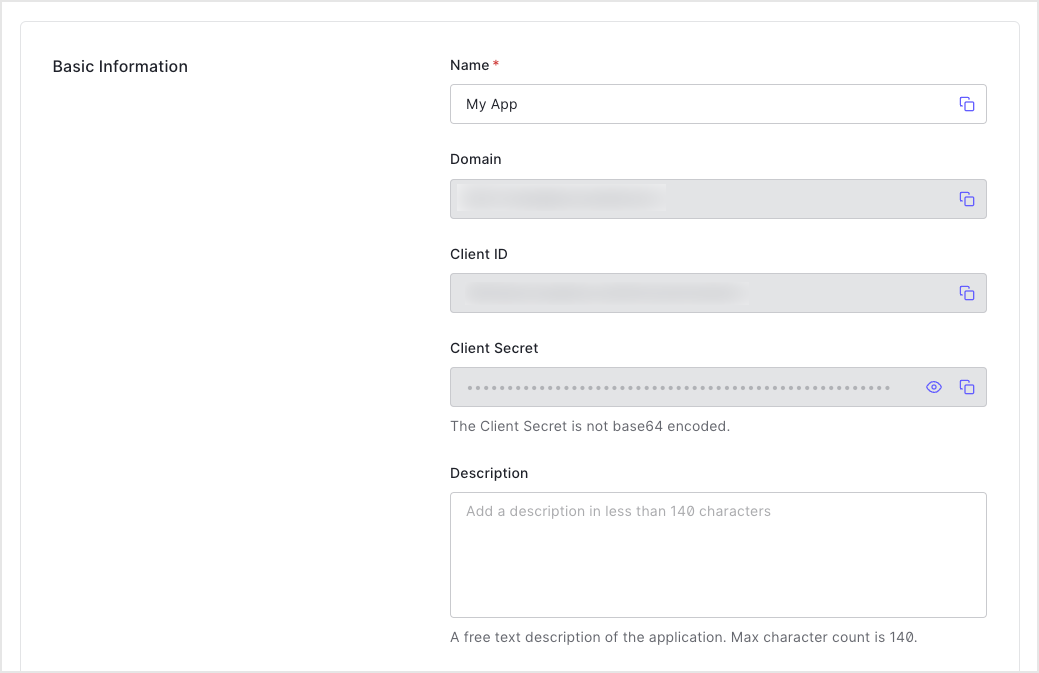
- Name: The name of your application. Editable, and will be seen in the portal, emails, logs, and so on.
- Domain: Your Auth0 tenant name. You choose this when you create a new Auth0 tenant, and it cannot be changed. If you need a different domain, you must register for a new tenant by selecting + Create Tenant in the top-right menu.
- : The unique identifier for your application. You will use this when configuring authentication with Auth0. Generated by the system when you create a new application and cannot be modified.
- : A string used to sign and validate for authentication flows and to gain access to select Auth0 API endpoints. By default, the value is hidden, so check the Reveal Client Secret box to see it. While the Client ID is considered public information, the Client Secret must be kept confidential. If anyone can access your Client Secret, they can issue tokens and access resources they shouldn’t be able to access.
- Description: A free-text description of the Application’s purpose. Maximum of 140 characters.
Application Properties
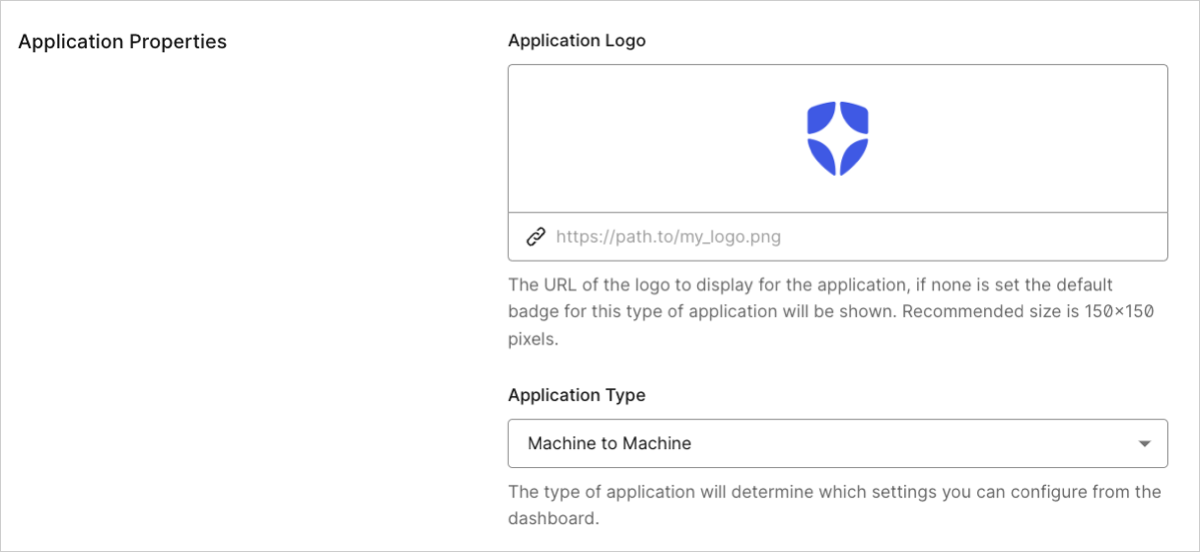
- Application Logo: The URL of a logo (recommended size: 150x150 pixels) to display for the application. Appears in several areas, including the list of applications in the Dashboard and customized consent forms. If none is set the default badge for this type of application will be shown.
-
Application Type: The Auth0 application type determines which settings you can configure using the Dashboard. (Not editable for M2M apps. Sometimes disabled for other Auth0 application types if the selected grant types are only allowed for the currently selected application type.) Use the drop-down to select from the following types:
- Machine to Machine: Non-interactive applications, such as command-line tools, daemons, IoT devices, or services running on your backend. Typically, you use this option if you have a service that requires access to an API.
- Native App: Mobile or Desktop applications that run natively in a device (such as iOS or Android).
- Regular Web App: Traditional web apps that perform most of their application logic on the server (such as Express.js or ASP.NET).
- Single Page App: JavaScript apps that perform most of their user interface logic in a web browser, communicating with a web server primarily using APIs (such as AngularJS + Node.js or React).
Application URIs
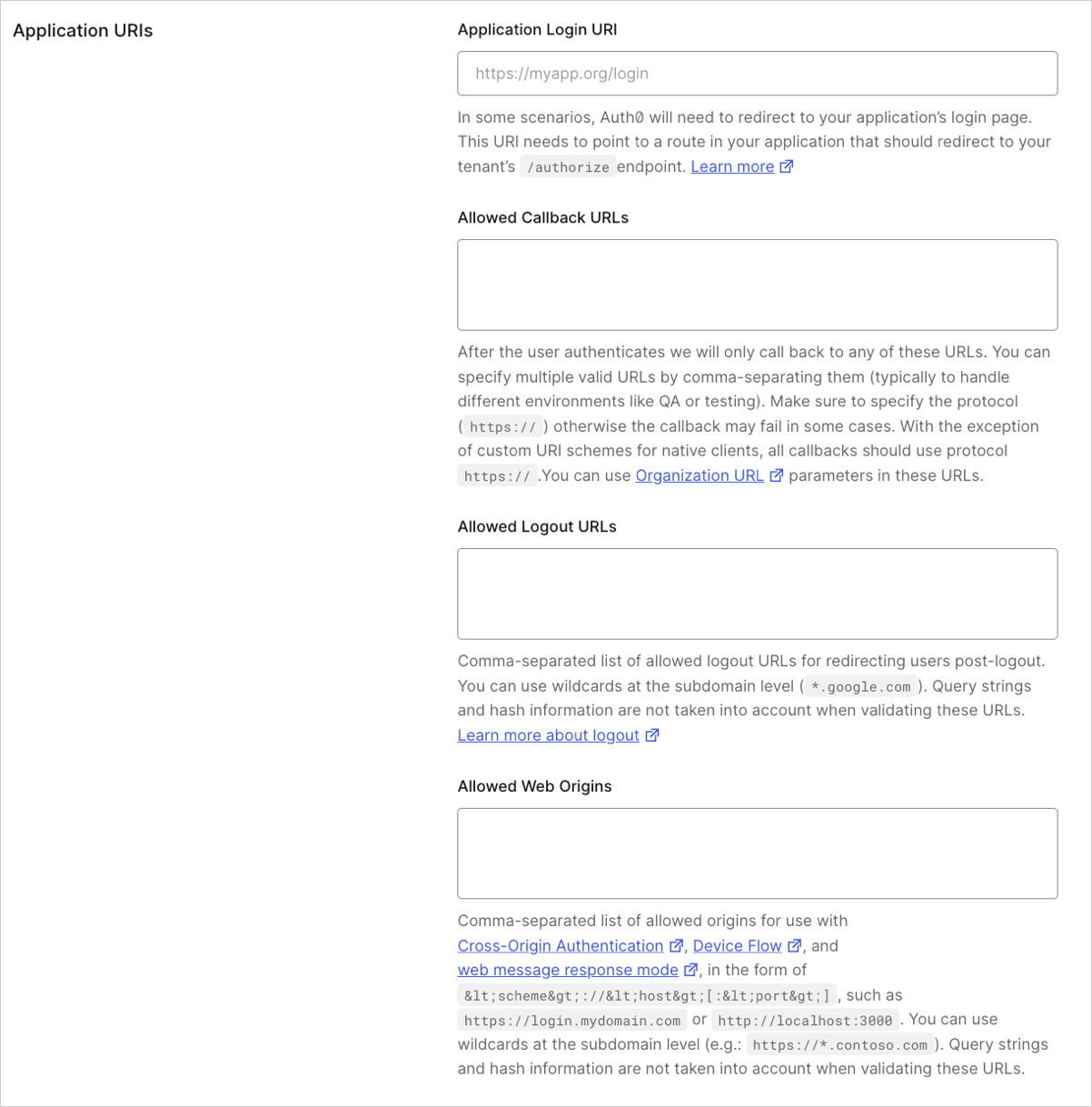
- Application Login URI: In some scenarios, Auth0 will need your application to redirect to your application’s login page. This URI needs to point to a route in your application that redirects to your tenant’s
/authorizeendpoint. It would usually take the form ofhttps://myapp.org/login. To learn more, read Configure Default Login Routes. - Allowed Callback URLs: Set of URLs to which Auth0 is allowed to redirect users after they authenticate. You can specify multiple valid URLs by comma-separating them (typically, to handle different environments like QA or testing). For production environments, verify that the URLs do not point to localhost. You can use the following placeholders in this field:
- Wildcards: Use
*for subdomains (*.google.com) Not recommended for production environments. - Organization placeholders: Use
{organization_name}to dynamically specify a registered organization’s name (for example,https://{organization_name}.example.com). - Custom Domain placeholders: Use
{custom.domain.metadata.KEY}to dynamically populate the URL based on metadata from the custom domain used in the request (for example,https://{custom_domain.metadata.public_app_url}/callback).
- Wildcards: Use
The first URL listed in this field is taken as the default callback URL when the corresponding protocol flow does not explicitly specify one. This applies specifically to SAML, WS-Fed, and SAML IdP-initiated SSO flows.
{organization_name} placeholder should be preferred, where relevant. To learn more, read Subdomain URL Placeholders.
- Allowed Logout URLs: After a user logs out from Auth0, you can redirect them with the
returnToquery parameter. The URL that you use inreturnTomust be listed here. You can specify multiple valid URLs by comma-separating them. For production environments, verify that the URLs do not point to localhost.- Wildcards: Use
*for subdomains (*.google.com) Not recommended for production environments. - Custom Domain placeholders: Use
{custom.domain.metadata.KEY}to dynamically populate the URL based on metadata from the custom domain used in the request (for example,https://{custom_domain.metadata.public_app_url}/callback).
- Wildcards: Use
- Allowed Web Origins: List of URLs from where an authorization request using Cross-Origin Authentication, Device Flow, and
web_messageas the response mode can originate from. You can specify multiple valid URLs by comma-separating them. For production environments, verify that the URLs do not point to localhost. Paths, query strings, and hash information are not taken into account when validating these URLs (and may, in fact, cause the match to fail). You can provide up to 100 URLs in the Allowed Web Origins field.- Wildcards: Use
*for subdomains (*.google.com) Not recommended for production environments. - Custom Domain placeholders: Use
{custom.domain.metadata.KEY} to dynamically populate the URL based on metadata from the custom domain used in the request (for example,https://{custom_domain.metadata.public_app_url}/callback).
- Wildcards: Use
- Allowed Origins (CORS): List of URLs that are allowed to make Cross-Origin Resource Sharing (CORS) requests to Auth0.
- Custom Domain placeholders: Use
{custom.domain.metadata.KEY}to dynamically populate the URL based on metadata from the custom domain used in the request (for example,https://{custom_domain.metadata.public_app_url}/callback).
- Custom Domain placeholders: Use
ID Token
In the ID Token section, enter the ID Token Expiration (in seconds) which is the amount of time before the Auth0id_token expires. The default value is 36000 seconds which is 10 hours.
Use Auth0 instead of the IdP to do Single Sign-on: If enabled, this setting prevents Auth0 from redirecting authenticated users with valid sessions to the identity provider (such as Facebook or ADFS). Legacy tenants only.
Refresh Token Rotation
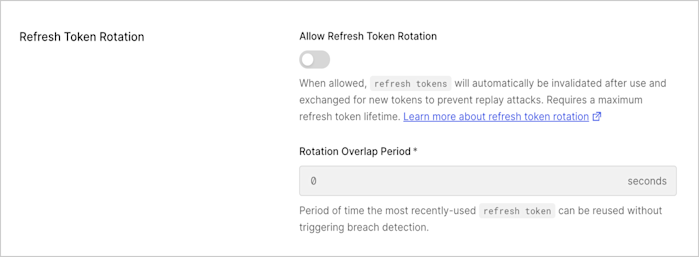
In the Rotation section, enable or disable rotation. When enabled, as a result of exchanging a refresh token, a new refresh token will be issued and the existing token will be invalidated. This allows for automatic detection of token reuse if the token is leaked. In addition, enter the Rotation Overlap Period (in seconds). This interval is the allowable leeway time that the samerefresh_token can be used to request an access_token without triggering automatic reuse detection. To learn more, read Refresh Token Rotation.
Refresh Token Expiration
In the Refresh Token Expiration section, enable or disable absolute and inactivity expiration and set the lifetimes (in seconds) for each. To learn more, read Configure Refresh Token Expiration.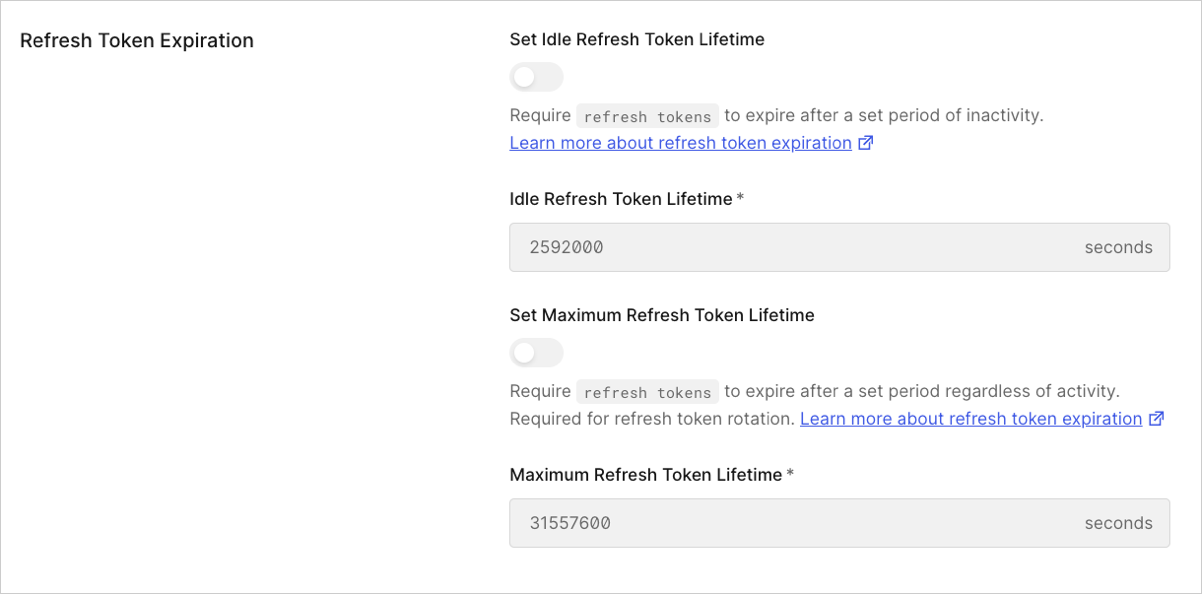
Advanced settings
The Advanced Settings section allows you to:- Manage or add application metadata, device, , and WS-Federation settings
- Obtain certificates and information
- Set the grant type(s) for the application
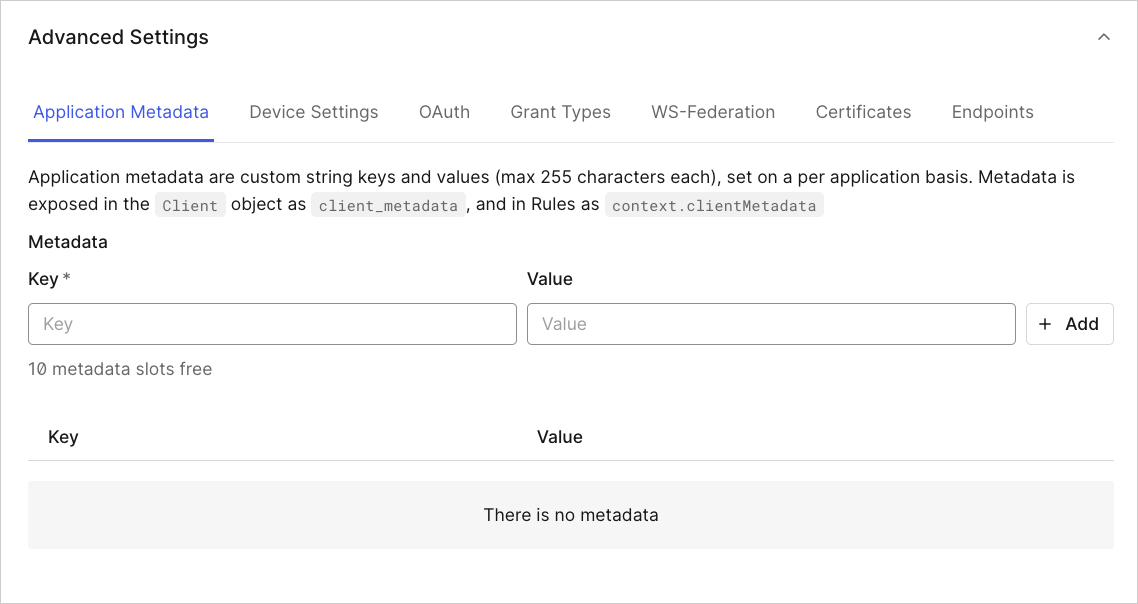
Application Metadata
Application metadata are custom string keys and values (each of which has a character maximum of 255), set on a per-application basis. Metadata is exposed in the application object asclient_metadata, and in rules as context.clientMetadata. You can create up to 10 sets of metadata.
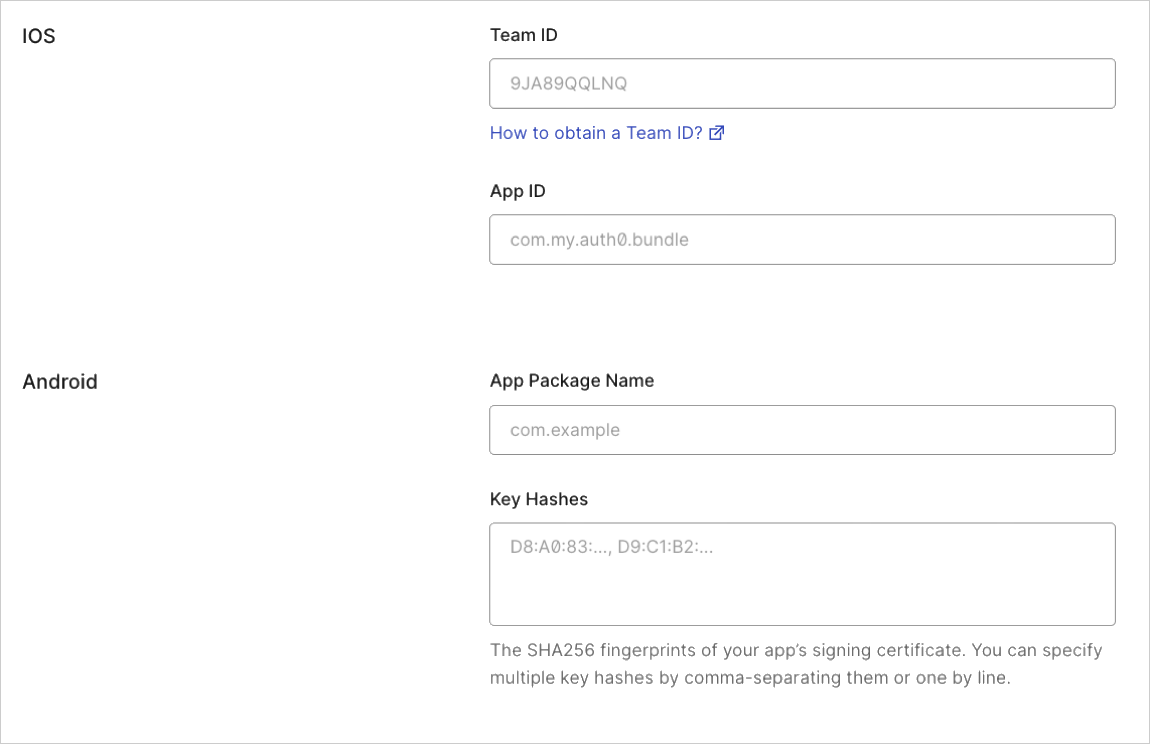
Device Settings
If you’re developing a mobile application, enter the necessary iOS/Android parameters.- When developing iOS apps, you’ll provide your Team ID and App ID. To learn more, read Enable Universal Links Support in Apple Xcode.
- When developing Android apps, you’ll provide your App Package Name and your Key Hashes. To learn more, read Enable Android App Links Support.
OAuth
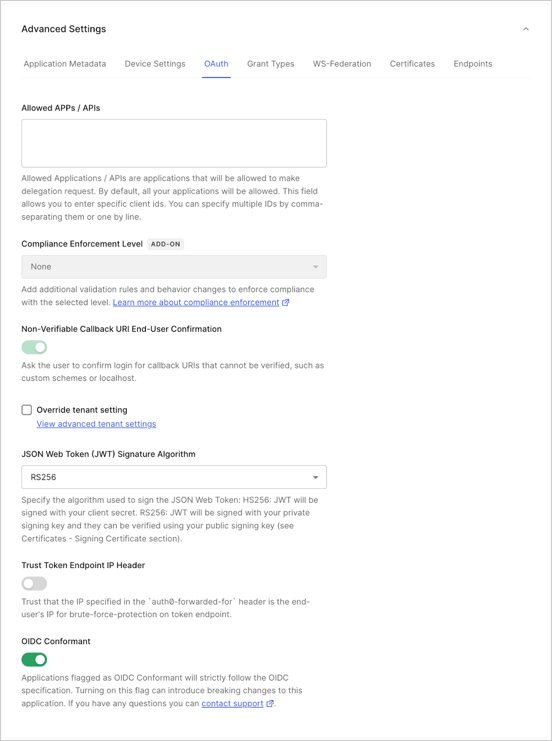
- By default, all apps/APIs can make a delegation request, but if you want to explicitly grant permissions to selected apps/APIs, you can do so in Allowed Apps/APIs.
- For customers using the Highly Regulated Identity add-on, use the Compliance Enforcement Level setting to set your level of compliance. For more information, review Configure FAPI Compliance.
- Non-Verifiable Callback URI End-User Confirmation: Use this setting to control whether the user is prompted to confirm login when a Non-verifiable URI is used as callback. Auth0 recommends that you do not skip end-user confirmation in these cases. This setting takes precedence over the tenant setting with the same name. To learn more, read Measures Against Application Impersonation.
- Set the algorithm used (HS256 or RS256) for signing your . To learn more, read JSON Web Token Signing Algorithms. When selecting
RS256(recommended), the token will be signed with your tenant’s private key. - Toggle the Trust Token Endpoint IP Header setting; if this is enabled, the
auth0-forwarded-foris set as trusted and used as a source of end user IP information for protection against brute-force attacks on the Token endpoint. This setting is only available for Regular Web Apps and M2M Apps. - Toggle the switch to indicate if your application is OIDC Conformant or not. Applications flagged as OIDC Conformant will strictly follow the OIDC specification.
Grant Types
Select grant types to enable or disable for your application. Available grant types are based on the application type.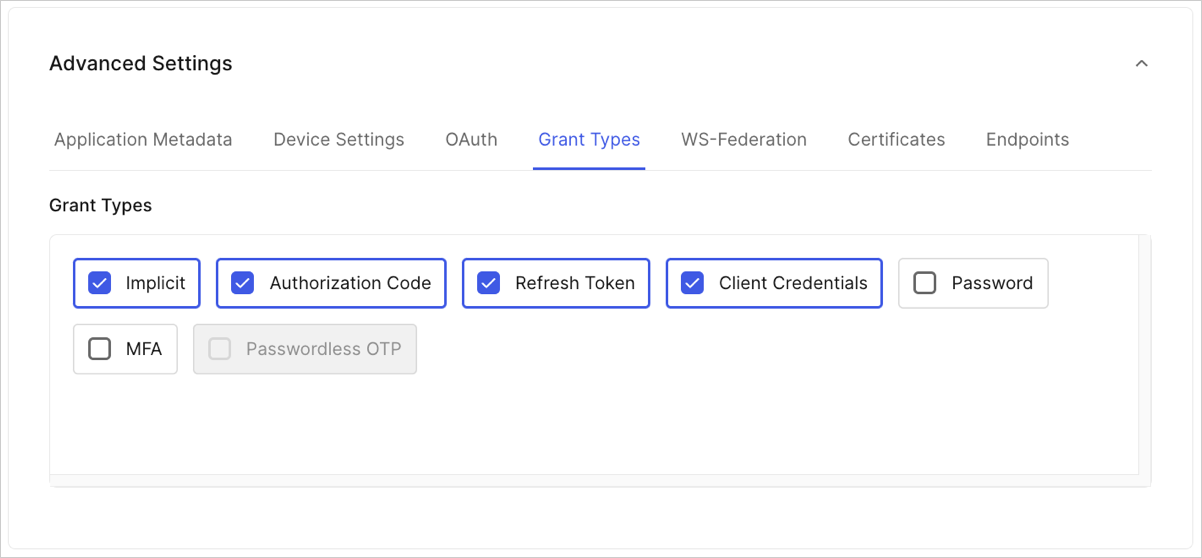
WS-Federation
Manage or add WS-Federation settings.
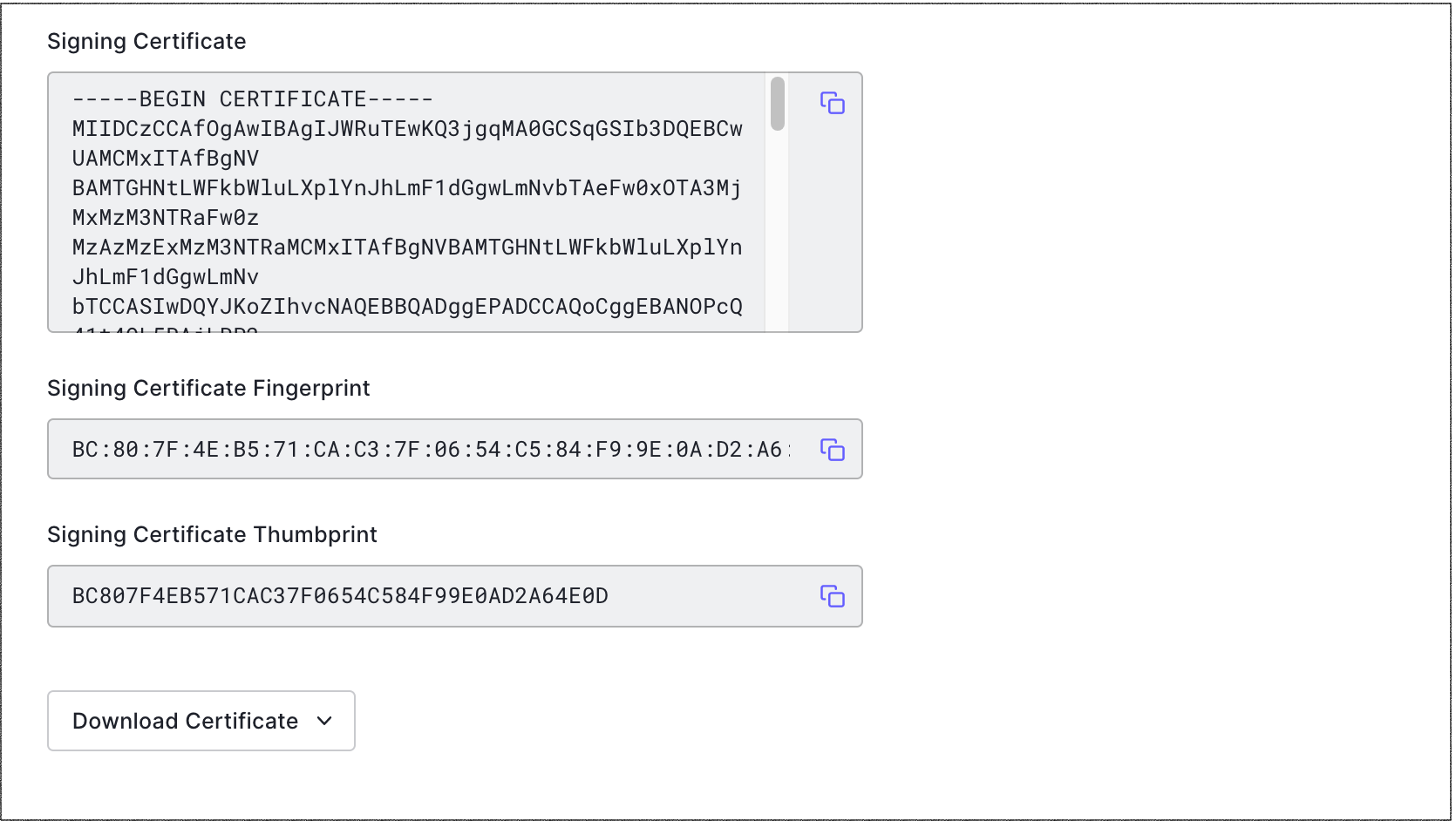
Certificates
Manage or add the signing certificate, and its fingerprint and thumbprint.