https://{yourDomain}/.well-known/``jwks.json.
If you generate your own signing keys, you can import the public key to your tenant’s /.well-known JWKS endpoint. Auth0 can be the single distribution point for Auth0 signing keys and your custom signing keys. If your business case requires your application to be embedded in remote devices, you can migrate your existing signing keys for Auth0 to publish the public key to your /.well-known endpoint.
When access tokens with your custom signing keys are being issued as a result of a user authentication and :
- Auth0’s Key Management System is responsible for protecting the signing keys you generate and provide.
- Auth0 issues tokens for authentication and authorization as the .
- Auth0 publishes a list of valid public keys at a distribution URL specific to the tenant.
- A proxy solution receives Auth0 issued tokens and makes them available to legacy applications and APIs.
- Customer applications use the issued access tokens to consume APIs and resources.
- APIs and resources servers validate the signature of the access tokens presented to them by retrieving the public key from Auth0’s JWKS distribution to perform the token signature verification.
How it works
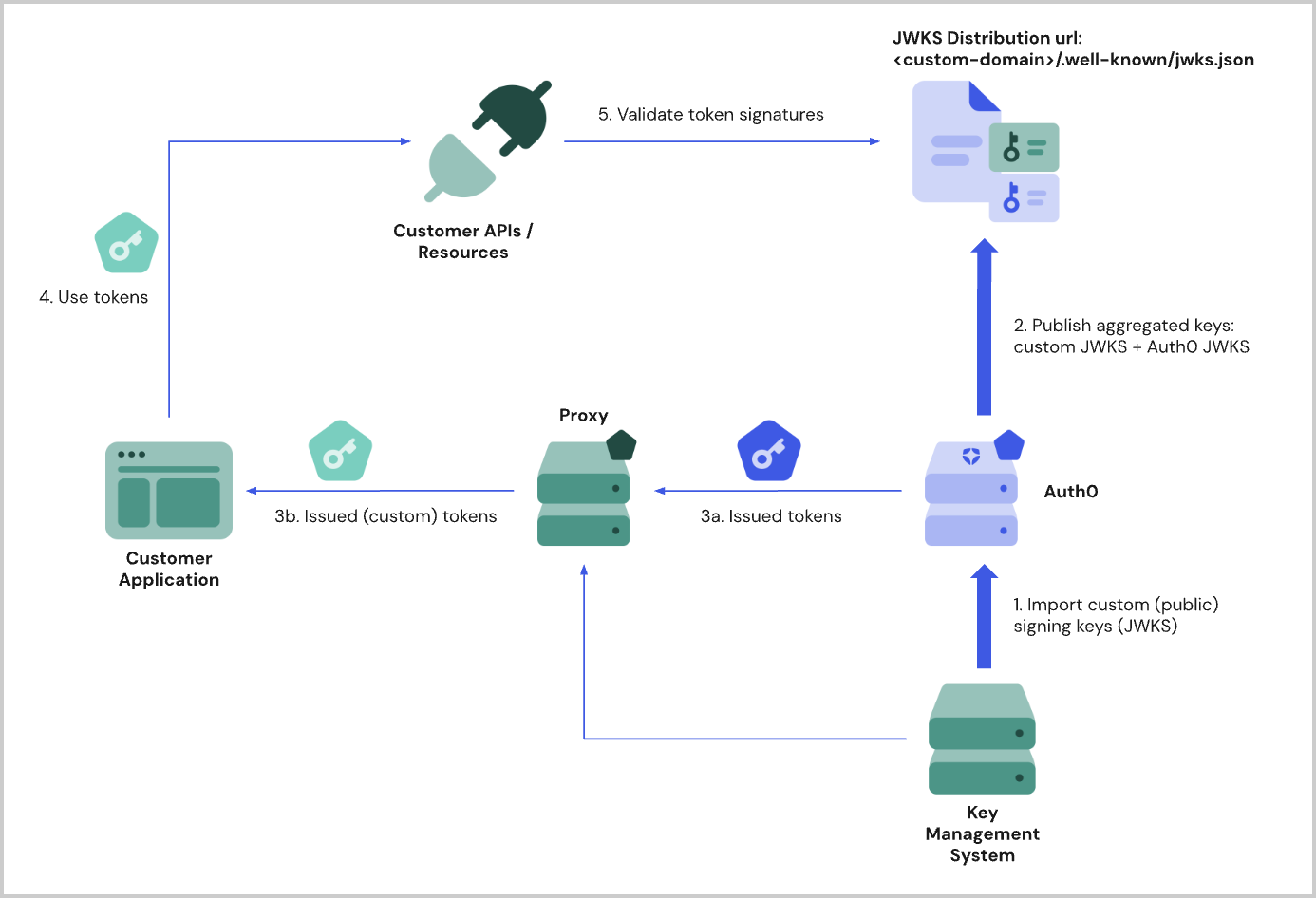
- The public part of the signing key is imported to Auth0 and pend publication to Auth0 keys as an aggregated JWKS.
- The public signing key is published to the well-known endpoint of your tenant’s custom domain:
{yourCustomDomain}/.well-known/jwks.json. - Auth0 issues access tokens. Those tokens are customized and re-signed with your signing key
- Your application uses the customized tokens for access to your resources, such as APIs.
- Auth0 distributes your key by publishing to the
/.wellknownendpoint.
Prerequisites
To import custom signing keys into Auth0, you must:- Configure a . The aggregated JWKS is served from a custom domain and is not available on the canonical domain. To learn more, read Custom Domains.
- Use Auth0’s Private Cloud. You can only import signing keys in Private Cloud environments. To learn more, read about our Private Cloud on AWS and Azure.
Configure your custom keys with Management API
Use the to upload your custom keys in the form of JWKS. To create new (replace all existing) custom keys, make aPUT call to the Create or replace custom signing keys endpoint to import a set of custom public keys into Auth0. Existing custom keys will be replaced by the new set. You can import up to ten custom keys in JWKS format.
Once imported, the custom public keys prepend to the list of Auth0-generated keys and will be published to your tenant’s well known endpoint URL for distributing JWKS.
GET call to the Get custom signing keys endpoint to retrieve the set of custom keys as an array of JWK objects.
To delete existing custom keys, make a DELETE call to the Delete custom keys endpoint to delete the custom keys.
