Configure the login experience of your application
Your application can be configured in the Login Experience tab to support three user types:- Individuals
- Business Users
- Both
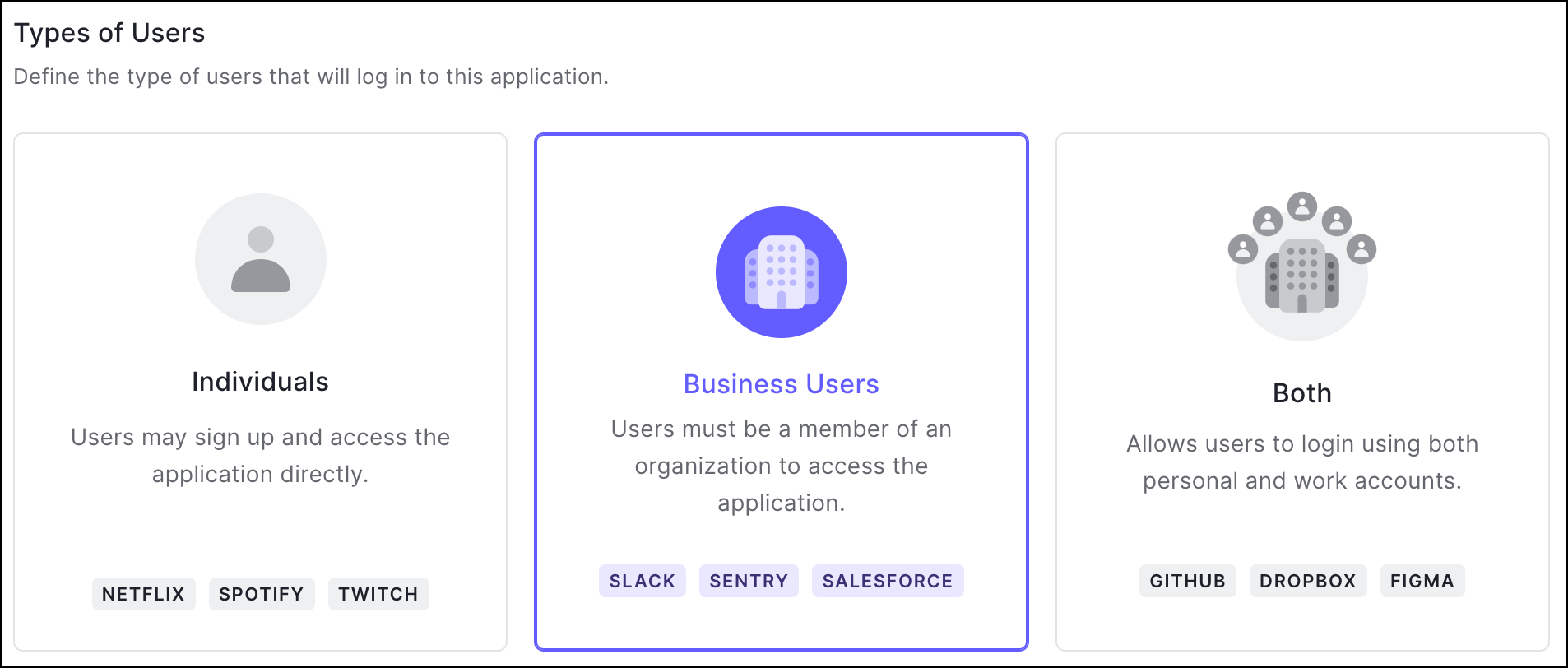
organization_usage parameter of the Update a client endpoint to set the appropriate type of user. For more information on both methods, review Define Organization Behavior.
Configure the Login Flow for your Application
After selecting Business Users or Both, you can further customize the experience that your users have when logging into your application. Most organizations should choose Prompt for Credentials, then enable Identifier First Authentication. If you already know the Organization with which a user is attempting to log in, the No Prompt option along with Custom Development with Organizations allows your app to maintain a branded and customized login flow.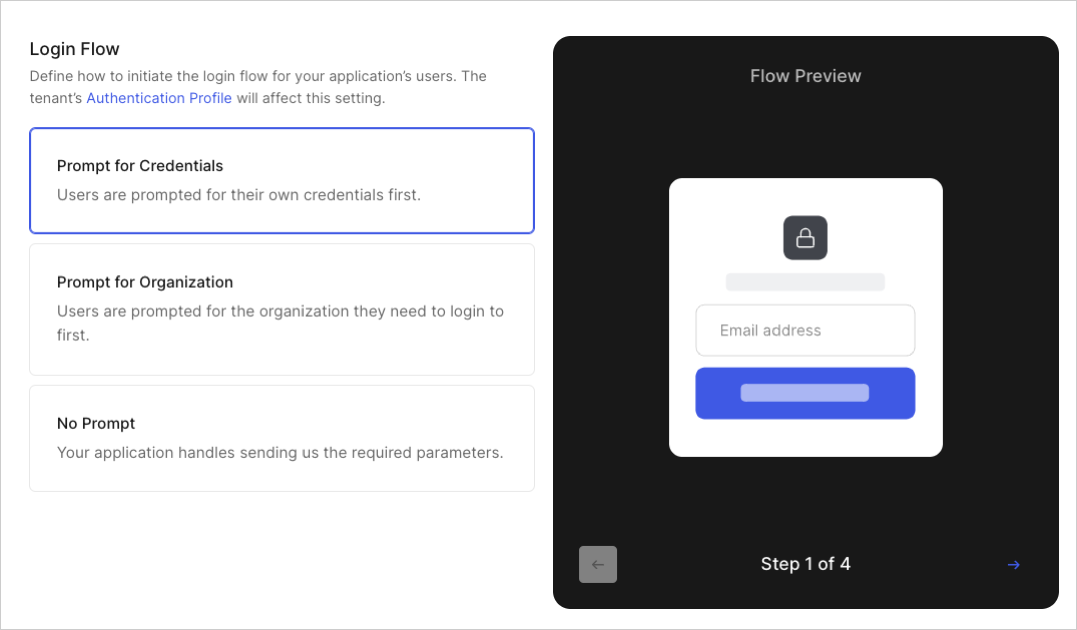
Note: Even when selecting Prompt for Credentials, you can still direct users to log in with a specific organization’s login prompt as needed.
organization_require_behavior parameter of the Update a client endpoint to set the appropriate flow. For more information on both methods, review Define Organization Behavior.
Identifier First Authentication with prompt for credentials
If your enterprise application uses Enterprise Federation, you can activate Identifier First Authentication with Home Realm Discovery in its Authentication Profile. Once enabled, Home Realm Discovery detects email addresses from a known domain and automatically sends them to the proper Workforce login.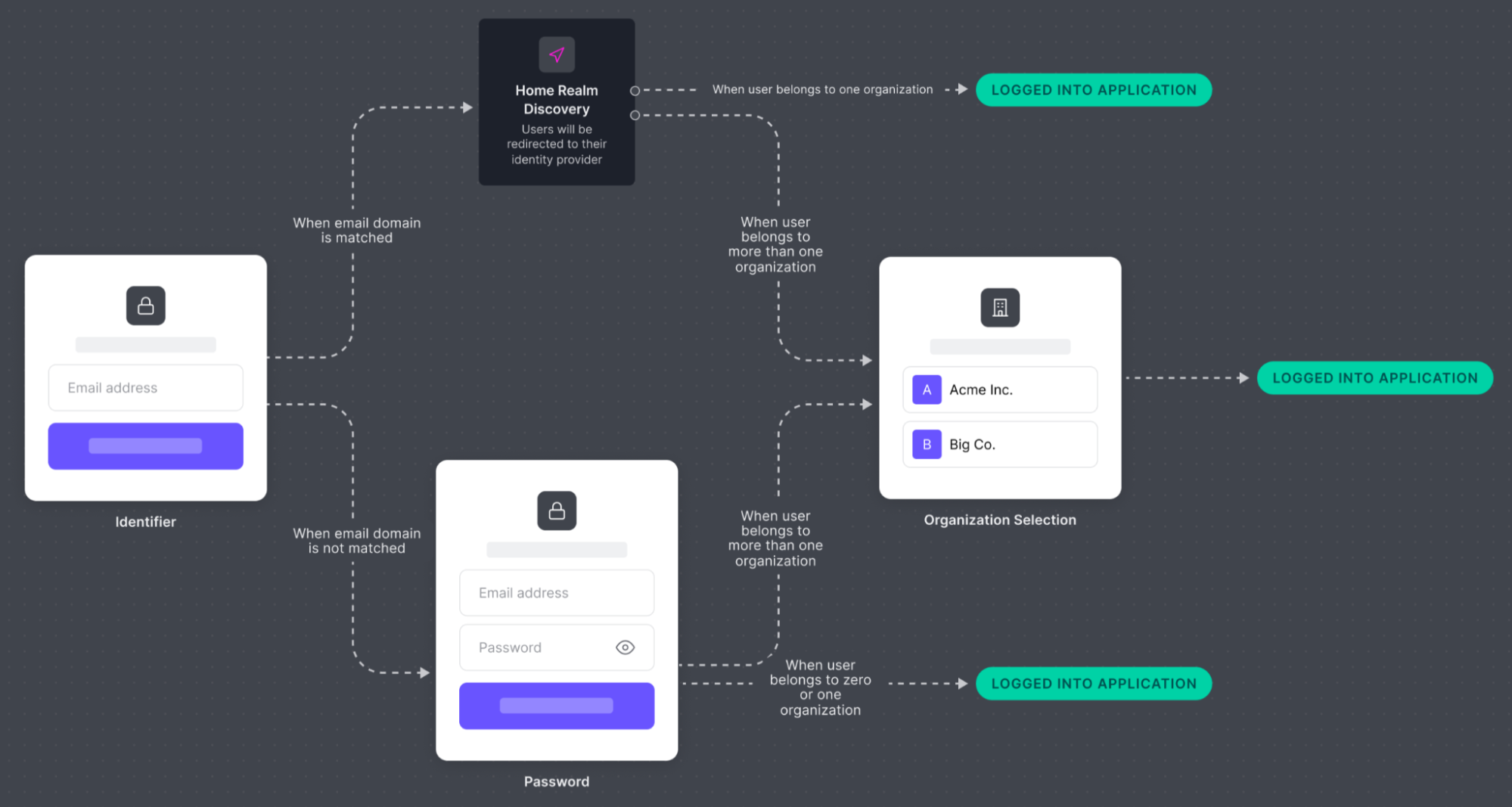
Identifier First Authentication with prompt for Organization
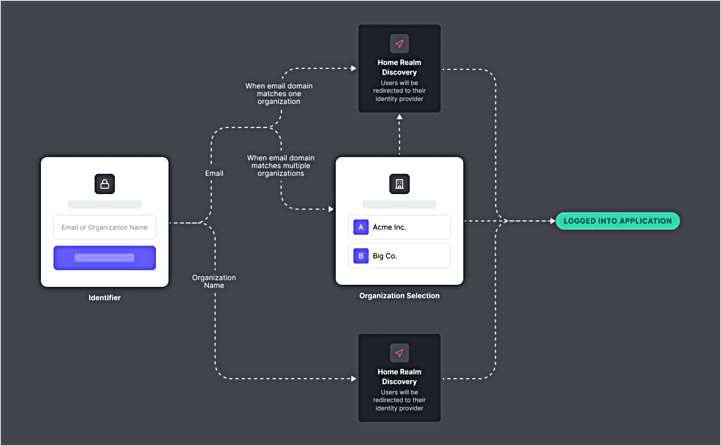
User input
The user begins by entering either:- Their email address (for example,
alice@rockymountainadventures.com) - Their organization name (for example,
Rocky Mountain High Adventures)
Organization Domain Discovery (optional)
If a tenant has configured verified Organization domains and noorganization parameter is provided, Auth0 attempts to determine the user’s organization automatically:
- If exactly one Organization matches, Auth0 automatically selects it and continues the Identifier First Authentication flow in that Organization’s context.
- If multiple Organizations share the same domain or name (for example, both AdventureZ and Granite Outpost each configured
travelco.com), Auth0 displays an Organization selector so the user can choose. Once chosen, Auth0 continues the Identifier First Authentication flow. - Only verified domains are used for discovery; pending domains are ignored.
- If no match is found, Auth0 proceeds with standard Identifier First Authentication.
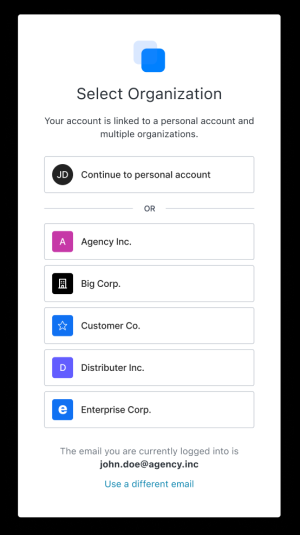
- Both: The prompt screen will include both the Organization Prompt and an option to Continue with Personal Account.
- Business Users: The option to continue with a personal account will not be displayed, and the user must log in with an Organization.
Identifier First Authentication
The goal of Identifier First Authentication is to determine which connection or Identity Provider (IdP) to route the user. Once the organization (if any) is determined, Auth0 applies Identifier First Authentication with Home Realm Discovery:- If a
connectionparameter is provided, Auth0 uses it to route the user to that specific connection. - Otherwise, Auth0 examines all Enterprise Connections enabled for both the application and the organization (if applicable).
There are use cases - such as multiple database configurations assigned to different Organizations - in which Auth0 cannot determine which IdP an user’s email is associated with. In these cases, select Prompt for Organization as your login initiation prompt or send the
organization parameter to Auth0.identifier_first parameter of the Update prompts settings endpoint.
Auto-Membership
Instead of inviting or assigning users to an Organization directly, you may want to allow any user that is able to authenticate with a federated IdP to be granted access to an Organization. For these scenarios, Auth0 recommends the Auto-Membership setting. Auto-membership is typically triggered by directing a user to log in using the Organization’s login prompt, which can pass the connection and organization parameters on the user’s behalf. If a user’s desired organization cannot be determined prior to login, the Prompt for Credentials flow grants membership to the sole organization with auto-membership configured. However, there may be scenarios in which you cannot determine a user’s desired organization prior to sending them to log in. In this case, you can use the aforementioned Prompt for Credentials flow but note that the user will only be granted membership in the organization if one and only one organization has this connection set as an enabled connection for the organization with auto-membership activated. You can use the Management API to configure auto-membership. Specifically, use theassign_membership_on_login parameter of the Modify an organization’s connection endpoint.
