Risks and considerations
IdP-Initiated flows carry a security risk and are therefore not recommended. The recommendation is to use SP-Initiated flows whenever possible. Make sure you understand the risks before enabling IdP-Initiated SSO. In this scenario, Auth0 receives the unsolicited response from the IdP and the application receives the unsolicited response from Auth0. Neither entity can verify that the user started the flow. Because of this, enabling this flow opens the possibility of an Login CSRF attack, where an attacker can trick a legitimate user into unknowingly logging into the application with the identity of the attacker.OpenID Connect IdP-initiated flow
Connect (OIDC) does not support the concept of an IdP-Initiated flow. So while Auth0 offers the possibility of translating a SAML IdP-Initiated flow (from a SAML connection) into an OIDC response for an application, any application that properly implements the OIDC/OAuth2 protocol will reject an unrequested response. When using OIDC applications, the best option is to have your application create a login endpoint. This endpoint’s sole purpose is to initiate the redirect back to the IdP (your Auth0 tenant). If you use multiple IdPs, be sure that the login endpoint is either specific to the identity provider or can accept a parameter to identify which IdP initiates the workflow. An alternative approach is to have users start the login flow at the application.Post-back URL
When using IdP-Initiated SSO, make sure to include the connection parameter in the post-back URL: If you are using the Organizations feature, you can optionally include an organization parameter containing the organization ID of the desired organization:In order for users to successfully log-in using this method, the connection must be enabled for the Organization. Additionally, you must either configure auto-membership for the enabled connection or ensure users have membership for the Organization.
Lock/Auth0.js
If your application is a single-page application that uses Lock or Auth0.js to process the authentication results, you must explicitly indicate that you want to allow IdP-Initiated flows and thus open the application to possible Login CSRF attacks. If you are using Auth0.js, you must update thewebAuth.parseHash of the library and set the flag __enableIdPInitiatedLogin to true.
const lock = new Auth0Lock(clientID, domain, options)
Here’s the flag itself:
var options = { _enableIdPInitiatedLogin: true };
Note that the enableIdPInitiatedLogin flag is preceded by one underscore when used with Lock and two underscores when used with the auth0.js library.
Set up IDP-initiated SSO
- Go to the Dashboard > Authentication > Enterprise and choose SAMLP Identity Provider.
-
Under Settings you can see the configuration for IdP-Initiated SSO.
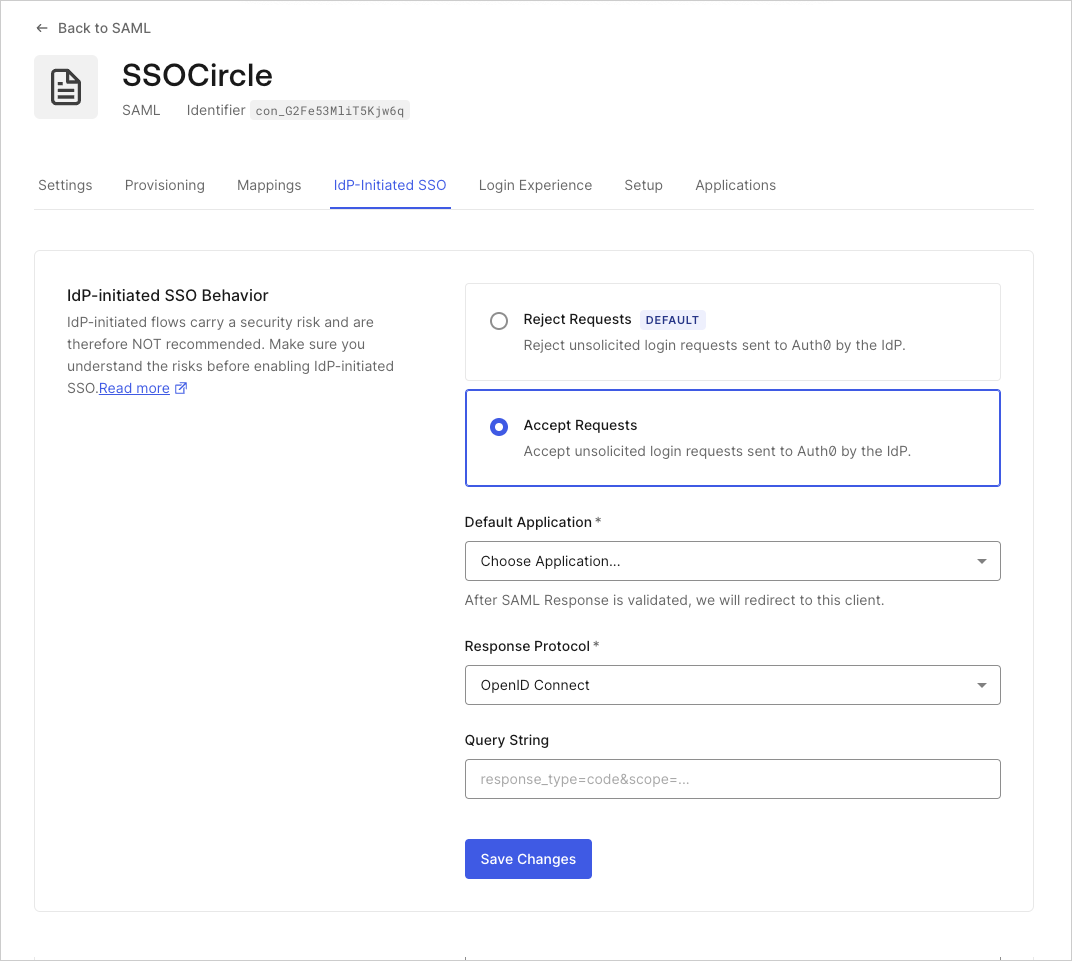
- IdP-initiated SSO Behavior: This option allows you to enable IdP-initiated logins for the SAML connection. Select Accept Requests and complete all the required fields.
- Default Application: When the IdP initiated login succeeds this is the application where users are routed. This setting shows available applications enabled for this connection. Select the application from the dropdown that you want the users to login with IdP initiated. Only one application can be selected for an IdP-initiated login per SAML connection.
- Response Protocol: This is the protocol used to connect your selected Default Application. Most commonly, applications are configured with the OpenID Connect protocol (see above). However, if you have configured a SAML2 Web App addon for your application and want to route the SAML assertion you will need to select SAML. Once a valid SAML Assertion has been passed to the postback URL, Auth0 sends a login response to the configured default application’s first allowed callback URL using the chosen response protocol, which can be modified using the query string field to specify a
redirect_uriif you use OIDC.- If the callback URL configured for the application includes a Multiple Custom Domains (MCD) placeholder, the system dynamically populates it using the metadata value that corresponds to the custom domain of the postback URL that received the inital request from the IdP. For more information, see Multiple Custom Domains.
- Query String: Query string options help to customize the behavior when the OpenID Connect protocol is used. You can set multiple options similar to setting parameters with a query string. You can set:
| Setting | Description |
|---|---|
redirect_uri | When the IdP-initiated login has completed the request is then redirected to the first URL listed in the Allowed Callback URLs for the application. However, if you set a redirect_uri, the IdP will redirect to this URL. This adds flexibility for cases such as when you have a set subdomain scheme with a wildcard and you only want to redirect to one specific subdomain. |
scope | Define scopes for the ID token sent. You can set multiple scopes. |
response_type | Set the token for the Implicit Grant Flow for SPAs. You can set code for the Authorization Code Grant Flow for regular web apps. |
redirect_uri=https://jwt.io&scope=openid email&response_type=token

