Multifactor Authentication (MFA)
Learn everything about Multifactor Authentication (MFA) and how you can start using it right now in your application.
What is Multifactor Authentication?
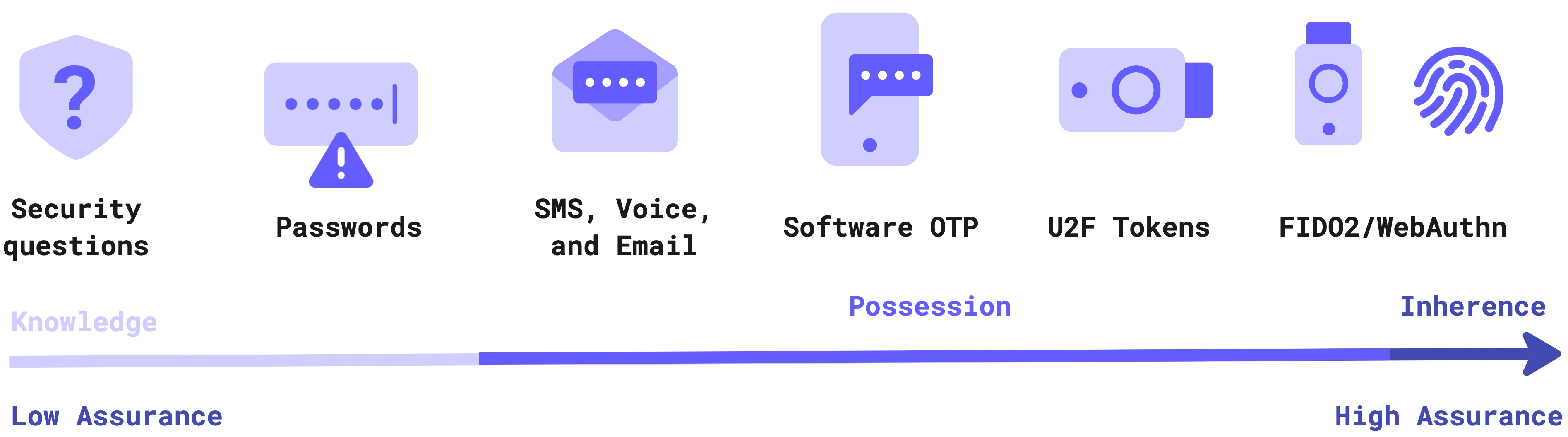
Multi-Factor Authentication (a.k.a. MFA) is the process whereby a user provides an additional level of authentication via the use of an additional factor. MFA is a complement to First-Factor authentication - which is typically where a user authenticates using a UserID and Password, or Passwordless workflow.
Why is MFA necessary?
Multifactor Authentication is important to provide enhanced security to your critical systems. The extra layer(s) of protection that MFA provides are typically triggered on abnormal or specific situations, such as login from a different device, location, or time frame. This can help prevent attackers - that only have one of your authentication factors - from gaining access to your account(s). For example, if your password is stolen, MFA will typically provide one or more additional layers of protection from attack by whoever stole your password!
Typical MFA Deployment
MFA (often referred to as step-up authentication) is typically deployed across all users. And typically employs an additional user authentication mechanism - also known as a factor - in an attempt to prove that a user is in fact who they say they are. The use of MFA can be an excellent deterrent against Phishing attacks and the like.
A More Adaptive Approach
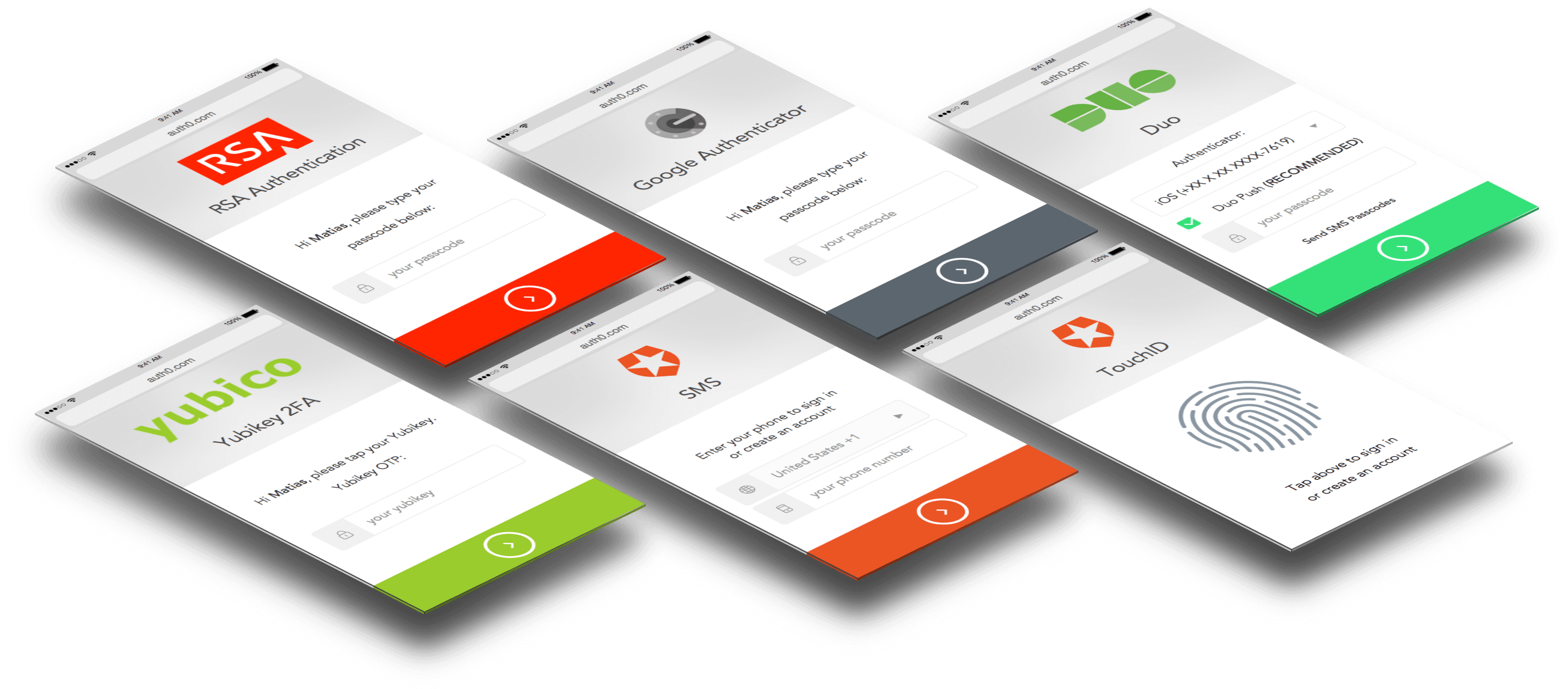
With Auth0 Adaptive MFA you can decide exactly when a user needs to provide their additional authentication factor. So users only need to go through additional security when an additional level of security is absolutely required. And you can progressively roll out MFA too; choose groups of users at a time rather than forcing everyone to use MFA all at once. Integrated via Universal Login, Adaptive MFA gives you the flexibility to make certain that the user experience is as frictionless as possible.
Compliance with Standards
We’re HIPAA and SOC2 compliant, which assures you that we comply with all best practices of identity management. Additionally, if you require an extra layer of security you can turn on advanced policies like multifactor authentication, password policies, brute force protection and much more with just one click!
Stay Informed
Discover helpful CIAM articles that are timely and relevant, whatever your level of experience. Whether you prefer to learn by reading, viewing, listening, cloning repos, copying code, or attending a workshop or conference, our content is everywhere and made for developers like you.
Sign up for free
Start building today and secure your apps with the Auth0 identity platform today.