Fast response allowed many organizations to survive and thrive in 2020. Orgs went remote overnight; businesses launched consumer-facing apps, and consumers shifted buying patterns online.
Going fast gets products to market, it gives consumers choices, and it helps companies scale. But when you jump ahead seven to 10 years in your digital road map, you risk leaving a few security and data privacy concerns behind. I reached out to key members of my security team, as well as our data privacy team, to put together this three-part series based on our industry experience and observations.
Each post will focus on protecting and securing two critical areas: your workforce and your consumer-facing apps. The first post will focus on security details to check and mitigate now. The second will focus on immediate data privacy concerns with the help of Auth0 Vice President, Privacy Lucy McGrath. And the third post will help you put together a plan for the future that will make it easier the next time you want to turn on the speed — and to remain current in an ever-changing security landscape.
The thing is that security is a global team sport. As more of us shift to working and living online, everything is more connected — and that can be a good thing. Securing your personal identity, your business identity, and helping increase security at your business can actually make an impact. Here’s what you can do to help make the internet safer for everyone.
Why Remote Work Forced a Change in Security Thinking
Before the world started working remotely, a lot of companies used a castle-and-moat approach to security. They relied on a combination of physical security and internal networks to ensure that employees and outsiders only accessed necessary information. They might even have relied on SaaS companies to provide some of their protections, but the thinking was still pretty much “protect the castle.”
Suddenly workers were working anywhere in the world, maybe on their own devices. Without remote experience, your security team might not have had time to think through all of the security issues inherent with having remote endpoints. For example, to ensure that they properly protect these assets against current threats like ransomware and malware, it would be appropriate to install leading next-gen antivirus on these machines.
Role-based privileges and policies also abruptly needed to follow the user. I know I work for an identity company, but it was identity and policy federation that anticipated this need and allowed for a rapid response.
Now some companies are making work from home a permanent part of their employee offering. Since Auth0 was built as a remote-friendly, globally dispersed company, we’ve had some time to think through the security concerns. Here’s what you need to consider to protect your customers, your business, and your employees:
- Secure the endpoints. Services like CarbonBlack or CrowdStrike can help prevent malware or breaches occurring from endpoints.
- Update bring your own device policies. Rethink how and where employees are accessing business and customer data. Do you need to restrict access in public spaces? Adjust policies?
- Update action policies. What do your employees do if a work computer is stolen? What steps do they need to take if the information is exposed at home? A 1Password survey found that 51% of work from home (WFH) parents surveyed said their children had accessed their work accounts, sometimes accidentally deleting necessary files. How can you support your employees??
- Human risk is increased. Have a look at the next section.
The Human Element
This is the critical part of this series — the human element is the most important aspect of security and data privacy.
Security awareness training needs to happen at every single level of your organization.
A malicious actor is going to use everything you need to do business — email address patterns, information on your website, social media posts, and items gleaned from news articles all to try to gain entry to your system. While the attacks will vary, they usually follow this pattern: human factor + inject something into the code + lack of input validation + insufficient logging and monitoring.
If something looks like it’s coming from your CEO or payroll, an employee might fall for it and supply a way into your system. And once a bad actor is in, there’s lots they can do.
But if you train your entire team to watch out for phishing attacks, you can stop them at the first step. This post is a good place to start.
Attacks evolve, so even though security awareness is something you should pause and do now, it’s something you’re going to need to do regularly. Developing a security culture throughout your org provides great protection. To do business with some industries like finance or healthcare, the training will be required to cover specific areas and will need to be documented. The training you provide can also help protect your employees in their personal lives.
Top 7 Things to Do Now to Check Your App’s Security
This can seem like a lot if you don’t have an in-house security team (and maybe if you do). One principle of security is encouraging diversity of thought not only because it’s the right thing to do but because studies show it makes teams more productive. In security, diversity of thought makes it easier to spot potential threats. This is part of why even large teams rely on external testing vendors and may even need to provide proof of outside testing for certifications like CSA Star and PCI.
- Get an external third-party pen test — and implement the recommendations. A penetration test is where you hire a verified third party to attempt to find your app’s vulnerabilities. They will sign a non-disclosure agreement (NDA) and provide a detailed report outlining their findings and usually with recommended fixes cataloged by severity. Discovering vulnerabilities can be scary, and there is the temptation to use fear to drive organizational change, but we’ve found that partnering and collaborating with other teams and leadership can often get changes implemented faster.
- Review best practices for your cloud-based services. When people go really fast, they may not take the time to fully understand the technology and security controls. This is a great time to go back and pay really close attention to the docs provided by your third-party vendors.
“Many common AWS security issues, for example, happen as a result of not following AWS security best practice guidelines when setting up the infrastructure. This can lead to open and accessible EC2 security groups, public S3 buckets, unprotected EMR clusters, and more,” says Auth0 Detection and Response Security Engineer Troy Wegner (formerly of AWS and Amazon.com).
- Perform static and dynamic code analysis. Static analysis reviews the code as it exists. Dynamic analysis looks for vulnerabilities while the code is being executed and for unexpected outcomes. Ideally, you want to move towards baking both into your Software Development Lifecycle (SDLC). Devs may not always enjoy adding this to part of their process—more on how to add this analysis to your long-term software development plans in the final post.
- Think through vulnerability management and updates. Since humans are fallible and it’s humans who make code, it’s inevitable that you’re going to run into vulnerabilities. If you don’t have a plan for pushing updates, now’s the time to make one so you don’t hear about something BIG like the Heartbleed Bug and find yourself painfully updating ad-hoc.
In general, you’re going to need to test every time your devs update something and whenever your tech stack libraries or any of the main operating systems updates. Services like Chef, Puppet and Terraform can make this easier by pushing updates from a central server to connected servers. In the final post, we’ll get into longer-term strategies for updates, like maintaining a Golden Amazon Machine Image (AMI) if you’re on AWS. For now, just document how and when you’re going to update and test.
- Threat model. A lot of security is determining risks. Ideally, you’ve threat modeled before building your app, but in some ways, it’s easier to model after it’s live. Yes, you can hire a trusted third party to do this for you. To give you a sense of the thought process, I asked Troy to threat model this restaurant scenario. Security engineers often diagram vulnerabilities, so we also include Troy’s whiteboard as a reference.
Let’s say you’re a local restaurant who responded to COVID by offering the ingredients to make your tastiest dishes and recipes to your customers via curbside pickup. You hired someone to put the app together quickly, but now your region is opening up, and you’ve decided this channel of operations should continue contributing to your bottom line.
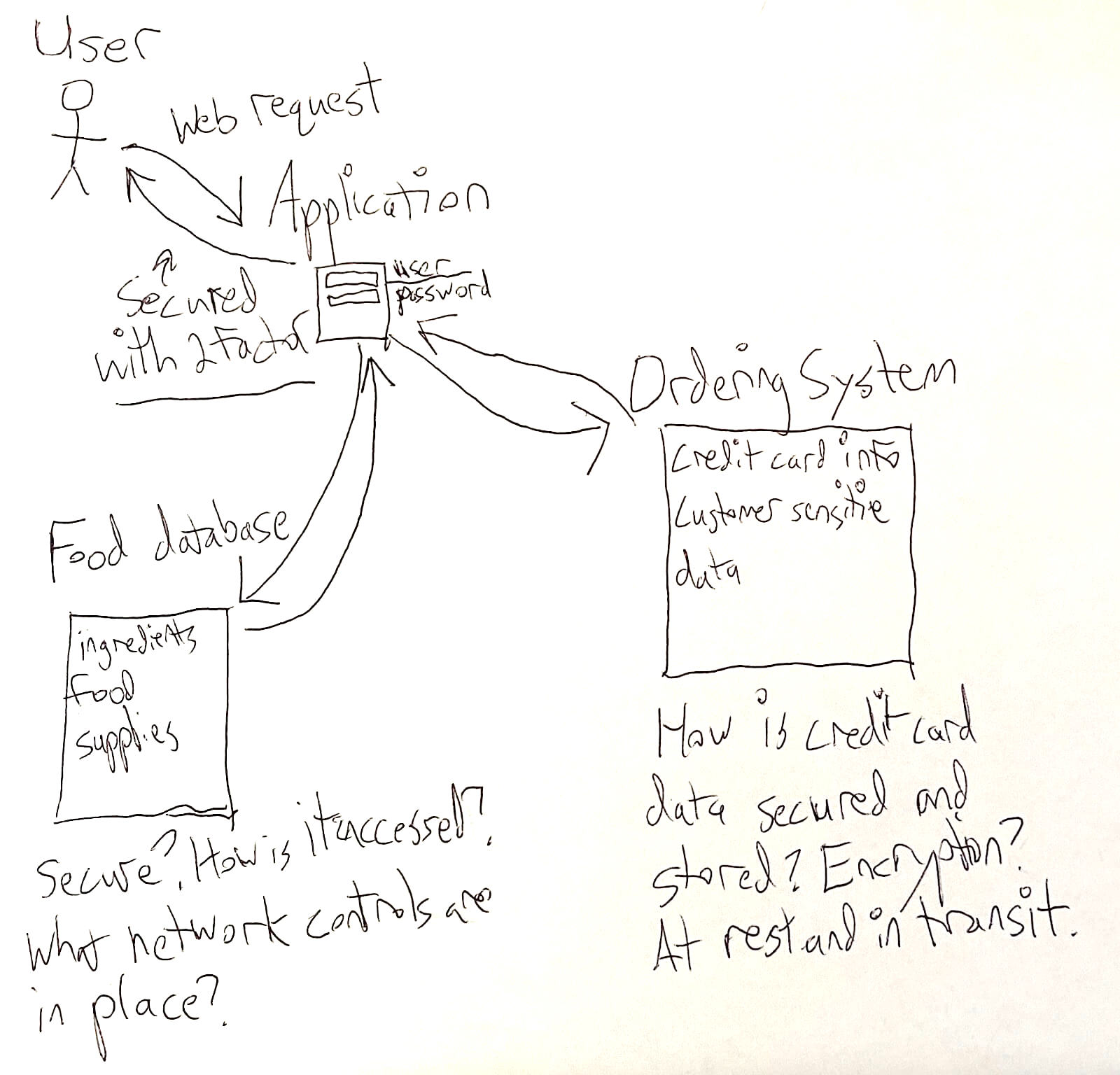 Figure 1: Auth0 Senior Security Engineer - Detection and Response Troy Wegner’s whiteboard of our restaurant scenario.
Figure 1: Auth0 Senior Security Engineer - Detection and Response Troy Wegner’s whiteboard of our restaurant scenario.
- Start with authentication because you know customers need to authenticate in order to interact with your app. How are they authenticating? Are they only using a username and password? If they are only using a username and password for authentication, then you have just hit on your first major risk (user compromise/phishing/user impersonation).
- As a way to address the first risk identified, you have chosen to go with two-factor authentication for your users. But here is where things get interesting; which 2-factor options do you want to support? There are authenticator apps, FIDO U2F, Push-based 2FA, and SMS (the weakest available option). Each option has its own pros and cons to consider.
- Since this is a restaurant, you’re also somehow connecting the app to the food supply. How are you measuring and validating your existing ingredients inventory to ensure you do not oversell based on your total ingredients available? Are you using a database to store this information? If so, where does this database live, is it protected or hardened information security wise, and if so, how is it hardened? How do you authenticate to the database, is it updated regularly, do you perform backups, etc.
- If your service has gotten really popular, too many people might try to order at once, and that could overwhelm the app’s limits. The app could go down due to resource constraints based on how it is architected. This is basically the risk a DOS/DDOS would present in bringing your app down and making it no longer available to your customers. In order to mitigate a DDOS risk, you might have a plan to make your app more fault tolerant and highly available by using load balancing, increasing back-end servers to handle the load, or using a front-end CDN to help distribute load across various edge locations.
- Most likely, your app is taking payment and processing it in order to fulfill orders; how are customer payment and other sensitive information being handled/stored? If you accept credit cards or debit cards, PCI compliance is a concern you should address.
- Here is where you would now want to think through and fully diagram out the rest of how the app works and uncover any other risks or bottlenecks that currently exist with your app, place a severity on those risks, and determine by severity which risks you want to fix, and which ones you are ok accepting.
- Turn on your logs — and make sure they’re monitored. Turning on logs can seem like common sense, but because there’s often an expense attached to logging and getting the data analyzed, the logs might not always be turned on. It’s really hard to know what to fix after a malware outbreak or other issues occur, especially if your logs aren’t turned on and are being actively analyzed.
So this is where we tell you to turn on the logs for all the services you’re using. You should also make sure that a trusted third-party vendor or trained security engineer is watching your logs and building actionable detections based on those log sources to look for suspicious or anomalous activity.
- Take action. Logs, vulnerability assessments, pen tests — these things can help you identify what needs to be fixed, but you still need to fix it. Breaches and ransomware are the obvious security problems you want to avoid. How your security challenges impact consumer behavior might not be as clear. Lost conversions, abandoned shopping carts, and low time on site are all indications that your target audience may not feel comfortable sharing their data with you. Our customers tell us that an app or site that feels secure (think smooth login, logical and smooth payment process) supports their business goals.
If You Need More Help
Authentication is often a critical part of securing an app or workplace. If you’d like to understand how Auth0’s solutions might help make your app more secure, please reach out to the team at Auth0.
My next post will focus on immediate data privacy concerns with the help of Auth0 Vice President of Privacy Lucy McGrath.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Jameeka Aaron
CISO
Jameeka has over 20 years of Information Technology and Cyber Security experience. She is a versatile leader, successfully leading teams as both a CISO and CIO across various industries including; Aerospace & Defense, Apparel, Retail, and Manufacturing at both Fortune 100 and privately held companies and many spaces in between.
She is highly skilled in Business Engagement (International and U.S. based) Audit, Compliance, Vulnerability, Risk and Identity Management, Digital Transformation, Mergers, Acquisitions, Divestitures, and leading Cross-Functional and Matrixed teams.
