Auth0 supports many common identity scenarios. One of them is a SaaS app being used by companies with their own identity systems. This is the classic federation scenario.
To illustrate this, lets start by introducing the characters:
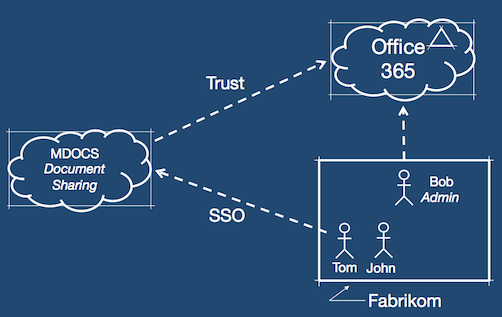
- Fabrikom is a small business, using Office365
- MDOCS is a document sharing app hosted in the cloud
There are four challenges here for MDOCS:
How to simplify the on-boarding of new customers. This involves automating the trust relationship between the app and their customers' identity systems (Office365 in this example)
How to do Single-Sign-On so customers can use their Office365 credentials, but mdocs being a multi-tenant app, how to easily accept other platforms like Google Apps or Active Directory.
How to query the user directory when there is one, so mdocs can implement a "people picker" that is relevant to the organization using the app.
How to keep track of who uses what, for access audit.
1. Self-Service on-boarding:
In this first video, you will see Bob (admin @ Fabrikom), connecting MDOCS to their instance of Office 365:
2. Single-Sign-On, Directory Query:
In this second video, you will see Tom (an employee @ Fabrikom) that logs into MDOCS using his Office 365 credentials. He accomplishes this through the Auth0 Login Widget.
Then he creates a document and shares it with a colleage John. The "people picker" UI is using Auth0 API to query users in Fabrikom's user directory (Office 365 in this case).
3 Dashboard:
In this last video, you will see an MDOCS administrator using Auth0 dashboard. He explores all connections (social and enterprise). Notice the Fabrikom connection created automatically in the on-boarding phase. He then browses the Auth0 API Explorer and uses it to retrieve all Fabrikom users (returned as a JSON array). This API call is in essence the same used in MDOCS on the "people picker". The Auth0 API Explorer allows you to explore the API capabilities without the need to write any code.
About the author
Eugenio Pace
CEO and Co-Founder