Between social distancing, an uncertain economic outlook, and the Coronavirus itself, business leaders have enough on their plates without having to worry about cyberattacks. Unfortunately, cybercriminals aren’t taking a vacation; they’re using the Coronavirus pandemic as an opportunity to prey upon organizations around the globe, with potentially disastrous results.
Around the world, security experts are reporting an alarming uptick in Coronavirus-related scams and attacks on our most vital infrastructure.
It’s easy to feel powerless in the face of this epidemic, but when it comes to cybersecurity, executives can actually do a great deal to limit the damage. Put measures in place now to protect your business’ data from attack, and you’ll come out the other side of the pandemic better equipped to deal with cybersecurity threats. Let’s start by identifying those threats.
Cyberattacks Surge During Coronavirus
It was tempting to hope that hackers might give the world a break during a global health crisis. In fact, security company Check Point has reported a sixfold increase in the average daily number of attacks in recent weeks. Of Coronavirus-related attacks, they report that 94% are phishing scams. This statistic is echoed by Google, which said it rejected close to 18 million virus-related phishing emails per day in one week in April.
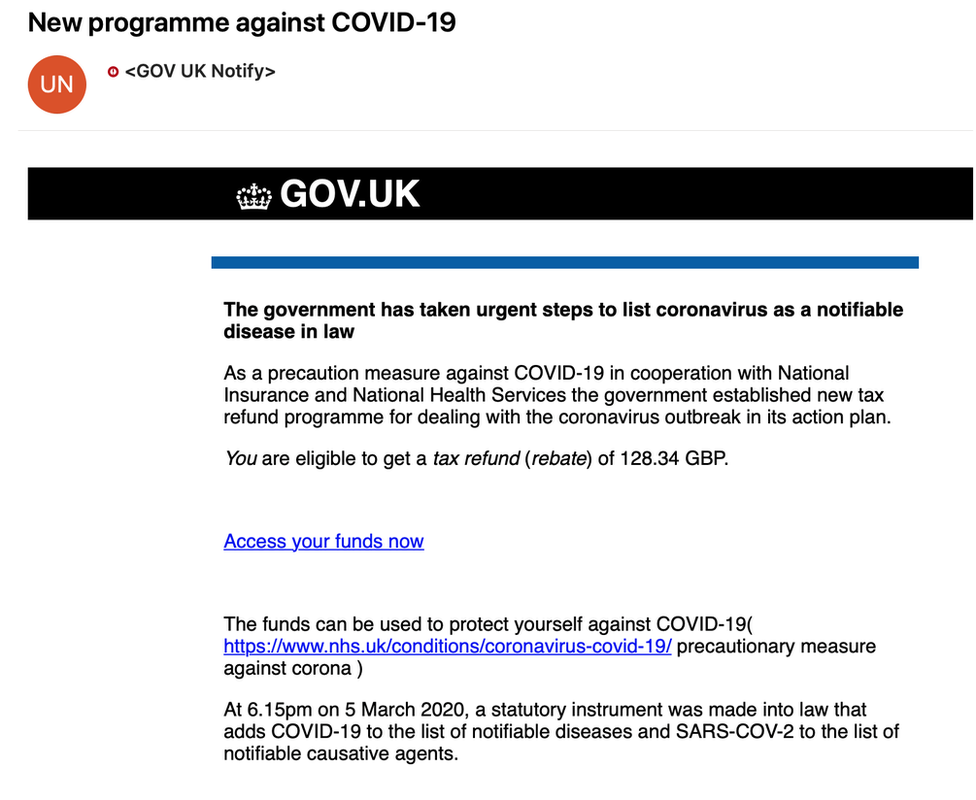
These phishing scams can take a myriad of forms, but criminals posing as government agencies are particularly common. They may offer false guidance, claim to have a list of new Coronavirus cases, or offer people help getting their stimulus checks or other financial assistance. Regardless of the ploy, the goals are the same: trick the reader into clicking on a link, downloading an attachment that exposes them to malware, or entering in private information, which hackers can then use to hijack their identity.
Many phishing attacks also pose as internal business emails, taking advantage of the confusion resulting from people working from home. Even individuals who would normally be more cautious about clicking on a suspicious link may have their judgment compromised due to pandemic-related stress. People hoping for miracle cures or financial relief are far more likely to click on suspicious links than they would be otherwise.
Tragically, one of the hardest-hit sectors during the Coronavirus has been healthcare, which has been victim to a spate of ransomware attacks. As Michael Salát of Avast has written, “hospitals are not necessarily more susceptible to ransomware attacks,” but since any system downtime could literally cost lives, “they are more likely than other organizations to pay the ransom.” Both the Department of Homeland Security and INTERPOL have issued warnings about cyberattacks in healthcare and urged hospitals to educate their employees on email safety, external backups for critical data, and strong, unique passwords.
{% include tweetquote.html quotetext="As @avast’s threat intelligence director @michal_salat has noted, “hospitals are not necessarily more susceptible to ransomware attacks” — but attacks can cost lives — and they’ve tragically seen an increase during COVID. " %}
The importance of these steps was highlighted by the experience of an Illinois hospital, which had to pay hackers $300,000 in ransom to get back access to their system after being locked out for three days. As a hospital administrator said, “The only good thing was that just a few months before, we had put our electronic medical records and our email on the cloud, so they were not affected.”
How to Protect Against Coronavirus-Era Cyberattacks Today
The Coronavirus pandemic is an ideal situation for hackers since they thrive on confusion, ignorance, and misinformation. To thwart them, businesses need to counter with communication, education, and knowledge.
Step one is to counter misinformation and confusion by educating your employees on cybersecurity best practices.
These include:
- Use a unique password for every application to guard against phishing and credential stuffing attacks. Ideally, all your employees should be using a company-approved password manager to ensure they aren’t re-using passwords.
- Be on guard against common phishing techniques, such as emails purporting to be from company representatives but with an unfamiliar or misspelled email address.
- Regularly update all software, especially anti-virus software, on any device (including mobile devices) on which you conduct company business.
It’s up to you how you educate your employees, but given how vital this information is and how overwhelmed your team is likely to be, you should consider something more in-depth than a simple email. Conducting video training with specific examples of phishing attempts will make a bigger impact and let you respond to any questions your team has.
If possible, you should mandate that all work is done on company-issued devices since employees are less likely to be as vigilant about security updates and downloads on their personal devices. If that’s not an option, you should still ensure that any remote tools you’re using are secure and you’re not compromising data security in the name of convenience. (That’s particularly true for the healthcare sector, in which telemedicine is opening up exciting possibilities but also sparking concerns over patient privacy.)
As always, one of the best defenses against unauthorized intrusions into your system is to implement a sophisticated Identity and Access Management (IAM solution) using multi-factor authentication (MFA). MFA works by requesting an additional form of credentials beyond a username/password combination, such as a one-time code or biometric. That way, even if an employee unwittingly shares their password in a phishing scam or is the victim of a credential stuffing attack, a hacker can’t use that information to waltz into your system.
Auth0 Signals is a new service designed to help facilitate this by offering a real-time assessment of a login attempt’s threat level and when to request additional credentials.
</div>
Build Digital Resiliency to Guard Against Tomorrow’s Attacks
In choosing how to protect your company’s data, it’s important to think beyond short-term survival strategies and find solutions that are designed to last for more than a few months. After all, many experts predict a second wave of the pandemic that could mean a return to social distancing and remote work. And Coronavirus aside, cybersecurity threats to business are on the rise, so it’s important to be proactive rather than merely reactive.
Conduct risk assessments of your company’s technology, especially every tool your employees may need to work from home. Norton advises remote teams to “control the urge to improvise” by switching to unsecure applications when their work-approved tools fail. Yet the best way companies can protect against so-called Shadow IT is to make sure that every piece of software that your team will need to remotely collaborate works as it should.
{% include tweetquote.html quotetext="Build digital resiliency — it’s important to think beyond short-term survival strategies for protecting your company’s data and find solutions that are designed to last for more than a few months. " %}
As Auth0’s CSO Joan Pepin has written, you should also draw up a pandemic plan to prepare for future crises. That way, in the event of an emergency, all parties know their roles, and your business won’t descend into the kind of confusion that makes it easy prey for hackers. Making this plan will also deliver immediate benefits since you’ll spot potential weak points in your company’s documentation, technology, and overall structure.
Be Careful, Not Fearful
In times of crisis, when resources (and patience) are stretched thin, it can be challenging to think about long-term solutions. But the Coronavirus is highlighting why it’s so vital to have a culture of security in place to keep a crisis from becoming a catastrophe. That culture should include regular audits, employee training, and third-party partners you trust to keep your systems updated. It’s the difference between building a lean-to shelter to get through a storm and building a sturdy house that will keep out all the storms to come.
If you’d like to learn more about how a sophisticated IAM platform can protect against cyberattacks without slowing your business down, please reach out to the team at Auth0.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Duncan Godfrey
Sr. Director of Security and Compliance (Auth0 Alumni)