"In today's online-first, intensely competitive environment, creating a monolithic, inflexible CIAM system will quickly put the firm on the path toward extinction." - Forrester's Customer-Obsessed IAM Operating Model April 2020
There is an "old-school" view of Identity and Access Management (IAM) that sees it purely as a security requirement for apps and websites. Simply put, IAM is there to keep the bad guys out and let the good ones in.
A more progressive view recognizes how IAM can help provide a better level of user convenience and app-level personalization, as well as lower-friction interactions. Plus, it can offer the business better CRM data, a lever for managing data privacy and compliance controls, and (if implemented properly) a consistent security perimeter across all apps/properties.
But there's a third level of benefit of IAM that IT often overlooks: A consistent, flexible IAM foundation can contribute to the firm's overall digital agility.
Here's why: IAM systems have traditionally been embedded into apps and frameworks (think: React, Angular, JS, etc.). Using that approach, each app runs the risk of becoming an IAM silo unto itself. And when it comes time to integrate those apps with other identity-driven systems, the approach can create a massively inflexible infrastructure.
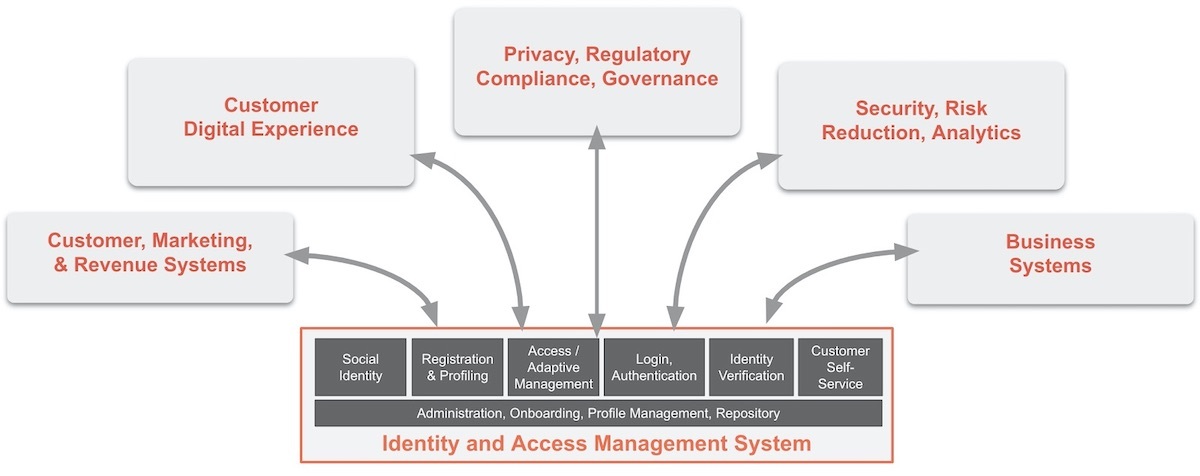
Worse, firms should expect that many of their custom apps will have to work alongside other enterprise apps — e.g., marketing, digital experience, privacy/governance, business systems, and of course, security and analytics. However, the reality is that the logical topology surrounding your IAM system will always be dynamic and distributed — plan for it. The nature of enterprise systems IAM needs to interface with will always change. But when business leaders don't plan a consistent IAM foundation, digital agility is one of the big losers.
Identity Has Become a Foundational Component of Digital Transformation, IT Agility, and Infrastructure Modernization
Digital transformation initiatives are when progressive software-driven companies shift from rigid, monolithic IT infrastructures and apps into more componentized API-first architectures. These are more easily reassembled/rearchitected and reused (see this great blog about API strategies by Informatica). Component software also means that app updating can be done on a piece-part basis, without requiring the entire application to be retested and QA'd.
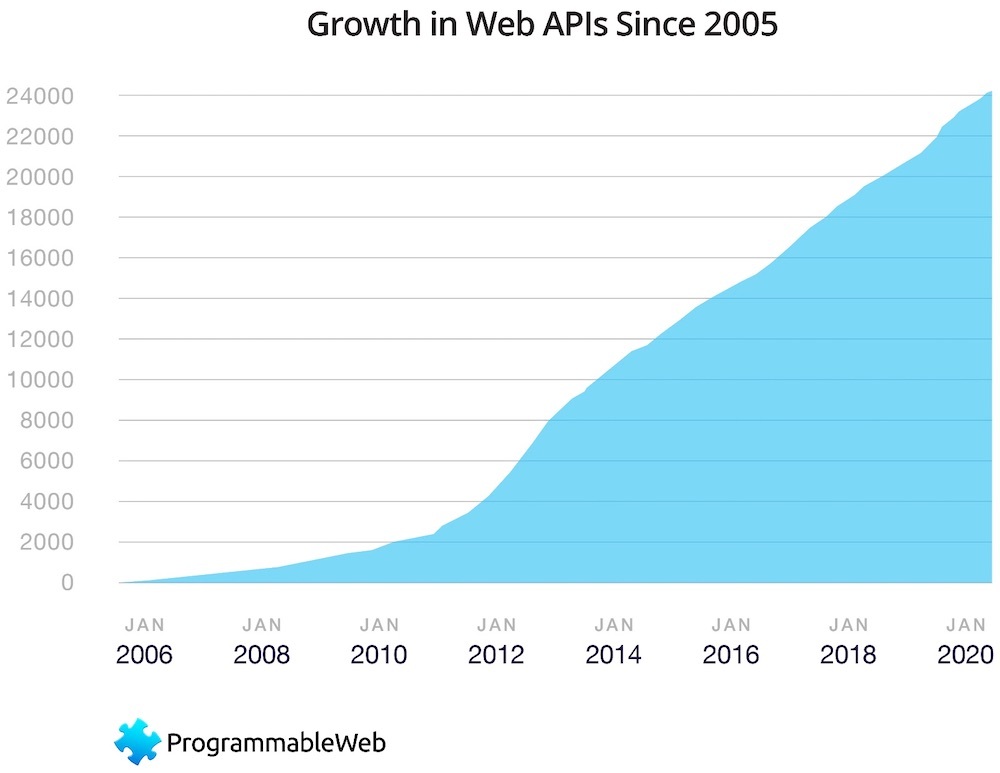
When shifting to an API-based strategy, there is often a simultaneous replatforming initiative for some (or all) of the components, shifting them into the cloud and/or onto serverless cloud platforms. These initiatives also help businesses respond more rapidly to fast-moving opportunities and/or competitive issues. The growth of API-first architectures and use of serverless execution platforms has been nearly geometric during the past few years.
Distributed and loosely coupled
In software design, a loosely coupled system is one where each component has, or makes use of, little or no knowledge of the other components. This could include the coupling of software classes, interfaces, data, and other SaaS services. Loose coupling is important because it allows you to rearchitect specific components in the future with minimal impact to other components.
Often, one of the loosely-coupled underpinning layers of these digital transformation initiatives is security and access management — certainly found at the application level, but also even at the component level. With potentially millions of such API-first distributed components being deployed, each component, app, and composite application must be reliably and consistently secured, embracing the capacity to be identity-aware.
Decoupling identity from the application and/or app component means avoiding inconsistent IAM stores/DBs, yet ensuring a consistent privacy model, reliable access, and a strong security perimeter.
The auth0 Point of View: Your Identity Management Functions Must Be Componentized, Programmable, and Cloud-Neutral
Many of today's IAM technologies are embedded in programming frameworks and therefore hardwired to apps. We believe these IAM functions must — and will — become decoupled from the apps they support. Decoupling IAM helps release customers from the bonds of vertical integration stacks that are inherently siloed, brittle, and fundamentally non-optimized for the complexity of today's identity needs.
IAM functions should also be released from mega-cloud lock-in. The market requires an IAM foundation that's open and customizable — rather than a foundation that binds customers to an Amazon, Azure, or Google agenda.
This matters because an IAM approach that's API-first, application-decoupled, and componentized also allows developers and their enterprises to rearchitect and dynamically deploy new updates, features, and functionality without disrupting the underlying identity infrastructure. That results in the ability to respond to business conditions and competitive situations more quickly and reliably.
Some closing recommendations
For executives, technology agility equates to business agility. Work with your technical colleagues to understand what IAM underpinnings you currently have and how those will need to evolve to work alongside adjacent systems for marketing, digital experience, privacy/governance, business systems, and security and analytics. Urge technical partners to: *Seek to componentize applications underpinned by a consistent IAM infrastructure. Treat IAM as a reusable component service the way you use other reusable SaaS services (e.g., payments, databases).
Measure and justify the benefits of IAM across your infrastructure. Collaborate with colleagues in security, customer experience, web, and CRM teams; assess where identity can yield quantifiable top-line revenue and competitiveness.
Prioritize customer outcomes within digital transformation initiatives. Digital agility and transformation program outcomes must be driven by a focus on responsiveness to customer needs and expectations. Identity management foundations not only contribute to a consistent/reusable infrastructure but also help build a comprehensive customer 360°.
Neutralize cloud vendor lock-in risk with an independent, cloud-neutral IAM system. Long-term agility and avoidance of high switching costs are further enabled by using an independent, cloud-neutral IAM service.
For technologists, it's time to apply IAM like other loosely-coupled SaaS services you commonly use. For example: *Use familiar API and microservices principles when adding IAM into your platform. Select a reusable, easily-integrated cloud IAM service that's compatible with a broad set of programming languages and frameworks.
Reduce IAM time to production; simplify app reuse. Get your team started quickly with a solution offering SDKs, quickstarts, and implementation guidance.
Consolidate user IAM systems and databases. Use an IAM solution offering a range of migration tools and customer DB connections to fit the user migration scenario best for you.
To learn more about how IAM contributes to overall digital agility, explore our identity resources, or reach out to sales.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Ken Oestrich
VP Product Marketing, Messaging, Content, DevRel. (Auth0 Alumni)