Developers are increasingly relying on powerful AI command-line interface (CLI) tools to write code, debug issues, and automate tasks. These AI assistants have become trusted partners in our daily workflows. But what happens when that trust is exploited?
An AI-powered, CLI-targeted supply chain attack is a cyberattack that leverages AI to compromise a system through its software dependencies and tools. This has opened the door to a new kind of attack that turns these helpful tools into insider threats, capable of stealing your most sensitive data from right inside your terminal.
This isn't a theoretical risk, it's an emerging threat.
An attack on "Vertigo"
Jane is a developer for a well-known tech company and a dedicated maintainer of Vertigo, a popular open-source utility that's been downloaded over a million times. Unknown to her, a small bug in her project's continuous integration/continuous delivery (CI/CD) pipeline accidentally exposed her package registry publishing token to a malicious actor.
Here’s how the attack could unfold:
Step 1: Compromise publisher credentials
An attacker, having stolen Jane’s publishing token, now has the ability to publish new versions of Vertigo. They publish a new version, 2.7.1, that seems to have a bug fix, but secretly contains a malicious post-install script.
Step 2: The post-install surprise
When Jane's colleagues and other developers update their local version of Vertigo to 2.7.1, the malicious script automatically executes on their machines. The script immediately begins to raid their systems, seeking out valuable secrets. It quickly finds a treasure trove of sensitive files, including an unencrypted SSH key, a GitHub Personal Access Token (PAT), and several private .npmrc files containing other developers' package registry tokens.
Step 3: Weaponize AI assistants
The script doesn't stop there. It then searches for and finds a popular AI coding assistant on the developer's machine. It then uses flags like --dangerously-skip-permissions to bypass the assistant's built-in security features. The script instructs the AI assistant to perform a system-wide scan for all files matching "private key," ".wallet," and ".env." It uses the AI's advanced file-searching capabilities to efficiently identify and log the absolute paths of all sensitive data. The AI assistant, now an unknowing accomplice, helps the malware locate all the secrets on the machine.
Step 4: The exfiltration: A public betrayal
With a list of all the sensitive files, the script uses the stolen GitHub PAT to create a new public repository under the developer's identity. It then base64-encodes all the harvested data and uploads it to the newly created public repository, which makes stolen secrets easily accessible to the attacker.
Step 5: Mislead and disrupt
As a final act of sabotage and to cover its tracks, the script appends a sudo shutdown -h 0 command to the developer's .bashrc and .zshrc files, causing their machine to shut down immediately after they open a new terminal. This creates confusion and disrupts their work.
An identity-first defense strategy
This threat scenario highlights that modern software security is tightly linked to identity and access management. Preventing and mitigating these attacks requires a defense-in-depth strategy centered on securing developer identities and their credentials.
Following three core concepts, here's how Jane and her company can defend against this AI-powered attack:
Concept 1: Secure package publishing with OpenID Connect (OIDC) Trusted Publishing
The attack on Vertigo began when Jane's long-lived package registry publishing token was compromised. To prevent this, her company should have used a package registry supporting Trusted Publishing with OIDC. This modern approach eliminates the need for static, long-lived secrets.
Instead of storing a static secret like a NPM_TOKEN in their CI/CD pipeline, the company can configure their package registry to trust their CI/CD provider, such as GitHub Actions, via OIDC. OIDC allows the CI/CD system to exchange its identity for a short-lived, cryptographically secure token.
For example, with npm Trusted Publishing, when a new version of Vertigo is published, a unique token is automatically generated for that specific workflow run. This token is temporary and can't be reused, expiring almost instantly. Even if an attacker were to compromise the CI/CD job, there would be no persistent secret to steal. This eliminates the persistent target that was the initial entry point for the attack, making the software supply chain more secure.
Concept 2: Enforce the principle of least privilege
The attacker was able to exfiltrate all the data and upload it to a public repository because they stole a GitHub Personal Access Token (PAT) with broad permissions. Jane's company must enforce the principle of least privilege for all credentials.
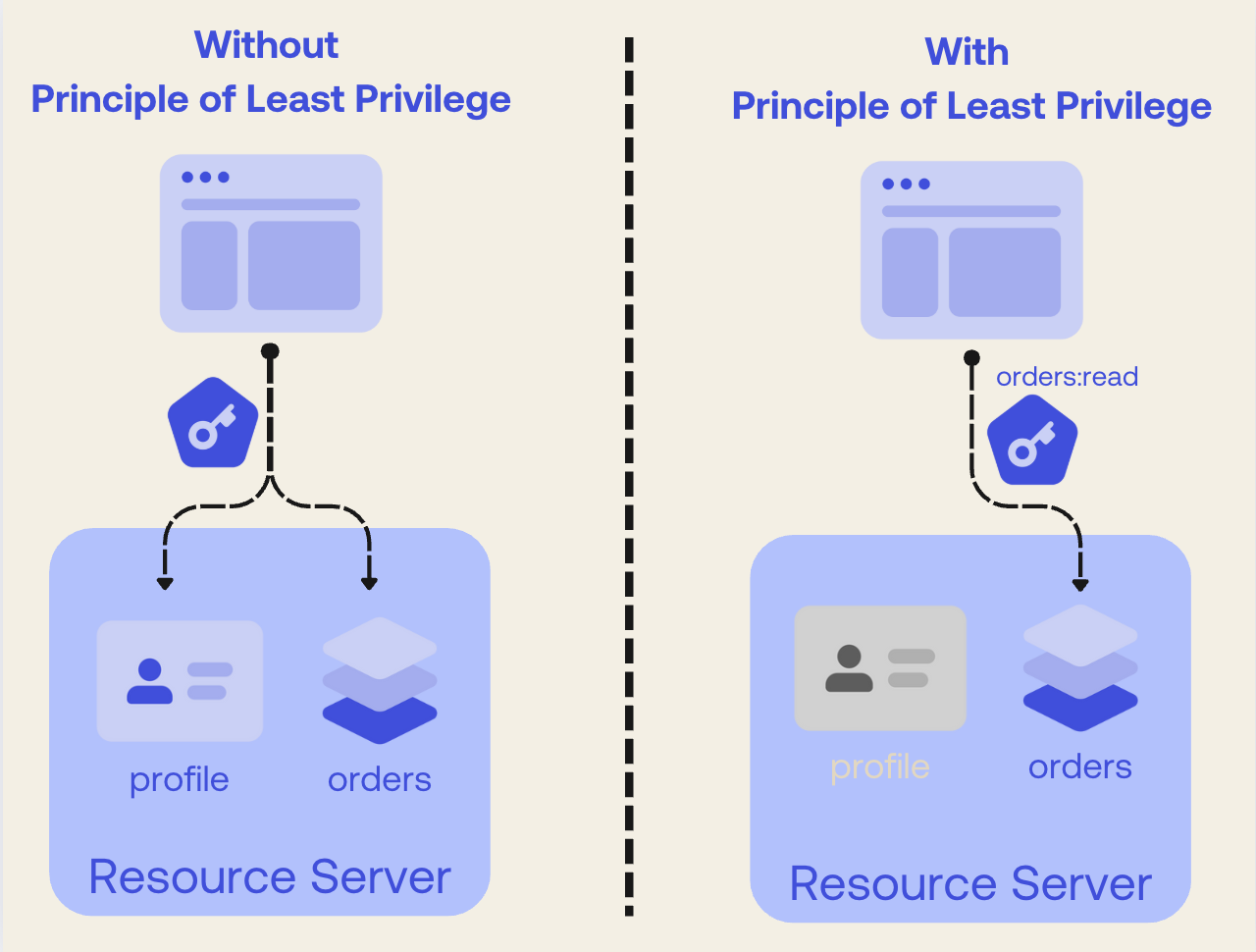
Second, they should set a mandatory expiration date on all tokens. Had the stolen PAT expired after a few days, the attacker would have had a much smaller window to use it, limiting the scope of the damage.
Concept 3: Mandate multi-factor authentication (MFA)
The first step in any of these supply chain attacks is often gaining access to a maintainer's account. A common method is through compromised credentials from a phishing attack or password spraying. To combat this, Jane's company should require MFA for every developer and contributor account on platforms like GitHub and npm.

Enforcing MFA makes it exponentially harder for an attacker to compromise an account, even if they have the correct password, as they would also need a second form of authentication, like a code from a mobile app. This simple step can prevent the initial breach that kicks off the entire attack chain.
While adhering to these three core concepts may not offer an impenetrable shield against all future attacks, they serve as a crucial bedrock upon which to construct a robust and adaptive security framework. These concepts are designed not as a static defense, but as a dynamic foundation that allows for continuous improvement and responsiveness to evolving threats.
Fortify your development environment
With new threats constantly emerging, it's crucial for every developer and organization to take immediate steps to secure their development environments.
Here's a checklist of key actions you can take today:
- Audit your dependencies. Regularly check your
package-lock.jsonoryarn.lockfiles for suspicious packages or versions, and use tools likenpm auditto identify known vulnerabilities. - Rotate credentials regularly. Make it a habit to rotate API keys, PATs (Personal Access Tokens), and SSH keys. If a breach is ever suspected, rotate them immediately.
- Migrate CI/CD to OIDC. Prioritize moving publishing workflows away from static secrets to OIDC (OpenID Connect)-based trusted publishing.
- Enforce MFA everywhere. Protect your accounts on GitHub, npm, and other critical platforms with the strongest multi-factor authentication methods available.
- Be cautious with shell scripts. Beware of packages with
postinstallscripts. Before you install, inspect the package's contents or use tools that can analyze package behavior in a sandboxed environment. - Monitor your environment. Stay vigilant for unexpected behavior from your tools, especially those with broad file system access. The weaponization of AI CLIs shows that even trusted tools can be abused.
The rapidly evolving threat landscape means attackers will continue to find creative ways to exploit developer tools. By building a strong foundation with identity-first security, you can ensure your development environments remain secure and innovative.
Auth0 can help fortify your development practices and safeguard your environments with our comprehensive solutions including:
- Multifactor Authentication (MFA): Protect your accounts on critical developer platforms with the strongest MFA methods available.
- OIDC Integration: Prioritize moving your publishing workflows away from static secrets to OIDC-based trusted publishing.
- Fine-Grained Authorization (FGA): Implement least-privilege tokens to limit access and reduce the blast radius of a potential compromise.
About the author

Will Johnson
Developer Advocate
Will Johnson is a Developer Advocate at Auth0. He loves teaching topics in a digestible way to empower more developers. He writes blog posts, records screencasts, and writes eBooks to help developers. He's also an instructor on egghead.io.
View profile