Passwordless Connections
Passwordless connections allow users to log in without the need to remember a password. Instead, users enter their mobile phone number or email address and receive a one-time password (OTP) or link, which they can then use to log in.
When a user authenticates through a passwordless connection, their profile is created on the connection using Auth0 as the Identity Provider (IdP). Since you can't force users to use the same mobile phone number or email address every time they authenticate, users may end up with multiple user profiles in the Auth0 datastore. If this happens, you can associate multiple user profiles by linking their accounts.
Passwordless connection vs. passwordless login
A passwordless connection is another type of connection separate from any existing database, social, or enterprise connections. Even though a user from an Auth0 user database or social provider might share the same email address, the identity associated with their passwordless connection is distinct. As with linking multiple email addresses or mobile phone numbers used for the Passwordless connection, account linking can also be used to associate a passwordless identity with identities from other types of connections.
In addition to supporting passwordless with passwordless connections, Auth0 lets you define a passwordless flow using WebAuthn with Device Biometrics. To learn more, review Configure WebAuthn with Device Biometrics for Passwordless Authentication.
Benefits
The benefits of using passwordless authentication include:
Improved user experience. Users only need an email address or mobile phone number to sign up.
Enhanced security. Passwords are a major vulnerability as users reuse passwords and are able to share them with others. Passwords are the biggest attack vector and are responsible for a significant percentage of breaches. They also lead to attacks such as credentials stuffing, corporate account takeover, and brute force attacks.
Reduced total cost of ownership. Managing passwords is expensive between implementing password complexity policies, managing password expiration and password reset processes, hashing and storing passwords, and monitoring breached password detection.
Supported authentication methods
Auth0 passwordless connections support OTPs sent through SMS or email, and magic links sent through email.
SMS
When using passwordless authentication with SMS, users:
Provide a mobile phone number instead of a username/password combination.
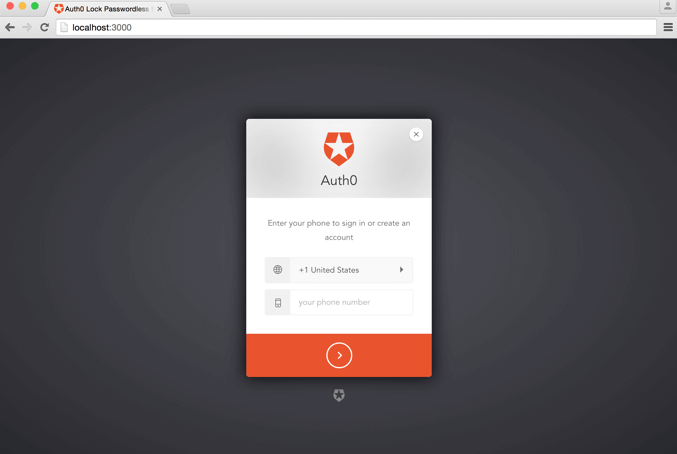
Receive an OTP through SMS.
Enter the OTP on the login screen to access the application.
When using passwordless authentication with email, users:
Provide an email address instead of a username/password combination.
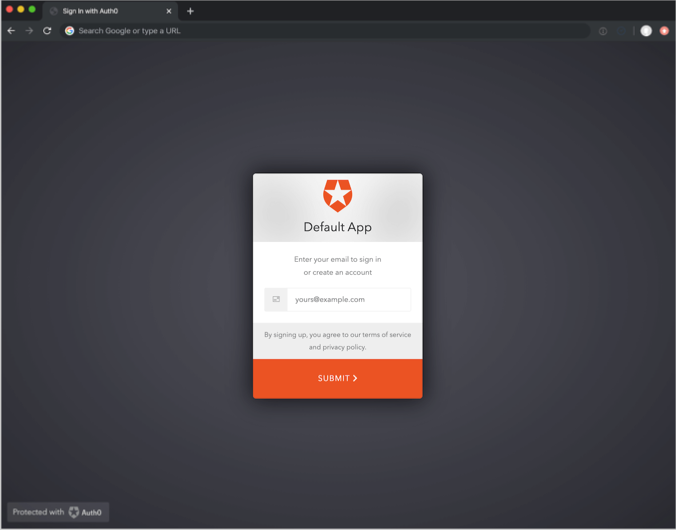
Depending on how you have configured your passwordless connection, receive either an OTP or magic link through email.
Enter the OTP on the login screen (or open the magic link in the email) to access the application.
Implement Passwordless
To implement passwordless, you'll need to make two key decisions:
Which authentication factor(s) you want to support
Which login type you want to use
Authentication factors
When deciding to support an authentication factor, you must consider the user's experience, which that depends on your application and its target audience. If the application will run on mobile phones, it is highly likely that users will be able to receive SMS messages. If it's an internal web application that is used in an environment where users cannot have their mobile phones with them, email would be the only choice.
If you decide to use email, then you need to decide between OTPs or Magic Links. We recommend using OTPs, because the login flow is more predictable for end users. To learn more about authentication factors, read the following articles:
Login type
Auth0 recommends using either the Universal Login or the Classic Login experience to implement Passwordless authentication, but you may decide that Embedded Login is the best choice for your application.
To learn more about how to configure Passwordless authentication for different login types, read the following articles:

