AI agents are moving from helpful assistants to autonomous actors. They don’t just summarize documents or answer questions—they take actions on our behalf: managing calendars, filing support tickets, and even completing purchases.
To do any of that, they need context. Who is the user? What are they allowed to do? What’s happening in the session?
Today, delivering that context to an agent is messy and ad hoc. That’s where the Model Context Protocol (MCP) comes in—a new specification designed to standardize how context is passed to AI models.
At Auth0, we believe MCP is necessary but insufficient.
It’s a great first step, but it must be paired with robust identity and access controls. Without them, AI agents operate on blind trust, which is a massive security and privacy risk.
This is where identity standards like OAuth 2.0 and OIDC, alongside tools like Auth0, come in.
The Rise of Capable AI Agents (and Why Context Matters)
AI agents are growing more capable. Developers are building agents that can:
- Query internal systems and databases
- Execute transactions
- Act as customer support reps or internal assistants
- Chain together APIs and services to complete user goals
However, to act effectively and safely, these agents need access to context—structured information about the user, their permissions, their past behavior, and their intent. Without context, the agent is just guessing.
Today, there’s no standard way to pass that context. Developers are building custom solutions—often without a strong security model.
MCP: A Powerful Foundation for Context
MCP is a crucial step toward solving this. Created by Anthropic, MCP provides a standardized payload format for delivering relevant information to AI agents—user identity hints, permissions, claims, and more.
We applaud the teams defining this specification. Standardization helps agents interoperate, improves developer experience, and lays the groundwork for more powerful agent behavior.
But here’s the catch:
MCP does not secure the payload. It defines what context can be sent—not who can send it, whether they’re authorized, or what the agent can do with it.
This creates significant risk:
- Anyone could invoke an agent.
- Any context could be injected—true or not.
- Any action could be taken on behalf of a user.
MCP is the envelope. But we still need to know who can send it and what the recipient can do with it.
The Critical Missing Layer: Identity
Passing sensitive data or enabling agent actions without robust authentication and authorization is dangerous. We can think of MCP without security the same way as an API endpoint without security – both are just communication protocols, and security must be layered on top. The lack of security could cause:
- Impersonation – Malicious actors pretending to be someone else (i.e., who is really invoking the agent and providing context?)
- Data leakage – Agents receiving context they shouldn’t have access to (i.e., is the context provider authorized to share this specific user data?)
- Privilege escalation – Tricking an agent into acting beyond its scope (i.e., can the agent be tricked into performing actions the user isn’t authorized to do?)
- Compliance violations – handling sensitive data without proper controls (GDPR, CCPA, HIPAA, etc.)
These aren’t hypothetical. AI agents will soon be responsible for customer interactions, business workflows, and system integrations. We can’t afford to leave their security to chance. MCP needs a robust mechanism to verify the source of the context and authorize what context is shared and what actions the agent can subsequently take.
Security must be built in—not bolted on.
Identity Protocols Are the Key
Thankfully, we don’t need to invent a new solution.
Established identity standards—OAuth 2.0 and OpenID Connect (OIDC)—are perfectly suited to solve this problem.
They are mature, well-understood standards for delegated authorization and authentication and provide the exact tools MCP needs:
- OIDC: Authenticates the entity (user, system, or service) interacting with the agent.
- OAuth 2.0: Authorizes what context can be shared and what the agent can do on the user’s behalf—using scopes, access tokens, and delegated permissions.
This makes it possible to:
- Ensure only authenticated users or systems can invoke the agent.
- Use granular scopes to control what context is sent in the MCP payload.
- Define what downstream actions an agent is allowed to take—based on token claims.
As Aaron Parecki notes in his breakdown of OAuth for MCP, these protocols map cleanly onto the challenges MCP doesn’t solve.
Auth0 Is the Bridge
This is where Auth0 fits in.
Auth0 is uniquely positioned to operationalize secure MCP implementations. Our platform brings OAuth 2.0 and OIDC to agents to enable more secure and scalable workflows.
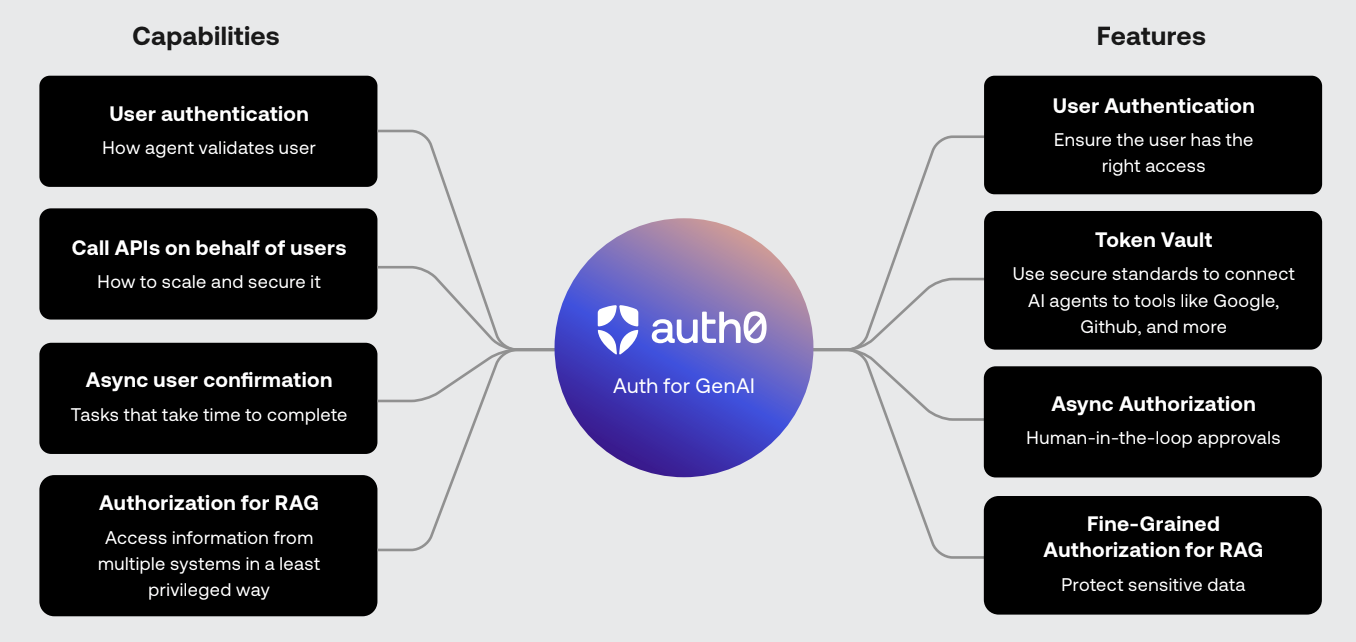
We’re investing in new capabilities designed specifically for AI security, including:
- User authentication to easily implement secure login experiences for AI agents, from interactive chatbots to background workers.
- Token Vault to securely call APIs like Google, Slack, Spotify, and Github on users’ behalf while seamlessly integrating an application with other products.
- Async Authorization to enable autonomous agents to work independently while maintaining user control by getting explicit user approval for critical actions.
- Fine-grained authorization for RAG to enforce granular permissions for document retrieval and helps ensure AI agents only access authorized content.
And because this builds on existing identity infrastructure, you get the benefits of:
- Developer familiarity
- Reduced integration overhead
- Centralized policy management
- Better auditability and compliance
We make securing AI agents feel like a natural extension of your current Auth0 implementation—not a one-off hack.
A Real-World Scenario
Let’s walk through what this looks like in practice:
- A user logs into your customer support portal—powered by Auth0.
- The app requests an access token with scopes like
read:user_profile,read:recent_orders. - Auth0 authenticates the user and issues a signed token containing relevant claims.
- The application constructs an MCP payload using claims from the token.
- The AI agent receives the payload, verifies the token, and uses only the authorized context to respond.
- Later, the user says, “Reorder my last purchase.” The agent requests a new token with the scope
execute:reorder, prompting the user to re-consent via OAuth. - Auth0 issues the new token. The agent performs the action—securely, transparently, and with the user’s permission.
Every step is authenticated. Every action is authorized. Check out more examples on our documents page.
The Bottom Line: Secure AI Starts with Identity
AI agents are the next interface frontier—but only if we get security right.
MCP is foundational—but without an Identity solution, it’s not safe for real-world use.
Auth0 provides the missing layer—bringing identity, permissioning, and governance to the world of AI agents. Our platform makes it possible to adopt MCP without compromising on trust, compliance, or control.
Learn more about securing AI interactions, read our documentation, and contact us to discuss your AI security needs.


