Self-Service SSO is only available to B2B customers on Professional or Enterprise plans.Users with the following Dashboard roles can engage with this feature:
- Admin and Editor - Connections users can create and manage self-service profiles.
- Viewer - Config users can view self-service profiles only.
- Okta Workforce Identity (using OIDC)
- Entra ID
- Google Workspace (using OIDC)
- Keycloak
- Microsoft Active Directory Federation Services (ADFS)
- PingFederate
- Generic OIDC
- Generic
- Okta Workforce Identity (using OIDC)
- Entra ID
- Generic OIDC
- Generic SAML
How it works
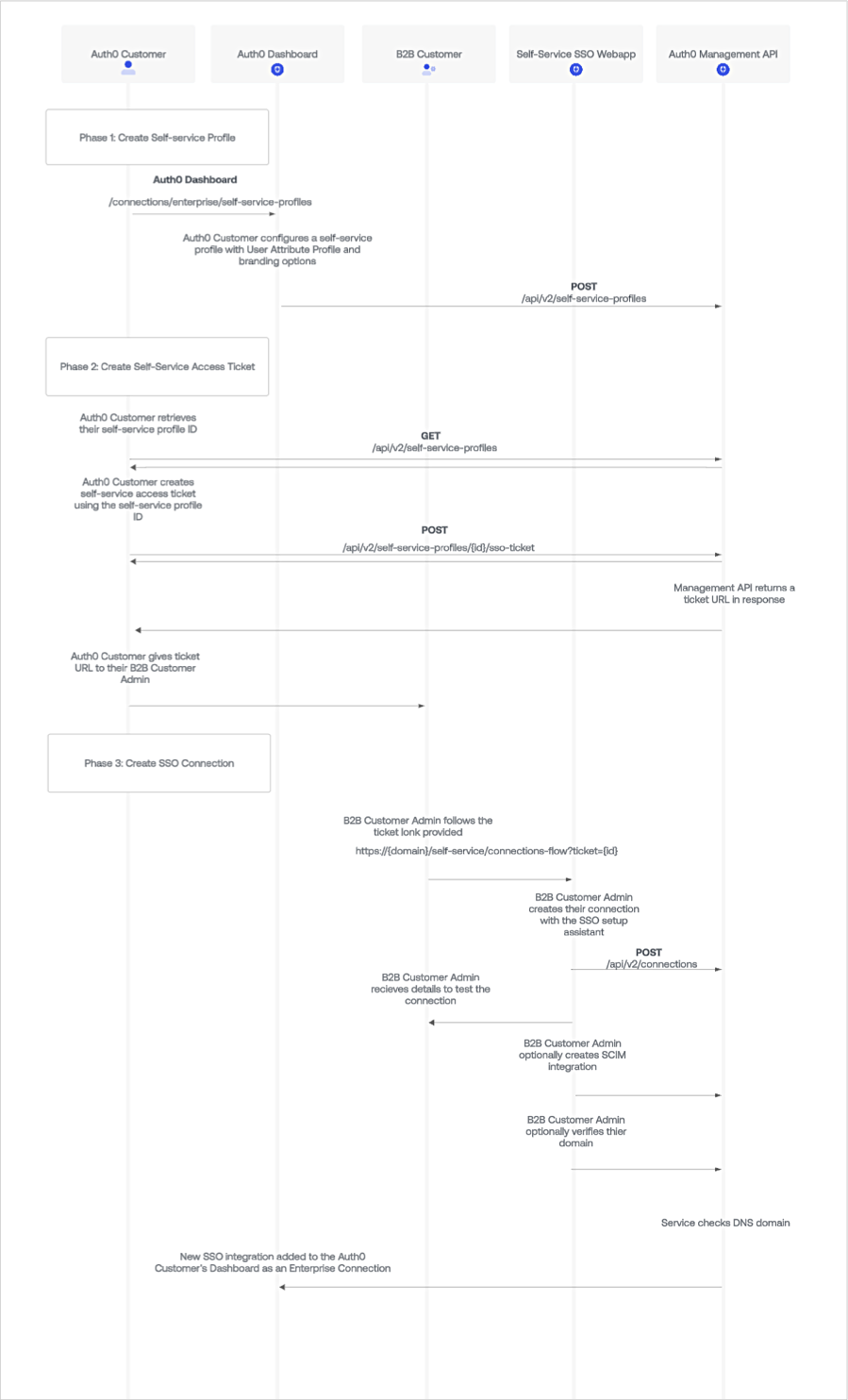
Self-Service SSO uses the following components to delegate setup to your customers:- Self-service profile: Defines key elements of customer SSO implementations, such as the identity providers they can use for SSO and which user attributes they must capture, such as email. You can create up to 20 profiles in your tenant for different customers or segments.
- Self-service access ticket: Grants your customers admin access to the self-service assistant and sets specific details for the resulting Enterprise connection. Those customer admins can either create new or modify existing connections.
- SSO setup assistant: Guides your customer admins through the SSO setup process. To learn more about this experience, review the Self-service assistant experience.
Self-Service SSO workflow
The steps below provide the general workflow for using Self-Service SSO. These tasks can be completed through either the or the .- You (the Auth0 customer) create a self-service profile in your tenant.
- You then create a self-service access ticket associated with that self-service profile. When generating the ticket, you can decide whether your customer admin will create a new connection or modify an existing connection through the self-service assistant.
- You retrieve the ticket URL from the asset created in Step 2 and send the link to your customer admin.
- Your customer admin launches the self-service assistant via the ticket URL and follows the steps provided to configure their connection and optionally complete domain verification. If the ticket is for a single Organization with Discovery enabled, the assistant automatically detects domains already verified for that Organization. This allows the admin to associate existing domains with the new connection instantly, bypassing re-verification.
- A new or updated Enterprise connection pointing to the customer’s application becomes available in your Auth0 tenant.
Self-service assistant experience
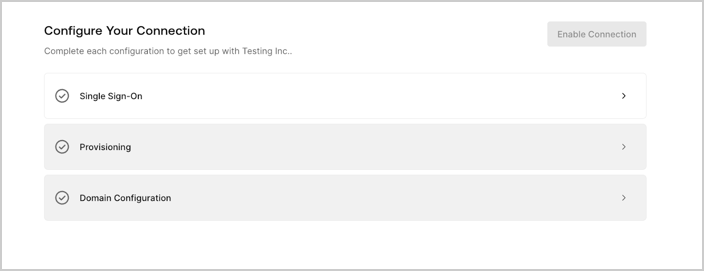
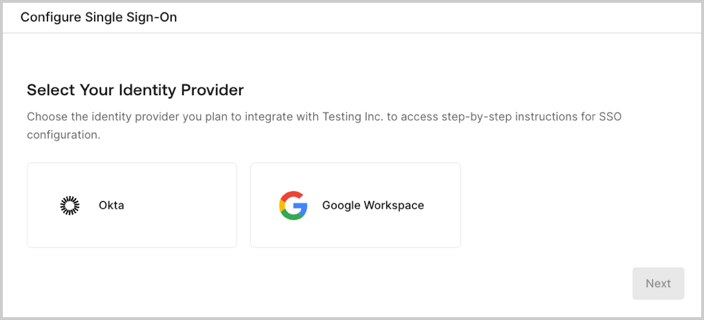
The self-service assistant is a multi-step experience that guides customer admins through configuring SSO and optionally verifying their domain. This experience includes both interactive elements as well as instructions for making the appropriate changes in their selected IdP system. While the exact requirements for configuring SSO vary by IdP, the general workflow for the self-service assistant includes the following:- Select Identity Provider: The customer admin selects which IdP to configure for SSO. The list of options the customer admin can choose from is determined by the associated self-service profile.
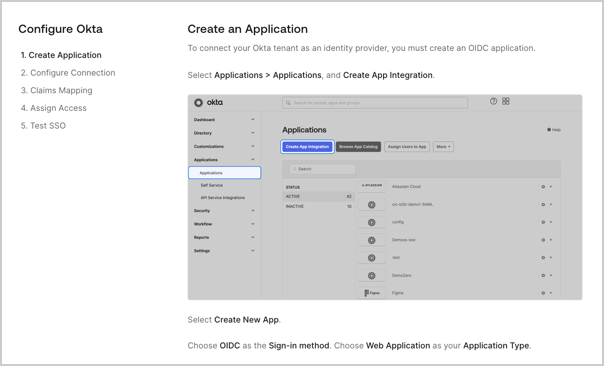
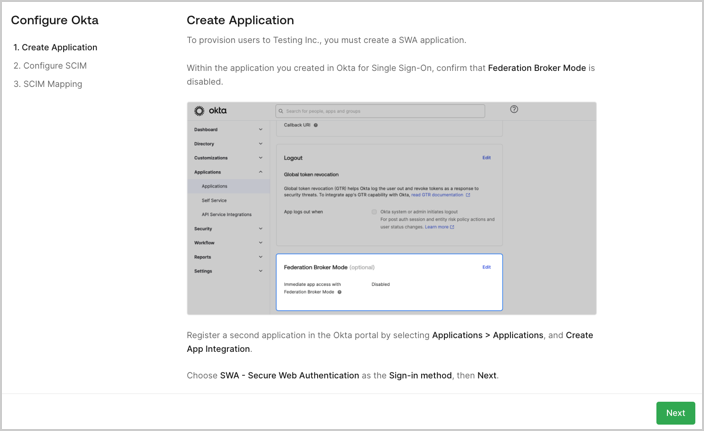
- Create Application: The customer admin follows the written instructions to create an application in their selected IdP system.
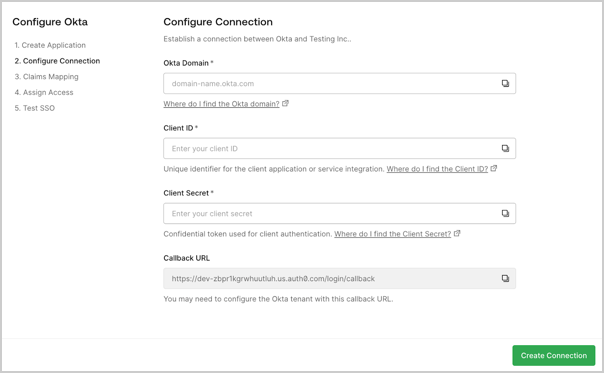
- Configure Connection: The customer admin completes a brief form to create or modify a connection in Auth0. This form collects information such as the customer’s domain, client ID, and client secret.
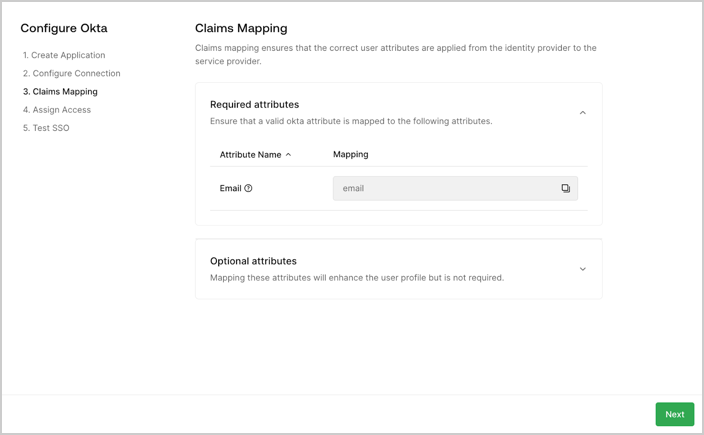
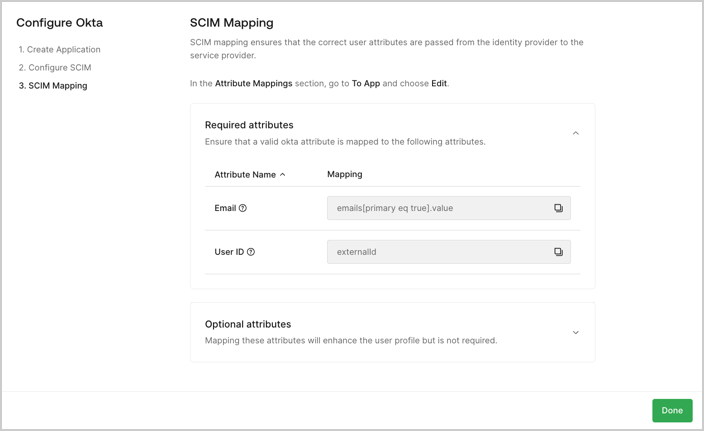
- Claims Mapping: The customer admin reviews the required and optional user attributes they must capture through their SSO connection. Then, they map these user attributes, or claims, in their IdP system.
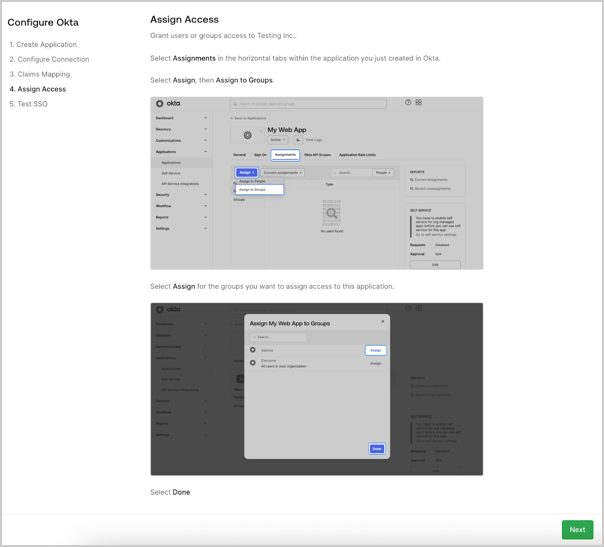
- Assign Access: The customer admin follows the written instructions for their IdP system to grant users or user groups access to your application.
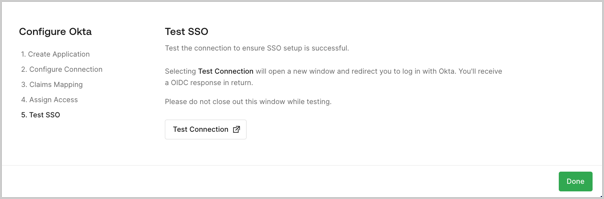
- Test SSO: The customer admin uses the button provided to test their SSO connection in a new tab. Unless domain verification is enabled, the customer admin can complete the setup process after this step to enable their connection.
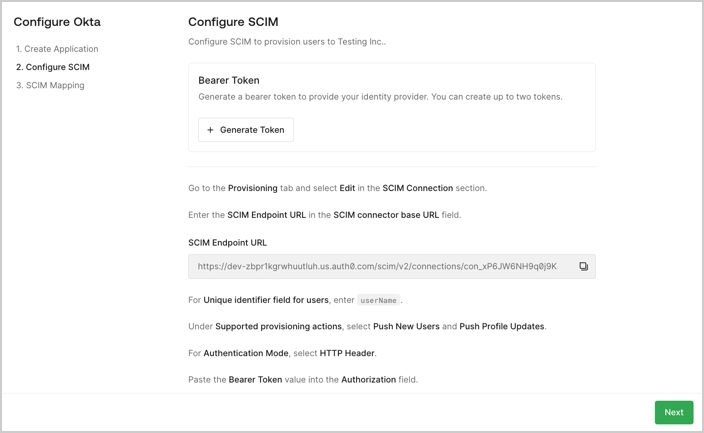
- (Optional) Provisioning: The customer administrator configures user provisioning for their connection by following the provided instructions:
- Create the application in their IdP.
- Generate a SCIM bearer token in the assistant and copy the SCIM bearer token and SCIM endpoint URL into their IdP’s configuration.
- Review the required and optional attributes defined in the User Attribute Profile (UAP). Map these attributes to the corresponding SCIM fields in their IdP system.
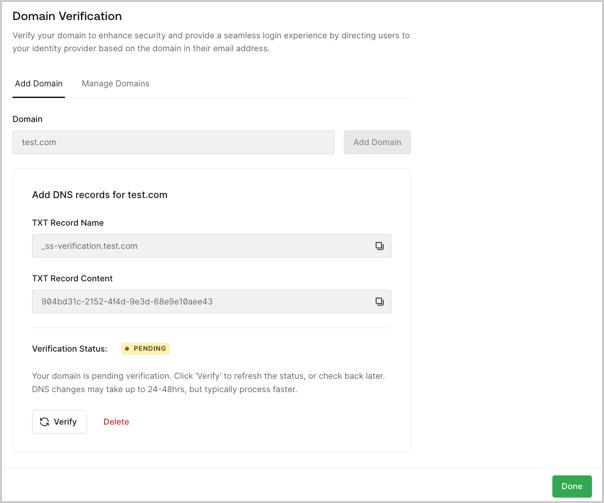
- (Optional) Domain verification and association: Customer admins manage the domains used for authentication and routing. Domain verification requires customers to prove ownership of their domains. Domain association allows the reuse of existing trusted identities.
| Configuration | Description |
|---|---|
| Verified Domain Association | Customer admins select and associate existing domains with the new connection without verifying the DNS TXT record if the ticket is scoped to one Organization and the Organization:
|
Domain Verification set to Required | Customer admins must successfully verify a new domain via DNS or associate an existing verified domain before they can enable the connection. |
Domain Verification set to Optional | Customer admin can choose to enter a new domain for verification, associate an existing one, or skip the step. In all cases, the admin can enable the connection regardless of the verification status. |
Domain Verification set to Off | Custom admins do nothing. This step does not appear to customer admins, and the flow ends after Test SSO. |
| Allow Use of Domains for Organization Discovery is enabled | This option is available when generating a ticket for one Enabled Organization. When selected:
|
Example self-service assistant flow
The images below demonstrate an example self-service assistant experience. In this example, a customer admin configures SSO with Okta Workforce as their IdP. 1. Select Single Sign-On