Private Key JWT Client Authentication for OpenID Connect (OIDC) and Okta Workforce connections is currently available in Early Access. By using this feature, you agree to the applicable Free Trial terms in Okta’s Master Subscription Agreement.
- An increased risk of interception and re-use, as client secrets must be transmitted between parties for every request.
- Limited mechanisms available to enforce expiration and prevent re-use by malicious actors.
- An increased risk of leaks or exposure due to both parties holding the client secret.
How it works
The OIDC Connection flow uses authenticated endpoints such as/oauth/token or /oauth/par to verify a client’s identity against the or OpenID provider. With Private Key JWT Client Authentication, a signed client assertion JWT is passed to the OpenID provider instead of a client secret.
The client assertion JWT contains the following claims:
- An
aud() identifying the OpenID provider’s . - A
jti(JWT ID) to enable one-time use or replay protection. - An
exp(expiration time) that limits the token’s validity window. - A
subandissidentifying the .
Private Key JWT Client Authentication Flow
After a user completes authentication with an upstream (IdP), the user is redirected to Auth0 with an authorization code that is exchanged for tokens at the OpenID provider’s token endpoint. When Private Key JWT is enabled for a connection, the call to the OpenID provider’s token endpoint uses a client assertion instead of a client secret for a more secure authentication. The following steps demonstrate a typical Private Key JWT Client Authentication flow.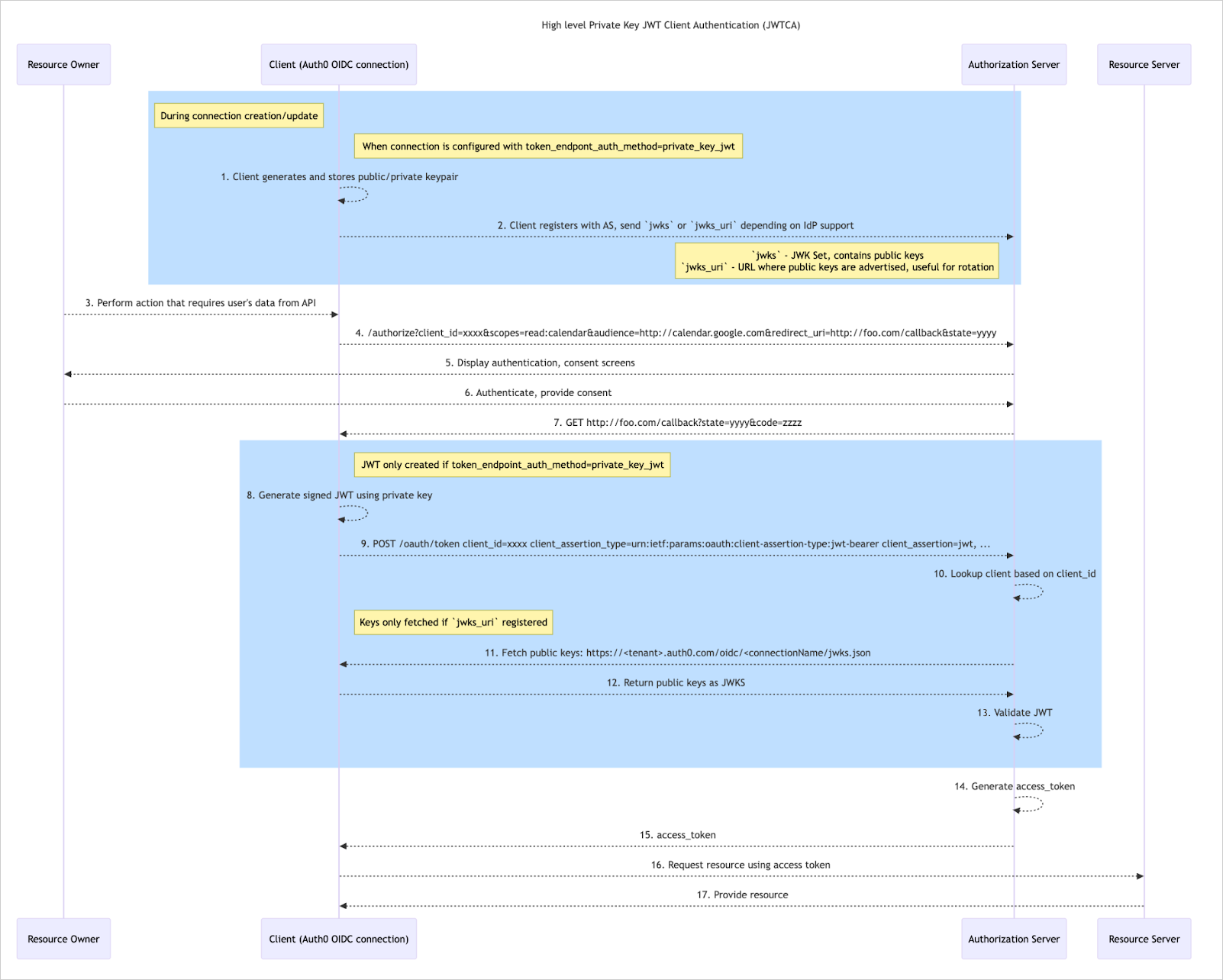
To complete this flow, you must first configure a new or existing OIDC or Okta Workforce connection with
token_endpoint_auth_method=private_key_jwt through either your Auth0 Dashboard or the Management API. To learn more, review the Configure Private Key JWT Client Authentication section.-
After configuring your connection, Auth0 automatically generates and stores two public and private key pairs.
- One key pair is the active
currentset, while the other set is labeled asnextto support key rotation.
- One key pair is the active
-
Depending on your IDP, you next either:
- Download the
currentpublic key and upload the file to the Authorization Server, or: - Copy and paste the
jwks_urito the Authorization Server.
- Download the
- A user performs an action that requires authentication, such as logging in to your application.
- Auth0 sends a request to the Authorization Server to initiate authentication.
- The Authorization Server displays authentication and consent screens to the user.
- The user authenticates and provides consent to the Authorization Server.
- The Authorization Server sends an authorization code to Auth0.
-
Auth0 generates a client assertion JWT and signs it using the
currentprivate key. - Auth0 passes the client assertion JWT to the Authorization Server.
-
The Authorization Server looks up the client based on the provided
client_id. -
The Authorization Server fetches public keys from Auth0 if a
jwks_uriwas provided; otherwise, the server identifies the public key registered in step 2. -
If the
jwks_uriwas requested, Auth0 returns the public keys as JWKS. -
The Authorization Server validates the JWT by verifying the signature with the
currentpublic key, identified bykidin the header of theclient_assertionJWT. - The Authorization Server generates an access token.
- The Authorization Server passes the access token to Auth0.
- Using the access token, Auth0 requests a resource from the Resource Server.
- The Resource Server provides the resource to complete the flow.
Configure Private Key JWT Client Authentication
You can configure OIDC and Okta Workforce enterprise connections to use Private Key JWT Client Authentication through either the Auth0 Dashboard or Management API. Steps for each method are provided below.- Private and public signing key pairs are automatically generated by Auth0 per connection.
- You can currently only use the RS256 algorithm for signing client assertion JWTs.
- Signed JWTs expire automatically after 60 seconds.
Auth0 Dashboard
You can use the Auth0 Dashboard to configure Private Key JWT Client Authentication for both new and existing OIDC and Okta Workforce connections.If your custom OIDC connection uses an IdP that does not advertise support for back-channel communication or
private_key_jwt as a client authentication method in its metadata, you will not be able to set up Private Key JWT Client Authentication through the Auth0 Dashboard.- New Connection
- Existing Connection
- On your Auth0 Dashboard, navigate to Authentication > Enterprise.
- Next to OpenID Connect or Okta Workforce, select Create.
- In the General section, provide details for your new connection, including its name and discovery URL.
-
Configure the following fields to enable Private Key JWT:
- Set Communication Channel to Back Channel.
- Set Authentication Method to Private Key JWT.
- Select Create to save your new connection.
Management API
You can use the Management API to configure Private Key JWT Client Authentication for both new and existing OIDC connections.- New Connection
- Existing Connection
To create a new OIDC connection that uses Private Key JWT Client Authentication, call the Create a Connection endpoint with the following
Example POST call
connection.options properties set appropriately:| Property | Description |
|---|---|
type | Set this property to back_channel. |
token_endpoint_auth_method | Set this property to private_key_jwt. Notes:
|
token_endpoint_auth_signing_alg | Set this property to RS256. Notes:
|
Retrieve Signing Keys
After your connection has been configured to use Private Key JWT Client Authentication, you can retrieve its public keys through either the Auth0 Dashboard, the Management API, or a public JWKS URI.Auth0 Dashboard
Auth0 Dashboard
To retrieve signing keys through the Auth0 Dashboard:
- Navigate to Authentication > Enterprise.
- Next to OpenID Connect or Okta Workforce, select Browse.
- Choose the appropriate connection. Then, access its Credentials tab.
- Locate the Credentials section and select the Download icon next to the appropriate signing key.
Management API
Management API
To view public keys through the Management API, call the Retrieve Connection Signing Keys endpoint using the ID of your connection.Example GET callExample response
Public JWKS URI
Public JWKS URI
Some identity providers allow public keys for private_key_jwt to be provided in the form of a public JWKS (JSON Web Key Set) URI.If public keys have been generated for a connection, you can retrieve them by adding the following URI to your IdP configuration:
Rotate Signing Keys
Private Key JWT Client Authentication supports signing key rotation for increased security compared to the static, long-lived nature of shared client secrets. Rotating signing keys enhances security by limiting the exposure time of any single key, reducing the window of opportunity for an attacker to compromise it. It also allows for rapid response in the wake of a security incident. To avoid disruption, Auth0 recommends rotating signing keys after one year. You can use either the Auth0 Dashboard or the Management API to rotate signing keys:Auth0 Dashboard
Auth0 Dashboard
To rotate your signing keys through the Auth0 Dashboard:
- Navigate to Authentication > Enterprise.
- Next to OpenID Connect or Okta Workforce, select Browse.
- Choose the appropriate connection. Then, access its Credentials tab.
- In the Credentials section, select Rotate Keys.
- On the popup, select Save to confirm the rotation.
Management API
Management API
To view public keys through the Management API, call the Rotate Connection Signing Keys endpoint using the ID of your connection.After rotation, any in-flight JWTs signed with the previous key immediately become inactive and may fail verification with your IdP.
Understanding key rotation
On your OIDC or Okta Workforce connection, your signing keys are assigned one of the following statuses:
- Current: The signing key currently in use for the application.
- Next: The next signing key to use for the application after the current key is revoked.
- Previous: An expired or otherwise revoked signing key that is no longer in use.
current and next keypair is generated. A key is only marked as previous after rotation occurs.When rotating signing keys, the following changes occur:- The
currentkey is removed and revoked, and any JWTs signed with this key will fail verification with the IdP if the IdP was configured with thejwks_uri. - The
currentkey is assigned thepreviousstatus. - The
nextkey becomes the active key and is given thecurrentstatus. Going forward, client assertion JWTs will be signed with this key. - A new signing key is automatically generated to replace the rotated key. The new signing key has the
nextstatus.

