- Maximum Lifetime: Set a refresh token or refresh token family lifetime after which the user must re-authenticate before being issued a new access token. If you disable this setting, the maximum lifetime will be indefinite.
- Idle Lifetime: Set the idle lifetime of issued refresh tokens to expire if the user is not active in your application during a specified period.
Use the Dashboard
- Go to Dashboard > Applications.
- Select the application you want to configure.
- Go to the Settings tab.
-
Under Refresh Token Expiration, enable Set Idle Refresh Token Lifetime. When enabled, a refresh token will expire based on the idle refresh token lifetime, after which the token can no longer be used. If rotation is enabled, an expiration lifetime must be set.
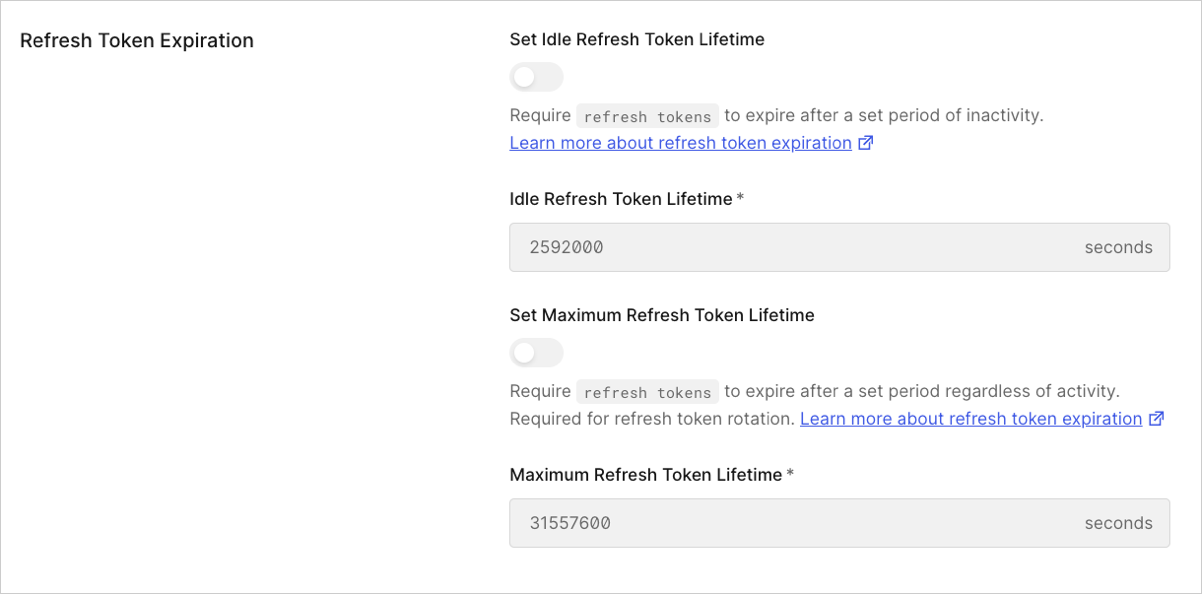
-
Enter Idle Refresh Token Lifetime in seconds. The refresh token expires after the specified interval and can no longer be used to get a new access token. When rotation is enabled, the idle refresh token lifetime also applies to the ability to get new tokens.
Lifetime Value Default 2,592,000 seconds (30 days) Minimum 1 second Maximum 31,557,600 seconds (1 year) - The Idle Refresh Token Lifetime can not exceed the Maximum Refresh Token Lifetime.
- The calculation for one year is equivalent to 365.25 days to account for leap years.
- Enable Set Maximum Refresh Token Lifetime. When enabled, a refresh token will expire based on a specified maximum refresh token lifetime, after which the token can no longer be used.
-
Enter Maximum Refresh Token Lifetime in seconds. If the refresh token is not exchanged within the specified interval, the refresh token expires and can no longer be used to get a new access token. The idle refresh token lifetime expiration period is renewed each time the refresh token is exchanged for a new access token within the interval.
Lifetime Value Minimum 1 second Maximum 31,557,600 seconds (1 year) - Select Save Changes.
Use the Management API
You can configure the maximum and idle lifetime settings in the payload for the Management API /api/v2/clients/ endpoint. Here is an example that sets expiration lifetime for a non-rotating refresh token:Support and limitations
- The maximum refresh token lifetime is determined at issuance and remains fixed throughout its lifetime, even if the application’s maximum refresh token lifetime is updated. However, you can actively override the maximum refresh token lifetime at issuance using sessions with Actions, including during successful refresh token exchanges.
- The idle refresh token lifetime reflects current application settings and updates with each successful refresh token exchange.
- If you configure the Maximum Refresh Token Lifetime for an application, any non-expiring refresh tokens issued by that application becomes expiring refresh tokens after a successful Refresh Token exchange.
- Once a non-expiring refresh token becomes a expiring refresh token, it cannot be reverted back to a non-expiring refresh token.
- You can opt-in to use refresh token expiration capabilities; no action is required by you. Existing refresh tokens are not affected.
- Refresh token expiration works with the following flows:
- All Auth0 SDKs support refresh token expiration.
- The refresh token expiration feature complies with the OAuth 2.0 Security BCP recommendations.
The OAuth BCP states that refresh tokens issued for browser-based applications must have an expiration and either enforce sender-constraint or rotate tokens with each request. Therefore, SPAs will default into rotation and will not support non-expiring refresh tokens.

