Time flies when you are having fun. It's December already and we are getting ready to wrap up this year. 2018 was a prolific year for the Auth0 blog: we published more than 200 posts (😱) where we tackled a diverse amount of topics: frontend and backend technologies, data breaches, GDPR, Cybersecurity, Company Culture, and of course, Identity.
We believe looking back is key to look ahead. That is why this week, we are going to take a look back at the best and most impactful posts we have published in 2018.
One article wouldn't be enough to review this amazing year, that's why we have decided to split this year in review into 3 parts: Developer Posts, Security Posts, and Identity Posts.
Without much further ado, here's the roundup of our 10 most-popular security posts this year!
Auth0's 10 Most-Popular Security Posts in 2018
The following posts are not listed in any particular order.
- What is Data Security?
Security Risk: 20+ Billion IoT Devices by 2020
- 4 Tools To Improve Your Team's Threat Intelligence
- Common Threats in Web Application Security
- Why Customer Identity and Access Management is Critical to Digital Success
- Cloud-Scale Thinking from Day One for Your SaaS Products
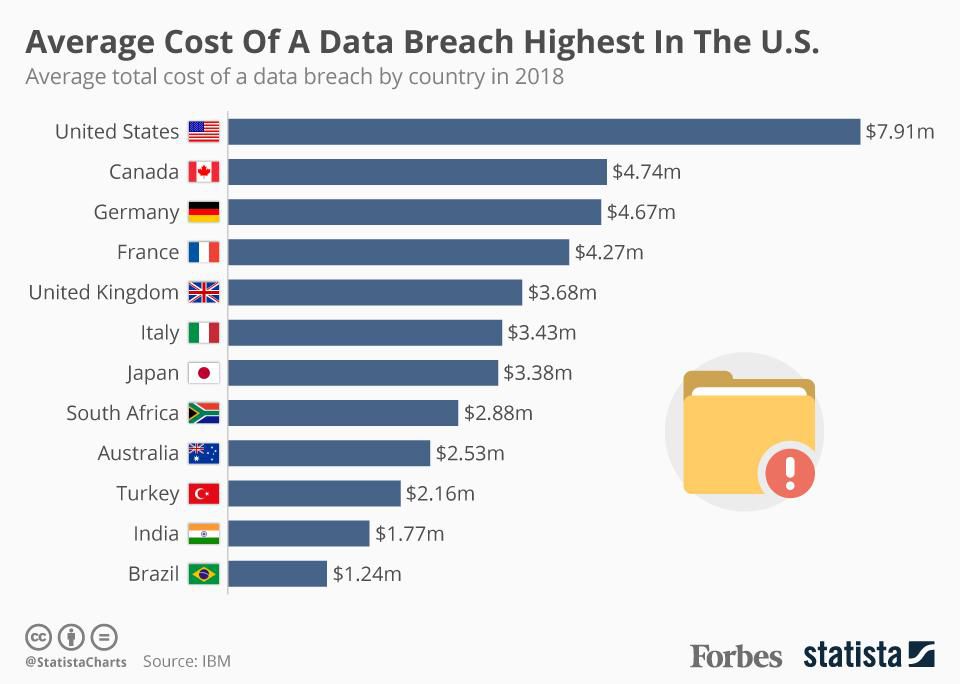
- What is a Data Breach?
- A Tour Through the OWASP Top 10
- How Two-Factor Authentication (2FA) Can Help Financial Institutions Reduce Data Breaches
- Brace Yourself: The GDPR Ripple Effect in California
1. What is Data Security?
What is data security and why it's so important? we've made this article to get you thinking about the definition of data security in the corporate world — and what it means for your team today.
2. Security Risk: 20+ Billion IoT Devices by 2020
Unprotected IoT devices can make it easy for bad actors to cause global damage—botnets increased 140% last year. Gartner analysts predict more than 20 billion connected things will be in use by 2020. Is the world ready for IoT?
3. 4 Tools To Improve Your Team's Threat Intelligence
Four tools to help you cut through the noise, quickly figure out where to focus your energy, and actively respond to suspicious behavior.
4. Common Threats in Web Application Security
In this article we'll attempt to cover a comprehensive security strategy for web applications to protect against common threats in web application security and mitigate their impact.
5. Why Customer Identity and Access Management is Critical to Digital Success
Going through a digital transformation? Maintaining continuous customer engagement throughout this challenging process can help keep sales on track. This article explains how Customer Identity and Access Management can help.
6. Cloud-Scale Thinking from Day One for Your SaaS Products
Explore some of the key technical considerations you have to make while building highly-scalable SaaS products. Learn how to use reliable PaaS (Platform as a Service) vendors available in the market instead of utilizing your valuable engineering resources on infrastructure requirements and make your engineers available to focus on what matters the most, the key features of your project.
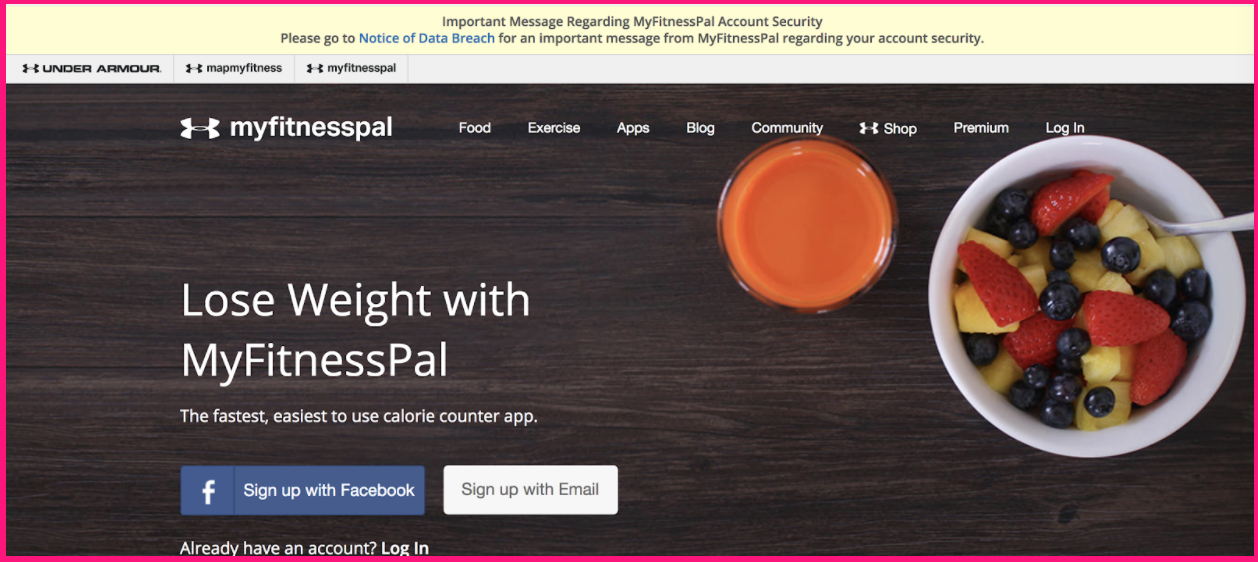
7. What is a Data Breach?
This piece breaks down the new meaning of data leak in today's complex threat environment.
8. A Tour Through the OWASP Top 10
Let's take a run through the OWASP Top 10 looking at the threats and what we could be doing to make sure our own applications are secure, and examine features of the Auth0 platform that help to mitigate or entirely remove such threats from your concern.
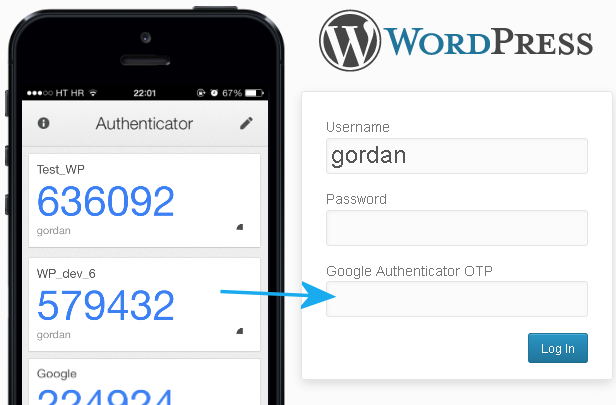
9. How Two-Factor Authentication (2FA) Can Help Financial Institutions Reduce Data Breaches
Two-factor authentication or 2FA adds an additional step to the process. Like a double security door — if a thief unlocks the first one, he's blocked by another. Learn how 2FA can help Financial Institutions reduce Data Breaches.
10. Brace Yourself: The GDPR Ripple Effect in California
2018 was the year that the General Data Protection Regulation (GDPR) finally kicked in. While the GDPR is EU-centric, several countries and states in the U.S. have followed suit with similar privacy initiatives, like the CCPA (California Consumer Privacy Act).
What's Next?
We are already preparing our content pipeline for 2019. Digital privacy and cybersecurity are areas that keep evolving as they are challenged by data breaches, vulnerabilities, and sociopolitical policies. We are committed to keep our blog in sync this constant evolution.
We'd like to take this opportunity to thank all of our readers for their consistent support and feedback. Is there anything that you'd like us to cover in 2019? Any particular security or business trend or topic? Please let us know in the comments below or through social media (Twitter, LinkedIn). As always, you can subscribe to our newsletter to receive a weekly digest of our blog content.
Happy Holiday Season!
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Ramiro Nunez Dosio
Manager, Social Media (Auth0 Alumni)