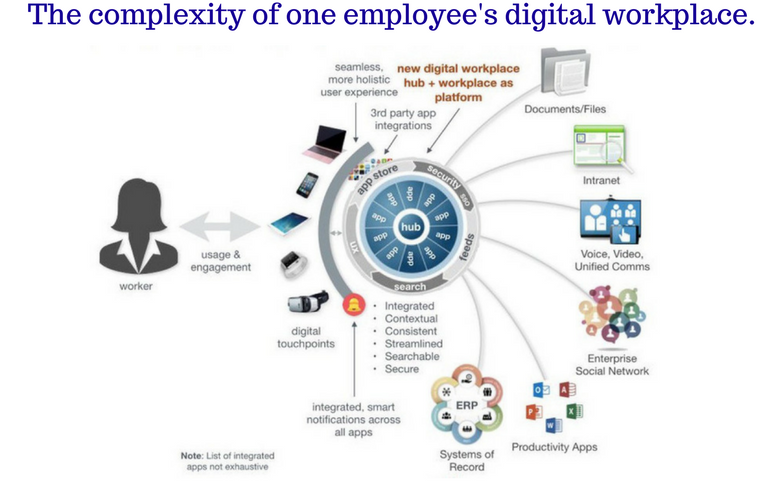
Your company would never let a random person walk through the front door of the office without authorization, grab a cup of coffee and start going through confidential files. In the digital workplace, this is exactly what is happening, minus the coffee.
Today, work happens in the cloud on multiple devices, which means your company's data and systems are accessible from anywhere.
You have to find new ways to manage your employees' identities and permissions, so the right people have access to the right systems and data. While security is critical, adding too many security measures hampers productivity.
So how do you balance security and productivity within the modern digital workplace where employees are using unsanctioned devices, running hundreds of applications and sharing company resources with outside partners?
Start with an identity and access management (IAM) tool that is designed to keep up with the pace of digital transformation.
Simplify the digital workplace with IAM
Software for businesses is booming. But hundreds of applications running on unsanctioned devices poses a huge security risk and keeps IT professionals up at night.
While the complexities of managing access across so many tools and devices is a huge challenge, the benefits of the digital workplace are ushering in a new era of productivity where employees can work anytime, in any place with anyone around the world. Digital transformation is moving fast, and it's your job to stay ahead of the game.
[Source]
That's why cloud IAM tools, like Auth0, are growing so quickly. IT departments no longer need to manage access and authorizations in-house, or scramble to keep up with securing every new application and cloud system that employees bring into the corporate environment.
IAM tools simplify the complexity of the digital workplace by managing all of your user identities and access permissions across your internal systems, employee devices and cloud-based technologies. All of your users, both internal and external, are authenticated and authorized based on the roles that you set within one easy-to-use system.
IAM allows you to keep up with the pace of technology, but more importantly, the security features are designed to enhance productivity. Your organization can maintain high-level security measures, while removing the barriers that interrupt a productive workflow.
Better productivity without a security compromise
Employees expect a quick and seamless experience when accessing all of their tools. When a user can't log in or is locked out, valuable time is lost contacting a help desk. Productivity comes to a screeching halt.
The whole point of digital integration is to be more productive by eliminating tedious and repetitive tasks, including logging in to multiple applications every day. So how can you keep security and permissions in place while eliminating individual logins for every single application? Single sign-on.
In the same way your Google sign-on gives you access to several other applications like Google Analytics, Youtube, and Adwords without re-entering your username and password, good identity management will enable your organization to implement a single sign-on for your entire network.
Once users create their single sign-on (SSO) credentials, they'll no longer have to waste time logging in over and over, giving them a seamless work experience regardless of the application, device or domain.
Single sign-on drastically reduces IT help desk tickets and centralizes admin tasks like password resets. When a password is revised, the change automatically updates every app and system connected to the SSO. IT no longer spends all day helping users with access issues, while your employees enjoy a seamless, more productive work experience.
Added security that provides flexibility
Employees need the flexibility to work on any device or register a new application to conduct business, but the proliferation of 3rd party applications has broadened the security surface area far beyond any internal IT department can manage.
Cyber threats have become an everyday reality for both large and small businesses. The 2016 Cyber Security Intelligence found that 60% of data hacks involved an employee's access data. Either a hacker used an employee's credentials or the employee abused their access privileges.
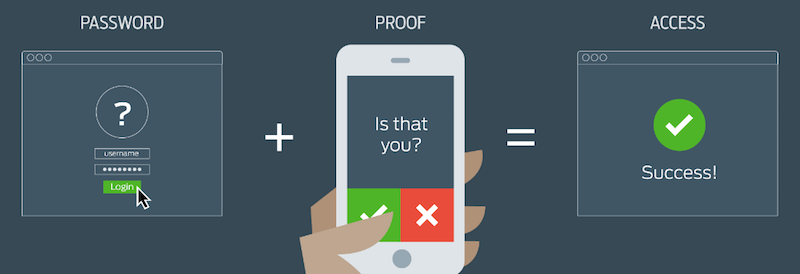
IAM tools that offer multifactor authentication (MFA) provide an extra layer of security that allows your team to use any devices and sign up for new applications without the worry of compromising credentials.
MFA is one of the best ways to identify and verify a user. By asking them for several pieces of information through various stages, the user must demonstrate knowledge (E.g. password or pin number) and possession (E.g. mobile phone). For example, a user is prompted to input their password, which triggers an SMS message with a unique code.
[Source]
When something unusual is detected, such as a sign-in attempt from a new device, MFA requires the user to have two or more types of ID proof before gaining access. If your password is compromised, your account remains safe. Apps like Auth0 Guardian offer easy setup for MFA security.
Multifactor authentication offers the flexibility for employees to securely access their resources wherever and whenever, enhancing their productivity.
Automated permissions keeps business moving
The basic idea behind IAM is to grant each user access to their authorized resources using one set of credentials, which helps streamline IT's workload in tracking permissions. But the bigger challenge for IT is in keeping up with each user's ever-changing privileges status.
In a given week, you can have new employees needing access to start working, other people leaving the company who need their access terminated, and a variety of other employees changing roles, who require different levels of access.
Tracking each user's permissions within an organization is nearly impossible. Your IT team shouldn't waste their valuable time trying to keep up with these constant changes.
The right IAM tool centralizes control of identity and access with an interface that helps you manage every aspect of user ID including automating authorizations, creating and provisioning users, password resets and blocking and deleting users.
Administrators can stay ahead of the constant changes by defining security protocols for specific applications and granting permissions to users to access resources at different levels from a central control panel. For example, when an employee leaves the company, your human resource system triggers IAM to terminate access for that user.
You can also automate authorizations by setting rules that define user requirements, such as by devices, location or by limiting unsanctioned applications from connecting to your corporate environment.
When an employee's status changes, they can't wait days for access. Automated permissions and centralized user management help you keep up with the daily authorization changes.
Stay ahead of your company's digital transformation
Your digital workplace is constantly evolving as technology continues to evolve. Employees have the tools and access to information to be more productive. The goal is to keep your company's resources secure without hindering this new level of productivity.
The right IAM technology solution should deliver the best-in-class security measures that work to create a flexible and efficient workflow for employees across all of their tools. When users have a great work experience, they probably won't thank you, but they will work faster and smarter, which helps the company succeed.
About the author

Diego Poza
Sr Manager, Developer Advocacy (Auth0 Alumni)