It’s June 1972. A man named Frank Wills notices tape covering the locks in the building he’s guarding in Washington, D.C. He untapes them, thinking nothing of it. A few hours later, he returns and the locks are taped once again to keep the doors open. He calls the police.
Five men are arrested in their attempt to wiretap the Democratic Party’s headquarters in the Watergate complex. The group was subsequently found to have ties to President Nixon, and the Watergate scandal became one of the first high-profile data breaches in recent history.
Today, we think of data breaches as the Reddit or T-Mobile incident or the Equifax scandal. But before the internet was ubiquitous, a data breach could mean something as simple as viewing sensitive personal information, like medical or financial records before they were thrown out, or listening in on phone conversations.
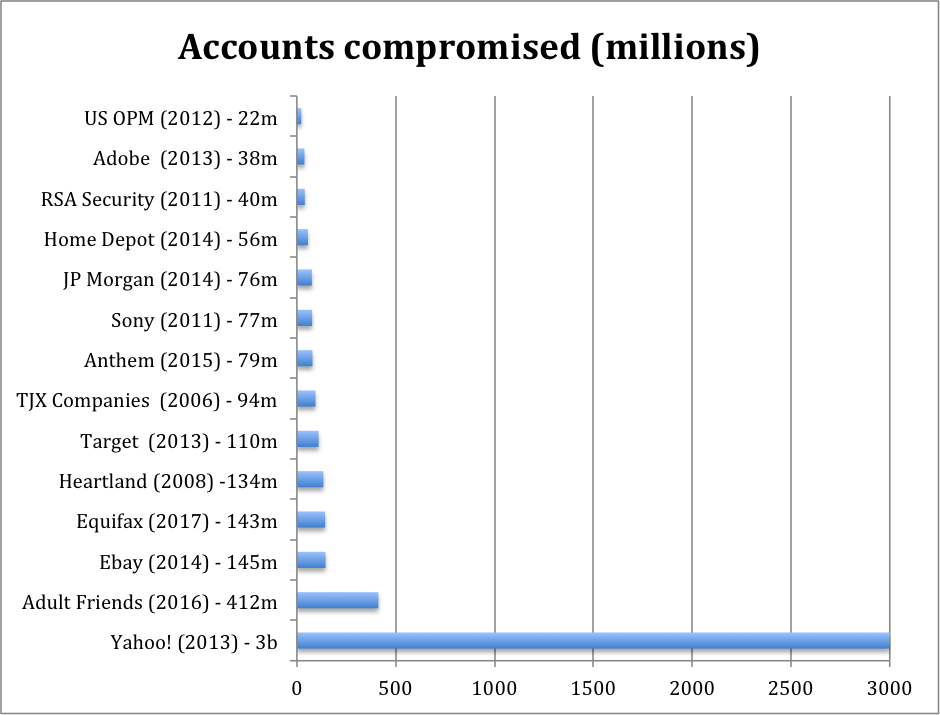
Here’s a breakdown of the largest data breaches in the past decade:
In the first half of 2018 alone, there were 668 breaches and over 22 million records exposed.
Incidents are occurring at an increasing pace, volume, and complexity. What's going on beneath the surface?
How Does a Data Breach Happen?
Cyber attacks on company and personal information can occur in several ways, including common attacks, like:
- Malware (infiltration of malicious software, such as ransomware and spyware, through holes in outdated systems)
- Phishing (e-mails designed to steal data by tricking recipients into installing spyware)
- USB traps (hardware devices that employees often plug into their computers that contain malware)
- Mobile attacks (e.g., phishing text messages)
Unauthorized access is at the root of many harmful data leaks. In March 2018, for example, a user gained access to Under Armour's MyFitnessPal user data. 150 million accounts were compromised, including usernames, email addresses, and hashed passwords — all because a hacker was able to get into their network and extract data undetected.
What a Data breach Can Cost Your Company
A data breach can cost you millions — not to mention lasting reputational damages and loss of customer trust. With the credit card numbers, social security numbers, and other sensitive data from customers that you've stowed suddenly up for grabs, you're vulnerable to a tirade of complaints and churned accounts.
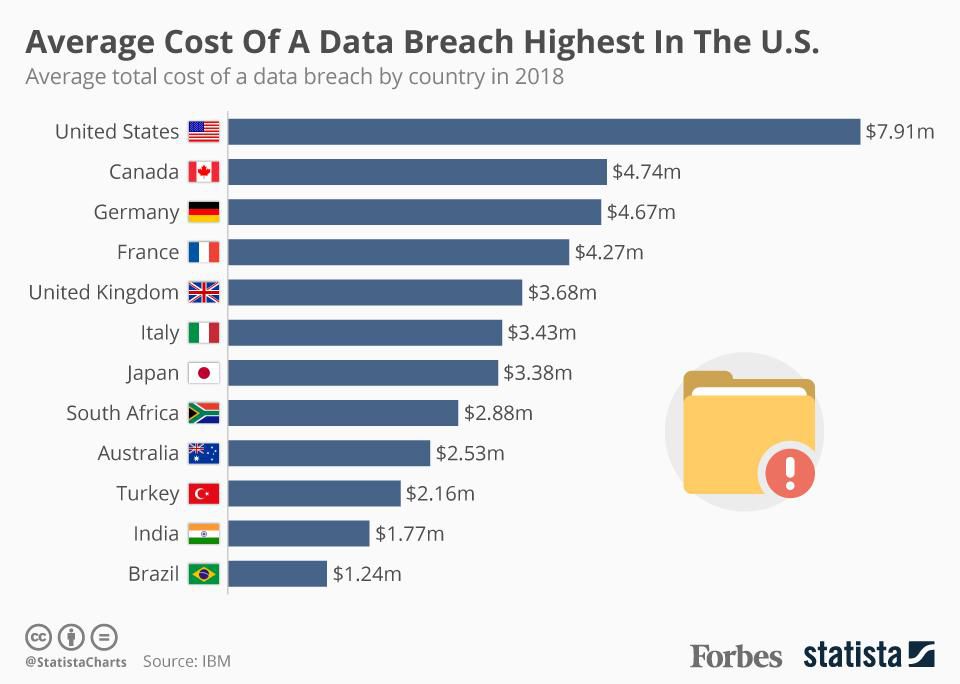
If you're in the U.S., you could be particularly unlucky, with the average financial loss ticking in at $7.91 million per incident.
“The average financial loss in the U.S. is ticking in at $7.91 million per incident.”
Tweet This
This just scratches the surface, however. Equifax, for example, is seeing costs from its massive data breach in 2017 surge past $400 million in 2018.
In settlement costs alone, Target has had to shell out over $18 million following its 2013 incident.
Whether it's legal costs, coughing up money to overhaul your current security system, or increased customer churn — you can’t afford a major data leak.
In a rapidly evolving threat environment, how do you stay safe and avoid a worst-case scenario that derails your progress?
How to Avoid Data Breaches
It’s impossible to fully remove the risk of a security breach as threats are evolving more rapidly than solutions. In recent years we've seen a rise in:
- state-sponsored attacks
- disinformation scandals like Facebook’s
- higher instances of denial of service attacks on IoT devices, and even
- “whaling” of high net worth individuals (a step beyond spear-phishing that lures people to send money to a fake account).
But despite escalating threats and more cases of information stolen, there are several simple steps you can start with (along with more complex solutions after you've nailed down the basics) that can significantly reduce the chances of an incident — no matter what your company size is. You don't have to be a large enterprise to start safeguarding your most important assets.
You’d be surprised at how few companies are taking the basic precautions. Wombat Security recently revealed that nearly 30 percent of employees don't know what phishing is, and almost 60% haven't heard of ransomware. Don't be one of these stats!
Regularly Update Your Software
Many companies, even big successful ones, are working with outdated systems. Modernizing legacy systems and apps can go a long way towards creating a wall that hackers don't breach.
Equifax, for example, had ample opportunity to avoid its massive data leak if it had simply used an available software patch on time.
Instead, attackers entered its system through an unprotected web-application vulnerability. Don’t wait to take precautions.
Implement and Measure Employee Risk Training
While your employees are your biggest asset, they can also be your weakest link when it comes to security. Well-meaning employees might pick up a stray USB device and install it out of curiosity (not knowing it’s plagued by malware) or open an email from an unfamiliar address and unintentionally open a portal to sensitive corporate information.
There are several training programs you can use to make sure your team has the basics down and to help bolster your security. While this is not a comprehensive list, try out courses from:
- Rapid7
- Cofense (formerly PhishMe)
- Wombat Security
- Symantec Security Awareness
- Barracuda PhishLine
If you’re a government organization, the Federal Virtual Training Environment (FedVTE) provides free online modules on risk management and malware analysis. Managed by the U.S. Department of Homeland Security, FedVTE also helps with industry certifications like Certified Information Systems Security Professional (CISSP).
Whatever training route you take, make sure you measure its effectiveness by quantifying changes in employee behavior afterwards. Just 48 percent of organizations said they took time following a training to assess this. You don’t want to make investments that don’t deliver results.
Focus on Identity Management
In addition to an inconsistent user experience, lower conversion rates, and higher developer costs — an inability to manage the identity of your users leads to vulnerable web and mobile applications.
Build or outsource your identity-management needs to proactively vet all users on your platform. This will allow you to more easily implement proven security tools like Multi-factor Authentication or Social Login.
What to Do If a Data Breach Occurs
In the unfortunate event of a security breach, put your customers first. While it’s imperative to investigate the incident, patch and/or completely update your security systems, and train your employees so that they are better able to stop threats before they spiral out of control — you need to quickly communicate the occurrence to your affected (or potentially affected) user base.
Deliver as much information as you can to help your customers understand the scope and details of the incident, reassure them that you are taking steps to rectify the damages, and give them the reins to make additional fixes on their own. This will help them feel more in control of their own security and sensitive information.
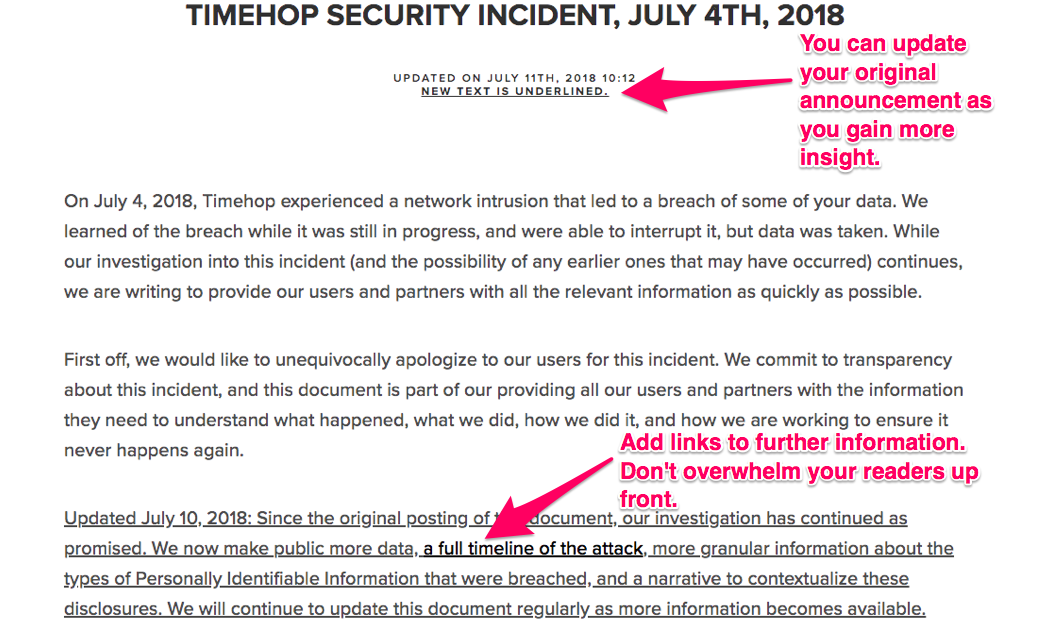
For example, start by publishing an initial announcement on your website:
Include critical information like the date of the breach, what was stolen, what your company is doing to rectify the situation, and what users can do on their end to mitigate damage.
Consider holding off on certain forms of communication like text message alerts. Like we saw with the T-Mobile data breach, these can amplify concerns about phishing and make you seem less professional. While SMS can be a great marketing tactic in campaigns where your users have already opted in and are expecting alerts, it can feel like another intrusion if coupled with a data breach.
Once you communicate the incident in a clear and professional manner, work quickly to update your software, provide additional employee training, and refocus on identity management tools and processes that provide more security and transparency.
Taking swift measures will help you regain customer trust and bolster your organization against further threats so that you can scale without worry.
About the author

Martin Gontovnikas
Former SVP of Marketing and Growth at Auth0 (Auth0 Alumni)
Gonto’s analytical thinking is a huge driver of his data-driven approach to marketing strategy and experimental design. He is based in the Bay area, and in his spare time, can be found eating gourmet food at the best new restaurants, visiting every local brewery he can find, or traveling the globe in search of new experiences.View profile